Run secured archive services on a single host - dcm4che/dcm4chee-arc-light GitHub Wiki
Secured Archive services using Keycloak as Authentication Server.
(Optional) Create system groups and users with particular group and user IDs used by the archive services on the host
$ sudo -i
# groupadd -r slapd-dcm4chee --gid=1021 && useradd -r -g slapd-dcm4chee --uid=1021 slapd-dcm4chee
# groupadd -r postgres-dcm4chee --gid=999 && useradd -r -g postgres-dcm4chee --uid=999 postgres-dcm4chee
# groupadd -r dcm4chee-arc --gid=1023 && useradd -r -g dcm4chee-arc --uid=1023 dcm4chee-arc
# groupadd -r keycloak-dcm4chee --gid=1029 && useradd -r -g keycloak-dcm4chee --uid=1029 keycloak-dcm4chee
# exit
Continue using Docker Command Line or Docker Compose alternatively:
-
$ docker network create dcm4chee_network -
Start OpenLDAP Server as described in Run minimum set of archive services on a single host.
-
Launch a container providing Maria DB Server into the created network, e.g:
$ docker run --network=dcm4chee_network --name mariadb \ -p 3306:3306 \ -e MYSQL_ROOT_PASSWORD=secret \ -e MYSQL_DATABASE=keycloak \ -e MYSQL_USER=keycloak \ -e MYSQL_PASSWORD=keycloak \ -v /etc/localtime:/etc/localtime:ro \ -v /etc/timezone:/etc/timezone:ro \ -v /var/local/dcm4chee-arc/mysql:/var/lib/mysql \ -d mariadb:10.11.4Publishing MariaDB Server port
3306from the container to the host by-p 3306:3306enables to access the MariaDB Server also by external MariaDB/MySQL clients. It is not required for running Keycloak, because the Keycloak container connects the Server port of the MariaDB Server container over the created bridge network.-e MYSQL_ROOT_PASSWORD=secret -e MYSQL_DATABASE=keycloak \ -e MYSQL_USER=keycloak \ -e MYSQL_PASSWORD=keycloak \set the password of the MariaDB
rootsuperuser account, the name of the database, a user and its password.See further available environment variables of the MariaDB container.
Bind mount
-v /etc/localtime:/etc/localtime:roand-v /etc/timezone:/etc/timezone:roduplicates your host timezone inside the container. Otherwise, the container timezone is UTC. Attention: If there is no/etc/timezoneon your host, you have to create one (e.g.:$ echo "Europe/Vienna" > /etc/timezone) before launching the container, otherwise the container will not start.Bind mount
-v /var/local/dcm4chee-arc/mysql:/var/lib/mysqltakes care to store the database in the specified host directory. It is initialized on first container start-up if it is not already present in the specified host directory. That ensures that the data does not get lost on deletion and re-creation of the MariaDB Server container. -
Launch a container providing preconfigured Keycloak Authentication Server into the created network, e.g:
$ docker run --network=dcm4chee_network --name keycloak \ -p 8843:8843 \ -e KC_HTTPS_PORT=8843 \ -e KC_HOSTNAME=https://<docker-host>:8843 \ -e KC_HOSTNAME_BACKCHANNEL_DYNAMIC=true \ -e KC_BOOTSTRAP_ADMIN_USERNAME=admin \ -e KC_BOOTSTRAP_ADMIN_PASSWORD=changeit \ -e KC_DB=mariadb \ -e KC_DB_URL_DATABASE=keycloak \ -e KC_DB_URL_HOST=mariadb \ -e KC_DB_USERNAME=keycloak \ -e KC_DB_PASSWORD=keycloak \ -e KC_LOG=file \ -e ARCHIVE_HOST=<docker-host> \ -e KEYCLOAK_WAIT_FOR="ldap:389 mariadb:3306" \ -v /etc/localtime:/etc/localtime:ro \ -v /etc/timezone:/etc/timezone:ro \ -v /var/local/dcm4chee-arc/keycloak:/opt/keycloak/data \ -d dcm4che/keycloak:26.0.6-p 8843:8843 \publishes the https (
8843) port of Keycloak from the container to the host to enable connections from external https clients to Keycloak.The port number is set by:
-e KC_HTTPS_PORT=8843 \to avoid collisions with the https port used by Wildfly with the deployed dcm4che Archive 5 application by default.
-e KC_HOSTNAME=https://<docker-host>:8843 \specifies the full URL the Keycloak server will become accessible for external clients - particularly web browsers.
-e KC_HOSTNAME_BACKCHANNEL_DYNAMIC=true \enables to access backend endpoints of the Keycloak server by a different URL as the frontchannel configured by
KC_HOSTNAME, enabling communication over docker overlay/bridge networks from other docker containers - particularly from the archive container.-e KC_BOOTSTRAP_ADMIN_USERNAME=admin \ -e KC_BOOTSTRAP_ADMIN_PASSWORD=changeit \is required to create an admin account to be able to login to the admin console of the Keycloak master realm at
https://${KC_HOSTNAME}:${KC_HTTPS_PORT}[/${KC_HTTP_RELATIVE_PATH}]. Once the first user with administrative rights exists, you may use the UI to change the password or create additional admin users and/or delete that initial admin user.-e KC_DB: mariadb -e KC_DB_URL_DATABASE: keycloak -e KC_DB_URL_HOST: mariadb -e KC_DB_USERNAME: keycloak -e KC_DB_PASSWORD: keycloakspecifies the database vendor, name, host, user name and password of the database used by Keycloak.
KC_DB_URL_DATABASE,KC_DB_USERNAMEandKC_DB_PASSWORDhave to match with the values set forMYSQL_DATABASE,MYSQL_USERandMYSQL_PASSWORDon launching the MariaDB Server container, andKC_DB_URL_HOSThave to match with its container name.KC_LOG=fileenables logging to file
/opt/keycloak/data/keycloak.log, instead of logging to the standard output.If you set the environment variables
LDAP_BASE_DN,LDAP_ROOTPASSfor the LDAP server container, you have to set that environment variables also for the Keycloak container. Otherwise Keycloak will fail to connect to the LDAP Server.-e ARCHIVE_HOST=<docker-host> \specify the public hostname of the archive device referred by OIDC Keycloak clients for securing the UI and the Wildfly Administration Console of the archive initialized on first startup. You have to replace <docker-host> by the hostname of the docker host, which must be resolvable by your DNS server.
-e KEYCLOAK_WAIT_FOR=ldap:389 mariadb:3306delays the start of Keycloak until OpenLDAP slapd and MariaDB server is listening on the specified ports, which prevents error on restart of all containers caused by failures to connect LDAP by Keycloak, before OpenLDAP slapd and MariaDB server is ready to accept connections.For further available environment variables of the Keycloak container see https://github.com/dcm4che-dockerfiles/keycloak-quarkus#environment-variables.
