aws diagrfms, security, prices, route tables, gwlb, inspection - yar145/mytestrepo1 GitHub Wiki
0.05 per Site-to-Site VPN connection per hour
Data transfer out on AWS Site-to-Site VPN incurs data transfer out charges that are explained in the EC2 on-demand pricing page. Data Transfer
Data Transfer OUT From Amazon EC2 To Internet AWS customers receive** 100GB of data transfer out to the internet free each month, aggregated across all AWS Services and Regions (except China and GovCloud). The 100 GB free tier for data transfer out to the internet is global and does not apply separately or individually to AWS Regions. First 10 TB / Month .09 per GB**
Data Transfer OUT From Amazon EC2 To Europe (Ireland) .02 per GB
Data Transfer within the same AWS Region Data transferred "in" to and "out" from Amazon EC2, Amazon RDS, Amazon Redshift, Amazon DynamoDB Accelerator (DAX), and Amazon ElastiCache instances, Elastic Network Interfaces or VPC Peering connections across Availability Zones in the same AWS Region is charged at .01/GB in each direction. IPv4: Data transferred “in” to and “out” from public or Elastic IPv4 address is charged at .01/GB in each direction. IPv6: Data transferred “in” to and “out” from an IPv6 address in a different VPC is charged at .01/GB in each direction.
Data transferred between Amazon EC2, Amazon RDS, Amazon Redshift, Amazon ElastiCache instances, and Elastic Network Interfaces in the same Availability Zone is free.
Pricing examples Pricing example 1: Site-to-Site VPN
You create an AWS Site-to-Site VPN connection to your Amazon VPC in US East (Ohio). The connection is active for 30 days, 24 hours a day. You transfer 1,000 GB in and transfer 500 GB out through this connection.
AWS Site-to-Site VPN connection fee: There is an hourly fee for AWS Site-to-Site VPN, while connections are active. For the US East (Ohio) Region, the fee is $0.05 per hour. You pay $36.00 per month in connection fees. Data transfer out fee: The first 100 GB are free, so you pay for 400 GB at $0.09 per GB. You pay $36.00 per month in data transfer out fees. You pay $72.00 per month for AWS Site-to-Site VPN.
Pricing example 2: Accelerated Site-to-Site VPN
You create an Accelerated Site-to-Site VPN connection from your Amazon VPC in US East (Ohio) to a remote site in Europe. The connection is active for 30 days, 24 hours a day. You transfer 1,000 GB in and 500 GB out through that connection.
Accelerated Site-to-Site VPN connection fee: There is an hourly fee for Accelerated Site-to-Site VPN, while connections are active. For the US East (Ohio) Region, the fee is $0.05 per hour. You pay $36.00 per month in connection fees. Data transfer out fee: The first 100 GB are free, so you are charged for 400 GB at $0.09 per GB. You pay $36.00 per month in data transfer out fees. AWS Global Accelerator hourly fee: You pay hourly for two Global Accelerators for each hour the connection is active. The hourly fee for each Global Accelerator is $0.025, or $0.05 per hour. You pay $36.00 per month in Global Accelerator hourly fees. Accelerated Site-to-Site VPN Data Transfer Premium fee: The fee for VPN Data Transfer Premium is decided by the larger direction of data transfer, in this case 1,000 GB of data transferred in. The fee is $0.015 per GB for 1,000 GB of traffic between Regions in America and Europe. You pay $15.00 per month in Accelerated Site-to-Site VPN Data Transfer Premium fees. You pay $123.00 per month for Accelerated Site-to-Site VPN.
AWS Client VPN endpoint association $0.10 per hour AWS Client VPN connection $0.05 per hour
AWS route tables
AWS Route Table Concepts and How Route Tables Work
AWS Private Link , VPC EndPoints
AWS PrivateLink | VPC Endpoint Service | Demo
Gateway Endpoint


