Threat Hunting RCE Zimbra CVE 2022 37042 - sudokom/All-About-Red-Team GitHub Wiki
The first step is to find a CVE which you wanna hunt on! We will be taking an example of CVE-2022–37042 . The next step is to find some shodan/fofa dorks using which we can find multiple IP’s vulnerable to this particular CVE. You can create your own Dorks, or Google it up. A lot of researchers do post dorks for the same. In our case it is going to be:
Shodan-query : http.favicon.hash:”1624375939" 200
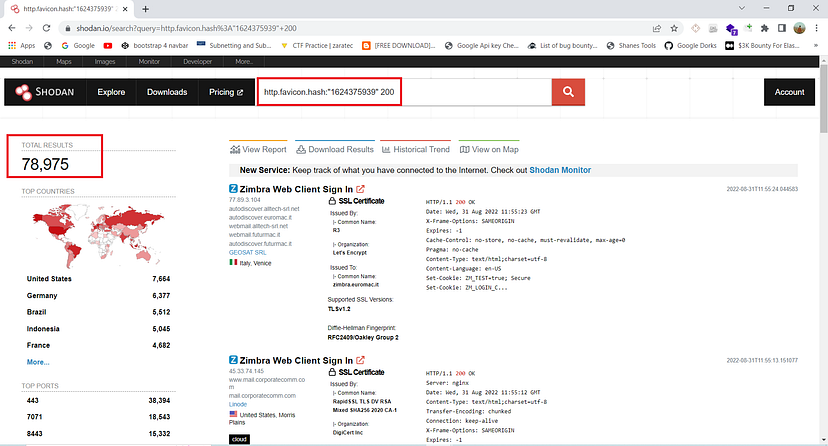
The next step is to pass this dork to uncover to get a list of all the domains.
Command: cat dorks.txt| uncover | tee -a final.txt
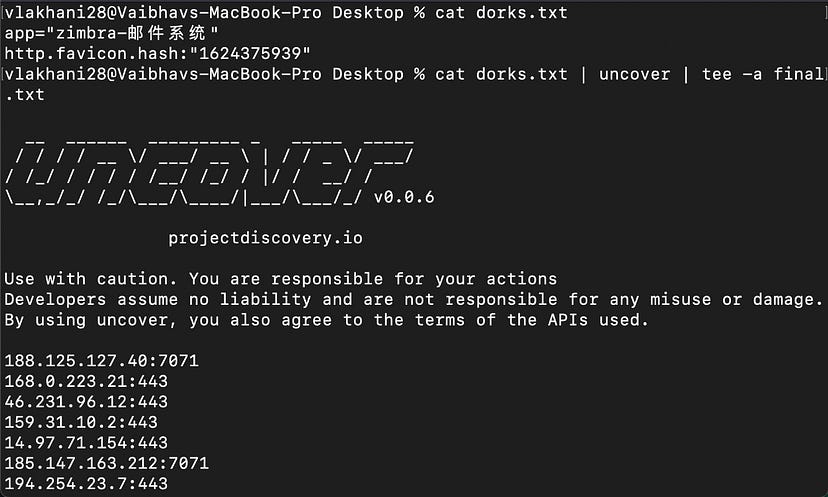
Now while checking how many IP’s do we have we found the following result :
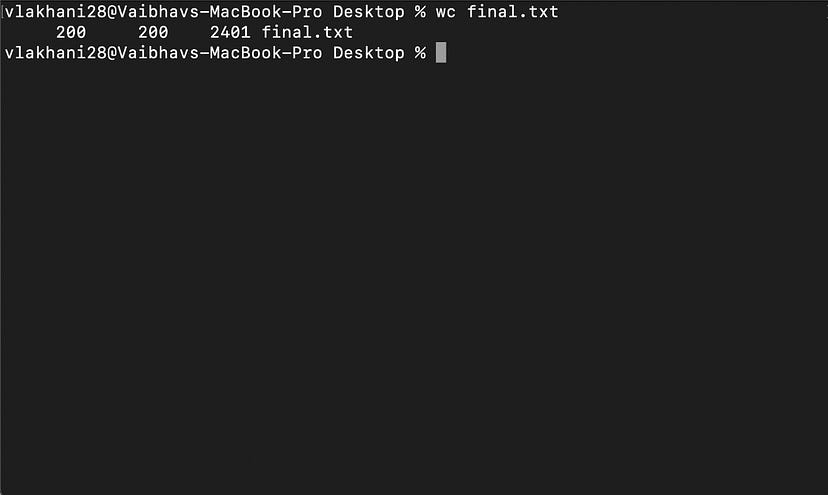
We have only 200 results from uncover whereas we found almost 79k IP’s from shodan .This is because of the Shodan Api limit.
So to increase our scope we thought of modifying our dork by adding more filtering to extract more IP’s from shodan via uncover . Also you can add multiple shodan API keys in uncover’s config file .
Modified dork using country parameter :
http.favicon.hash:”1624375939" country:”US”
Now we will pass this list of dorks to uncover :

So finally we have more IP’s now .
You can create your own dorks with different parameters to obtain more results from shodan using this technique and do share with us in the comments section.
Next, pass the list of IP’s to httpx to find the ones which are up and running. And then supply it to nuclei with the template name to find the ones which are valid.
Command: cat fin.txt | httpx — silent | nuclei -t ../nuclei-templates/cves/2022/CVE-2022–37042.yaml

The entire process can be converted with this one liner script:
Command: cat dorks.txt| uncover — silent | httpx — silent | nuclei -t ../nuclei-templates/cves
We hope that this technique might help you to mass hunt CVE’s and find a lot of Vulnerable domains .
Happy Hunting!