Bind mount
-v /etc/localtime:/etc/localtime:roand-v /etc/timezone:/etc/timezone:roduplicates your host timezone inside the container. Otherwise the container timezone is UTC. Attention: If there is no/etc/timezoneon your host, you have to create one (e.g.:$ echo "Europe/Vienna" > /etc/timezone) before launching the container, otherwise the container will not start.Bind mount
-v /var/local/dcm4chee-arc/keycloak:/opt/keycloak/datamaps Keycloak log and temporary files to the specified host directory.By default the https service will use the certificate
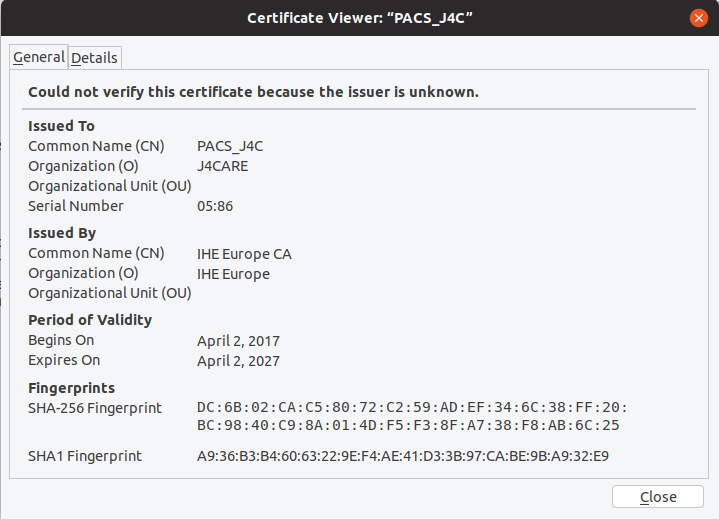 for handling TLS connections. To avoid the security warning of Web Browsers accessing the Keycloak UI or the WildFly
Administration Console, you have to provide a certificate which Common Name and/or Subject Alt Name matches
the host name and which is signed by a trusted issuer in a keystore file in PKCS #12
or Java KeyStore (JKS)
format, bind mount the file or its containing directory into the container, and refer it by environment variable
KC_HTTPS_KEY_STORE_FILE.
for handling TLS connections. To avoid the security warning of Web Browsers accessing the Keycloak UI or the WildFly
Administration Console, you have to provide a certificate which Common Name and/or Subject Alt Name matches
the host name and which is signed by a trusted issuer in a keystore file in PKCS #12
or Java KeyStore (JKS)
format, bind mount the file or its containing directory into the container, and refer it by environment variable
KC_HTTPS_KEY_STORE_FILE.Check the Keycloak server log if Keycloak started successfully:
$ tail -f /var/local/dcm4chee-arc/keycloak/log/keycloak.log 2022-06-09 16:06:19,360 INFO [org.jgroups.protocols.pbcast.GMS] (keycloak-cache-init) 875d7be6d885-1337: no members discovered after 2002 ms: creating cluster as coordinator 2022-06-09 16:06:19,369 INFO [org.infinispan.CLUSTER] (keycloak-cache-init) ISPN000094: Received new cluster view for channel ISPN: [875d7be6d885-1337|0] (1) [875d7be6d885-1337] 2022-06-09 16:06:19,373 INFO [org.infinispan.CLUSTER] (keycloak-cache-init) ISPN000079: Channel `ISPN` local address is `875d7be6d885-1337`, physical addresses are `[172.21.0.3:44392]` 2022-06-09 16:06:19,873 INFO [org.keycloak.connections.infinispan.DefaultInfinispanConnectionProviderFactory] (main) Node name: 875d7be6d885-1337, Site name: null 2022-06-09 16:06:19,935 INFO [org.keycloak.services] (main) KC-SERVICES0050: Initializing master realm 2022-06-09 16:06:22,169 INFO [org.keycloak.services] (main) KC-SERVICES0004: Imported realm dcm4che from file /opt/keycloak/bin/../data/import/dcm4che-realm.json. 2022-06-09 16:06:22,405 INFO [org.keycloak.services] (main) KC-SERVICES0009: Added user 'admin' to realm 'master' 2022-06-09 16:06:22,719 INFO [io.quarkus] (main) Keycloak 19.0.1 on JVM (powered by Quarkus 2.7.5.Final) started in 8.238s. Listening on: https://0.0.0.0:8843 2022-06-09 16:06:22,719 INFO [io.quarkus] (main) Profile prod activated. 2022-06-09 16:06:22,719 INFO [io.quarkus] (main) Installed features: [agroal, cdi, hibernate-orm, jdbc-h2, jdbc-mariadb, jdbc-mssql, jdbc-mysql, jdbc-oracle, jdbc-postgresql, keycloak, logging-gelf, narayana-jta, reactive-routes, resteasy, resteasy-jackson, smallrye-context-propagation, smallrye-health, smallrye-metrics, vault, vertx]
See further environment variables of Keycloak
-
Start PostgreSQL Server as described in Run minimum set of archive services on a single host.
-
Launch a container providing Wildfly with deployed dcm4che Archive 5 application into the created network, e.g:
$ docker run --network=dcm4chee_network --name arc \ -p 8080:8080 \ -p 8443:8443 \ -p 9990:9990 \ -p 9993:9993 \ -p 11112:11112 \ -p 2762:2762 \ -p 2575:2575 \ -p 12575:12575 \ -e POSTGRES_DB=pacsdb \ -e POSTGRES_USER=pacs \ -e POSTGRES_PASSWORD=pacs \ -e AUTH_SERVER_URL=https://keycloak:8843 \ -e UI_AUTH_SERVER_URL=https://<docker-host>:8843 \ -e WILDFLY_WAIT_FOR="ldap:389 db:5432 keycloak:8843" \ -v /etc/localtime:/etc/localtime:ro \ -v /etc/timezone:/etc/timezone:ro \ -v /var/local/dcm4chee-arc/wildfly:/opt/wildfly/standalone \ -d dcm4che/dcm4chee-arc-psql:5.34.2-securewhich differs from Run minimum set of archive services on a single host only by
-
-e AUTH_SERVER_URL=https://keycloak:8843- ensures, that the archive connects to the keycloak container via the bridge network using the right port, specified by keycloak container-e KC_HTTPS_PORT=8843, -
-e UI_AUTH_SERVER_URL=https://<docker-host>:8843- you have to replace <docker-host> by the hostname of the docker host, which must be resolvable by your DNS server - and -
-d dcm4che/dcm4chee-arc-psql:5.34.2-secure- to select the Docker image for the Archive with secured UI and secured RESTful services. If you want to secure the Archive UI without securing the RESTful services use-d dcm4che/dcm4chee-arc-psql:5.34.2-secure-uiinstead.
If you set the environment variables
REALM_NAMEorSSL_REQUIREDfor the Keycloak server container, you have to set that environment variables also for the Archive container. Otherwise the background out of band REST invocation to Keycloak for user authorization will fail.If you want to run more than one Archive container, you have to specify different values for environment variable
UI_CLIENT_ID(default:dcm4chee-arc-ui), and register each of the Archive UIs in Keycloak.See further environment variables of Archive
-
-
Sign in with User/Password
root/changeitat the Realm Admin Console of Keycloak athttps://<docker-host>:8843/admin/dcm4che/consoleNote :- Replace
<docker-host>by the hostname of the docker host. - If you changed the default realm name
dcm4cheby environment variable REALM_NAME for Keycloak and Archive Containers, replacedcm4cheby that value in the URL.
