Nessus Scanning - whiteowl911/leveleffect GitHub Wiki
Detailed Overview of Nessus Professional

When it comes to security, Tenable products and their Nessus Professional vulnerability scanner belong to the top preferred choices today by many leading companies and security professionals. This article provides closer look and discusses some of the key aspects and reasons why Nessus is so popular in the security industry. Let’s dive right into it.
What Nessus can do?
There are two main functions of this software:
Vulnerability scanning
The primary functionality and the original purpose of Nessus was to provide users with a security scanner, so that they can test their systems for vulnerabilities. Some of the types of vulnerabilities that Nessus can detect are:
- Outdated software and missing security patches
- Misconfigurations and insecure settings
- Detection of known vulnerabilities and CVEs
- Default, blank or weak passwords
- Web application vulnerabilities
Compliance auditing
Nessus also contains extensive capabilities when it comes to compliance auditing. It can perform variety of audits, such as for instance:
- PCI DSS compliance audits
- CIS benchmarks
- Cloud infrastructure audits
- Configuration audits
More details on these are provided further down below.
How Nessus works?
As we already mentioned, Nessus is a vulnerability scanner. This means that it is essentially a massive database of vulnerabilities with some very smart engineering around it. In fact, its vulnerability database is so massive and the engineering done so well that Tenable products are the preferred choice by many well established security companies. They are capable of scanning practically any IT infrastructure asset with almost incomparable level of technological coverage.
Technological reach
Tenable works in close collaboration with all major IT companies around the globe. They work with software and hardware vendors, security companies, security researchers and so on. This allows them to keep track of every newly found vulnerability and to continue expanding their database of vulnerabilities. And this brings the key value to us penetration testers, ethical hackers, auditors and others. Simply said, they maintain this giant database of vulnerabilities for us, so we don’t have to remember every single vulnerability. On every single system. That ever existed. In history.
What can you do with Nessus?
Vulnerability scans
In the main menu there are number of preconfigured vulnerability scanning templates available:
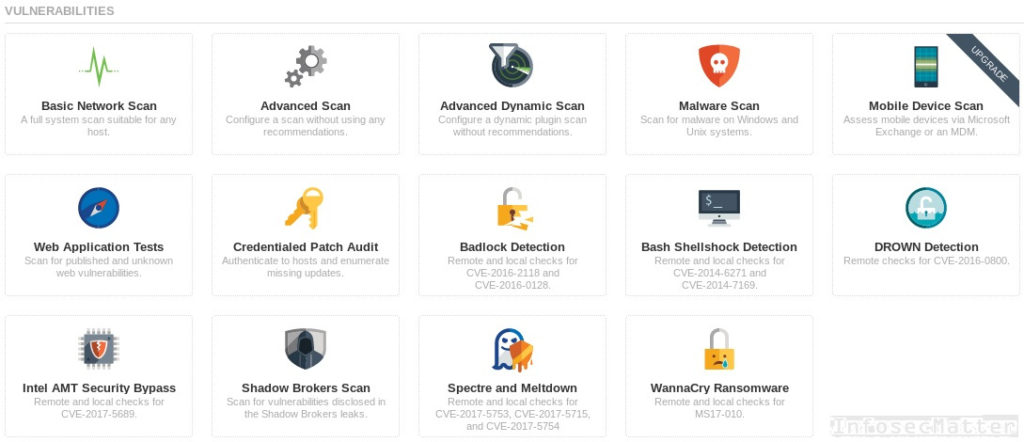
Descriptions of the scanning templates:
-
Basic Network / Advanced Scan – This is the main scanning capability, which allows you to scan remote systems for vulnerabilities. As a target you can specify a single system, a network, or a list of systems and network ranges. You can also provide credentials for the target systems and Nessus will be able to perform additional checks locally on the systems.
-
Malware Scan – This scan will perform remote checks for known backdoor ports and ports associated with malware activity. If you provide credentials, it will also check the systems for known malware IOCs. It will check locally on the systems for malicious processes, network connections to known botnets, identify potentially unwanted programs (PUA/PUP) and much more.
-
Web Applications Test – A vulnerability scan specific to web servers and web applications. This test will check not only for known vulnerabilities, but it will also perform a range of dynamic tests, similar to what Burp Proxy active scanner or Netsparker can do.
-
Credentialed Patch Audit – Here you provide administrative credentials to your target asset and Nessus will check whether the asset is up-to-date and fully patched. You can audit whole range of things, from operating systems (e.g. Windows, Unix) to network devices (e.g. Cisco, Juniper), databases (e.g. Oracle, IBM), security appliances (e.g. F5 Networks, Palo Alto) and much more.
