Deployment guide for GCC - OfficeDev/microsoft-teams-apps-icebreaker GitHub Wiki
How to choose the deployment procedure appropriate for your configuration?
Note : This guide is intended for customers requiring the deployment of Icebreaker of Office 365 Government Community Cloud (aka GCC) only - The standard deployment for Azure AD Commercial tenant is located here
Microsoft provides different cloud offering across Office 365, Azure or the Power Platform to meet customers compliance and regulation requirements. While the global Office 365 and Azure flavors, referred as “Commercial” cloud, are the default and most used environments, customers can choose other alternatives that we’ll refer as Microsoft Cloud for Government.
Microsoft Cloud for Government provides a comprehensive cloud platform designed expressly for U.S. Federal, State, and Local Governments to meet the U.S. Government’s thorough security and compliance regulations. Microsoft Cloud for Government meets the standards of many government agencies, including FedRAMP, HIPAA, and CJIS, to name a few.
Depending on the cloud offerings that are used, there are differences to consider in terms of service availability and URLs to access and manage those services. Here is a global representation of these different configuration across Office 365, Azure and Power Platform for Commercial and US Gov cloud offerings.
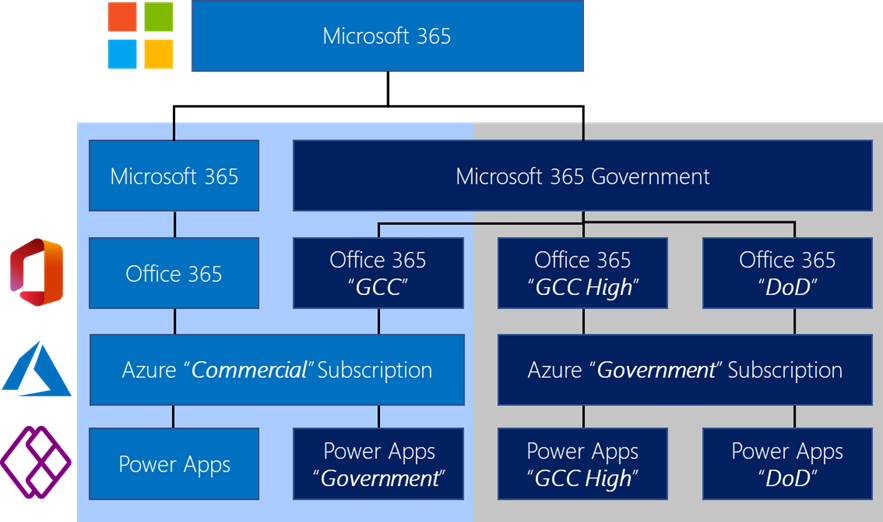
If you need more information on these offerings for US Sovereign Cloud, please refer to the following article - https://aka.ms/AA632wo
Here are the tests to run to identify you current GCC setup :
Check 1 - Identify your Office 365 configuration.
- From a web browser, go to https://gettenantpartitionweb.azurewebsites.net/
- Enter the name of your Azure AD tenant – e.g. contoso.onmicrosoft.com.
- Press “Lookup tenant” and check the results.
| Lookup Results | Mapping |
|---|---|
| Azure AD Instance: Azure AD Global, Tenant Scope: Not applicable | O365 Commercial |
| Azure AD Instance: Azure AD Global, Tenant Scope: GCC (Moderate) | O365 GCC |
| Azure AD Instance: Azure AD Government, Tenant Scope: GCC High | O365 GCC-H |
Save this value as the result for Check 1
Check 2a - Identify your Azure configuration (for templates based on Azure resources only)
There are only two options here based on the URL used to access the Azure portal and deploy your resources.
| Azure portal URL | Mapping |
|---|---|
| https://portal.azure.com | Azure Commercial |
| https://portal.azure.us | Azure Government |
Save this value as the result for Check 2a
More info on Azure services and URL patterns for Commercial vs Gov clouds
Compare Azure Government and global Azure - Azure Government | Microsoft Docs
Check 2b - Identify your Power Platform configuration (for templates based on Power Platform only)
Here are the URL patterns for Power Platform to determine the cloud environment.
