20190709_jeffrey - silenceuncrio/diary GitHub Wiki
0850
review
0910
試著來解析一下目前 HTTPS 用來建 key 的 /usr/sbin/icos/web_x509_lighttpd.sh
#!/bin/bash
openssl req -x509 -newkey rsa:2048 -keyout /tmp/icos/web/lighttpd.pem -out /tmp/icos/web/lighttpd.pem -days 3650 -nodes -subj '/CN=localhost'
mv /tmp/icos/web/lighttpd.pem /etc/icos/web/lighttpd.pem
sync
以 M360P 為例
openssl version
root@M360-P:/home/admin# openssl version
OpenSSL 1.0.2 22 Jan 2015
看一下官方提供的 1.0.2 manpages
DESCRIPTION
The req command primarily creates and processes certificate requests in PKCS#10 format. It can additionally create self signed certificates for use as root CAs for example.
解析一下
PKCS - Public Key Cryptography Standards (公鑰密碼學標準) PKCS#10 - Certification Request Standard (憑證申請標準)
往下看 -x509 這個 COMMAND OPTIONS
-x509
this option outputs a self signed certificate instead of a certificate request. This is typically used to generate a test certificate or a self signed root CA. The extensions added to the certificate (if any) are specified in the configuration file. Unless specified using the set_serial option, a large random number will be used for the serial number.
If existing request is specified with the -in option, it is converted to the self signed certificate otherwise new request is created.
1300
早上發現我可以只為了 lighttpd 先準備好 key
root@M360-P:/tmp# time openssl genrsa -out /tmp/lighttpd.key 2048
Generating RSA private key, 2048 bit long modulus
.........................................................+++
.......................................................+++