-
CVE Checks – Nessus can also check for a variety of specific and generally popular vulnerabilities such as Spectre / Meltdown, Shellshock, DROWN, Badlock and others. You can quickly check whether your systems are vulnerable to WannaCry ransomware, for instance. Or you can scan your systems specifically for vulnerabilities that were exploitable with tools leaked by Shadow Brokers.
Compliance audits
From the compliance and policy audit perspective there is also a number of preconfigured templates in the main menu:
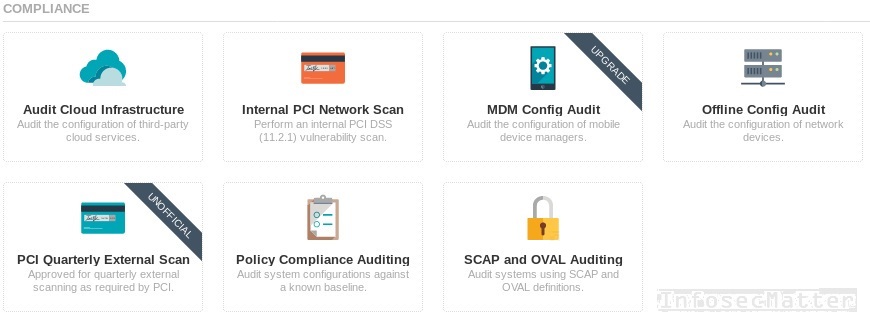
Descriptions of the audit templates:
-
Audit Cloud Infrastructure – With this test you can check configuration of your cloud instances, such as Amazon AWS, Microsoft Azure, Rackspace or others. All you need to do is to provide credentials for your instances and Nessus will do all the heavy lifting. It can perform CIS benchmarks, TNS best practices configuration audits and similar. You can also upload your own audit definitions.
-
Policy Compliance Auditing – This allows you to perform compliance audits of your assets against a known baseline (CIS, DISA STIG, PCI DSS, TNS are all supported). You can audit your network equipment, operating systems, security appliances, database systems, firewalls, web servers, applications servers, docker containers and many others.
-
Offline Config Audit – This is for offline configuration audits of your network equipment. What you can audit here is mostly firewalls, routers, switches, proxy servers and various security appliances. All you need to do is upload current configuration file from your device and select desired compliance benchmark (CIS, DISA STIG, PCI DSS, TNS).
-
SCAP and OVAL Auditing – Nessus also allows you to test your systems against your own provided OVAL or SCAP definitions. This allows you to define your own custom tests, patch audit checks, technical control compliance tests, or perform various security measurements of your systems.
As technology continues to evolve, Tenable constantly tries to keep up with it. They may update these menus and introduce new items into them as well. So don’t be surprised if things change here and there in the future.
Now let’s start zooming in on more technical aspects of the scanner and how things work under the hood.
Nessus under the hood
As we described above, this software can do many things and so to answer how Nessus works technically really depends on how will we use it. Let’s discuss some examples and common uses.
Typically, people use Nessus to perform vulnerability scans, so let’s have a closer look on what happens in this case.
Performing a vulnerability scan
To keep things simple, let’s assume we selected a Basic Network Scan of a single system and we kept all options default. We specified the IP address of the target system and clicked to launch the test. Now what will Nessus do can be broken down into the following phases:
-
Host discovery phase – At first, Nessus will try to find out whether the target is alive. It uses a number of techniques for this. Primarily it uses ICMP ping to “ping” the target. If it fails, then it will also try to connect to several common TCP ports. Additionaly, if the target is on the local network, it will also use ARP protocol to ping the target. Note that you can also skip the ping check in the options and make the Nessus scan without ping.
-
Port scanning phase – If the target is alive, Nessus will perform a port scan of the target. By default it will only scan TCP ports (approximately 4,790 commonly used ports). UDP ports will not be scanned. Note that you can always adjust these settings. It is a good practice to scan all the ports, which means that you would specify 0-65535 as the port range.
-
Service discovery phase – Next phase consists of identifying what kind of service is running on each identified open port. Nessus contains very sophisticated mechanism on how to identify different services and protocols. It will try to probe and fingerprint each open port on the remote target to understand exactly what kind of service (and what version) is running on the remote port. An example could be an Apache Tomcat web server version 7.0.73 running on port 8080 / tcp / www.
-
Assessment phase – This is the crown jewel phase, where the real strength of Nessus scanner lies. In this phase, the scanner will try to identify vulnerabilities on the target system. It will perform a variety of tests against each identified service. Note that Nessus will only select relevant tests appropriate to the detected service type.
