RESPONSE MANIPULATION - sudokom/All-About-Red-Team GitHub Wiki
Response Manipulation leads to Account Takeover
Description
This finding mainly relies on misusage of OTP to check user’s authentication which they bypass its OTP check using response manipulation.
Login Process of the App
This program’s user authentication is a bit different from other. It doesn’t take any password at login page. Instead, it would send an OTP to your e-mail everytime you login, and you need to provide the correct OTP within a few minutes in order to gain a successful login. A successful login request and response is as per below:

So, a POST request was made together with the OTP and e-mail address. If it is correct, it would returns a verified status, userid and a token. After the front-end has received this message, front-end would make another request together with the token to access user’s information:

However, if the OTP is incorrect, it would return something like below:
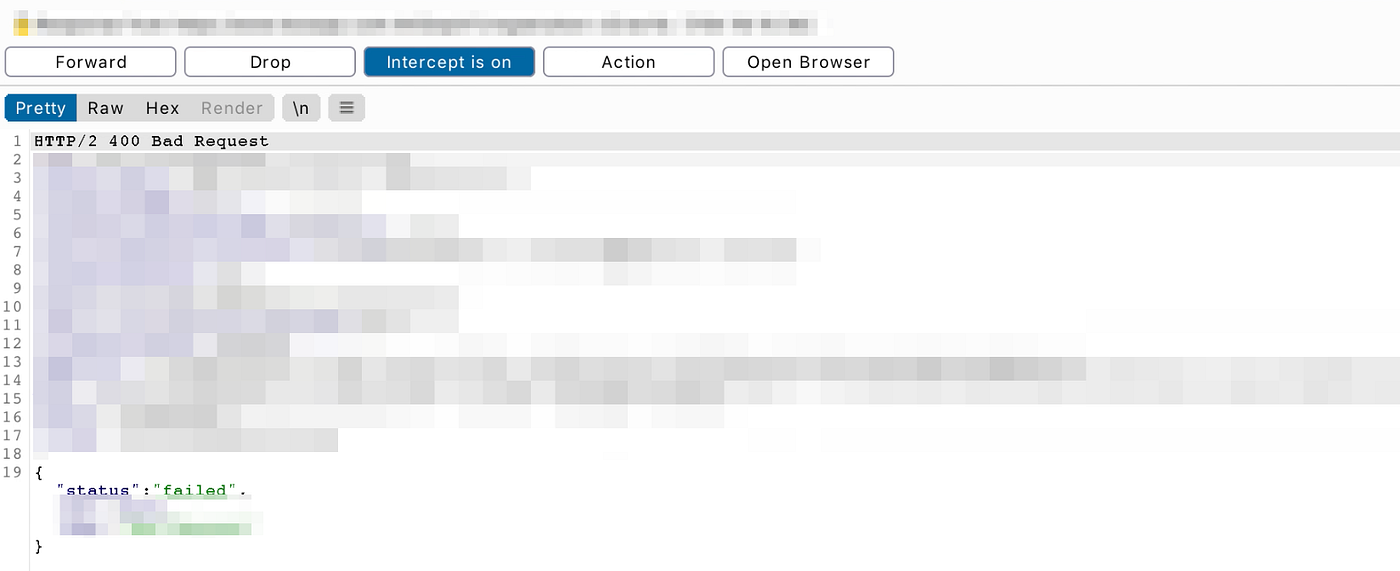
After logging in for several times, I noticed something wrong here. I noticed that for each time I login, the token does not change at all and this token has been used kind of as a session cookies to determine user’s authentication. So, I try to use response manipulation to login to the web app with a wrong OTP.
How to Reproduce the Bug
The bug can be reproduced by following few steps:
-
Copy the successful login response message below:

-
Now, turn on Burp and set intercept as On.
-
Follow normal login procedure. After an OTP is sent to your e-mail, forget about it. Input 0000 as the OTP and intercept the request. Then, press Action -> Do Intercetp -> Response to this request:
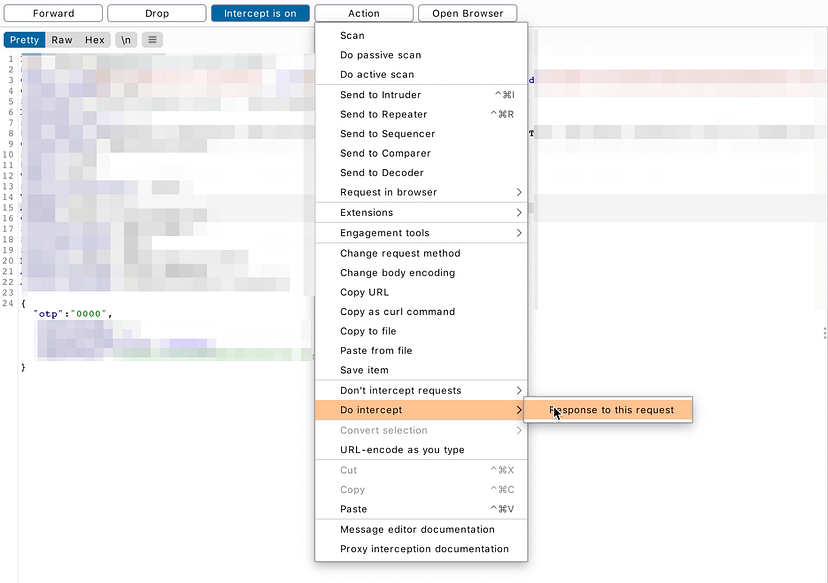
-
Now, forward the request, you should receive the login failed message:

-
Now, paste the response you copied in step 1 and press forward. Then, you would successully bypass the OTP check and lead you to your login session.