e is 65537 (0x10001)
real 0m 6.60s
user 0m 6.57s
sys 0m 0.03s
這種比較耗時的 process 可以只做一次
爾後每次 web 這個 icos module 在 init 的時候
再利用該 key 來產生 self signed root certificate
root@M360-P:/tmp# time openssl req -x509 -new -key /tmp/lighttpd.key -out /tmp/l
ighttpd.crt -days 3650 -nodes -subj '/CN=localhost'
real 0m 0.12s
user 0m 0.11s
sys 0m 0.01s
看一下該 certificate 的有效期
root@M360-P:/tmp# openssl x509 -in /tmp/lighttpd.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
84:ef:b6:c0:92:ea:77:c9
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=localhost
Validity
Not Before: Jul 9 13:07:08 2019 GMT
Not After : Jul 6 13:07:08 2029 GMT
Subject: CN=localhost
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d1:4d:70:45:e5:f1:dc:f7:7c:e0:ef:c4:6f:d3:
79:95:6d:da:f0:71:52:04:6b:93:df:49:5d:37:da:
9d:8f:0b:45:84:2b:e6:4a:ac:ec:8d:40:e3:44:f3:
e9:d2:4e:64:b1:30:70:51:0c:ed:ef:3d:82:ed:fb:
c7:d9:ec:5d:d7:12:22:3f:43:54:af:71:0f:c6:fe:
36:16:f3:9c:d8:ea:aa:28:d8:c3:f0:95:4a:1c:9d:
f5:51:de:e5:85:d1:2d:1f:3b:8e:7e:2d:42:e7:8b:
ab:11:df:b1:c8:18:61:7b:8e:08:6e:55:ad:1a:fb:
ab:bb:9f:d1:7c:fb:22:7b:3e:0a:15:f1:64:48:51:
91:02:6b:20:0b:c2:52:e7:b9:dd:c9:bc:b2:f0:9d:
6f:d0:93:df:e9:99:03:97:b7:92:3f:8a:cd:b5:79:
13:46:6e:08:49:49:86:14:61:59:35:5f:33:c3:ab:
c5:f5:82:d5:ab:64:75:fc:a0:99:10:99:f0:fe:55:
27:44:d8:4f:f1:0c:cc:01:0f:08:af:31:9f:e7:09:
78:28:66:9b:56:8f:66:cb:48:30:e3:da:cd:14:50:
d8:d4:be:8e:69:43:d7:19:92:3b:7b:f1:0c:93:ee:
31:44:5e:9a:e8:ea:1f:5b:3d:5a:a1:fe:f0:ec:c3:
