Secure Kibana using OAuth2 Proxy - dcm4che/dcm4chee-arc-light GitHub Wiki
Content
Run secured archive services and Elastic Stack on a single host explains securing access to Kibana using OAuth2 Proxy which shall allow only authorized users to access the audit messages and system logs with complete stack. Below configurations just highlight the OAuth2 Proxy specific part for independent tests.
-
Create a
Confidentialclient in Keycloak and note down itsSecretwhich shall be used below in OAuth2 Proxy docker configuration.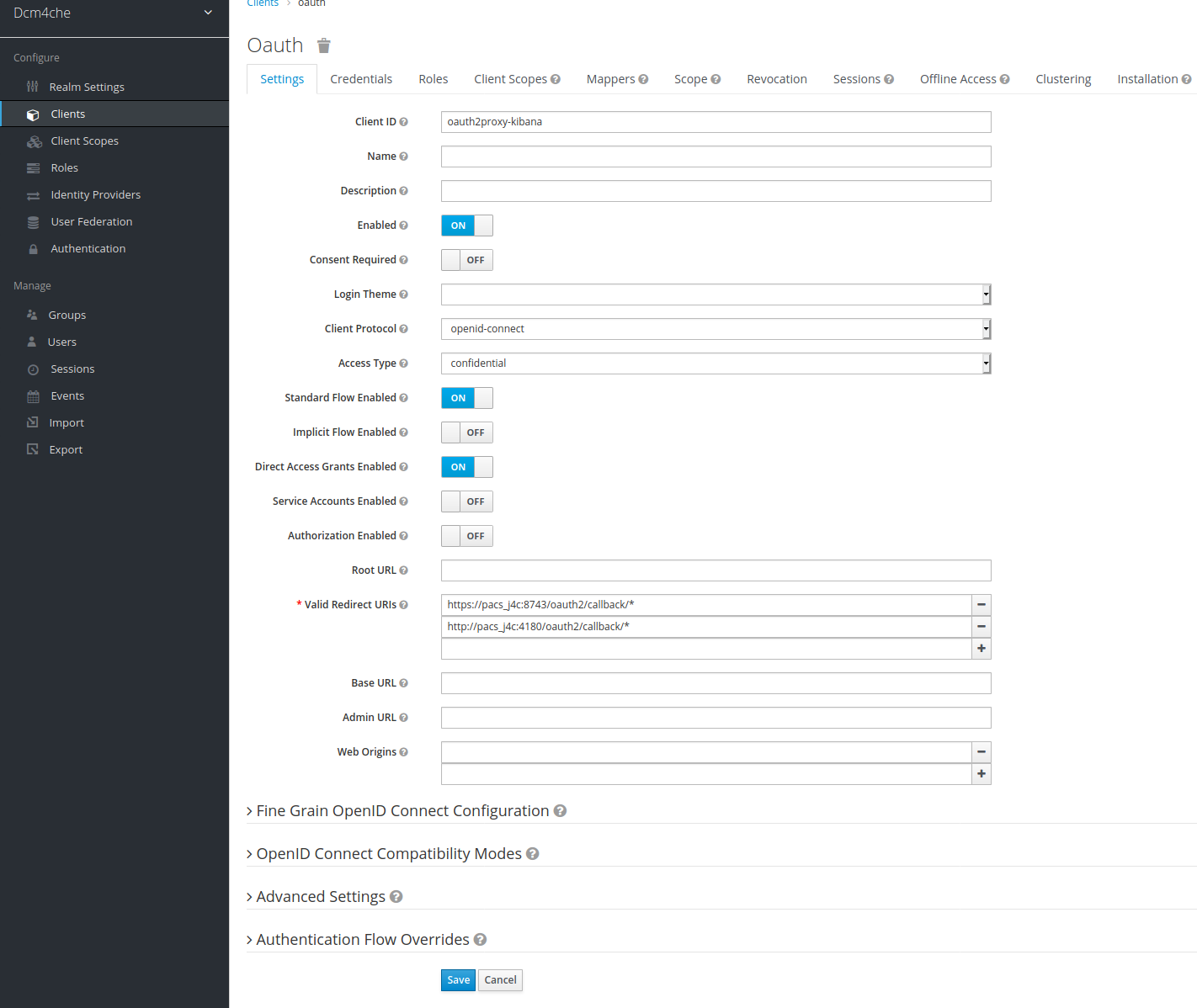
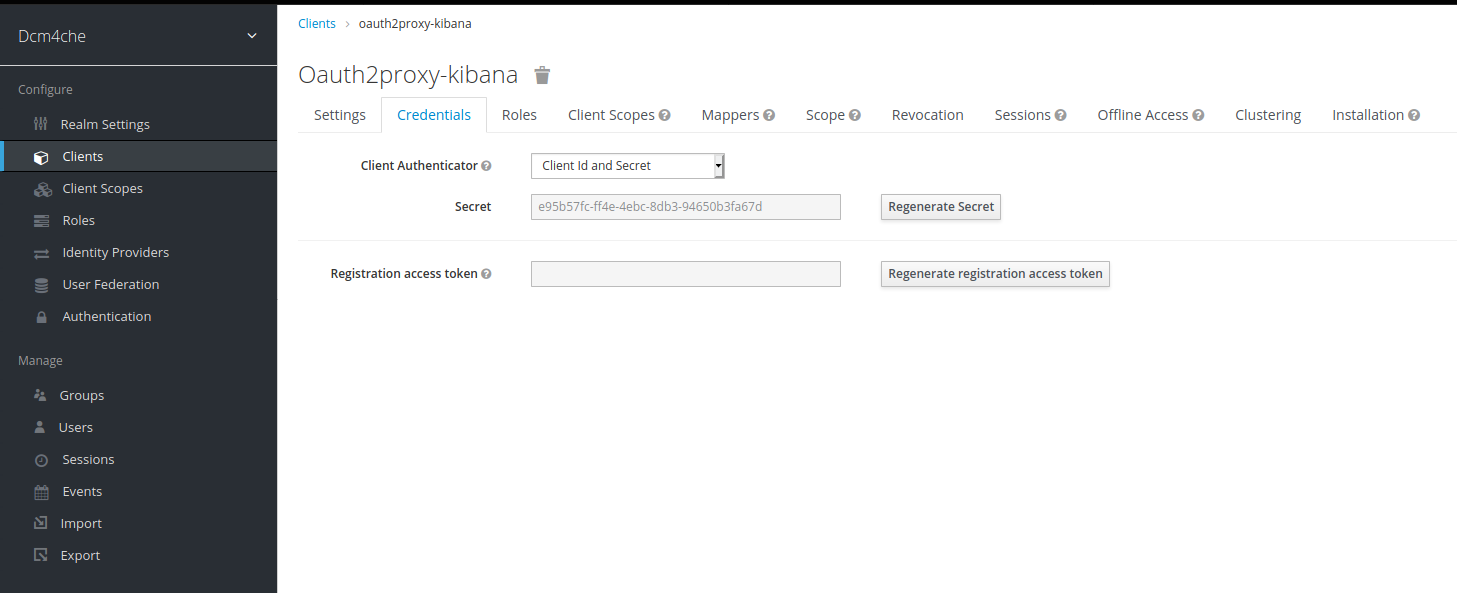
with Audience Token Mapper
audience: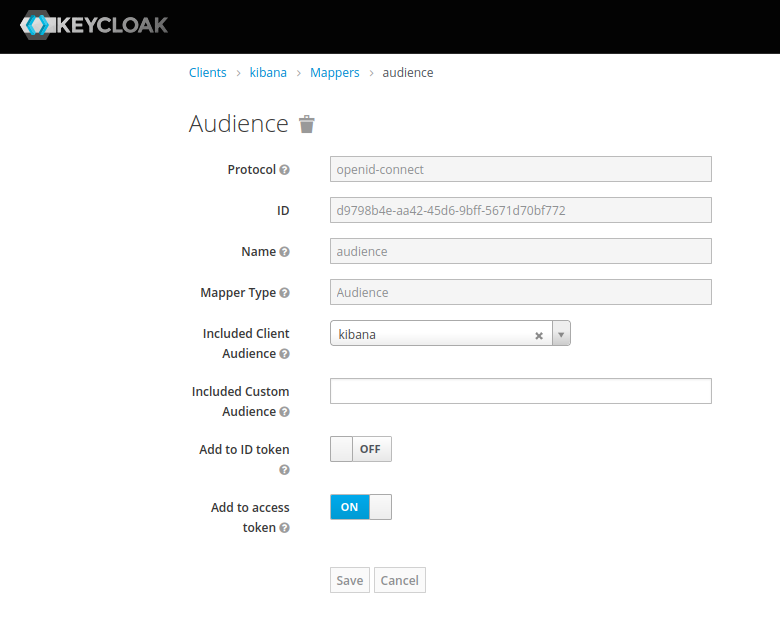
version: "3"
services:
kibana-oauth:
image: dcm4che/oauth2-proxy:7.5.1
ports:
- "8643:8643"
restart: on-failure
environment:
OAUTH2_PROXY_HTTPS_ADDRESS: 0.0.0.0:8643
OAUTH2_PROXY_PROVIDER: keycloak-oidc
OAUTH2_PROXY_SKIP_PROVIDER_BUTTON: "true"
OAUTH2_PROXY_UPSTREAMS: "http://kibana:5601"
OAUTH2_PROXY_OIDC_ISSUER_URL: "https://<docker-host>:8843/realms/dcm4che"
OAUTH2_PROXY_REDIRECT_URL: "https://<docker-host>:8643/oauth2/callback"
OAUTH2_PROXY_ALLOWED_ROLES: auditlog
OAUTH2_PROXY_CLIENT_ID: kibana
OAUTH2_PROXY_CLIENT_SECRET: changeit
OAUTH2_PROXY_EMAIL_DOMAINS: "*"
OAUTH2_PROXY_OIDC_EMAIL_CLAIM: "preferred_username"
OAUTH2_PROXY_INSECURE_OIDC_ALLOW_UNVERIFIED_EMAIL: "true"
OAUTH2_PROXY_COOKIE_SECRET: T0F1dGhLaWJhbmFUZXN0cw==
OAUTH2_PROXY_SSL_INSECURE_SKIP_VERIFY: "true"
OAUTH2_PROXY_TLS_CERT_FILE: /etc/certs/cert.pem
OAUTH2_PROXY_TLS_KEY_FILE: /etc/certs/key.pem
OAUTH2_PROXY_CUSTOM_TEMPLATES_DIR: /templates
depends_on:
- keycloak
Note :
-