Nessus scan report
After the scan is done, you can review the results in the web interface. You can also download the report as HTML page or as CSV file for further processing. The CSV format is particularly useful when writing reports, because it allows you to do text-processing on the results. You can for example extract vulnerable hosts, CVEs, get list of all identified webservers (URLs) or many other things.
You can also export the scan results from the web interface in native format (XML / .nessus). This allows you to make a backup of the results on your disk. You can then import them on to another Nessus instance, for example.
Here’s an example of completed vulnerable scan:
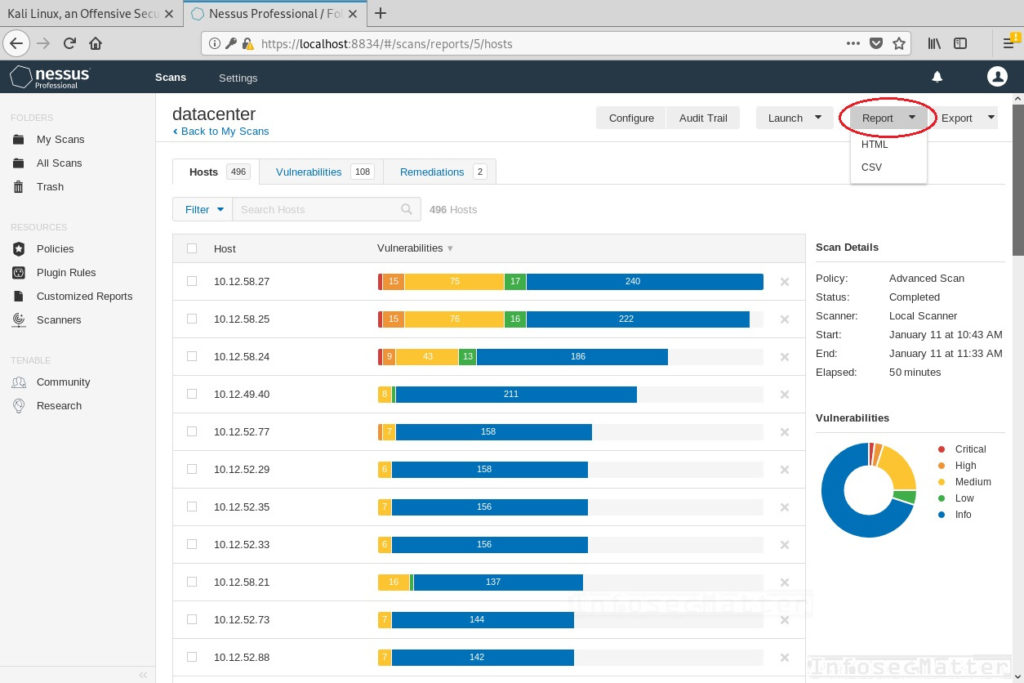
Performing a compliance audit
Another typical use of Nessus is to perform a policy compliance audit of a remote system.
Let’s say we wants to perform a policy compliance audit of a Docker container on a Linux server. We specified the IP address of the target system, provided root credentials and selected the desired compliance policy. Let’s see what happens under the hood when we hit the ‘Launch’ button:
-
Host discovery phase – Similarly as during a vulnerability scan, Nessus will first try to ensure that the target is alive. Everything here is the same in comparison with the vulnerability scan.
-
Port scanning phase – In order to perform a compliance audit, Nessus has to be able to authenticate to the target system. This means that there has to be some service running on the target system and therefore the target system will be port scanned. It is very similar with 2nd phase of the vulnerability scan with only difference that here the port scan parameters cannot be configured. Nessus will therefore perform default TCP port scan (approximately 4,790 ports) against the target.
-
Authentication phase – Now after Nessus confirmed availability of the target system, it will try to authenticate to it with the specified credentials. Note that in case of a Windows system, you can use either Kerberos credentials, LM or NTLM hash or password authentication methods. In case of a UNIX system, you can use even more methods such as password, public key, Kerberos, you can elevate your privileges with sudo, pbrun, dzdo or many other options. The provided credentials has to be administrative, otherwise Nessus will be unable to perform the audit.
-
Audit phase – In this phase, Nessus will perform the actual assessment. Based on the chosen compliance policy, it will perform selected checks on the remote system. For instance, it will run various commands on the system, examine the file system, inspect various configuration files and so on.
Nessus audit report
After the audit is done, you can then again review the results in the web interface. You can also download the HTML or CSV report, or export the results to your computer.