Keycloak docker image
dcm4che/keycloak:26.0.6and newer creates an OIDC client for the Archive UI on first startup, customizable by environment variables :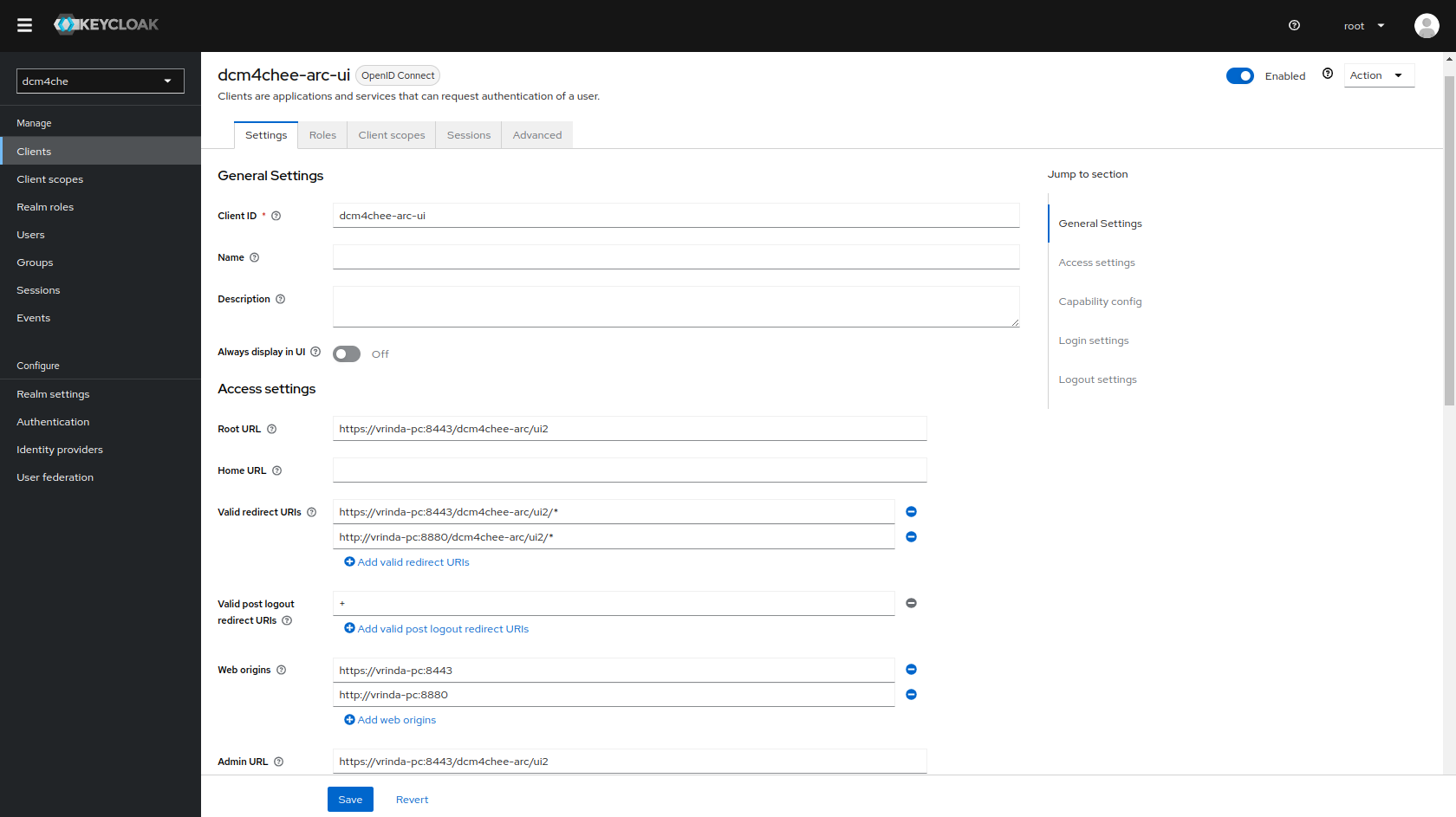
Only users with role
userare permitted to access the Archive UI and RESTful services. Depending on the UI Permission Configuration particular UI features are restricted to additional user roles. Users with roleroot- or the value specified by environment variable SUPER_USER_ROLE for the Archive container - have access to all UI features, independent of their other roles and configured UI Permissions.Sign out, before verifying that accessing the Archive UI at
http://<docker-host>:8080/dcm4chee-arc/ui2orhttps://<docker-host>:8443/dcm4chee-arc/ui2will redirect you to the Login page of Keycloak. You may sign in with User/Passwordroot/changeit,admin/changeitoruser/changeit.Every user can change her password and other account settings via
Edit Accountin theSign-in Toolsin the upper right corner of the Archive UI. Users withrealm-management -> view-realmrole mapped to them, also have a linkAdmin Realmto view the Keycloak Realm Admin Console.Only users with all roles specified by client
realm-managementare permitted to access the Keycloak Administration Console and perform administration changes. - Replace
-
Access to the Wildfly Administration Console is also protected with Keycloak.
