40.Data Security - yojulab/learn_networks GitHub Wiki
Computer security
What is the CIA triad (confidentiality, integrity and availability)?

Confidentiality, Integrity, Availability
Beyond CIA : Cyptography, Protocol Security, MAC(Media Access Control)
Error Detection Tech
BEC : Parity Checking, Check Sum Checking
FEC : Hamming code
Encryption and Decryption
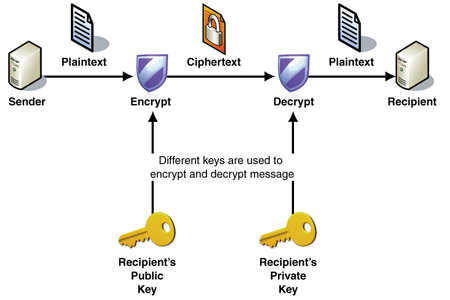
Types of Cryptography
- Symmetric cryptography [private key] : 대칭형, 공통키 - DES(Data Encryption Standard)
- Asymmetric cryptography [public key] : 비대칭형, 공개키, RSA (Rivest–Shamir–Adleman)
Encryption Methods
- Substitution Cipher, Transposition Cipher, Product Cipher, Algebraic Cipher