Here is the finished compliance audit results:
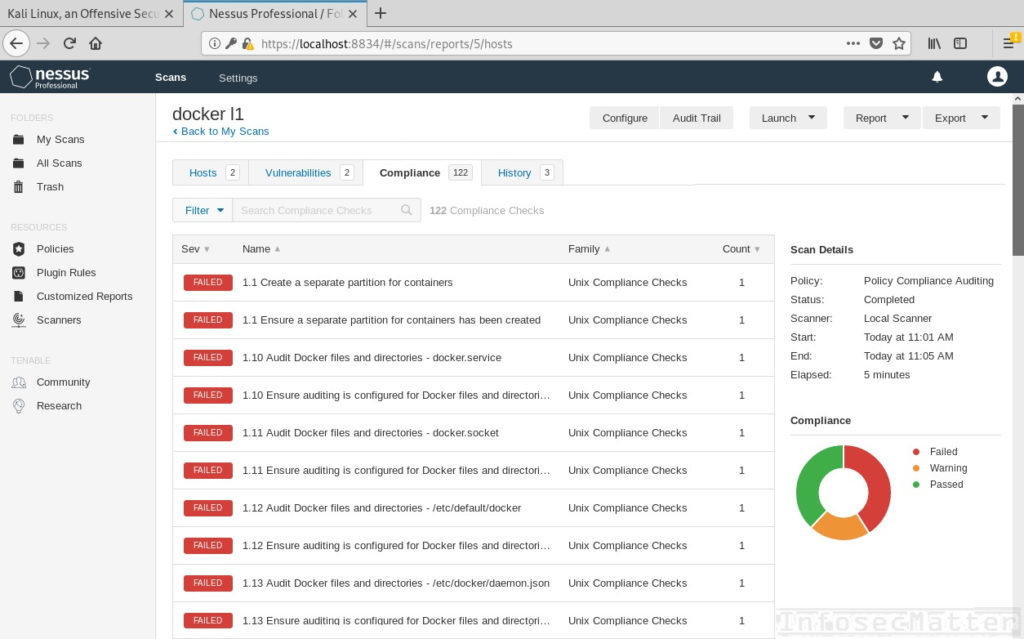
By the way..
Have you ever wondered what is the difference between CIS L1 and L2 benchmark profiles?
- CIS Level 1 identifies essential security settings that should be implemented on a system at minimum without disrupting any functionalities nor impacting performance.
- CIS Level 2 are for tighter security lock downs and for systems in highly secure environments. This could result in reduced functionality or degraded performance.
There is always a trade-off between security and usability. Anyway, if you want to learn more about CIS benchmarks, just visit the official website (link). Let’s get back to our topic.
What can Nessus scan?
We mentioned already that Nessus offers very compelling level of technological coverage. Let’s now dive little bit into this topic and see what systems, devices or applications can we actually scan (or audit) with it. We will also try to answer some of the frequently asked questions.
Can Nessus scan network devices?
Yes, it can. Nessus can do vulnerability scans as well as compliance and policy audits against all kinds of network devices. Let’s cover some examples in the following sections in detail.
Can Nessus scan switches?
Short answer is no. But it really depends on what you mean by scan. Let’s break this down into more detail.
Vulnerability scan of a switch

Suppose you want to do a vulnerability scan of a switch on your network. A typical network switch operates on Layer 2 of the OSI model, which means that it doesn’t have an IP address. It basically operates only on MAC address level. And so if it doesn’t have an IP address, you cannot scan it with Nessus. You cannot scan a MAC address with Nessus. A MAC address in the network is not running any services (e.g. a web server). There is nothing to connect to really. So no, Nessus cannot scan an ordinary, typical dummy L2 switch.
Layer 3 switches
There are also these devices called L3 switches. And these devices are basically enhanced L2 switches with some routing capabilities. A L3 switch can route IP packets and act as a router in a network. That means that it has an IP address. And if it has an IP address, then yes – you can totally scan a L3 switch with Nessus. Perhaps it is even running some services (e.g. a management interface).
Business class and enterprise level switches
If we are talking about business class and enterprise level switches (e.g. Cisco Catalyst), these devices typically have a designated interface for managing the switch. Usually it is referred as Ethernet management port and it is completely separated from all the other ports. If you connect your computer to this port, you will be able to access the management interface of the device and access all sorts of services (e.g. a Telnet, SSH, TFTP or SNMP). You can totally scan this with Nessus.