Keycloak docker image
dcm4che/keycloak:26.0.6and newer creates also another OIDC client for the Wildfly Administration Console on first startup, customizable by environment variablesWILDFLY_CONSOLE,ARCHIVE_HOSTandARCHIVE_MANAGEMENT_HTTPS_PORT: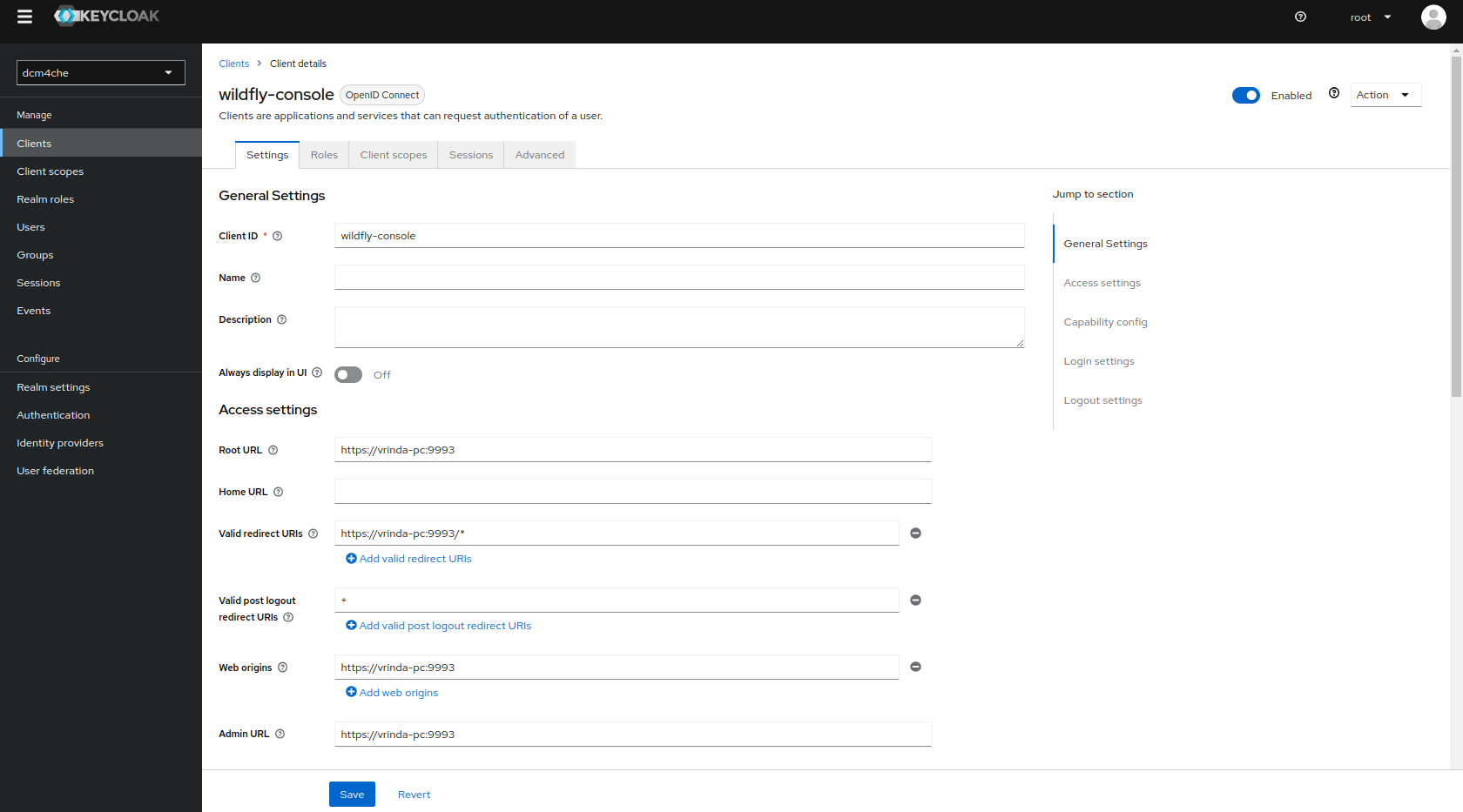
Only users with role
ADMINISTRATORare permitted to access the WildFly Administration Console.Sign out, before verifying that accessing the WildFly Administration Console at
http://<docker-host>:9990orhttps://<docker-host>:9993will redirect you to the Login page of Keycloak. You may sign in with User/Passwordroot/changeit. -
Secured archive setup has pre-configured users / roles intended for different purposes - refer Secure Archive Users and Roles.
Optionally, add separate users for Keycloak / Wildfly administration to decouple roles / responsibilities of archive
rootuser :Name Password Role(s) wildfly-adminchangeituser
ADMINISTRATORkeycloak-adminchangeituser
all roles specified by clientrealm-managementusing scripts :
-
add-keycloak-admin
