AWS KMS - keshavbaweja-git/guides GitHub Wiki
Architecture
AWS KMS is a tiered service consisting of web-facing AWS KMS hosts and a tier of HSMs. Cryptographic operations are performed on a distributed fleet of FIPS 140-2 validated hardware security modules (HSMs). The AWS KMS HSM is a multichip standalone hardware cryptographic appliance designed to provide dedicated cryptographic functions. AWS KMS hosts only allow TLS with a ciphersuite that provides perfect forward secrecy. AWS KMS authenticates and authorizes your requests using the same credential and policy mechanisms of AWS Identity and Access Management (IAM) that are available for all other AWS API operations.
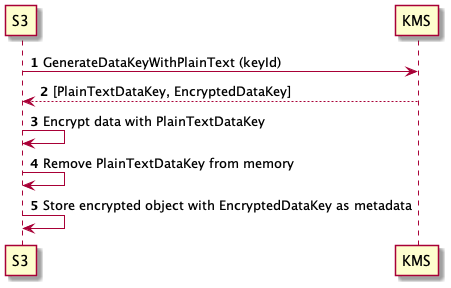
S3 SSE KMS - Encrypt
@startuml
autonumber
S3 -> KMS: GenerateDataKeyWithPlainText (KeyId)
KMS --> S3: [PlainTextDataKey, EncryptedDataKey]
S3 -> S3: Encrypt data with PlainTextDataKey
S3 -> S3: Remove PlainTextDataKey from memory
S3 -> S3: Store encrypted object with EncryptedDataKey as metadata
@enduml
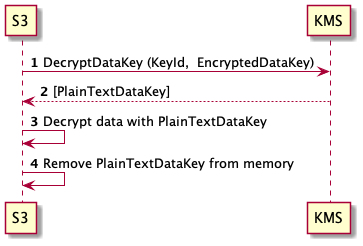
S3 SSE KMS - Decrypt
@startuml
autonumber
S3 -> KMS: DecryptDataKey (KeyId, EncryptedDataKey)
KMS --> S3: [PlainTextDataKey]
S3 -> S3: Decrypt data with PlainTextDataKey
S3 -> S3: Remove PlainTextDataKey from memory
@enduml
Features
AWS KMS uses hardware security modules (HSM) for key management, these HSMs are compliant with FIPS 140-2 Cryptographic Module Validation Program.
AWS KMS is integrated with more than 90 AWS services for data encryption.
AWS KMS is integrated with AWS CloudTrail to log key usage for auditing, regulatory and compliance needs.
AWS IAM policies and KMS key policies are used to control access to KMS keys.
AWS KMS supports "bring your own key", (BYOK), you can import your own key material into KMS key. With this option you can generate and manage key material outside of AWS infrastructure. You can manually delete imported key material at any time. Imported key material is supported only for symmetric KMS keys in AWS KMS key stores.
AWS KMS supports custom key stores backed by AWS CloudHSM clusters. AWS CloudHSM provides dedicated, single tenant hardware security module (HSM) which is FIPS 140-2 Level 3 certified. CloudHSM allows you to securely generate, store, and manage cryptographic keys with the keys only accessible by you, AWS personnel have no access to keys stored on CloudHSM. You can set up CloudHSM clusters with multiple HSMs for HA.
AWS KMS supports automated rotation of symmetric KMS generated keys once per year. The service automatically retains older versions of the key to decrypt data encrypted with older versions. Automated rotation is not supported for asymmetric KMS keys, keys with imported key material and keys in custom key stores like CloudHSM.