43:8f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
26:88:D0:F9:CA:2B:72:35:A1:A1:C2:AE:57:54:DA:59:C9:2C:52:C3
X509v3 Authority Key Identifier:
keyid:26:88:D0:F9:CA:2B:72:35:A1:A1:C2:AE:57:54:DA:59:C9:2C:52:C3
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
62:be:cb:34:ae:c1:69:d9:7e:97:57:19:60:1f:a2:4c:b9:dc:
70:00:5d:1f:62:5c:94:27:b5:54:13:0e:bc:7d:67:5d:14:f6:
b8:91:c1:96:b3:55:03:16:c0:2c:7e:b4:0e:d0:88:4b:15:13:
cf:ca:08:db:d1:c4:9d:b6:d4:e9:49:46:22:19:2f:77:ed:83:
40:9a:cc:4b:0e:ae:77:dc:96:29:54:a1:6c:d7:1f:2e:f1:c0:
9f:eb:ef:b5:15:2d:13:52:dd:c2:a0:c7:ae:f7:83:5d:c8:eb:
16:de:14:6f:00:38:ea:17:4e:79:bd:45:ef:75:54:b0:78:99:
cc:79:dd:41:b2:43:6b:13:e0:bc:33:7c:70:dc:83:a2:ca:71:
d2:96:98:3a:9c:08:b5:d9:1c:9b:32:32:18:14:11:84:3c:30:
6b:17:a5:de:e5:fb:92:c1:31:3b:6f:04:f4:f0:14:e0:6c:6a:
00:3c:1a:01:8d:c5:22:d8:29:4a:f3:f3:dd:83:73:5d:58:74:
0e:cc:c0:7a:76:99:cb:23:54:c1:84:3c:46:89:a5:89:eb:38:
f4:63:03:32:58:ba:78:b8:96:54:a1:c1:45:45:76:15:97:13:
c4:eb:13:7c:97:89:8f:d1:aa:e8:e7:1d:bc:67:f8:d6:0c:d5:
dc:79:e0:a4
這樣就不用擔心憑證過期的問題了
不過後來有了新發現
只要我們的設備是利用 -x509 這 option 來產生 self signed certificate 而不是一個 certificate request 的話
只要使用者透過瀏覽器跟我們設備作 HTTPS 連接
以 chrome 為例
不管憑證的有效期過期與否
瀏覽器都會顯示警告視窗
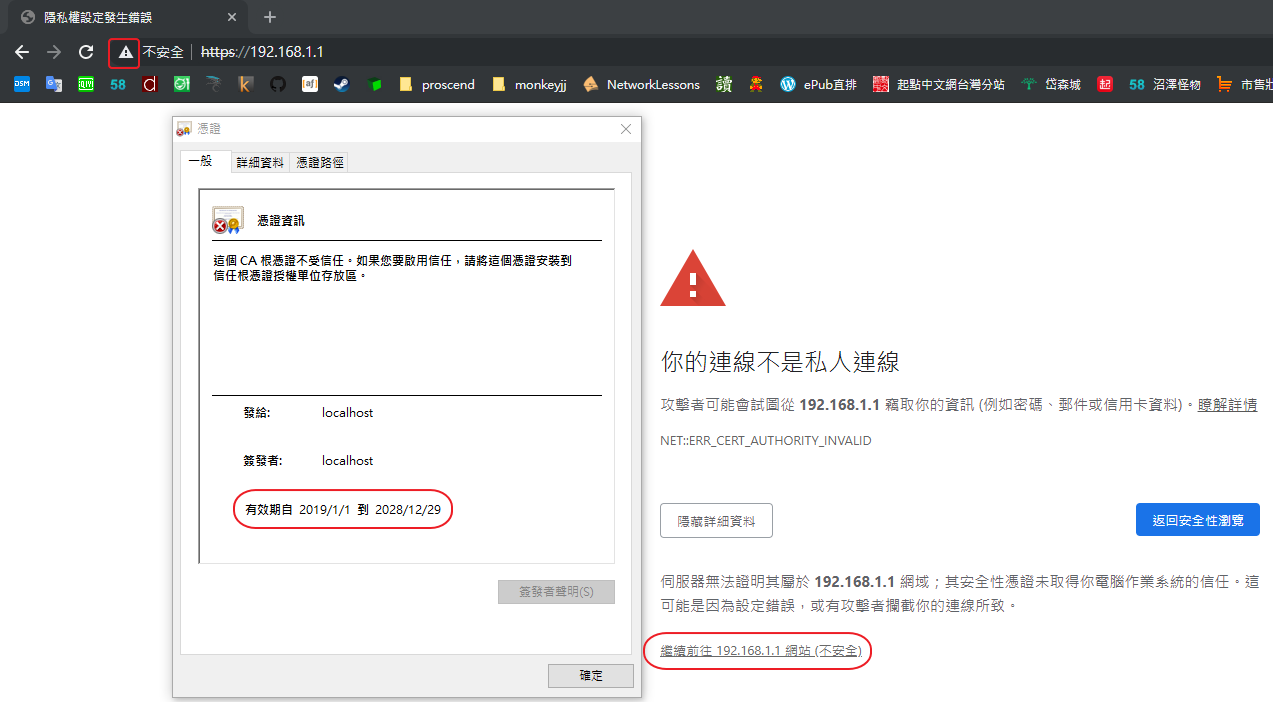
使用者要自行決定是否繼續前往
一旦點選繼續
那就算我們憑證的有效期過期了
HTTPS 也是能繼續使用
所以我們設備就不用去煩惱憑證過期與否的問題了
過不過期都沒有意義
因為我們設備的憑證是用 openssl -x509 這 option 來產生的
瀏覽器不管我們憑證的有效期過期與否
一律顯示警告視窗
讓使用者自行承擔風險
值得一提的是
參考 Lighttpd SSL Certificate Installation 可知
lighttpd HTTPS 所需的 ssl.pemfile 是由 key file 和 certificate file cat 在一起
1415
