Usage: Decoding How To - ptrkrysik/gr-gsm GitHub Wiki
This How To aims to provide users an overview of how to decode captured files using gr-gsm's grgsm_decode. We will use the same capture file that is used in the widely known Airprobe How-To. The file is available in the gr-gsm's test_data subrepository. You can also download it by running following commands in the gr-gsm's source directory:
git submodule init
git submodule update
Decoding BCCH
First let's take a look on the Broadcast channel.
We start wireshark at the beginning (see here for more info), so we can analyze the decoded messages.
Next start grgsm_decode with the following options:
grgsm_decode -c vf_call6_a725_d174_g5_Kc1EF00BAB3BAC7002.cfile -s $((100000000/174)) -a 725 -m BCCH -t 0
-c is specifying the cfile formatted file vf_call6_a725_d174_g5_Kc1EF00BAB3BAC7002.cfile
-s specifies the sample rate of the capture, which is dependent on the hardware. The file we are working on was captured with a sample rate of 100e6, but with a decimation of 174. That's why we perform the division 100000000/174, and put in inside the $((.....)) so that it is evaluated by your command line before passing it to the program. If you have no decimation, you don't have to do this.
-a 725 tells the app the ARFCN of the capture
-m BCCH is the channel type we are using, BCCH in our case
-t 0 specifies the timeslot
After running, look for the Immediate Assignments in Wireshark. It should look like on the following screenshot:
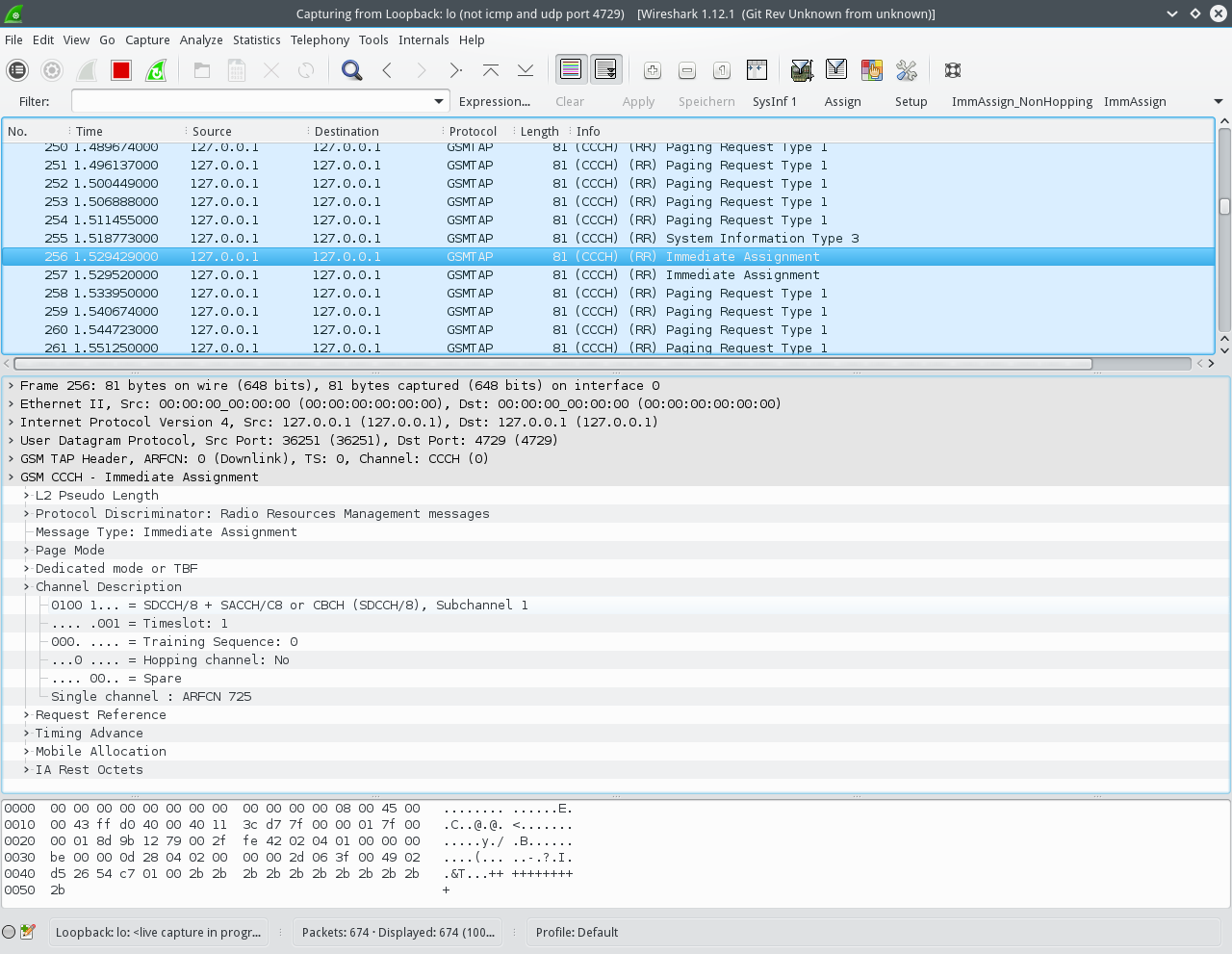
You can see that there is an Immediate Assignment to a SDCCH8 channel on timeslot 1.
Decoding SDCCH
Now we will take decode the assigned SDCCH that we found in the previous section.
We restart our Wireshark capture, and start the decoder app with the following options:
