Get OIDC Access Token using curl - dcm4che/dcm4chee-arc-light GitHub Wiki
Sign in to Keycloak Realm Admin Console with User/Password as root/changeit on
https://<docker-host>:8843/admin/dcm4che/console.
Note :
- Replace
<docker-host>with the hostname of the docker host. - If you changed the default realm name
dcm4cheby environment variable REALM_NAME for Keycloak and Archive Containers, replacedcm4cheby that value in the URL. -
https://<docker-host>:8843/admin/dcm4che/consoleapplies only for Keycloak versions 18.0 and higher and if default KC_HTTP_RELATIVE_PATH is used. - If lower versions of Keycloak are used or if KC_HTTP_RELATIVE_PATH
is set to
/authfor Keycloak v18.0+, then usehttps://<docker-host>:8843/auth/admin/dcm4che/console
-
Create an OIDC client with
curlasClient IDinGeneral Settingssection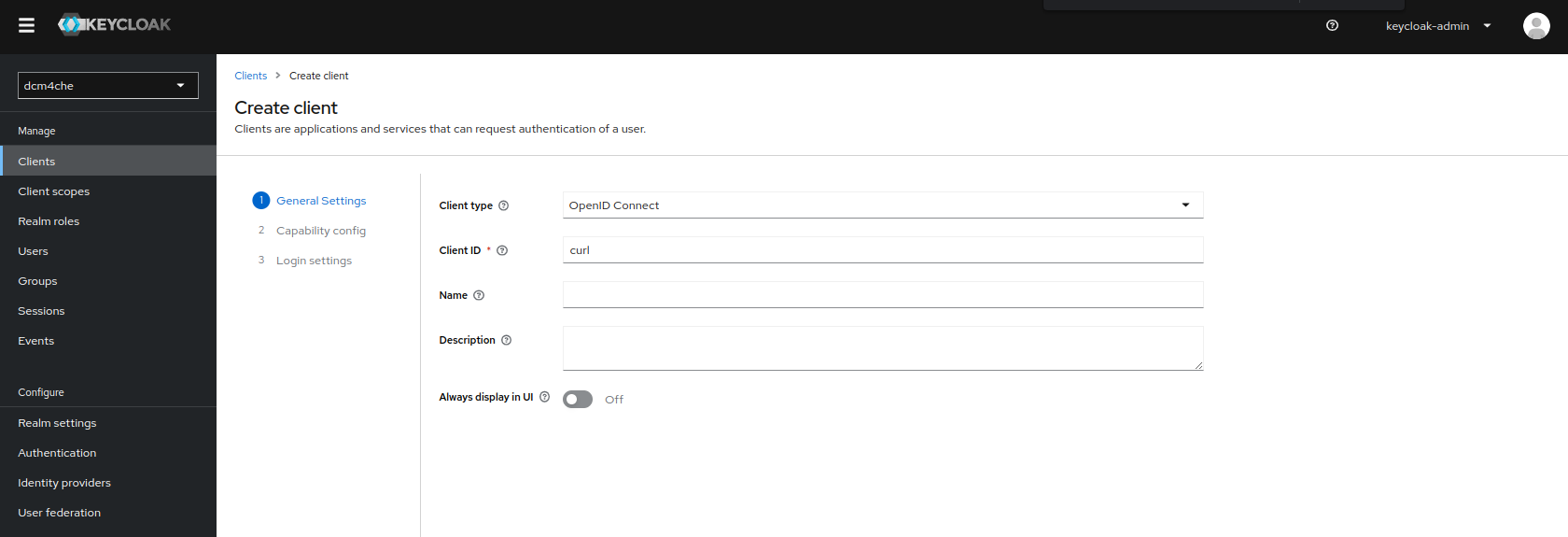
-
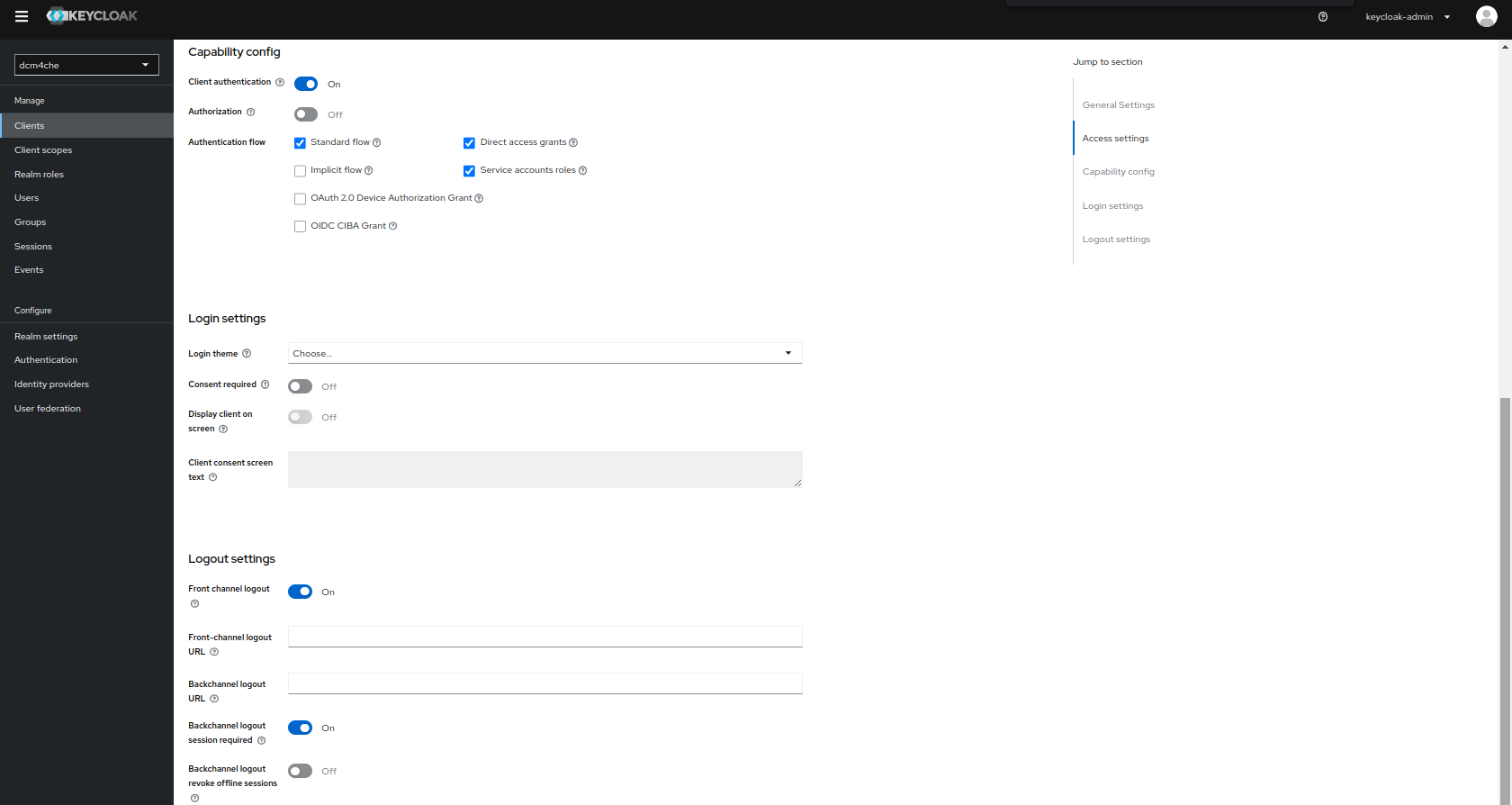
Turn