$ docker exec ldap add-keycloak-admin keycloak-admin changeit adding new entry "uid=keycloak-admin,ou=users,dc=dcm4che,dc=org" modifying entry "cn=user,ou=users,dc=dcm4che,dc=org" modifying entry "cn=create-client,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=impersonation,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=manage-authorization,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=manage-clients,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=manage-events,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=manage-identity-providers,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=manage-realm,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=manage-users,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=realm-admin,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=view-authorization,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=view-clients,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=view-events,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=view-identity-providers,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=view-realm,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=view-users,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=query-users,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=query-groups,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=query-realms,ou=realm-management,dc=dcm4che,dc=org" modifying entry "cn=query-clients,ou=realm-management,dc=dcm4che,dc=org" -
add-wildfly-admin
$ docker exec ldap add-wildfly-admin wildfly-admin changeit adding new entry "uid=wildfly-admin,ou=users,dc=dcm4che,dc=org" modifying entry "cn=user,ou=users,dc=dcm4che,dc=org" modifying entry "cn=ADMINISTRATOR,ou=users,dc=dcm4che,dc=org"resulting in
By default,
rootuser hasADMINISTRATORas well as all roles specified by clientrealm-management: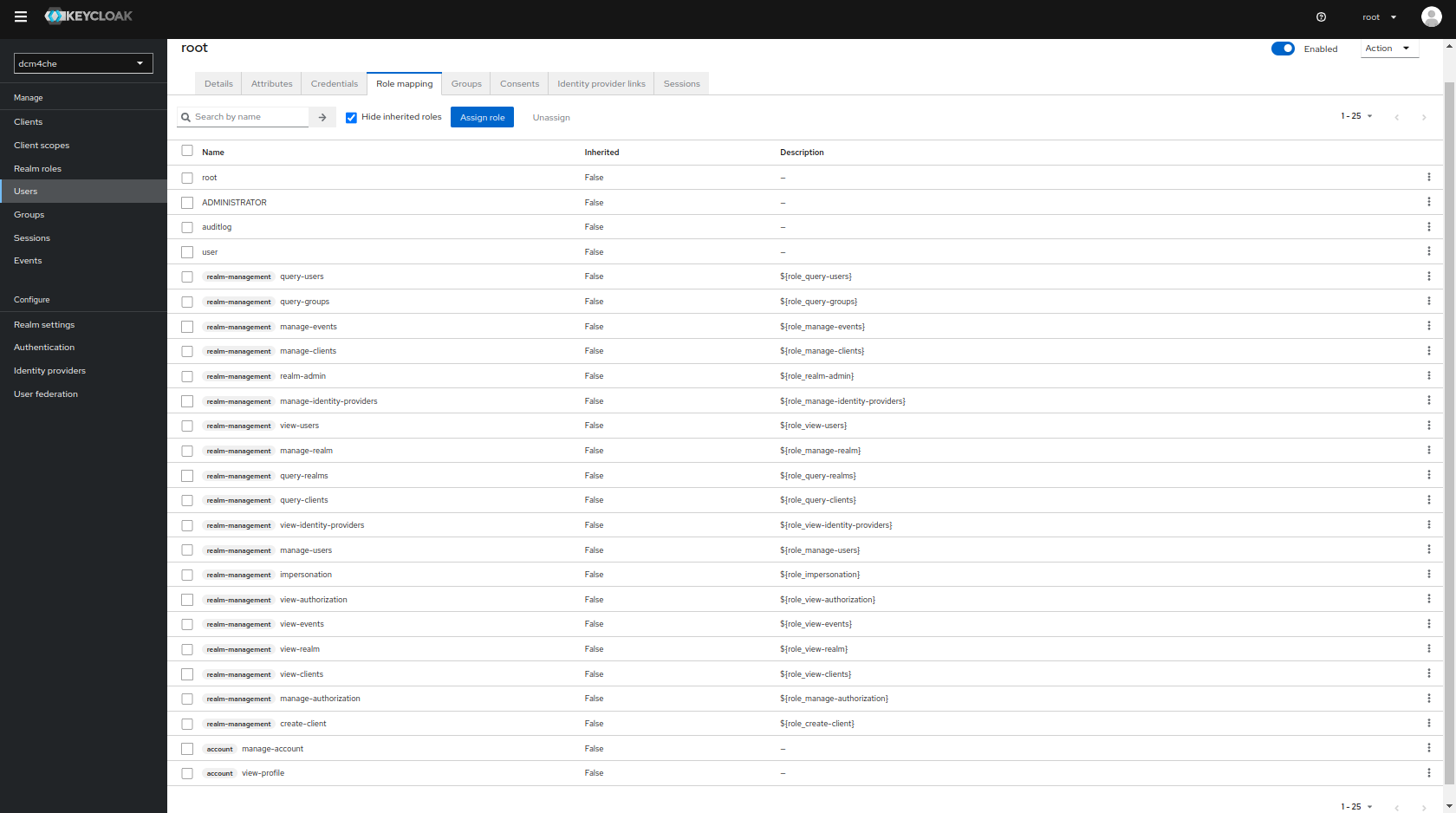
to allow full access to the Realm Admin Console of Keycloak and Wildfly Administration Console. If decoupling of management functions is required by your application, log in to Keycloak Admin Console at
https://<docker-host>:8843/admin/dcm4che/consolewithkeycloak-adminuser and unassignADMINISTRATORandrealm-managementclient role mappings fromrootuser.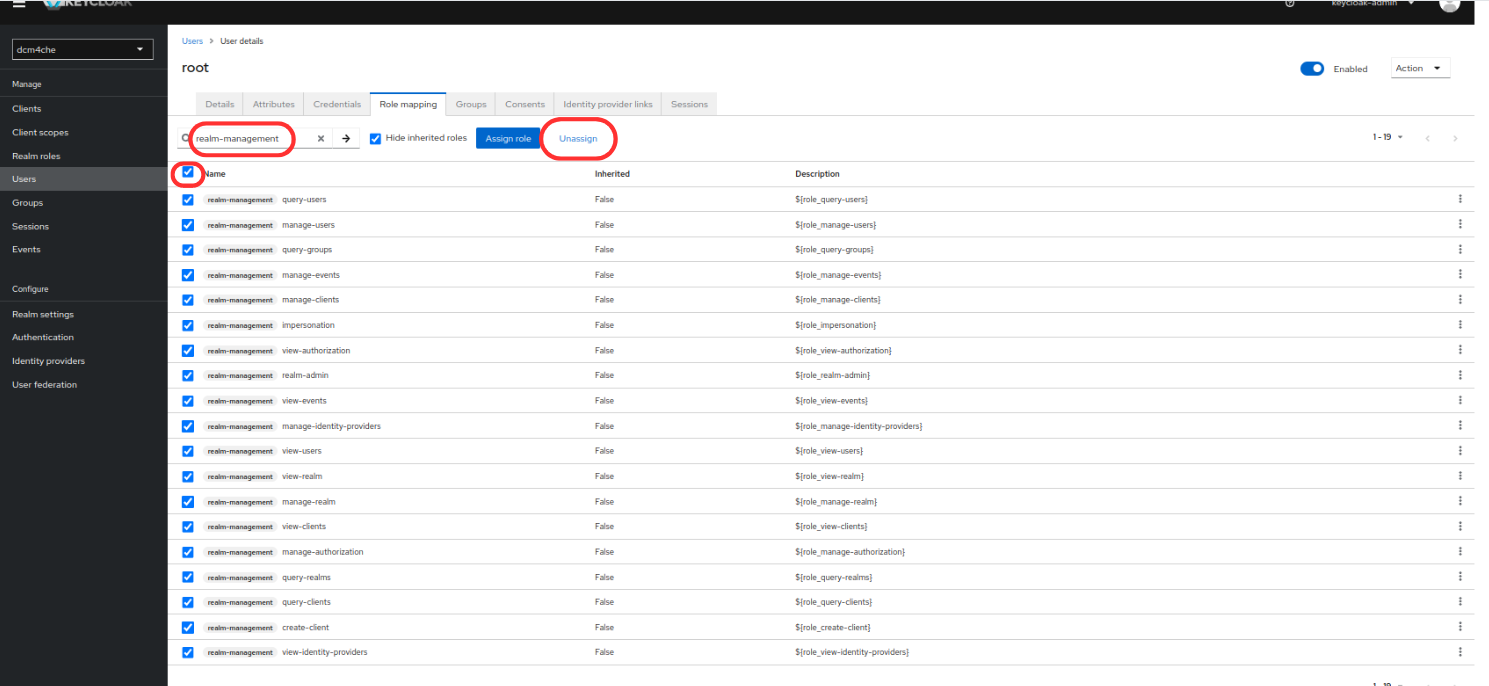
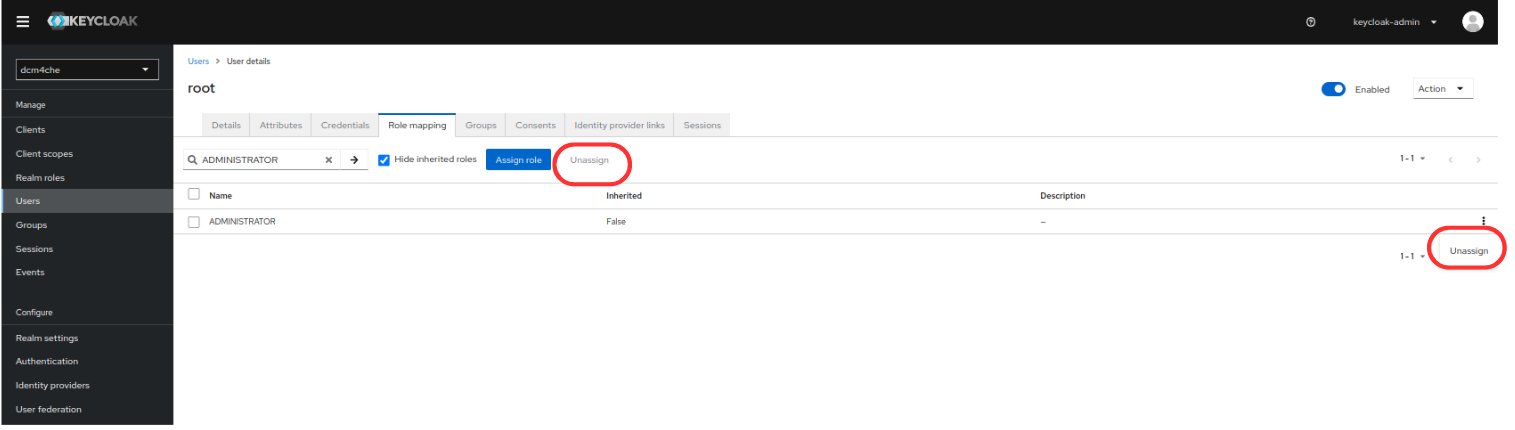
will result in