grgsm_decode -c vf_call6_a725_d174_g5_Kc1EF00BAB3BAC7002.cfile -s $((100000000/174)) -a 725 -m SDCCH8 -t 1
We just changed two options:
-m SDCCH8: we tell the app to decode a SDCCH
-t 1: we now want to decode timeslot 1, as the Immediate Assignment we previously found assigned the SDCCH on timeslot 1.
The output in Wireshark should look like on the following screenshot:
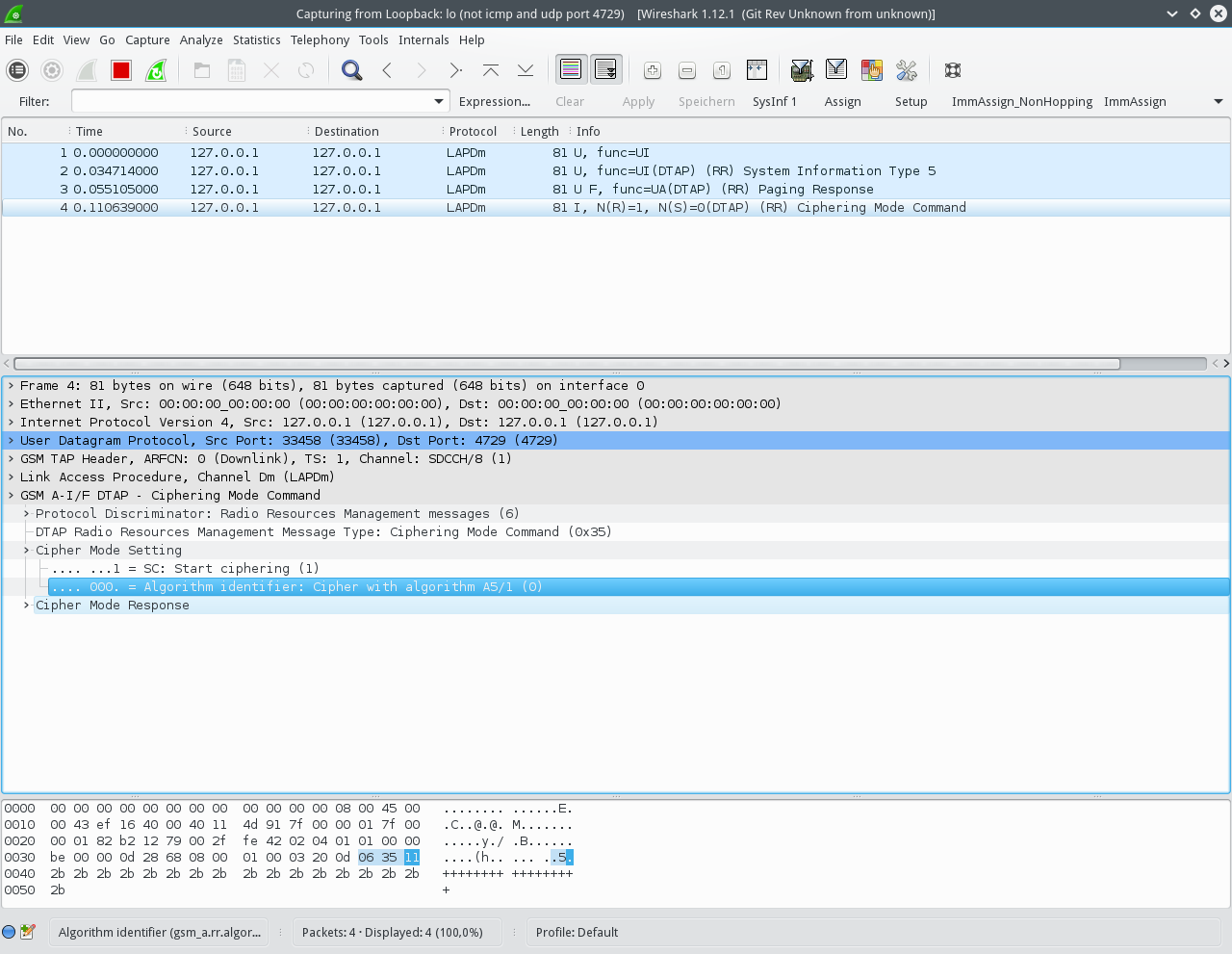
We can only see the unencrypted messages until the Ciphering Mode Command, where the BTS tells the mobile the Cipher to use. As we know the ciphering key Kc, we can use the decoder app to decrypt and decode all messages for us:
grgsm_decode -c vf_call6_a725_d174_g5_Kc1EF00BAB3BAC7002.cfile -s $((100000000/174)) -a 725 -m SDCCH8 -t 1 -e 1 -k 0x1E,0xF0,0x0B,0xAB,0x3B,0xAC,0x70,0x02
We just added two options:
-e 1: tells the decoder to use A5 cipher in version 1, as it was stated in the Ciphering Mode Command