| Power App portal URL | Mapping |
|---|---|
| https://*.powerapps.com | Power App Commercial |
| https://*.gov.powerapps.us | Power App GCC |
| https://*.high.powerapps.us | Power App GCC-H |
| Not supported | Power App DoD |
Save this value as the result for Check 2b
More info on Power Platform services and URL patterns for Commercial vs Gov clouds
Microsoft Power Apps US Government - Power Platform | Microsoft Docs
Check 3 - Are you running in multi or single-tenancy mode (for templates based on Azure resources only)?
This question is to determine if your Azure subscription is linked to the same Azure AD as the one where your Office 365 users are deployed.
If you use the same domain to access the Azure portal than your O365 services, the answer is single-tenancy. e.g. you use your O365 credentials to access the Azure portal.
Otherwise, the answer is multi-tenancy. e.g. you have different email addresses or use different Azure AD to access O365 and the Azure.
Based on these different checks, you can determine your configuration and which deployment model to use.
Save this value as the result for Check 3
Your Microsoft Teams app templates is based on Azure resources.
| Check 1 | Check 2a | Check 3 | Supported | Deployment scenario |
|---|---|---|---|---|
| O365 Commercial | Azure Commercial | Single | Yes | Standard |
| O365 Commercial | Azure Commercial | Multi | Yes | Standard (1) |
| O365 GCC | Azure Commercial | Single | Yes | Standard (2) |
| O365 GCC | Azure Commercial | Multi | Yes | Standard (1) (2) |
| O365 GCC | Azure Government | Single | Not Supported | Not Available (3) |
| O365 GCC | Azure Government | Multi | Yes | Hybrid |
| O365 GCC-H/DoD | Any | Any | Not Supported | Not Available (4) |
(1) Use the standard deployment procedure – Pay attention to the tenantID provided in the input parameters of the ARM template: you should change the default value (the Azure AD linked to your Azure subscription) to the Azure AD tenantID where your O365 users and services are located.
(2) Use the standard deployment procedure – Microsoft Teams admin portal for GCC now supports “Manage Apps” as well as “App setup policies” – Also, Teams for GCC now supports “Message Extensions” so there is nothing specific to do to deploy on O365 GCC compared to O365 Commercial with Azure Commercial.
(3) By design, O365 GCC and Azure Gov are connected to different Azure AD tenants – It’s not possible to be in a single tenant configuration with this setup.
(4) Most the Microsoft App templates rely on the Azure Bot Service to enable bot / Message Extensions in Teams. Microsoft Teams channel is not yet enabled for Azure Bot Service on Azure Government.
Before deploying a Teams app template to your Azure Government subscription, make sure that all the required services and pre-requisites are met. This means that the list of required Azure services are available and registered on the targeted region. This page explains how to verify that a resource provider is available and how to register it for your subscription -
Resource providers and resource types - Azure Resource Manager | Microsoft Docs
Your Microsoft Teams app templates is based on Power Platform.
| Check 1 | Check 2b | Supported | Deployment scenario |
|---|---|---|---|
| O365 Commercial | Power Platform Commercial | Yes | Standard |
| O365 GCC | Power Platform GCC | Yes | Standard (5) (6) |
| O365 GCC-H | Power Platform GCC-H | Yes | Standard (5) (6) |
| O365 DoD | Power Platform DoD | Not Supported | Not Available (7) |
(5) Use the standard deployment procedure – Depending on the pre-requisites and services used on the Power Platform, some Teams app template may not be available for O365 GCC/GCC-H. A complete list of O365 and Power Platform services available on Office 365 Gov and service plan is available here -
Office 365 US Government - Service Descriptions | Microsoft Docs
(6) For Teams app templates that require Dataverse for Teams in GCC/GCC-H, you will need an additional stand-alone license for Power Apps. This is a current limit.