Interface Endpoint



Private Link vs VPC Peering

Now you can calculate AWS cost in near real-time for your serverless applications
Concurrency Labs - AWS Price Calculator tool
GWLB
Access virtual appliances through AWS PrivateLink
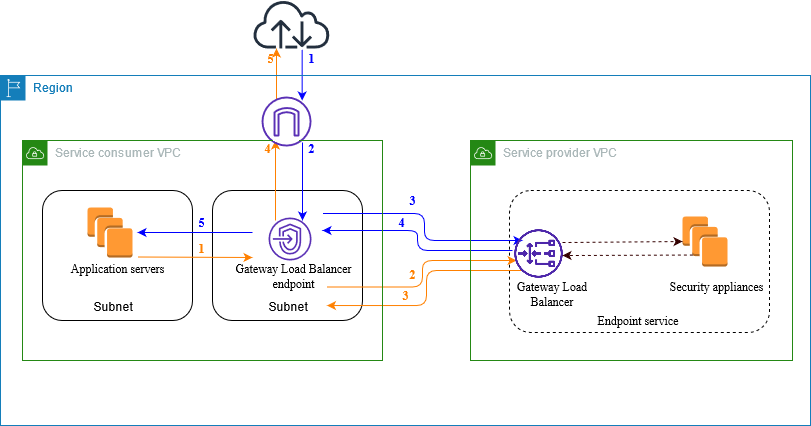
How to integrate Linux instances with AWS Gateway Load Balancer
https://github.com/aws-samples/aws-gateway-load-balancer-tunnel-handler
imspections methods
Centralized inspection architecture with AWS Gateway Load Balancer and AWS Transit Gateway
Amazon VPC Routing Enhancements Allow You to Inspect Traffic Between Subnets In a VPC
Deployment models for AWS Network Firewall with VPC routing enhancements
Implementing third-party firewall appliances in AWS: Comparing two methods
Best practices for deploying Gateway Load Balancer
Choose one-arm or two-arm firewall deployment modes for egress traffic inspection Choose one-arm or two-arm firewall deployment modes for SSL/TLS traffic inspection
CISCO
Cisco Secure Firewall 7.1 Release - Deployment with AWS Gateway Load Balancer
Are there any notes on how to configure the firewall for hair-pinning the traffic through the firewall as it nolonger has the traditional inside/outside setup? (see upper)
AWS Gateway Load Balancer and Geneve Single-Arm Proxy Deploy a Cluster for Threat Defense Virtual in a Public Cloud
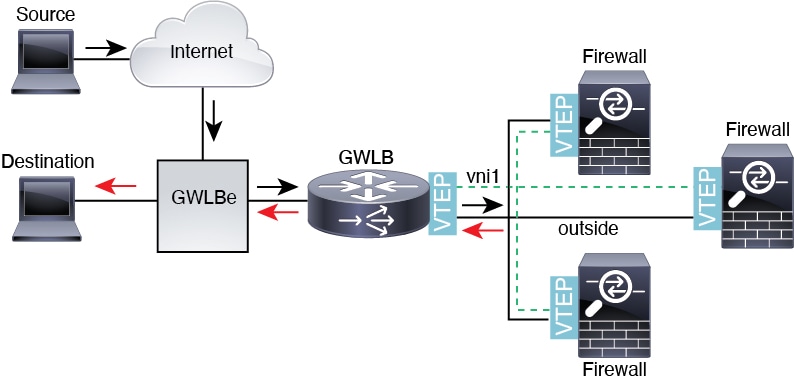
Configure Geneve Interfaces Configure Geneve Interfaces
Geneve is an encapsulation network protocol similar to Virtual eXtensible Local Area Network (VXLAN).
The FTDv supports Amazon Web Services (AWS) Gateway Load Balancer, which combines a transparent network gateway (that is, a single entry and exit point for all traffic) and a load balancer that distributes traffic and scales the virtual appliances such as the FTDv with the demand.
The FTDv deployed on AWS platform supports only the single-arm proxy mode.
PA
Associate a VPC Endpoint with a VM-Series Interface

Supported Cloud NGFW for AWS Deployments
FortiGate
In this document, we provide an example to set up the FortiGate Next Generation Firewall instance for you to validate that packets are sent to the FortiGate Next Generation Firewall for VPC-to-VPC and from VPC-to-Internet traffic inspection.
Creating Static Routes for Routing of Traffic VPC to VPC Packets to and from TGW VPCs, as well as on-premises, will be hairpinned off the LAN interface. As such, you need to configure appropriate route ranges that you expect traffic for packets that need to be forward back to TGW. For simplicity, you can configure the FW to send all RFC 1918 packets to LAN port, which sends the packets back to the TGW.
AWS diagrams, architecture, security
List of open source tools for AWS security: defensive, offensive, auditing, DFIR, etc. Topics