-k 0x1E,0xF0,0x0B,0xAB,0x3B,0xAC,0x70,0x02: specifies the cipher key to use for decryption
Wireshark should now display all the traffic for us:
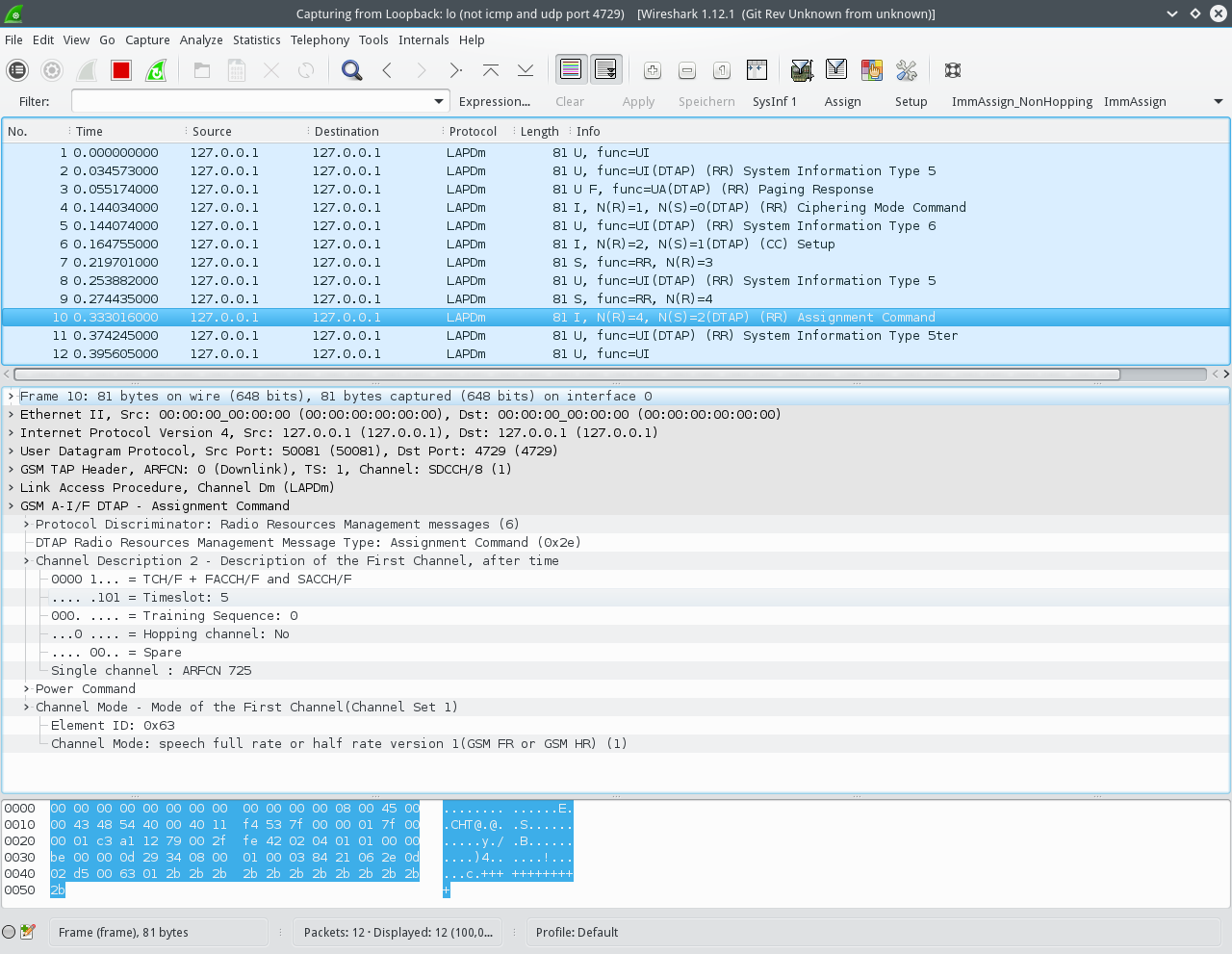
Note there is an Assignment message, which assigns the mobile a voice traffic channel on timeslot 5 using GSM-FR.
Decoding Voice Traffic
We can now decode the voice traffic on the assigned TCH/F channel.
Restart the Wireshark capture, and issue the following command:
grgsm_decode -c vf_call6_a725_d174_g5_Kc1EF00BAB3BAC7002.cfile -s $((100000000/174)) -a 725 -m TCHF -t 5 -e 1 -k 0x1E,0xF0,0x0B,0xAB,0x3B,0xAC,0x70,0x02 -d FR -o /tmp/speech.au.gsm
The changed options are:
-m TCHF: we want to decode a TCH/F (traffic channel, Full-rate)
-t 5: TCH/F is on timeslot 5, as we saw before
-d FR: the voice codec of the channel, as seen in the Assignment command.
-o /tmp/speech.au.gsm: the output file for the decoded voice traffic.