(7) Power Platform is not available on O365 DoD and is therefore out of scope.
What is “hybrid deployment”?
In this setup, the Office 365 users and Microsoft Teams service are hosted in a different Azure AD tenant as the Azure resources. Also, both O365 and Azure use a Government Cloud:
- Office 365 with a GCC Azure AD tenant
- Azure Government (https://portal.azure.us) associated to its GCC-H Azure AD tenant
To register a bot as an application in Microsoft Teams, the bot needs to be registered on the Azure Bot Service. This Azure Bot Service also needs to be deployed on an Azure subscription that is linked to the Azure AD tenant where your O365 users and Microsoft Teams service are. This is what we call the hybrid deployment.
Here is a high-level representation for the hybrid deployment.
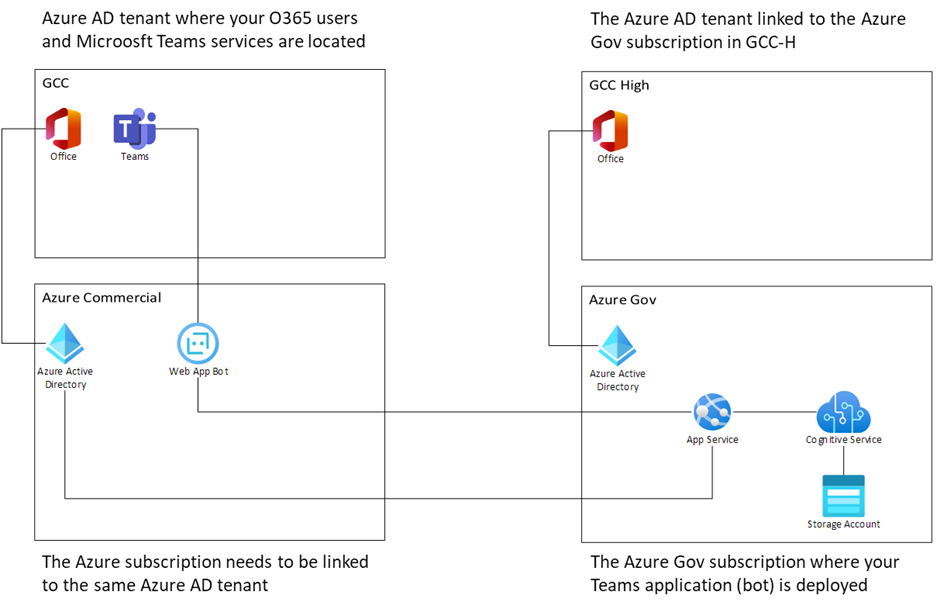
The hybrid deployment guide considers these multiple Azure subscriptions and Azure AD tenant. It also details the sequence and order of deployment of these resources.
Note : Azure Bot Service is only here to register your application as a bot in your Microsoft Teams environment. It is also used to activate SSO when needed, using the same Azure AD tenant where your O365 users are. There is no conversation data or attachments that transit via the Azure Bot Service deployed on Azure Commercial: all communications are in direct transit (https) between your Microsoft Teams service in GCC and the application bot hosted on Azure Government.
Deployment in O365 GCC tenant and Azure Commercial subscription
For O365 GCC deployment and Azure Commercial, the same deployment guide (available on Icebreaker GitHub repo) can be followed. Use O365 GCC tenant for App registration (Step 1 in deployment guide) and Azure commercial subscription for ARM deployment (Step 2 in deployment guide). Make sure tenant Id of O365 GCC tenant is added during ARM deployment.
Deployment in O365 GCC tenant and Azure Government subscription
For hybrid deployment, follow these deployment guide steps.
Prerequisites
To begin, you will need:
- An Azure Government subscription where you can create the following resources:
- Azure Logic App
- App Service
- App Service plan
- Azure Cosmos DB account
- Application Insights
- An Azure Commercial subscription where you can create the following resources:
- Bot Channels Registration
- A copy of the Icebreaker app GitHub repo
Deployment Steps
Step 1. Register Microsoft Azure AD application
Register one Azure AD application in directory where the Team's users are homed (Office 365 GCC + Azure Commercial): for the bot and tab app authentication.