Credentialed audit of a switch
Now when we touched on management interfaces of switches, Nessus can also perform variety of credentialed (authenticated) tests of the switches. You can do patch audit, policy compliance test or configuration audit of switches. The most popular vendors such as Cisco, Juniper or Brocade are all supported. You can also just upload your configuration to the web interface and Nessus will audit it “offline” without having to access the switch.
Can Nessus scan routers?
Yes, you can definitely scan routers with Nessus. It’s the same case as with L3 switches or business class and enterprise level switches. If it has an IP address, then you can scan it. Furthermore, if you connect your computer on the management port, you will be able to access the management interface of the router and access all sorts of services (e.g. a Telnet, SSH, TFTP or SNMP). You can totally scan these with Nessus. Lastly, you can also perform a credential patch audit, configuration audit, or a policy compliance checks of the router.
Can Nessus scan firewalls?

Yes, you can definitely scan a firewall, but there are multiple aspects which needs to be considered. For starters, there are many kinds of firewalls and firewalls can have multiple interfaces. Therefore it really depends on what is your position and what exactly you are aiming to do. Let’s try to break this down.
Host-based firewall
If we are talking about host-based firewalls, such as a firewall running on a Windows system, then the answer is no. You can’t specifically aim on the firewall itself, because the firewall doesn’t have IP address on its own. You can only aim on the host system and in that case it would equivalent to a typical vulnerability scan of a Windows system, albeit potentially with some filtered ports.
Gateway with a firewall
In some small organizations you may find a Linux box acting as a router (gateway) providing access to the Internet. In such setup it is typical that the box has NAT and firewall rules configured on it using IPTables (or Nftables, UFW or similar), so it acts as a firewall as well. Is it any different from the previous case? No it’s not. You simply cannot aim on the firewall itself, because it doesn’t have IP address on its own. You can only aim on the system as a whole.
Business class and enterprise level firewalls
These kinds of firewalls usually have multiple interfaces, so it depends. But general rule still applies – if it has an IP address, then you can scan it. Moreover, similarly as with any other business class or enterprise level hardware, these network devices typically have a designated interface port for management purposes. If you connect your computer on the management port, you will be able to access all sorts of services (e.g. a Telnet, SSH, web interface or SNMP) to manage the firewall. You can totally scan them with Nessus.
Scanning through firewall
Scanning through firewall is definitely possible. But there are certain aspects which needs to be considered when doing this. Depending on the firewall rules and its configuration, your scans will most likely require some adjustments and fine tuning. This is because default scan settings are likely going to be too aggressive for the firewall and the firewall will block us. This would result in a slow or inaccurate scans.
Here are some guidelines from Tenable blog regarding scanning through firewalls and how to adjust your scans (link).
Firewall auditing
Nessus can also perform policy audits and configuration audits of various firewalls. Most major vendors such as F5 BIG-IP, Cisco ASA, Palo Alto or FireEye are all supported. In order to audit a firewall, you can either provide administrative credentials for accessing the firewall’s management interface, or you can also upload the firewall’s configuration to Nessus web interface to audit it “offline”.
Can Nessus scan printers?

Yes, Nessus can scan printers. However, scanning of printers is disabled by default, because printers are generally considered as fragile devices. Scanning of printers can cause all sorts of issues. For one it can cause them to malfunction or crash, which can be a serious problem for some organizations. Employees will not be able to print and this can sometimes be equal to losing money. Another thing that can happen is that the printers could start printing out pages of random information.
When you think about it, there is no real good reason to scan printers with a vulnerability scanner. I’m not suggesting that we should just completely ignore them during our penetration testing activities. In fact, printers can be source of all kinds of valuable information (e.g. usernames, email addresses etc.). But in general, it is not recommended to scan printers with vulnerability scanners and therefore it is disabled in Nessus by default.
Here’s the official statement from Tenable regarding scanning of fragile devices (link).
Can Nessus scan mobile devices?
Yes, it can. There is nothing stopping you from pointing Nessus at your mobile phones, tablets, smart watches or any other mobile devices. But do not expect to find much, because mobile devices typically do not expose any services. In fact, they usually filter and drop all incoming traffic.
There are also only a few basic plugins related to mobile devices in Nessus to detect major issues. For instance, it can detect if you left ADB debug port open on your Android device or similar issues, but not much more than that.