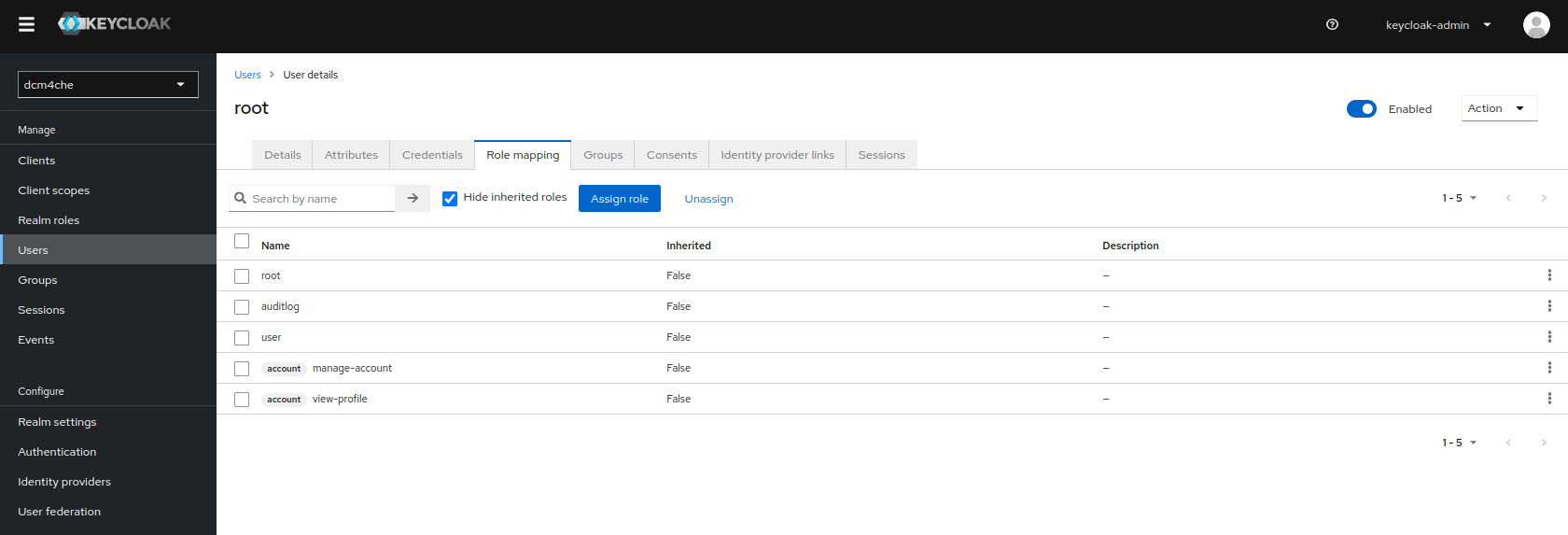
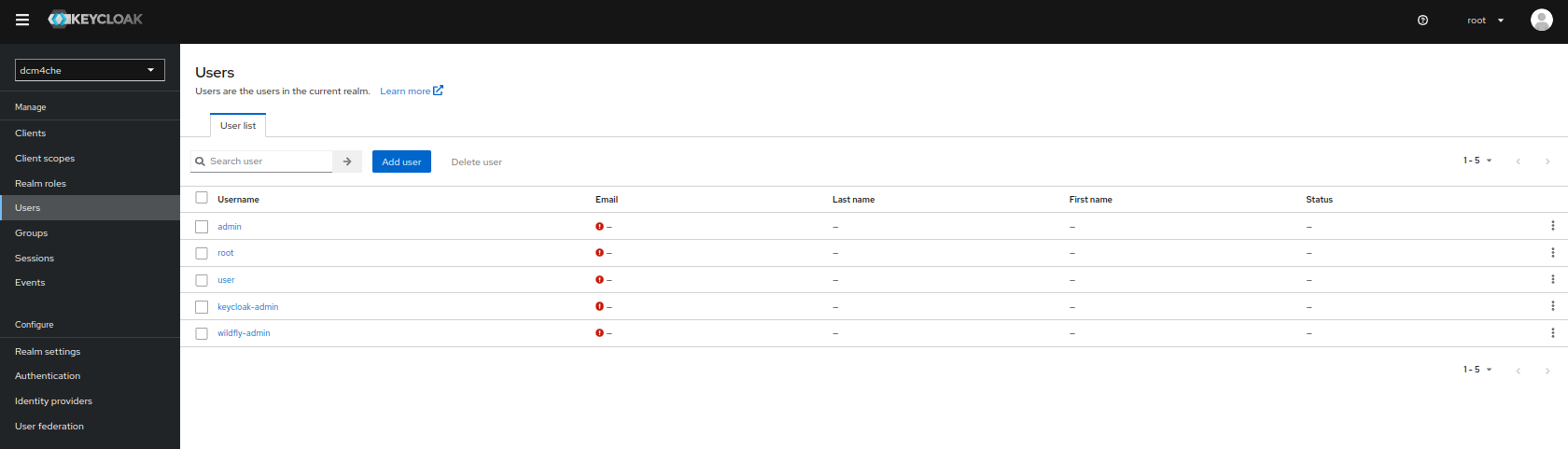
By default, the
Import Usersis turnedONwhich ensures import of LDAP users into Keycloak DB and synced by configured sync policies. Additionally,Sync Registrationsis also turnedONto add new users created by Keycloak in LDAP. Both these settings can be verified by navigating toUser Federation >> Ldapand navigating toSynchronization Settingsin the LdapSettingstab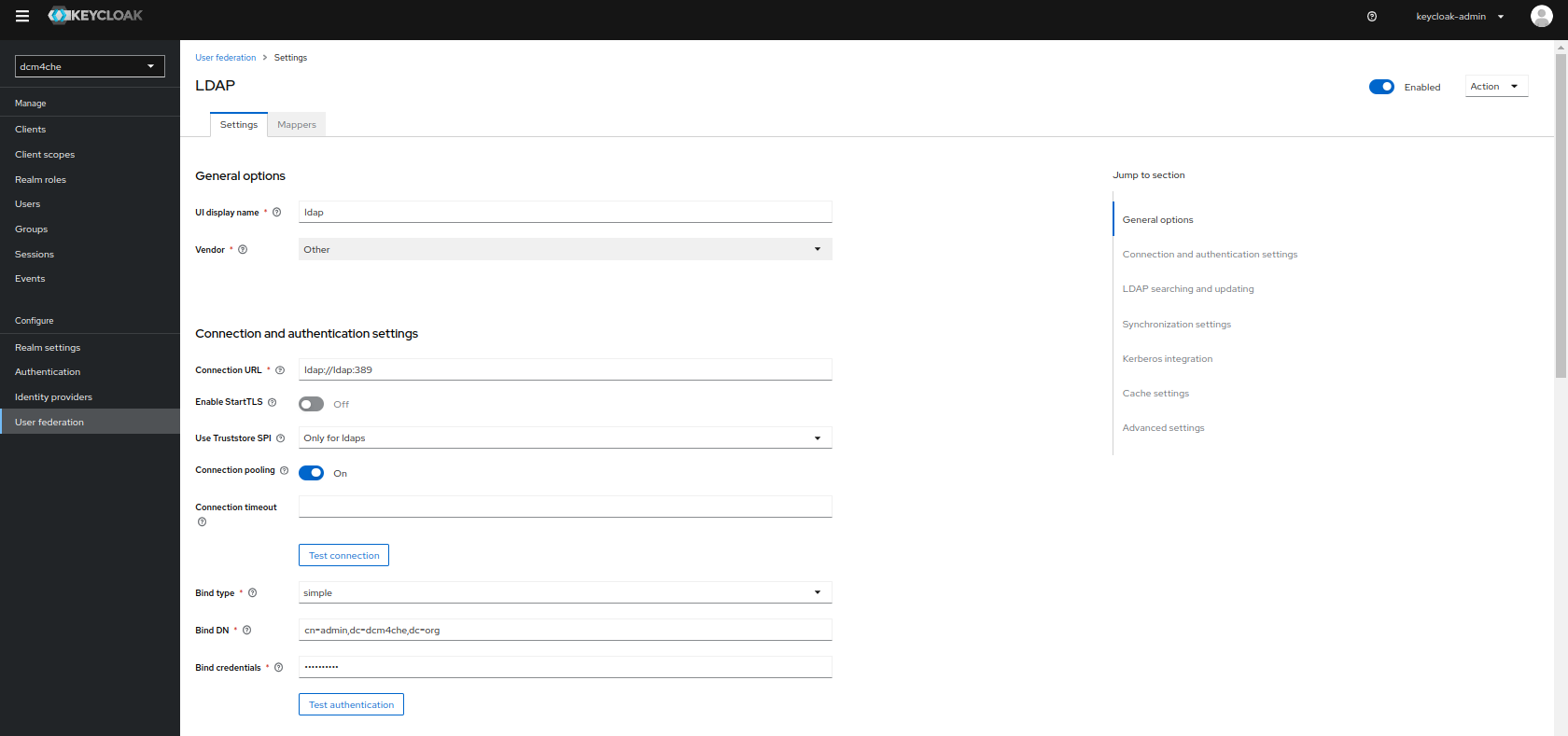
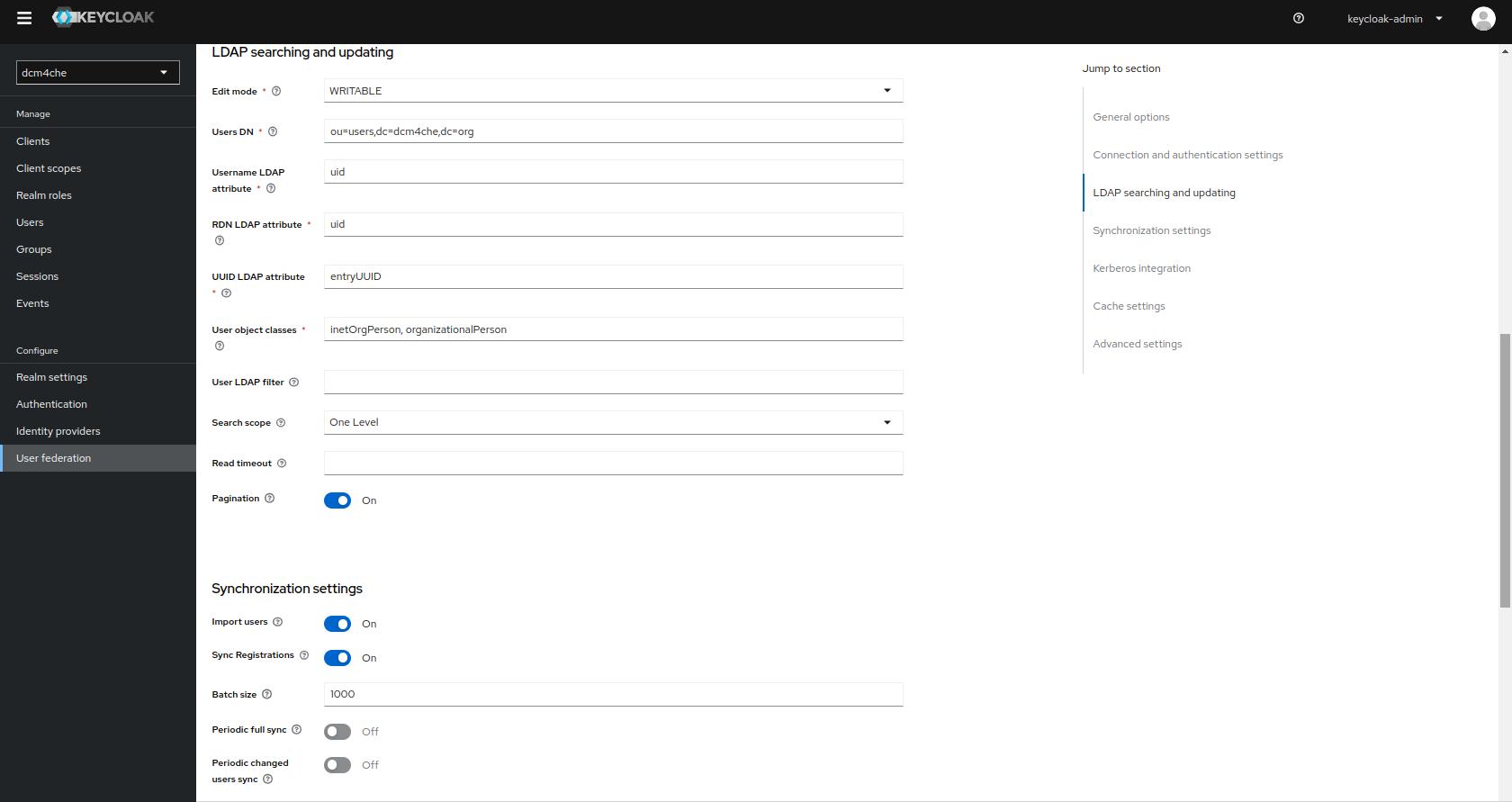
and edit, delete or add new users by navigating to
Users: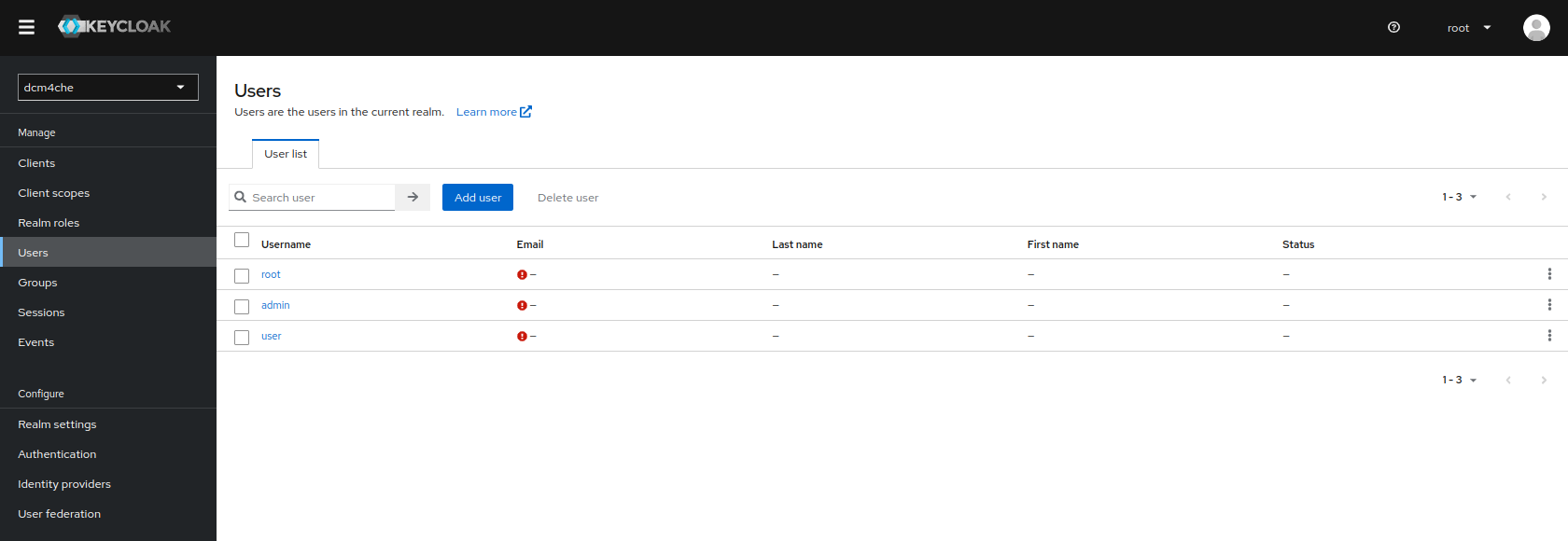
You may add additional Realm Roles associated with particular UI Permission Configuration and assign them to users to grant them the associated UI Permissions. (Users with role
root- or the value specified by environment variable SUPER_USER_ROLE for the Archive container - have access to all UI features, independent of their other roles and configured UI Permissions.) -
-
(Optional) Send CT images to the Archive using dcm4che/dcm4che-tools as described in Run minimum set of archive services on a single host.