ONtheClient Authenticationand selectService accounts rolesinAuthentication flowin theCapability Configsection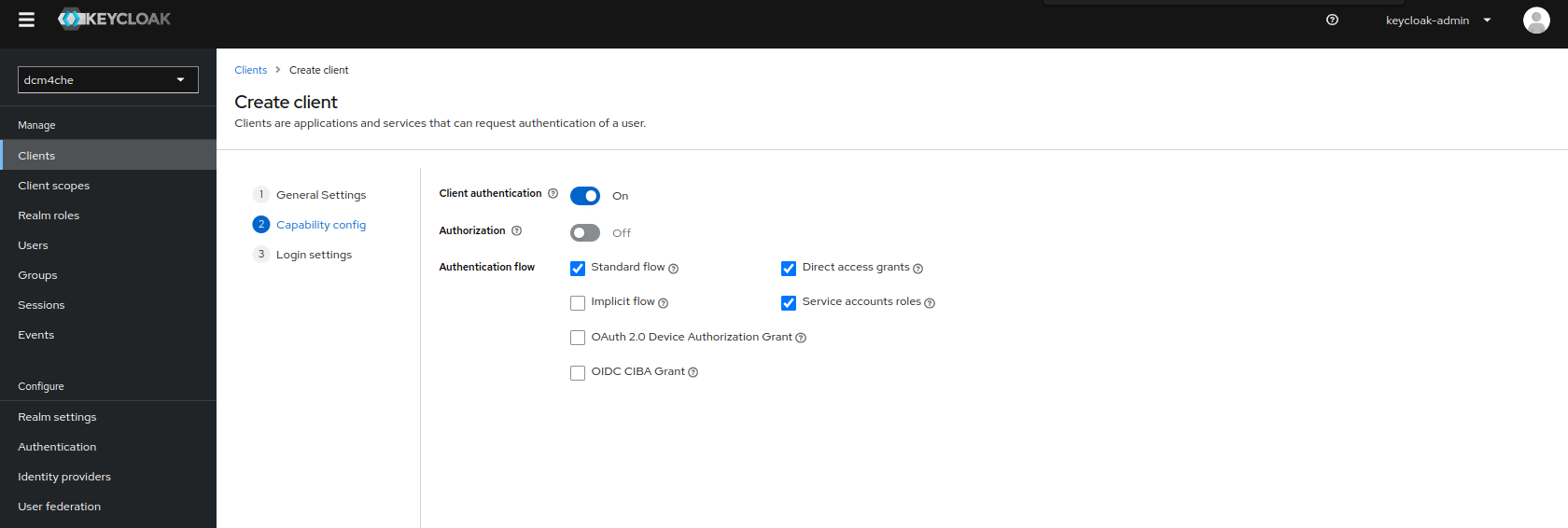
-
Add
/asValid redirect URIsinLogin Settingssection andSave.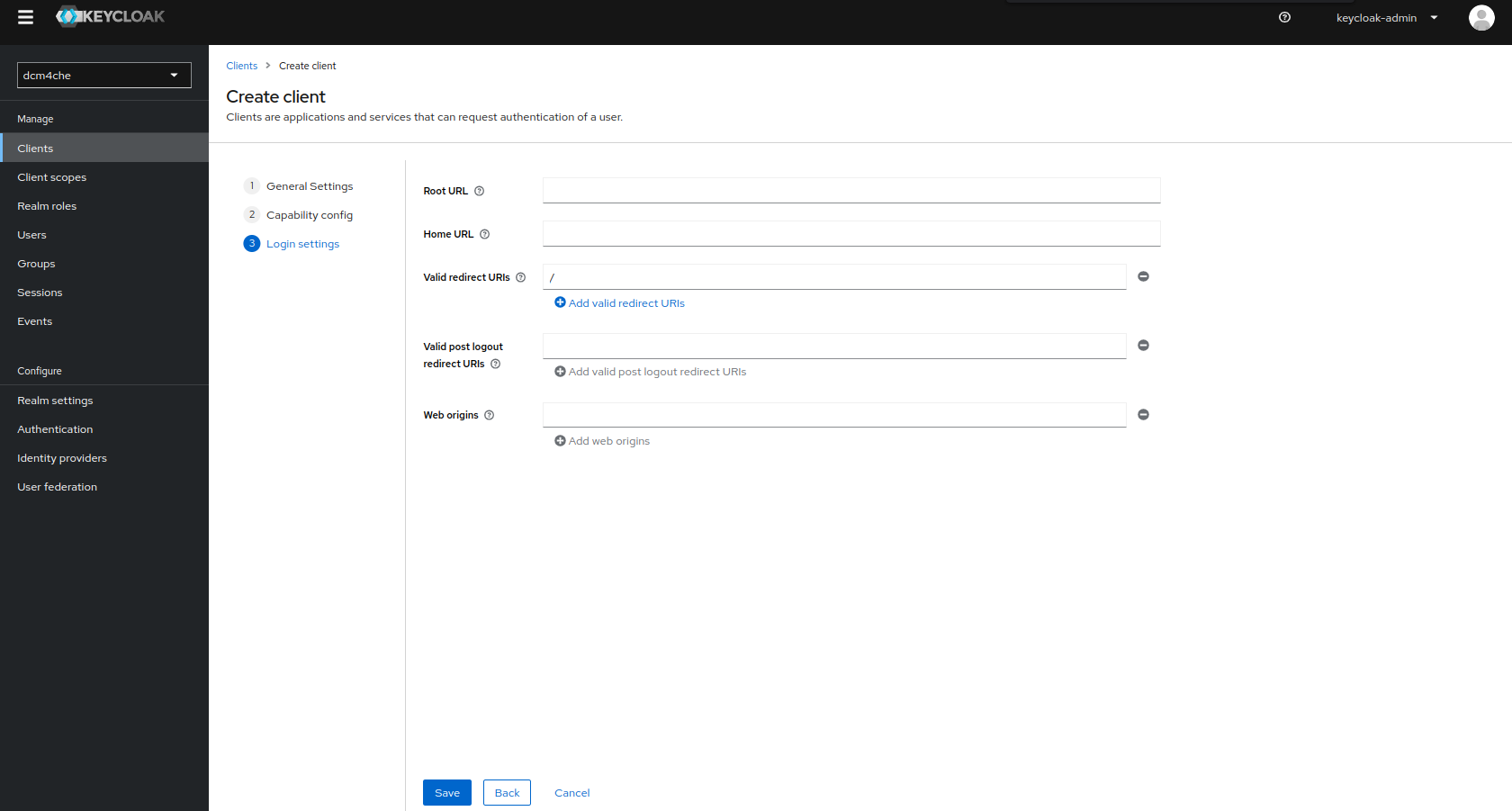
-