Here’s an example of a vulnerability scan of an iPhone:
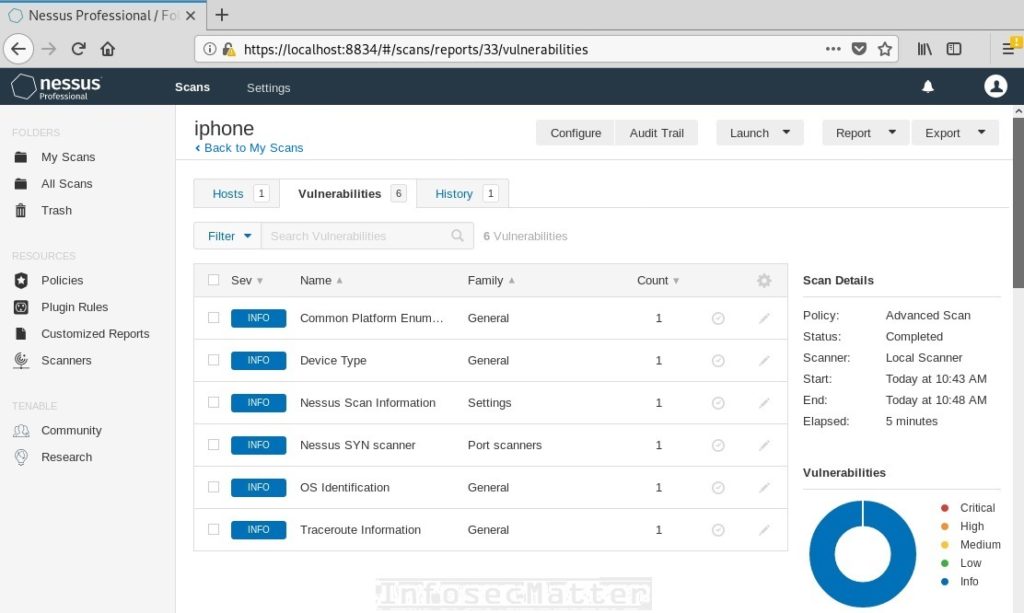
And here’s an Android example:
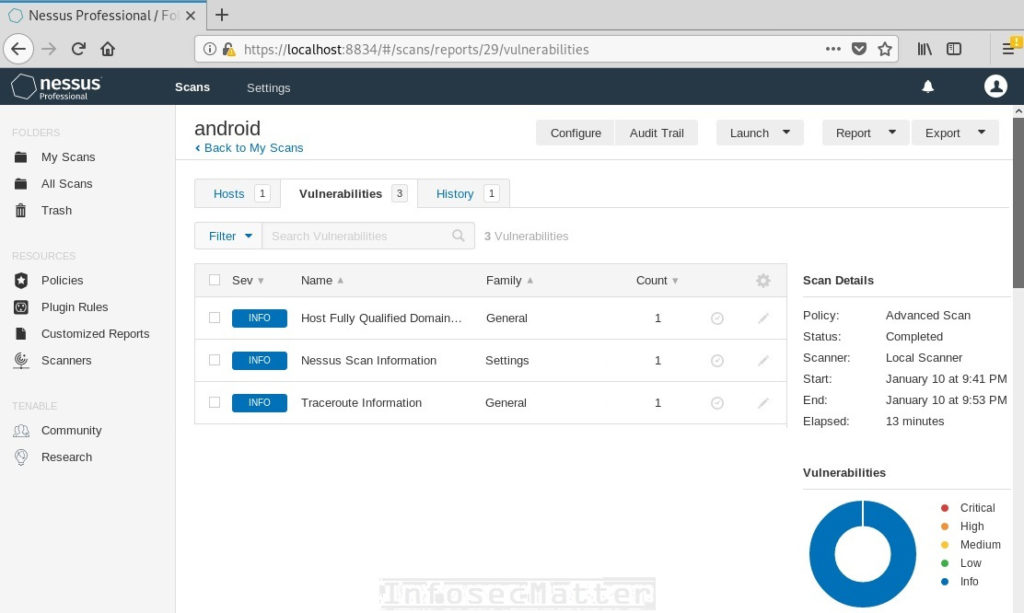
As you can see, there is nothing much to see. iPhone exposes one open port while Android doesn’t even expose a single one.
Audit of mobile devices
In corporate environments, mobile devices are usually managed through a centralized MDM solution, such as VMware AirWatch, Apple Profile Manager, Microsoft Intune, IBM MaaS360 or others. With upgraded solution (tenable.io) you can perform audits of the corporate mobile devices through the MDM solution. Tenable.io will access the devices through the MDM and it will perform configuration audits and identify vulnerabilities locally on the devices.
Audit of MDM solution
With the same upgraded solution (tenable.io) you can also perform configuration audits of the MDM solution itself. This will allow you to identify misconfigurations or insecure settings related to the MDM. Again, this is not available in the Nessus Professional version – you have to upgrade to tenable.io.
