Lesson 08 - chad-p/wiki-linux-class GitHub Wiki
Network Security
iptables
Plus:
- Its been around a long time so lots of documentation
- easy to script
- pre-installed on many distros (may be turned off)
- lots of flexability
Neg:
- ipv6 requires separate rules
- adding new rules requires entire ruleset to be reloaded
- Tables: Join similar actions, can consist of several chains
- Main
- Filter - Default (packet filtering)
- NAT - Nat rules
- Mangle - Modify IP headers such as TTL
- Other
- Raw - Connection tracking (mark packets)
- Security - SELinux controls
- Main
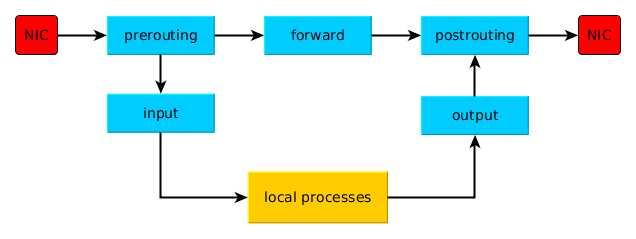
- Chains: Is a set of rules. Not all chains are available for all tables
- Pre-Routing - Receiving incoming packet
- Input - default policy is accept
- Forward
- Output
- Post-Routing
- Rules: Commands to manipulate network traffic

sudo iptables -nL View Chains
sudo iptables -t mangle -L View with pre/post route
sudo iptables -S List Rules
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
sudo iptables -L -v --line-numbers More verbose output with line numbers
sudo iptables -D INPUT 1 Remove the 1st rule
sudo iptables -F INPUT Flush (delete all rules) in INPUT chain
On reboot these changes will not be persistent
Easiest way is to download and run iptables-persistent
firewalld
firewall-cmd --state
firewall-cmd --get-default-zone
firewall-cmd --list-all
sudo firewall-cmd --info-service ssh
UFW
sudo ufw status verbose
fail2ban
sudo cp /etc/fail2ban/jail.{conf,local} Make backup copy to local
fail2ban-client -h
fail2ban-client status sshd
jail.local
[sshd]
enabled = true
maxretry = 3
findtime = 1d
bantime = 4w
ignoreip = 127.0.0.1/8 23.34.45.56
- Check out https://www.crowdsec.net/
Logs
- https://www.splunk.com/
- https://www.graylog.org/products/open-source#download-open
- https://www.loggly.com/ultimate-guide/linux-logging-basics/
Enumeration
Fuzzing to find files directories hidden but accessible. Can use tools such as DirBuster or nmap scripts.
SSH Banner
Hide your wives, hide your kids, hide your ssh banners they're hacking everyone up in here.
Wget
wget https://raw.githubusercontent.com/nmap/nmap/master/scripts/http-enum.nse
Curl
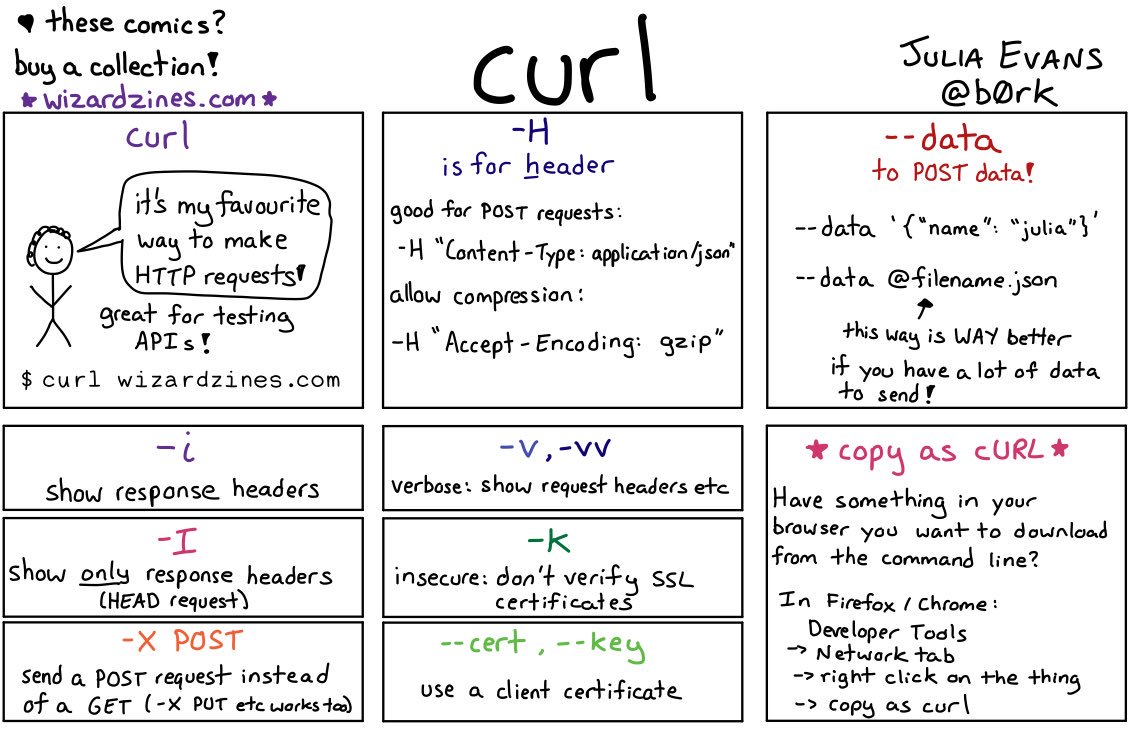
# Get Headers
curl -Is
# Ignore Cert
curl -k
# Follow redirects
curl -L
# Spoof Host Header
curl --verbose --header 'Host: example.com' 192.168.1.10
Download a file
curl -o nifi-1.9.2.zip http://ftp.wayne.edu/apache/nifi/1.9.2/nifi-1.9.2-source-release.zip