IAM: Identity and Access Management - rajeshkumarplv/aws-ccp-notes GitHub Wiki
IAM is a Global Service. Takes care of Users and Groups.
Root account created by default. Should not be used or shared. Users are people within an Org and can be Grouped. Users can belong to multiple groups.
Examples: Developers Group, Operations Group
IAM: Permissions.
In AWS you always apply the least privileged principle which means you do not give more permissions than a user needs.
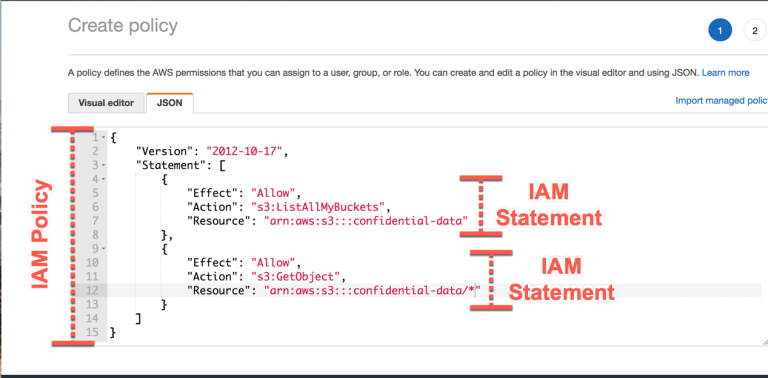
Users or Groups can be assigned JSON Documents called Policies.
IAM- Password Policy
Strong passwords == higher security of your account You can setup password policy Prevent password re-use Allow IAM users to change passwords
Multi Factor Authentication - MFA
You want to protect Root Accounts and IAM Users. MFA = password you know + security device you own!
If a password is stolen or hacked, account is not compromised.
MFA Devices for AWS:
Virtual MFA Device
- Google Authenticator.
- Authy
Universal 2nd Factor (U2F) Security Key
Hardware Key FOB MFA Device.
Hardware Key FOB MFA Device for AWS Gov Cloud (US) by SurePass.
How to access AWS?
- AWS Management Console -> -> Protected by Access Keys
- AWS CLI -> Protected by Access Keys
- AWS SDK -> Protected by Access Keys
Access Keys are generated through AWS Console. Users can manage their own Access Keys. Access Keys are Secret, like Password. Do not Share.
Do not use Root Account to create Security Credentials.
IAM Roles for AWS Services
In order for some AWS Services to perform actions on your behalf, we will assign permissions to AWS Services using IAM Roles. Common Roles are EC2 Instance Roles, Lambda Function Roles, Roles for CloudFormation.
IAM Security Tools
- IAM Credentials Report (At Account Level)
- IAM Access Advisor (At User level)
Guidelines and Best Practices.
- Dont use root account except for AWS Account Setup.
- Assign users to Groups and Permissions to Groups.
- Create strong password policy.
- Use and enforce use of MFA.
- Create and use Roles for giving permissions to AWS Services.
- Use Access Keys for Programmatic Access (CLI/SDK).
- Never share IAM Users and Access Keys.
Shared Responsibility Model of IAM
Customers are responsible for defining and using IAM policies. AWS is responsible for Infrastructure Security, Compliance Validation and Configuration and Vulnerability Analysis.