Home - cmlh/Maltego-haveibeenpwned GitHub Wiki
Maltego Integration
"Have I Been Pwned?"
Supported API Endpoints
"Have I Been Pwned?"
API v3
All haveibeenpwned API v3 endpoints are supported that integrate with [Maltego] entities and includes the following:
-
All breaches for an account i.e. e-mail address and alias, with and without the
truncateResponseparameter. -
Getting all breached sites in the system, with and without the
domainparameter.
Rate Limit
The rate limit of the following of haveibeenpwned API v3 endpoints are supported:
-
All breaches for an account i.e. e-mail address and alias.
Domain Search
The Domain Search Transforms require a @HaveIBeenPwned API Key:
Stealer Logs
The Stealer Log Transforms require a @HaveIBeenPwned "Pwned 5" API Key:
Pwned Passwords
API v2
The Searching by Range API endpoint is supported.
Further information from @troyhunt is published on his Blog [Post] and prior Tweet by @troyhunt.
Rate Limit
There is no rate limit for the API v3 endpoint.
Pwned Passwords List
The latest Version 8 of Pwned Passwords List is supported.
HTTP Status Codes
The following HTTP Status Codes of API v3 are supported:
400 "Bad Request"i.e. the e-mail address does not conform to RFC 822.401 "Unauthorized"i.e. the API key provided was not valid403 "Forbidden"i.e. no user agent has been specified in the request.404 "Not Found"i.e. the e-mail address or alias has not been breached or [the e-mail address is not] listed in a Paste.429 "Too Many Requests"i.e. the rate limit has been exceeded523 "Service Unavailable"i.e. These defences include blocks or JavaScript challenges by Cloudflare
Acceptable Use
It is possible to violate the "Querying the data for purposes that are intended to cause harm to the victims of data breaches" of the Acceptable Use policy.
@troyhunt can be reached for clarification at https://www.troyhunt.com/contact/
License
The Creative Commons Attribution 4.0 International License of haveibeenpwned is supported.
Maltego
Installation
The Maltego Transform Hub is the preferred installation method for end users with Maltego clients from v3.6 "Chlorine" release and onwards, including the "CE" (Community Edition), "Classic" and "XL" of "m4".
The Maltego Transform Hub does not install Maltego-Configuration-HIBP.mtz and consequently this has to be manually imported into Maltego.
End users with Maltego clients prior to the v3.6 "Chlorine" release, i.e. v3.3 "Radium", v3.4 "Tungsten" and v.3.5 "Carbon" are no longer supported due to the rotation of the X.509 Certificate in these versions [of the Maltego clients].
Maltego Transform Hub
The haveibeenpwned Maltego integration can be installed with the Maltego Transform Hub by dragging the mouse over and then clicking the "Install" button as per the following screenshot of the Maltego Client User Interface (UI):
Maltego Configuration Files
The Maltego Configuration Files are available on GitHub as Maltego-Configuration-haveibeenpwned.mtz and Maltego-Configuration-HIBP.mtz
Maltego Configuration
Entities
Custom Entities
The "Link Analysis" cmlh.linkAnalysis hidden entity is added to support the Not Found, Verified Breach, DataClasses et al flags.
The "Error" cmlh.error hidden entity is added to support error messages from @haveibeenpwned API.
The "Breach" haveibeenpwned.breach entity is added to support "Getting a single breached site".
Transform Seed
The Maltego Transform Seed is hosted at https://cetas.paterva.com/TDS/runner/showseed/haveibeenpwned and https://cetas.paterva.com/TDS/runner/showseed/HIBP
Transforms
All haveibeenpwned API v3 endpoints are supported that are applicable to Maltego Entities and include the following:
- From "Breach"
haveibeenpwned.breachTo "Domain"maltego.Domain - From "Alias"
maltego.AliasToBreaches for Account v3 - From "E-mail Address"
maltego.EmailAddressToBreaches for Account v3 - From "E-mail Address"
maltego.EmailAddressToPastes v3 - From "Breach"
breach.NameGetting a single breached site v3 - From "Domain"
maltego.DomainToGetting all breached sites in the system v3
Transform Set
The Maltego Transforms for haveibeenpwned belong to the Breached Transform Set which features concurrent execution of the Maltego Transforms Pastes @haveibeenpwned API v3 endpoint and Breached [E-mail] Account of the @haveibeenpwned API v3 endpoints.