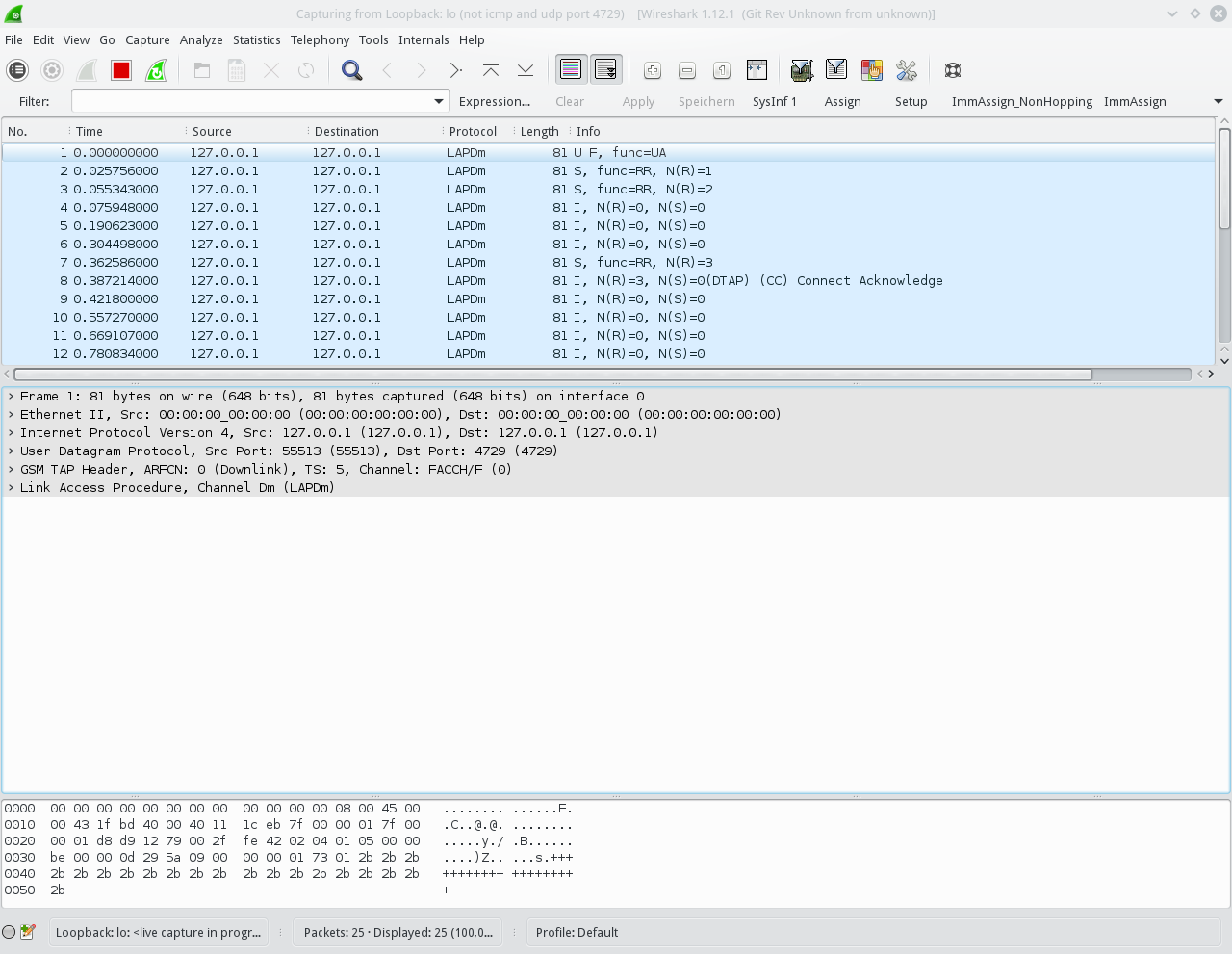
In Wireshark we can see the messages associated with the traffic channel, for example the Connect Acknowledge:
After the app is finished, you can open the resulting file /tmp/speech.au.gsm in a audio player that supports gsm codecs (for example VLC) and listen to the captured audio.