-
Log in to the Azure Portal for your subscription, and go to the “App registrations” blade here. Verify that you are on the same Azure AD tenant than your O365 users and where Microsoft Teams is deployed.
-
Click on "New registration", and create an Azure AD application.
-
Name: The name of your Teams app - if you are following the template for a default deployment, we recommend "Icebreaker".
-
Supported account types: Select "Accounts in any organizational directory"
-
Leave the "Redirect URI" field blank.

-
Click on the "Register" button.
-
When the app is registered, you'll be taken to the app's "Overview" page. Copy the Application (client) ID, Directory(tenant) ID. we will need it later. Verify that the "Supported account types" is set to Multiple organizations.

- On the side rail in the Manage section, navigate to the "Certificates & secrets" section. In the Client secrets section, click on "+ New client secret". Add a description for the secret and select an expiry time. Click "Add".

- Once the client secret is created, copy its Value; we will need it later.
At this point you have 2 unique values:
- Application (client) ID
- Client secret
Step 2: Deploy bots to your Azure Commercial subscription
- Click on the "Deploy to Azure" button below.
-
When prompted, log in to your Azure Commercial subscription.
-
Azure will create a "Custom deployment" based on the ARM template and ask you to fill in the template parameters.
-
Select a subscription and resource group.
- We recommend creating a new Resource group.
- The Resource group location MUST be in a datacenter that supports Application Insights.
-
Enter a "Base Resource Name", which the template uses to generate names for the other resources.
- Note the base resource name that you selected. We will need it later.
-
Fill in the various IDs in the template:
- Bot Client ID: The application (client) ID registered in Step 1.
- Bot App Password: The client secret from the Azure AD application registered in Step 1.
Make sure that the values are copied as-is, with no extra spaces. The template checks that GUIDs are exactly 36 characters.
-
If you wish to change the app name, description, and icon from the defaults, modify the corresponding template parameters.
-
Click on "Review + create" to start the deployment. It will validate the parameters provided in the template. Once the validation is passed, click on "Create" to start the deployment.
-
Wait for the deployment to finish. You can check the progress of the deployment from the "Notifications" pane of the Azure Portal.
-
Click on Bot Service created by ARM template. Name of Bot Service will be base resource name which was provided earlier.
-
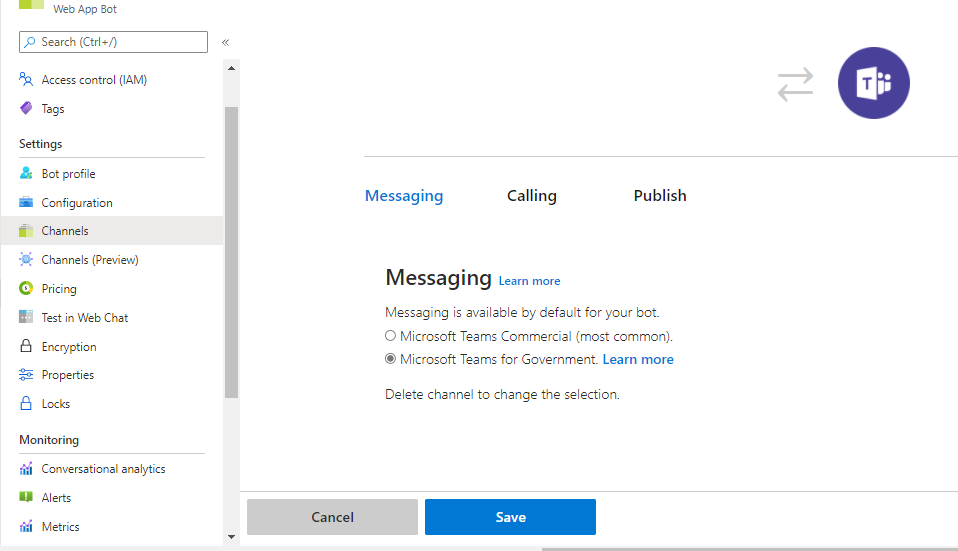
Click on Channels in Settings section of Bot Services and click on "Edit" button for Microsoft Teams Channel. Click on Delete Channel.
