GroundWork FoxHttp Interceptors & Authorization - viascom/FoxHttp GitHub Wiki
Authorizations are used to authorize a client to a server. Every authorization has a scope in which it will be executed. A scope is defined by the url and request type. If you use the DefaultAuthorizationStrategy you can also use placeholders (*) in your url. One scope can have none, one or many authorizations.
An authorization gets executed after the url has been processed an the headers and query parameters are set (right after the RequestHeaderInterceptor).
- BasicAuthAuthorization (example of BasicAuth)
- BearerTokenAuthorization
Because an authorization gets executed after the url, headers and query parameters has been set it is not possible to change the query parameters based on the FoxHttpRequestQuery. So if you want to change thr url or query parameters it is recommended to use the RequestInterceptor.
Interceptors are used to execute code at a specific point during a request.
FoxHttp knows 6 different interceptors:
- RequestInterceptor
- RequestHeaderInterceptor
- RequestBodyInterceptor
- ResponseCodeInterceptor
- ResponseBodyInterceptor
- ResponseInterceptor
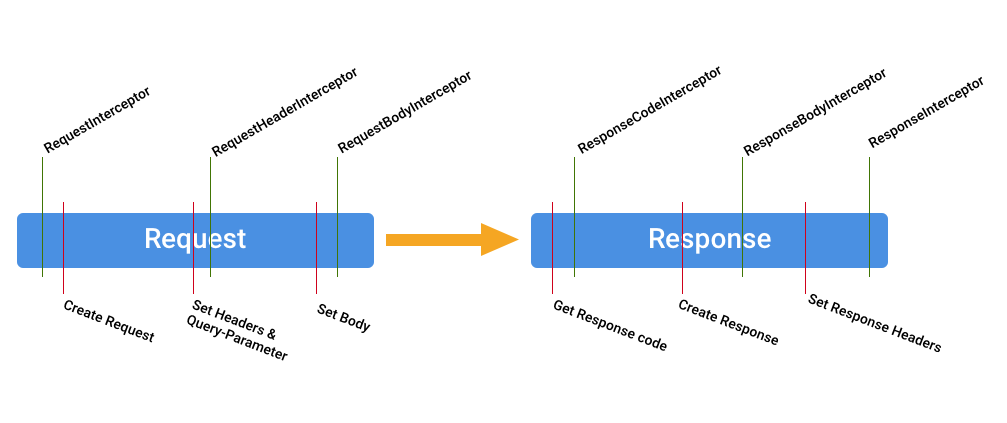
Every interceptor has a public void onIntercept(InterceptorContext context) throws FoxHttpException; method.
The InterceptorContext depends on the used interceptor. The context is used to read and write from the request/response.
All interceptors are stored in the FoxHttpClient. They can be added easily by the registerFoxHttpInterceptor method in the FoxHttpClientBuilder.
Every interceptor has a weight property which is used to define the order of the execution. The lowest number is executed first.
The following list should give you an idea which interceptor is used for what.
- Set a global query parameter.
- Change the url based on a rule.
- Set a product specific header.
- Change already set headers.
- Encrypt the serialized body (an example of a simple XOR-Interceptor).
- Calculate a checksum of the serialized body.
- Throw an exception if the response code is 500.
- Decrypt the serialized body.
- Change request meta data.
- Log the response.
- Save the response to a database.