OAUTH2_PROXY_OIDC_ISSUER_URL: "https://<docker-host>:8843/realms/dcm4che"applies only for Keycloak v18.0+ and if default KC_HTTP_RELATIVE_PATH is used. -
If lower versions of Keycloak are used or if KC_HTTP_RELATIVE_PATH is set to
/authfor Keycloak v18.0+, thenOAUTH2_PROXY_OIDC_ISSUER_URL: "https://<docker-host>:8843/auth/realms/dcm4che" -
OAUTH2_PROXY_TLS_CERT_FILEandOAUTH2_PROXY_TLS_KEY_FILEspecifies path to TLS certificate and private key in Privacy-Enhanced Mail (PEM) format to use for TLS support. To avoid the security warning of Web Browsers connecting to Kibana via OAuth2 Proxy, replace the certificate provided in/etc/certs/cert.pemof the docker image:
by a certificate whose Common Name and/or Subject Alt Name matches the host name and which is signed by a trusted issuer; bind mount the PEM files with the certificate and corresponding private key and adjust
OAUTH2_PROXY_TLS_CERT_FILEandOAUTH2_PROXY_TLS_KEY_FILEto refer their paths inside of the container.-
OAUTH2_PROXY_PROVIDERspecifies the OAuth provider. -
OAUTH2_PROXY_CLIENT_ID=kibana- specifies the Client ID used to authenticate to the Keycloak Server, -
OAUTH2_PROXY_CLIENT_SECRET=<kibana-client-secret>- specifies the Client Secret used to authenticate to the Keycloak Authentication Server for Confidential type kibana client. The value should match with that used during keycloak container startup. -
OAUTH2_PROXY_UPSTREAMSspecifies Kibana http URLhttp://kibana:5601as upstream endpoint. -
OAUTH2_PROXY_REDIRECT_URLspecifies the redirection URL for the Keycloak Authentication Server callback URL. -
OAUTH2_PROXY_OIDC_ISSUER_URLspecifies OpenID Connect issuer URL, wherein (8843) port refers toKC_HTTPS_PORTused on Keycloak container startup -
