Employing ADCS to Secure Network Communications - cfloquetprojects/homelab GitHub Wiki
Introduction
Today we will be installing Active Directory Certificate Services (ADCS) within our lab environment as a means of securing communications between our different networked devices using PKI.
Our main goal of securing these communications is achieved with ACDS using the CIA triad:
- Ensuring the Confidentiality of data through robust encryption
- Maintaining the Integrity of our data using digital signatures and hashes
- Achieving lasting Availability in part by securing our web servers against common attacks and eavesdropping.
Our deployment will consist of two distinct Windows Server 2019 (Desktop) hosts, one being our dedicated
rootcertificate authority (CA), and the other being the designatedissuingCA.
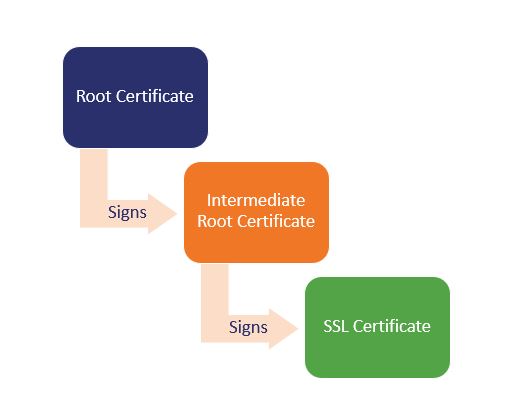
The diagram below describes the process in which we will be using to verify and sign our SSL certificates, with the
rootCA only being turned on (and thus vulnerable to attack) when it is used to sign theintermediate/issuingCA:
Pre-Flight Check:
It's crucial to have completed all 3 of my previous labs covering this topic, as this includes the installation and configuration of the Root CA, Subordinate/Issuing CA, as well as covering the configuration of auto-enrollment for domain-joined computers, which is what we will be using to secure web server communications.
Ensure the domain-joined computer that you will be accessing the local web server from has received it's certificate from the Subordinate CA.
Lastly, it's critical that your Subordinate CA has a tested and working A-record entry on your local DNS server so that clients can connect to it using the name that is on the certificate it was issued.
Configure HTTPS Binding within IIS Manager:
Most of the setup to achieve this has already been completed, with all that's left to do now is simply go into IIS Manager and navigate to the Default Web Site pane and choosing Bindings on the right-hand tab.
#1
Restart your web server from within the Default Web Site page, and then navigate to https://issuingca01.domain.com/certsrv to test both your HTTPS connection as well as your IIS Web Server serving the proper web page. You should be greeted with an authentication page, but then after entering credentials you should see something like the secured page below:
#2
In future labs, we will be adding SSL certificates to secure communications between our clients and many of our web-hosted infrastructure that we use and deploy in other labs, such as
Splunk ES,vCenter,Synology NAS, etc. Keep an eye out for those articles in the future, and thank you for reading this one!