Module #5 Journal Entries - wAlber47/Tech-Journal GitHub Wiki
Last week, during an exploit demonstration, we performed a hydra attack against the samwise account on cupcake. This week, we will extend this sort of informed guessing attack against two other targets. Trying to acquire easy to guess usernames/passwords is often the first step in the exploitation stage. This is different from brute-force attempts which can be very processor-intensive, take a very long time and may not yield results.
CEWL
The Custom Wordlist Generator included in Kali, crawls websites and creates a custom wordlist. In this assignment, we pulled down a list of words from each faculty's page. This gives us basic words to use when attempting to brute force their login.
The syntax for this was fairly simple, we used the -d flag to keep the program from scanning other sites. The default allows it to flake out to one other site attached to the main page that is being scanned. Without this, our scan would pull all the keywords each time.
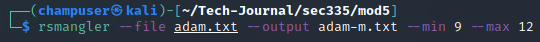
RSMangler
A really useful tool that adds various characters to lists of words. Commonly, it adds "l33t" speak, numbers, mixed cases, special characters, as well as others. For our lists, the flags that were used were -min 9 -max 12 as we knew the passwords were this length.
For example, with this tool, if you input the word "password", the list may be returned with:
password123
123password
pa$$word
PASSWORD
When combining this with the custom word lists that we created earlier, it they work together really well.
Hydra
As I was comfortable with it and wanted to get a little more experience, I chose Hydra for this section. The use case is almost exactly the same as here.

The one difference being that instead of using ssh, we used the http-get flag when specifying the type at the end of the command.
Issues
- SSH brute forcing took some time, could refine my word lists or possibly try another tool to shorten this