The saved settings can be viewed as
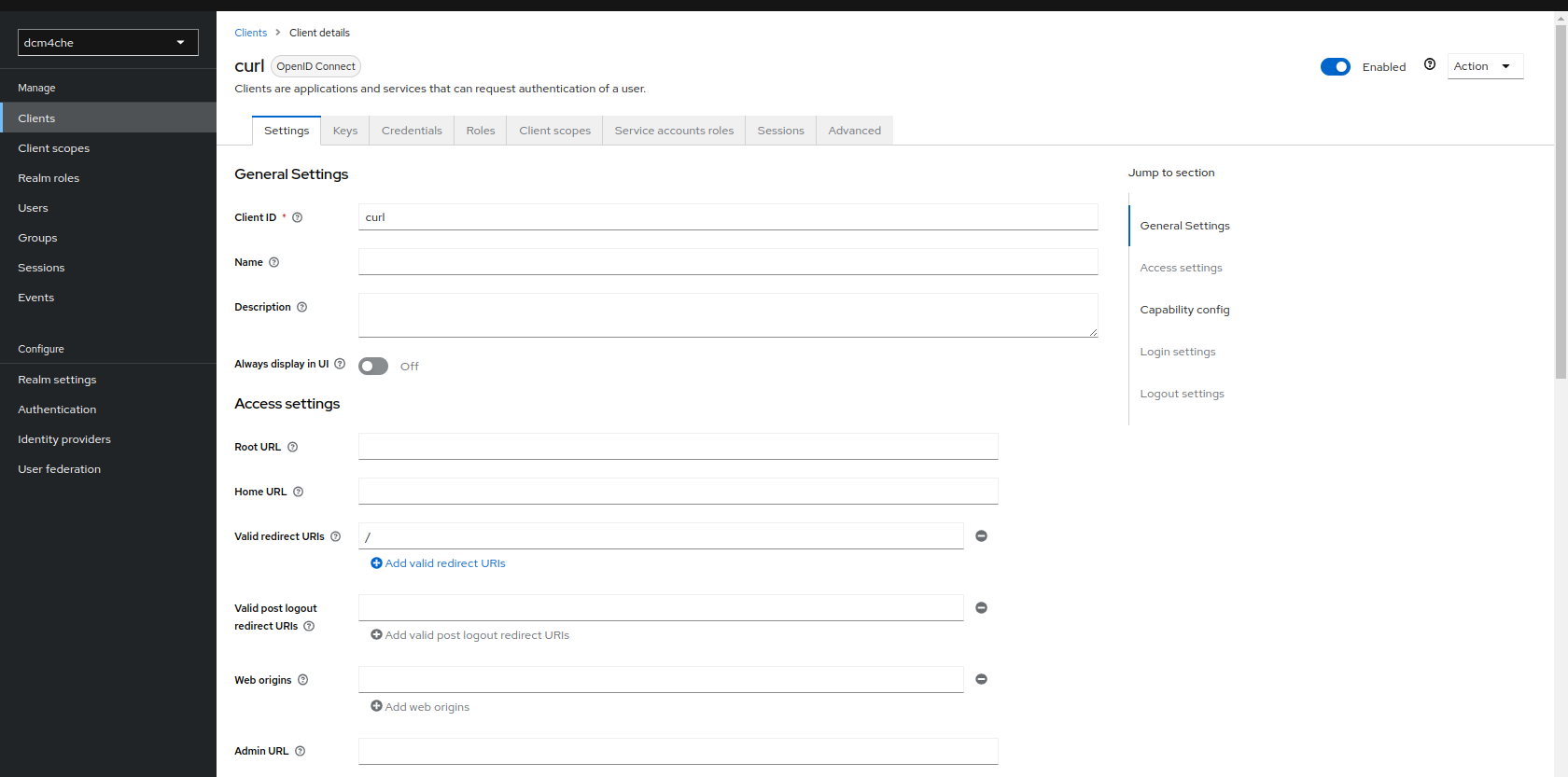
-
Add the Role
userin theService account rolestab, useAssign roleto assignuserrole to this client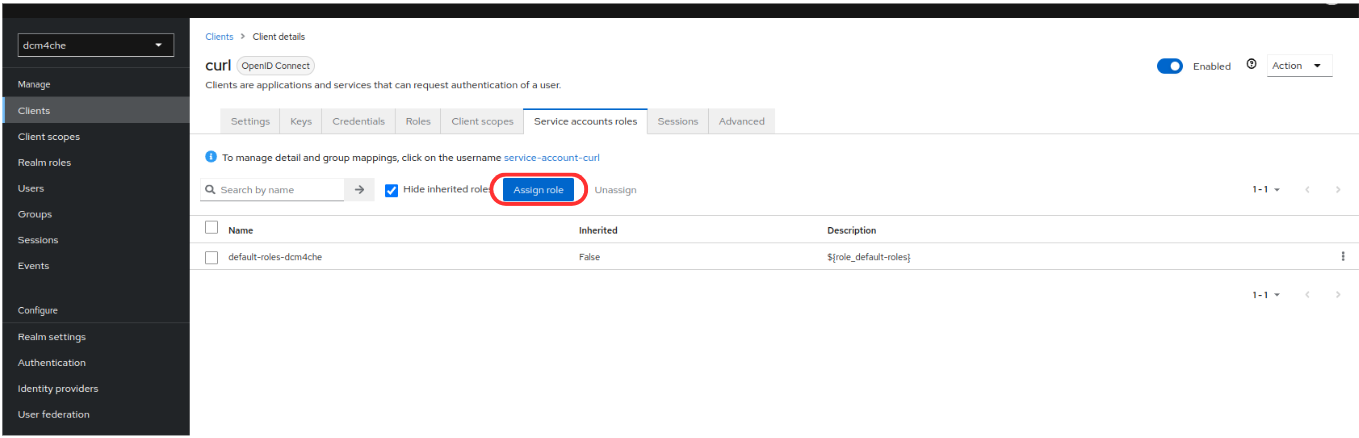
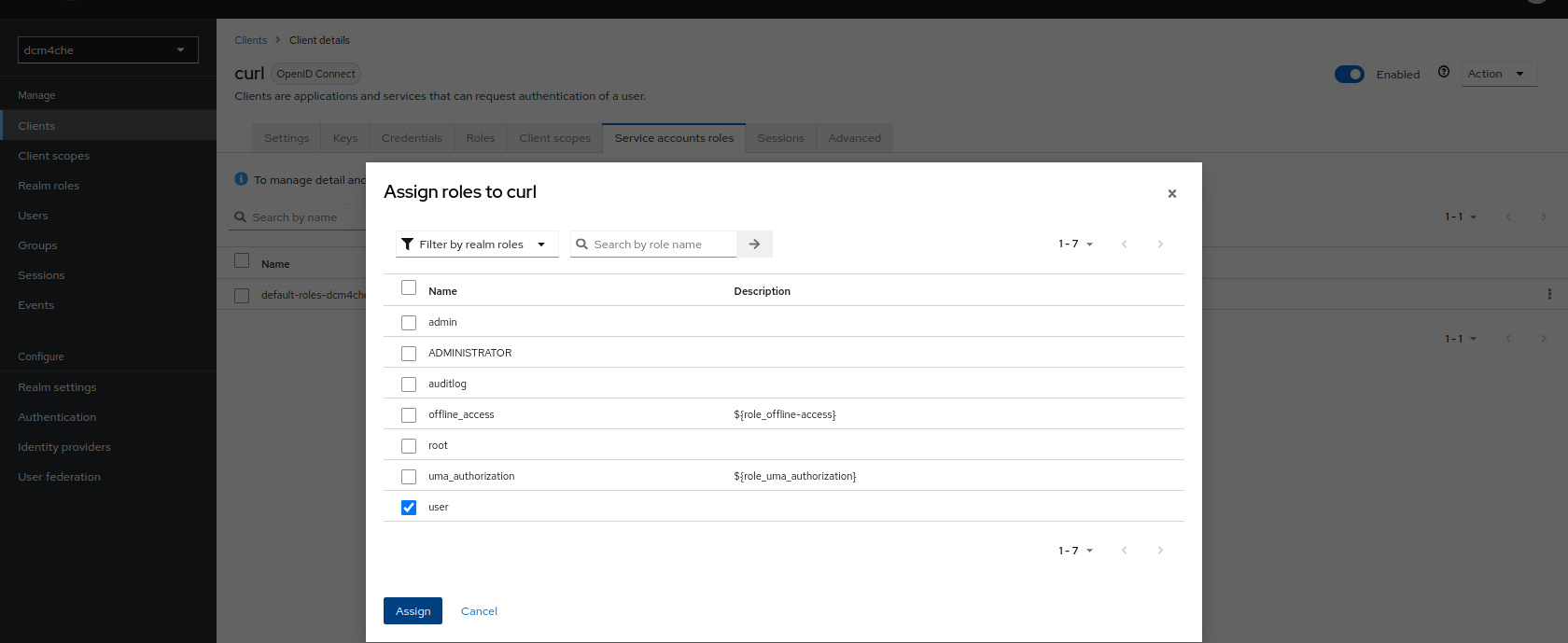