-
Once deleted, click on "Configure Microsoft Teams Channel" icon inside "Add a featured Channel". Select "Microsoft Teams for Government" and click on Save.
Step 3. Deploy remaining resources to your Azure Government subscription
- Click on the "Deploy to Azure" button below.
-
When prompted, log in to your Azure Government subscription.
-
Azure will create a "Custom deployment" based on the ARM template and ask you to fill in the template parameters.]
-
Select a subscription and a resource group.
- We recommend creating a new resource group.
- The resource group location MUST be in a datacenter that supports all the following:
- Azure Logic App
- App Service
- App Service plan
- Azure Cosmos DB account
- Application Insights
For an up-to-date list of datacenters that support the above, click here
-
Fill in the various IDs in the template:
-
AppName : Enter and reuse the same Base Resource Name, that you gave for bots deployment in your Azure commercial.
-
Bot App ID: The Application (client) ID from the Azure AD application created above
-
Bot App Password: The client secret from the Azure AD application created above
-
Tenant ID : The tenant ID registered in Step 1. If your Microsoft Teams tenant is same as Azure subscription tenant, then we would recommend to keep the default values.
-
Bot App Insights Key: Navigate to App Insights of bot deployed in Azure Commercial. Under left menu, select Properties under Configure. Copy the instrumentation key.
-
Make sure that the values are copied as-is, with no extra spaces. The template checks that the GUID is exactly 36 characters.
-
If you wish to change default values, modify the corresponding template parameters.
-
Click on "Review + create" to start the deployment. It will validate the parameters provided in the template. Once the validation is passed, click on create to start the deployment.
-
Once completed, navigate to the App Service you have created (it should be of type Microsoft.Web/sites with a name similar to "icebreaker-XXXXXXXXXXXXX"). Copy its URL; we will need it later. It should be similar to "https://icebreaker-XXXXXXXXXXXXX.azurewebsites.net" where the X's are the hash.

Step 4. Create the Teams app package
-
Open the
Manifest\manifest.jsonfile in a text editor. -
Change the placeholder fields in the manifest to values appropriate for your organization.
-
developer.name(What's this?) -
developer.websiteUrl -
developer.privacyUrl -
developer.termsOfUseUrl
-
Change the “botId” placeholder to your Azure AD application's ID from above. This is the same GUID that you entered in the template under “Bot App ID”.
-
In the "validDomains" section, replace the placeholder with your App Service's domain. This is your App Service's URL you copied above WITHOUT the "https://" e.g. "icebreaker-XXXXXXXXXXXXX.azurewebsites.net".
-
Create a ZIP package with
manifest.json,color.png, andoutline.png. The two image files are the icons for your app in Teams.
- Make sure that the 3 files are the top level of the ZIP package, with no nested folders.

Step 5. Run the app in Microsoft Teams
- If your tenant has sideloading apps enabled, you can install your app to a team by following the instructions below.
-
Upload package to a team using the Apps tab: https://docs.microsoft.com/en-us/microsoftteams/platform/concepts/apps/apps-upload#upload-your-package-into-a-team-using-the-apps-tab
-
Upload package to a team using the Store: https://docs.microsoft.com/en-us/microsoftteams/platform/concepts/apps/apps-upload#upload-your-package-into-a-team-or-conversation-using-the-store
- You can also upload it to your tenant's app catalog, so that it can be available for everyone in your tenant to install: https://docs.microsoft.com/en-us/microsoftteams/tenant-apps-catalog-teams
Troubleshooting
Please see our Troubleshooting page.