因為 M330 與 M360P
feature/lighttpd 都已 merge 回 develop branch 的緣故
目前 web server 已改由 lighttpd 來提供服務
我需要提醒大家把 lighttpd build 進 image 裡
而且要記得 source proenv.sh
M330
- proscend 外層目錄
- source proenv.sh
- make package/feeds/packages/lighttpd/{clean,compile,install}
M360P
- proscend 外層目錄
- source proenv.sh
- make package/net/lighttpd/{clean,compile,install}
目前 M330 已有災情傳出
1455
回到 M330 - develop
- Vendor/Prosucts = GENERIC/1_GENERIC_WIFI
1510
發現 chrome 可以匯入憑證
而 M330 self signed certificate 的憑證 若 有效期 過期的話
的確會有影響
M330 - 憑證到期
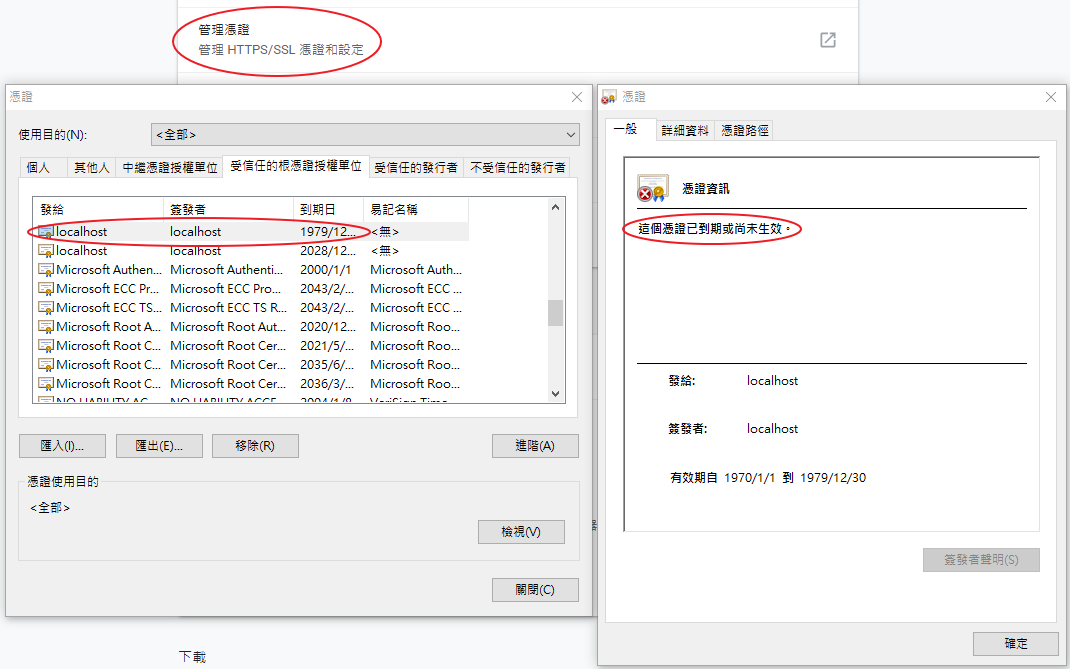
M360 - 憑證未到期
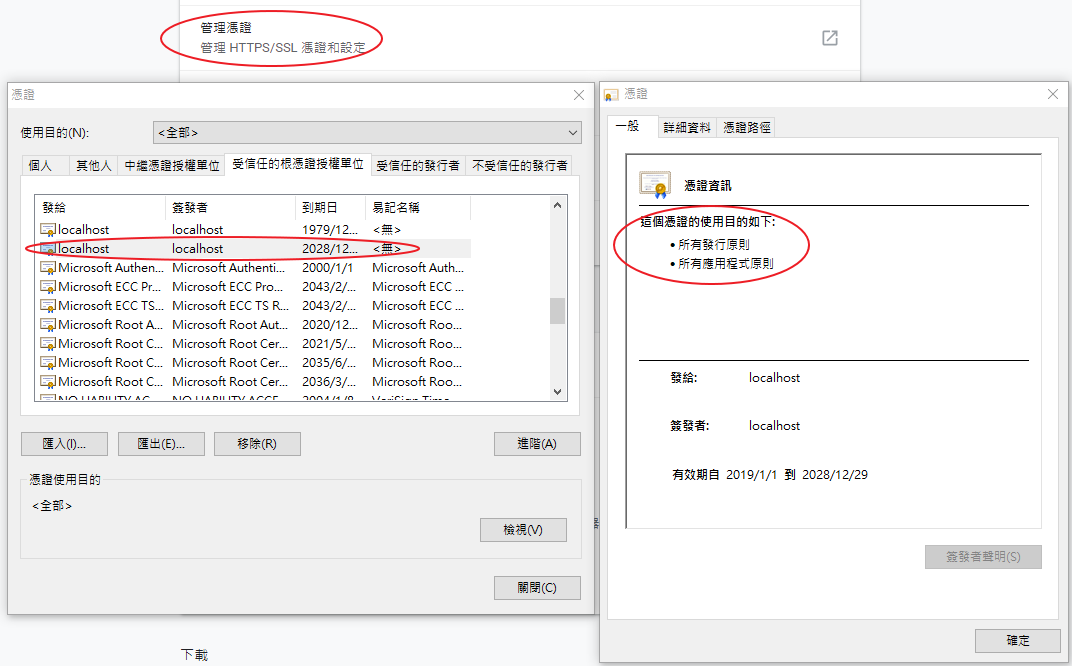
但就算匯入了 憑證未到期
瀏覽器一樣告知警告訊息給 user

看來真的沒必要為了 HTTPS 的 自簽 憑證 多作些什麼
徒勞無功
1555
M330 - develop
- Vendor/Prosucts = GENERIC/1_GENERIC_WIFI
WiFi 相關 CGI 都沒改到
M330 - develop - 'WiFi > WiFi Config'
commit 5f3de67088cbaf8608662a8e14a6f49ec757052d
Refs: [develop], {origin/develop}
Author: jeffrey <[email protected]>
Date: Tue Jul 9 16:06:10 2019 +0800
'WiFi > WiFi Config'
wifi_apsta.cgi
- jweb.access.filter(ATTVAL_SYSTEM_LEVEL1, _config);
- jweb.access.filter(ATTVAL_SYSTEM_LEVEL2, _apply);
- jweb.access.filter(ATTVAL_SYSTEM_LEVEL2, _set);
- jweb.access.filter(ATTVAL_SYSTEM_LEVEL1, _status);
- jweb.access.filter(ATTVAL_SYSTEM_LEVEL1, _help);
proscend/prosrc/webcgi/wifi_apsta.c | 12 ++++++------
1 file changed, 6 insertions(+), 6 deletions(-)
WiFi > MAC Filter 和 WiFi > Client List 都是呼叫同一支 wifi_apsta.cgi
1735
下禮拜預定的 task 原本是 M300 - DNP3 protocol
目前有個 task 優先序更高
M300 - Layer 2 Encapsulation over GRE (L2oGRE)
我需要評估並給出 schedule