Can Nessus scan containers?

Yes, you can scan docker containers with Nessus, although this falls more under compliance and audit category rather than vulnerability scanning.
When performing vulnerability scan of a system with docker installation, you will mostly see only informational messages such as that a docker service was detected running on the remote host. Unless there is docker API exposed on the target system, there is nothing much extra you can really see from the vulnerability scanning perspective.
The most value lies in the compliance and audit area. There is a number of CIS compliance policies related to docker available in the menu which you can use. You can scan your docker setup as well as the containers running on the target system. Keep in mind that this is a credentialed (authenticated) scan, so credentials are required to access the host.
How about docker images?
No, Nessus cannot scan docker images. It can only scan (audit) containers as described above. Neverheless, with upgraded solution (tenable.io) it is possible to scan docker images as well. In fact, it allows you to integrate scanning of your docker images directly into your CI and CD processes. You can scan your docker images as part of the development cycle automatically, or you can scan them ad-hoc.
Tenable has a designated solution for this called Container Security. More technical information can also be found here.
Can Nessus scan web applications?
Yes, it definitely can. There is a scan template for this in the main menu called ‘Web Application Tests‘. The scanner will first identify all web servers running on the target and then perform thorough vulnerability scan against each identified instance. Nessus contains specific tests for web servers and specific tests for web applications.
Once Nessus identifies a web server, it will start URL crawling in order to find deployed applications. Then it will run a whole range of dynamic tests against the identified applications. This is somewhat similar to what other web application scanners do (e.g. Burp Proxy active scanner or Netsparker). Although the functionality here is somewhat limited in comparison to those web application scanners, in overall it can bring a lot of value, because it scans for things the others scanners may not scan for.
Additionally, you can also specify credentials and perform authenticated test against the web application. This is useful when you need to test areas of the application available only when you are authenticated. Various methods of authentication are supported (Basic / Digest, custom login form using GET or POST request, session cookie import and others).
Can you scan an URL?
No, you cannot scan a specific URL with Nessus at this point. As a target you can only specify a FQDN, hostname, or IP address. Note that this may change in the future with new versions.
Can Nessus audit a web server?
Yes it can! There are many policy compliance audit templates for auditing web servers and application servers. All the following vendors are supported.
Web servers:
- Apache HTTP server
- Nginx web server
- Microsoft IIS
- Oracle HTTP Server
- IBM HTTP Server
- …
Applications servers:
- Apache Tomcat
- IBM WebSphere
- Oracle WebLogic
- RedHat JBoss EAP
- Jetty
- …
Can Nessus do penetration testing?
In short no, Nessus cannot do penetration testing. It is a vulnerability scanner and as such its primary place is in the Vulnerability Assessment area. Nessus is simply the “VA” part of the VAPT (Vulnerability Assessment and Penetration Testing). It is not the “PT” part. Nessus is very sophisticated tool and it can do many useful things, but it is just a tool. It is a tool used by penetration testers when they need to bring effectiveness (automation) into their work. You cannot simply run Nessus on a target and call it a penetration test.
Penetration testing requires human factor, because it is highly variable and specialized activity. Every organization is different. Every network and every asset in it can be different. Configuration of these assets, systems and devices can vary immensely among different environments. You cannot simply tell Nessus: “Go ahead and get me Domain Admin in this organization”, or “Get me into a CEO’s mailbox of this company”, or “Find me all vulnerabilities in this network”. Nessus cannot do that. Humans are still better at this.
Can Nessus scan SCADA?

Yes, it can. When it comes to OT and ICS area, Nessus contains hundreds of plugins (tests) specifically for SCADA systems. If a remote system is found to be exposing a SCADA interface during a vulnerability scan, the scanner can scan it for vulnerablities. However, SCADA devices are generally considered as fragile devices and therefore by default scanning of them is disabled. Make sure to enable it in the ‘Host Discovery’ settings if you want to include them in your scans.
Note that Tenable also has an upgraded solution specifically to cover whole ICS area called Industrial Security. This offers a robust solution for organizations with largely industrial technology footprint.
Can Nessus scan Linux?
Yes, it definitely can. It can not only scan Linux systems for vulnerabilities, but it can scan practically any other UNIX-like system as well. AIX, BSD, Solaris, HP-UX, you name it. It’s all there.
Furthermore, there are also many policy compliance audits available in Nessus to audit Linux systems. All major Linux distributions are supported. There are compliance policies (CIS, DISA STIG, PCI DSS, TNS) for RedHat, Centos, Ubuntu, Debian, Oracle Linux, SUSE and many others. Patch auditing and local security checks are also available for all of them.
