Azure Active Directory - barialim/architecture GitHub Wiki
What is Azure AD?
While they share a similar name, Azure AD is not a cloud version of Windows Server Active Directory. It's also not intended as a complete replacement for an on-premises Active Directory. Instead, if you're already using a Windows AD server, you can connect it to Azure AD to extend your directory into Azure. This approach allows users to use the same credentials to access local and cloud-based resources.
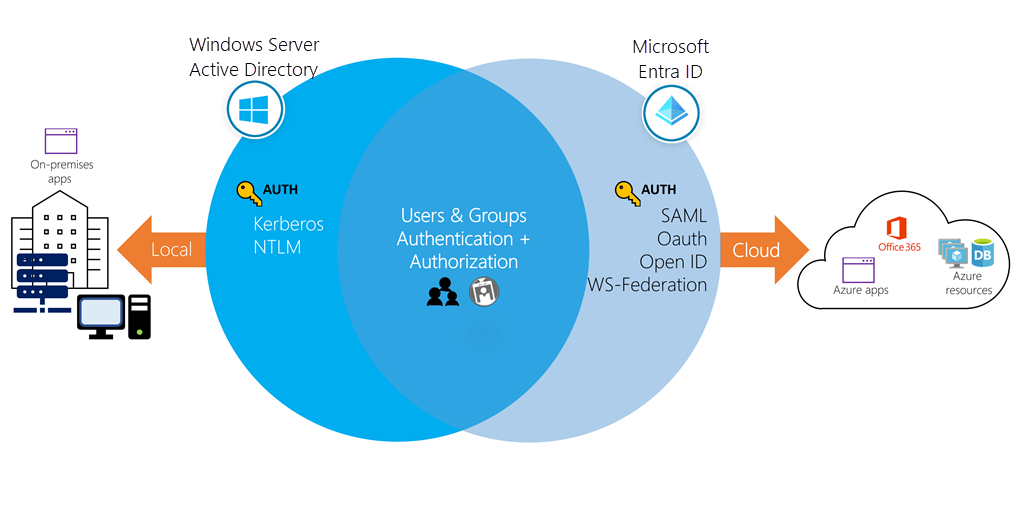
A user can also use Azure AD independently of Windows AD. Smaller companies can use Azure AD as their only directory service to control access to their applications and SaaS products, such as Microsoft 365, Salesforce, and Dropbox.
⚠️ NOTE: Keep in mind that this approach doesn't provide a completely centralized administrative model - for example, local Windows machines would authenticate using local credentials. Users can write applications to use Azure AD and provide authentication and authorization to be administered by a user in a single place.
Directories, subscriptions, and users
Microsoft offers several cloud-based offerings today - all of which can use Azure AD to identify users and control access.
Microsoft Azure Microsoft 365 Microsoft Intune Microsoft Dynamics 365 When a company or organization signs up to use one of these offerings, they are assigned a default directory, an instance of Azure AD.
Reference: R1
Enterprise State Roaming
Enterprise State Roaming (ESR) provides users with a unified experience across their Windows devices and reduces the time needed for configuring a new device.
⚠️ NOTE: Enterprise State Roaming (ESR) can be ONLY enabled for users. If device accounts are in a group for which you enable ESR, device accounts are ignored.
If User1 modifies the desktop background on Computer1, User1 will have the modified background when he is signed in to Computer2. ESR is enabled for Group1, which User1 is member of. Desktop background is one of the settings that is roamed by ESR. Because ESR is enabled for User1, the modified desktop background will be visible on all Windows 10 computers on which User1 signs in. That means that the modified desktop will be used also when User1 signs in to Computer3.
If User2 modifies the desktop background on Computer1, User2 will not have the modified background when he is signed in to Computer2. ESR is not enabled for User2 (or for Group2, which User2 is member of). This means that if User2 performs customization at one computer, those customizations will not roam and will not be used when User2 signs in to a different computer.
Reference: R1
User Principal Name (UPN) suffix
The User Principal Name (UPN) suffix is part of the logon name in AD. When you create a new account, by default it will use the DNS name of your AD domain.
For example: your local domain name is
contoso.localand you want to create a new user. The user that you want to create isBariali Mahmood. The standard in the organization for creating new users is "first.lastnam". The logon name will be[email protected].
❓ What if you want it to be [email protected]?
🅰️ Let's understand before I tell you how to add UPN suffix using GUI/Powershell...
Why do you need a UPN suffix?
- Implementing Office 365 in the organization
- The internal domain is a
contoso.localand you want users to log in withcontoso.comdomain - New software that requires the users UPN to match the user’s email address
Reference: R1
Synchronize specific users with particular UPN suffix
❓You manage an Active Directory domain named contoso.local.
You install Azure AD Connect and connect to an Azure Active Directory (Azure AD) tenant named contoso.com without syncing any accounts.
You need to ensure that only users who have a UPN suffix of contoso.com in the contoso.local domain sync to Azure AD.
🅰️ Solution: Create "Inbound" Direction rule using Synchronization Rules Editor in AD Connect to create a synchronization rule. Filtering what objects are synched to Azure AD is a common request as there're many instances where filtering by OU just doesn't cut it. One option is to filter users by their UPN suffix so that only users with the PUBLIC FQDN as their UPN suffix are synched to Azure AD (e.g. [email protected] would be synced while [email protected] would not).