-
$ docker stop ldap mariadb keycloak db arcand start all 5 containers again by:
$ docker start ldap mariadb keycloak db arc -
$ docker rm -v ldap mariadb keycloak db arcYou may delete the created bridge network by
$ docker network rm dcm4chee_network
Use Docker Compose
Alternatively to Docker Command Line one may use Docker Compose to take care for starting all 4 containers:
-
version: "3" services: ldap: image: dcm4che/slapd-dcm4chee:2.6.10-34.2 logging: driver: json-file options: max-size: "10m" ports: - "389:389" - "636:636" environment: STORAGE_DIR: /storage/fs1 volumes: - /var/local/dcm4chee-arc/ldap:/var/lib/openldap/openldap-data - /var/local/dcm4chee-arc/slapd.d:/etc/openldap/slapd.d mariadb: image: mariadb:10.11.4 logging: driver: json-file options: max-size: "10m" ports: - "3306:3306" environment: MYSQL_ROOT_PASSWORD: secret MYSQL_DATABASE: keycloak MYSQL_USER: keycloak MYSQL_PASSWORD: keycloak volumes: - /etc/localtime:/etc/localtime:ro - /etc/timezone:/etc/timezone:ro - /var/local/dcm4chee-arc/mysql:/var/lib/mysql keycloak: image: dcm4che/keycloak:26.0.6 logging: driver: json-file options: max-size: "10m" ports: - "8843:8843" environment: KC_HTTPS_PORT: 8843 KC_HOSTNAME: https://<docker-host>:8843 KC_HOSTNAME_BACKCHANNEL_DYNAMIC: 'true' KC_BOOTSTRAP_ADMIN_USERNAME: admin KC_BOOTSTRAP_ADMIN_PASSWORD: changeit KC_DB: mariadb KC_DB_URL_DATABASE: keycloak KC_DB_URL_HOST: mariadb KC_DB_USERNAME: keycloak KC_DB_PASSWORD: keycloak KC_LOG: file ARCHIVE_HOST: <docker-host> KEYCLOAK_WAIT_FOR: ldap:389 mariadb:3306 depends_on: - ldap - mariadb volumes: - /etc/localtime:/etc/localtime:ro - /etc/timezone:/etc/timezone:ro - /var/local/dcm4chee-arc/keycloak:/opt/keycloak/data db: image: dcm4che/postgres-dcm4chee:17.4-34 logging: driver: json-file options: max-size: "10m" ports: - "5432:5432" environment: POSTGRES_DB: pacsdb POSTGRES_USER: pacs POSTGRES_PASSWORD: pacs volumes: - /etc/localtime:/etc/localtime:ro - /etc/timezone:/etc/timezone:ro - /var/local/dcm4chee-arc/db:/var/lib/postgresql/data arc: image: dcm4che/dcm4chee-arc-psql:5.34.2-secure ports: - "8080:8080" - "8443:8443" - "9990:9990" - "9993:9993" - "11112:11112" - "2762:2762" - "2575:2575" - "12575:12575" environment: POSTGRES_DB: pacsdb POSTGRES_USER: pacs POSTGRES_PASSWORD: pacs AUTH_SERVER_URL: https://keycloak:8843 UI_AUTH_SERVER_URL: https://<docker-host>:8843 WILDFLY_CHOWN: /storage WILDFLY_WAIT_FOR: ldap:389 db:5432 keycloak:8843 depends_on: - ldap - keycloak - db volumes: - /etc/localtime:/etc/localtime:ro - /etc/timezone:/etc/timezone:ro - /var/local/dcm4chee-arc/wildfly:/opt/wildfly/standalone - /var/local/dcm4chee-arc/storage:/storage
you have to replace <docker-host> by the hostname of the docker host, which must be resolvable by your DNS server.
See all available environment variables for containers :
Note : If there are difficulties starting the archive service due to
There is insufficient memory for the Java Runtime Environment to continue. Cannot create GC thread. Out of system resources.adding the following option to the
arcservicesecurity_opt: - seccomp:unconfined -
$ docker-compose -p dcm4chee up -d Creating network "dcm4chee_default" with the default driver Creating dcm4chee_ldap_1 ... done Creating dcm4chee_mariadb_1 ... done Creating dcm4chee_db_1 ... done Creating dcm4chee_keycloak_1 ... done Creating dcm4chee_arc_1 ... done
in the directory containing
docker-compose.yml. -
Register the Archive UI as OIDC client in Keycloak as described above.
-
Register the WildFly Administration Console as OIDC client in Keycloak as described above.
-
$ docker-compose -p dcm4chee stop Stopping dcm4chee_arc_1 ... done Stopping dcm4chee_keycloak_1 ... done Stopping dcm4chee_ldap_1 ... done Stopping dcm4chee_mariadb_1 ... done Stopping dcm4chee_db_1 ... done
and start all 5 containers again by:
$ docker-compose -p dcm4chee start Starting ldap ... done Starting mariadb ... done Starting keycloak ... done Starting db ... done Starting arc ... done
-
$ docker-compose -p dcm4chee down Stopping dcm4chee_arc_1 ... done Stopping dcm4chee_keycloak_1 ... done Stopping dcm4chee_ldap_1 ... done Stopping dcm4chee_mariadb_1 ... done Stopping dcm4chee_db_1 ... done Removing dcm4chee_arc_1 ... done Removing dcm4chee_keycloak_1 ... done Removing dcm4chee_ldap_1 ... done Removing dcm4chee_mariadb_1 ... done Removing dcm4chee_db_1 ... done Removing network dcm4chee_network