Can Nessus scan MacOS X?
Yes, it definitely can. Not only it can scan Apple MacOS X remotely for vulnerabilities, there are also multiple policy compliance audits available (CIS, DISA STIG) for MacOS X, including detailed patch auditing and local security checks. All major MacOS X versions are supported.
Can Nessus scan ESXi hosts?
Yes, it can. The vulnerability scanner covers VMware ESXi very well. It will inform you about all missing updates and security patches on the remote ESXi hosts. It will also let you know which vendor advisories are unpatched (e.g. VMSA-2019-5519, VMSA-2018-6981) and so on.
Additionally, there are also multiple policy compliance audits available (CIS, DISA STIG) for ESXi hosts, including detailed patch auditing and local security checks. All ESXi versions are covered.
Can Nessus scan domain controller?
Yes, it can scan domain controllers. In Windows Active Directory (AD) environments, domain controllers are a vital part of the AD infrastructure and their security posture is truly critical. Nessus can not only scan domain controllers remotely as any other Windows system, there are also additional checks and multiple policy compliance audits available specific to domain controllers.
From remote vulnerability scanning perspective, all Microsoft Windows version are covered by remote (unauthenticated) checks. You will be informed about missing security updates, unpatched vendor advisories (e.g. MS17-010, MS14-066 etc.) including Microsoft Bulletins (e.g. KB4467680, KB4487044) and so on. There are also tests for misconfigurations and insecure settings, as with any other Windows system.
From auditing perspective, there are multiple policy compliance audits available in the menu (CIS, DISA STIG and also MSCT) specific to domain controllers. You can also perform a detailed patch audit and local security checks which contain specific additional tests for domain controllers.
Is it safe to scan domain controller?
Yes, it is totally safe. We have never encountered any issue during years of penetration testing when it comes to scanning domain controllers with Nessus.
Can Nessus scan itself?
Yes, Nessus can totally scan itself. Simply set your target to 127.0.0.1 (or localhost) and hit the ‘Launch’ button.
Conclusion
Nessus is an excellent tool for vulnerability assessment providing outstanding technological coverage. There is practically nothing that you cannot scan with it. Furthermore, new technologies come and go all the time and Tenable products have always adapted and evolved to reflect this. Not only they cover new technologies, they also support the legacy ones as well.
If you liked this article and you would like more, please subscribe to our mailing list and follow us on Twitter and Facebook to get notified about new additions.
SHARE THIS




TAGS | CIS | Compliance policy audit | DISA STIG | Docker | Domain controller | Linux | Mobile devices | MSCT | Nessus | Network devices | PCI DSS | SCADA | Security audit | TNS | VMware ESXi | Vulnerability scanner | Web applications
RECENT POSTS
Nessus Plugin Library
Solving Problems with Office 365 Email from GoDaddy
Empire Module Library
CrackMapExec Module Library
Metasploit Android Modules
MOST VIEWED POSTS
Top 16 Active Directory Vulnerabilities
Top 10 Vulnerabilities: Internal Infrastructure Pentest
Terminal Escape Injection
Cisco Password Cracking and Decrypting Guide
Capture Passwords using Wireshark
MOST VIEWED TOOLS
Port Scanner in PowerShell (TCP/UDP)
SMB Brute Force Attack Tool in PowerShell (SMBLogin.ps1)
SSH Brute Force Attack Tool using PuTTY / Plink (ssh-putty-brute.ps1)
Default Password Scanner (default-http-login-hunter.sh)
Nessus CSV Parser and Extractor
Leave a Comment
Your email address will not be published. Required fields are marked *
Type here..
Name*
Email*
Website
Save my name, email, and website in this browser for the next time I comment.
SEARCH THIS SITE
FOLLOW US
Github | Twitter | Facebook
Enter your email address:
CATEGORIES
- Bug Bounty Tips (10)
- Exploitation (13)
- Network Security (8)
- Penetration Testing (42)
- Tools and Utilities (9)
- Vulnerability Assessment (8)
ARCHIVES
- January 2022 (1)
- November 2021 (1)
- October 2021 (1)
- July 2021 (1)
- June 2021 (1)
- May 2021 (5)
- April 2021 (6)
- December 2020 (3)
- November 2020 (3)
- October 2020 (3)
- September 2020 (3)
- August 2020 (4)
- July 2020 (4)
- June 2020 (6)
- May 2020 (6)
- April 2020 (4)
- March 2020 (4)
- February 2020 (7)
- January 2020 (1)
RECENT POSTS