-
Store the
Secretfrom theCredentialstab, for later use.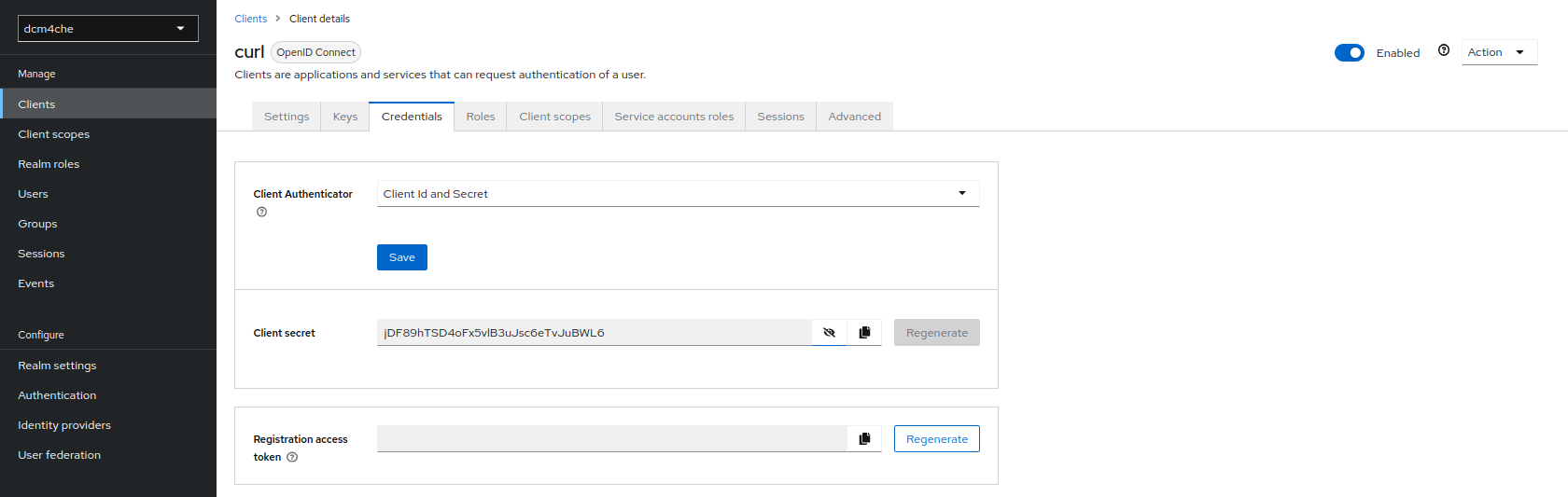
Request an access token using OAuth 2.0 Client Credentials Grant
Replace <docker-host> below with the hostname of the docker host.