OAUTH2_PROXY_ALLOWED_ROLES=auditlog- (keycloak-oidc) restrict logins to members of these roles (may be given multiple times) -
OAUTH2_PROXY_EMAIL_DOMAINSas*specifies to authenticate any email. -
OAUTH2_PROXY_OIDC_EMAIL_CLAIM="preferred_username"which OIDC claim contains the user's email (default "email") -
OAUTH2_PROXY_INSECURE_OIDC_ALLOW_UNVERIFIED_EMAIL="true"specifies to not fail if an email address in an id_token is not verified -
OAUTH2_PROXY_COOKIE_SECRETspecifies the seed string for secure cookies (optionally base64 encoded). -
OAUTH2_PROXY_SSL_INSECURE_SKIP_VERIFYastrueskip validation of certificates presented when using HTTPS providers. Alternatively, one may setOAUTH2_PROXY_PROVIDER_CA_FILES: /etc/certs/cacert.pemif certificate is to be validated using an authorized CA. -
OAUTH2_PROXY_SKIP_PROVIDER_BUTTONis optional. If set totrue, it will skip sign-in-page specifyingSign-on with Keycloakand directly show the Keycloak login page. -
OAUTH2_PROXY_CUSTOM_TEMPLATES_DIRspecifies the custom templates' directory location which contains the customized forbidden error page shown to unauthorized users on authentication. Note : OAuth2 proxy does not yet have a mechanism to only customize one of the templates (i.e. sign_in or error). Hence, if one wants to customize only one, both templates need to be still provided.
-
Note : Replace <docker-host> by the hostname of the docker host, which must be resolvable by your DNS server.
-
Access
https://<docker-host>:8643. After accepting and proceeding with the certificate security warnings, this should redirect to Keycloak login page. -
Login with the desired user credentials.
-
On successful authentication the Kibana home page is displayed.