Hash the passwords you store in the database by Tess - daoneandonly/backend-a2 GitHub Wiki
Hash the passwords you store in the database
You can compare storing passwords in cleartext as the equivalent of writing them down on a digital piece of paper. If passwords are stored this was an attacker would have easy acces these passwords and to each user account in the database. This is a big problem if you look at the fact that a lot of these users re-use or use variations of a single password, potentially allowing the attacker to access other services different from the one being compromised. So what can be done about it? The answer is hashing the users password. This means that a password is stored into data that cannot be converted back to the original password.
What is hashing about?
If you look at the dictionary definition, hashing means "chopping something into small pieces" to make it look like a "confused mess". You could say this applies to hashing a password. In cryptography, a hash function is a mathematical algorithm that maps data of any size to a bit string of a fixed size. We can refer to the function input as message or simply as input. The fixed-size string function output is known as the hash or the message digest (Auth0, 2018).
Hash functions that are used in cryptography have the following key properties:
• It's easy and practical to compute the hash, but "difficult or impossible to re-generate the original input if only the hash value is known." • It's difficult to create an initial input that would match a specific desired output. Thus, in contrast to encryption, hashing is a one-way mechanism. The data that is hashed cannot be practically "unhashed".
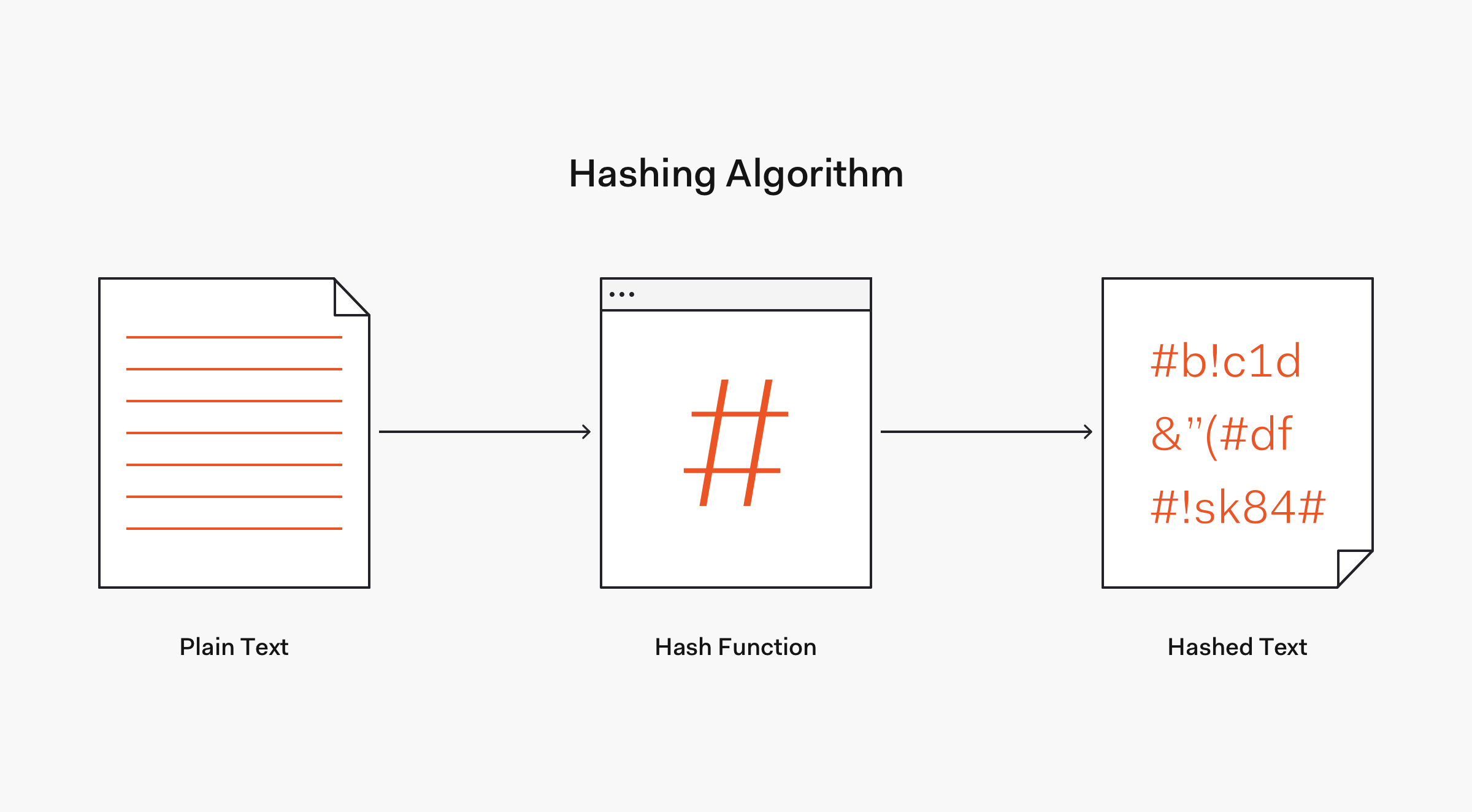
Limitations of Hash Functions
It may seem like hashing is robust, but if an attacker tries to steal the users passwords, and ends up with the hashed passwords, all that the attacker can see is data that is randomly generated and can't be reversed to plaintext due to the architecture of hash functions. An attacker would need to provide an input to the hash function to create a hash that could then be used for authentication, which could be done offline without raising any red flags on the server. The attacker could then either steal the cleartext password from the user through modern phishing and spoofing techniques or try a brute force attack where the attacker inputs random passwords into the hash function until a matching hash is found.
A brute-force attack is largely inefficient because the execution of hash functions can be configured to be rather long. But does the attacker have any other options?
Hashing is used for this project to protect the passwords of our users. We have used the npm package bcrypt to include the hashing.
Bronvermelding
Hash the passwords you store in the database
Arias, D. (2019, 30 september). Hasing Passwords: One Way Road to Security. Geraadpleegd op 26 maart 2020, van https://auth0.com/blog/hashing-passwords-one-way-road-to-security/
Foto:
Arias, D. (2019). Hashing [Foto]. Geraadpleegd op 27 maart 2020, van https://auth0.com/blog/hashing-passwords-one-way-road-to-security/