$ RESULT=`curl -k --data "grant_type=client_credentials&client_id=curl&client_secret=jDF89hTSD4oFx5vlB3uJsc6eTvJuBWL6" https://<docker-host>:8843/realms/dcm4che/protocol/openid-connect/token`
$ echo $RESULT | python -m json.tool
{
"access_token": "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJFZE5pZGhoRFIzMnZfZVJTSnhHVjZUbWlUMU85Wjd1bWw3cjFleEJ2Y1kwIn0.eyJleHAiOjE2ODE0ODA1MjUsImlhdCI6MTY4MTQ4MDIyNSwianRpIjoiMGNmZGQwYjUtODhmOC00MTg4LWI3NjMtYjYyNWFiZTBjNmI4IiwiaXNzIjoiaHR0cHM6Ly92cmluZGEtcGM6ODg0My9yZWFsbXMvZGNtNGNoZSIsInN1YiI6IjI0Yzc4ZTlkLTM2YzMtNDlhMS1iZjVkLTE4MGU3ZmUzN2YzMiIsInR5cCI6IkJlYXJlciIsImF6cCI6ImN1cmwiLCJhY3IiOiIxIiwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbIm9mZmxpbmVfYWNjZXNzIiwiZGVmYXVsdC1yb2xlcy1kY200Y2hlIiwidW1hX2F1dGhvcml6YXRpb24iLCJ1c2VyIl19LCJzY29wZSI6InByb2ZpbGUgZW1haWwiLCJjbGllbnRIb3N0IjoiMTkyLjE2OC4yLjIyMyIsImVtYWlsX3ZlcmlmaWVkIjpmYWxzZSwiY2xpZW50SWQiOiJjdXJsIiwicHJlZmVycmVkX3VzZXJuYW1lIjoic2VydmljZS1hY2NvdW50LWN1cmwiLCJjbGllbnRBZGRyZXNzIjoiMTkyLjE2OC4yLjIyMyJ9.Sb-XbdGAXyUIZW4rgW1b9l7rLv5t2k_2DYohCJy7GkcuQdI6U20qykATxyDtSFDAiWCqBBeUsOE_LXSowOnMwliPnuNXndvJv8iMbWJYztPNRPPPTB4cqKW50fti7v5vfHrqqH3asbrIIy-irN7DYgAOEsrYGVntiq9f8RIJ1TAL-2QRwzIN5u14WennXfHPjLD92HWShs7-CeR5h4XInQUf0rl-Qm50H-mFHpzb861h0LEq45sq697amc0oJr0tTwBitUnLGeWynX9Wzgx_gDy9mpwrVZSGfZEV6oBL5s4E7ymc477kZOHyQ51-zw_zoEMVJW96MjZQj9MsFgl04A",
"expires_in": 300,
"not-before-policy": 0,
"refresh_expires_in": 0,
"scope": "profile email",
"token_type": "Bearer"
}Note :
-
https://<docker-host>:8843/realms/dcm4che/protocol/openid-connect/tokenapplies only for Keycloak v18.0+ and if default KC_HTTP_RELATIVE_PATH is used. - If lower versions of Keycloak are used or if KC_HTTP_RELATIVE_PATH
is set to
/authfor Keycloak v18.0+, thenhttps://<docker-host>:8843/auth/realms/dcm4che/protocol/openid-connect/token
Replace <docker-host> below with the hostname of the docker host.
$ TOKEN=`echo $RESULT | sed 's/.*access_token":"\([^"]*\).*/\1/'`
$ curl -H "Authorization: Bearer $TOKEN" http://<docker-host>:8080/dcm4chee-arc/aets/DCM4CHEE/rs/studies/count
{"count":0}Inspect the included JSON Web Token (JWT)
$ JWT=`echo $RESULT | sed 's/[^.]*.\([^.]*\).*/\1/'`
$ echo $JWT | base64 -d | python -m json.tool
base64: invalid input
{
"acr": "1",
"azp": "curl",
"clientAddress": "192.168.2.223",
"clientHost": "192.168.2.223",
"clientId": "curl",
"email_verified": false,
"exp": 1681480525,
"iat": 1681480225,
"iss": "https://<docker-host>:8843/realms/dcm4che",
"jti": "0cfdd0b5-88f8-4188-b763-b625abe0c6b8",
"preferred_username": "service-account-curl",
"realm_access": {
"roles": [
"offline_access",
"default-roles-dcm4che",
"uma_authorization",
"user"
]
},
"scope": "profile email",
"sub": "24c78e9d-36c3-49a1-bf5d-180e7fe37f32",
"typ": "Bearer"
}<docker-host> returned above shall be the hostname of the docker host.