The Maltego Transforms for "Stealer Logs" belong to the Transform Set
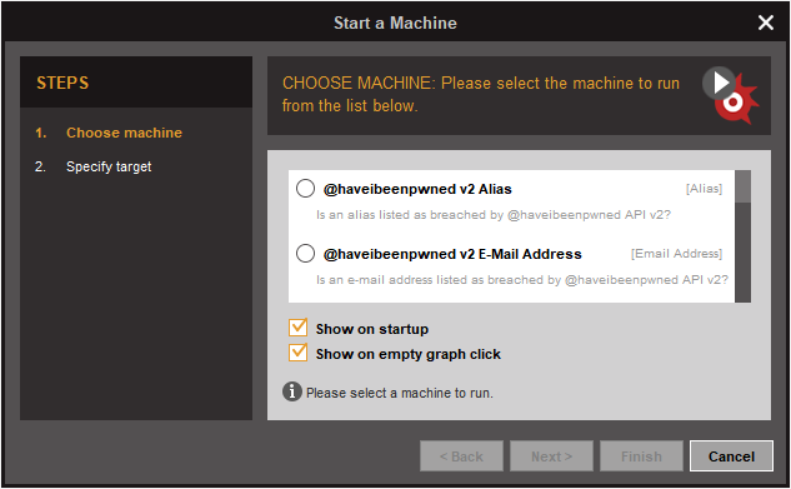
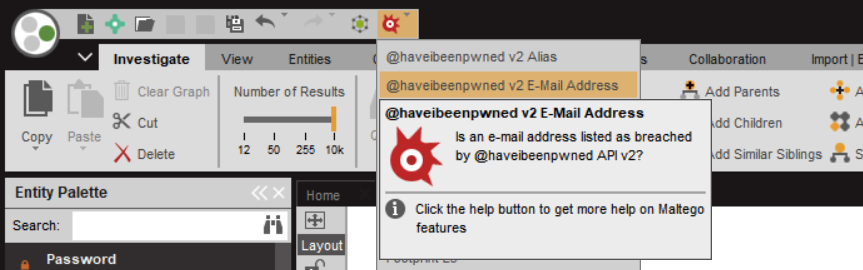
Machines
There are two Maltego Machines labelled haveibeenpwned v3 and the difference is their Maltego Input Entity i.e. "Alias" maltego.Alias and "E-mail Address" maltego.EmailAddress.
User Interface (UI) Messages
All Maltego Transforms
"@haveibeenpwned is licensed under Creative Commons Attribution 4.0 International"
"All breaches for an account" Maltego Transform
"[Int] breached accounts added to haveibeenpwned for [String]"
"All pastes for an e-mail address" Maltego Transform
"[Int] e-mail addresses extracted by @haveibeenpwned for [String]"
Display Information
haveibeenpwned Deep Links are inserted into each "E-mail Address" and "Alias" entity.
haveibeenpwned Pwned Websites are inserted into each "Domain" entity.
haveibeenpwned Creative Commons Attribution 4.0 International License is inserted to each returned Maltego Entity.
Bookmarks
Errors
OrangePurple - E-mail address not RFC 822 conformantOrangePurple - Exceeded Rate Limit of APIOrangePurple - NoUser-AgentRequest Header specifiedOrangePurple - Unicode Encoding Error
"Have I been pwned?"
- Red - Retired breach
- Red - Sensitive breach
- Red - Verified breach
OrangePurple - No Domain for Breach [Name]- Yellow - Fabricated breach
- Yellow - Spam list
- Yellow - Unverified breach
Green - E-mail address not found in pastesGreen - No breach recorded
Links
"Have I been pwned?"
- Red - Retired breach
- Red - Sensitive breach
- Red - Verified breach
- Yellow - Fabricated breach
- Yellow - Spam list
- Yellow - Unverified breach
Green - E-mail address not found in pastesGreen - No breach recorded
Recommended Workflow
"Have I Been Pwned?"
The haveibeenpwned Maltego Machines follow these approaches.
API v3
- Select all "Alias"
maltego.AliasMaltego Entities and execute theBreached Alias v3Maltego Transform. - Select all "E-mail Address"
maltego.EmailAddressMaltego Entities and execute theBreached E-mail v3Maltego Transform. - Select all "E-mail Address"
maltego.EmailAddressMaltego Entities and execute thePastes v3Maltego Transform. - Select all "Domain"
maltego.DomainMaltego Entities and execute theGetting all breached sites in the system v3Maltego Transform. - Select all "Breach"
haveibeenpwned.breachMaltego Entities and execute theGetting a single breached site v3Maltego Transform. - Select The Red,
Greenand Yellow Bookmarks.
The Convert Breach to Domain v3 Maltego Transform is not executed above as the Domain is already returned by the Getting all breached sites in the system v3 Maltego Transform.
"Pwned Passwords"
API v2
- Select all "Hash"
maltego.HashMaltego Entities and execute thev3 What is the k-anonymity of SHA-1 Hash?Maltego Transform. - Click the "Ball size by Weight"
Example Graphs
The Maltego-Graphs directory contains the following:
- Historical test data from the @haveibeenpwned API v1 and v2 web pages.
- All
Breachentities at the time that represent the Pwned Websites web page on @haveibeenpwned
Both the newer m4 mtgx and older 3 file formats are supported.mtgl
Uptime Status
The uptime status web page has been published at https://stats.uptimerobot.com/GMwJ3hYMY