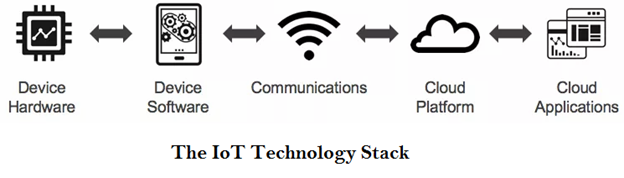
Introduction to IoT - aruna-sukrutha/IoT-on-AWS-Project-2 GitHub Wiki
What is IoT?
As this project is an implementation of IoT Technology, let's know what exactly the term "IoT" means. The "IoT" stands for "Internet of Things" and it is the network of physical devices which incorporates home appliances embedded with electronics,actuators and sensors for the purpose of connecting and exchanging data with other devices and systems over the internet. These devices range from ordinary household objects to sophisticated industrial tools. Connecting everyday things embedded with electronics, software, and sensors to internet enabling to collect and exchange data without human interaction is called as the Internet of Things (IoT). Realtime examples of IoT are Smarthome security systems, wearable health monitors, wireless tracking, biometric cyber security scanning and many more.
Why Is Internet of Things (IoT) so important?
Over the past few years, IoT has become one of the most important technologies of the 21st century. Now that we can connect everyday objects like kitchen appliances, cars, thermostats, baby monitors etc to the internet via embedded devices, seamless communication is possible between people, processes, and things. And also, IoT minimizes human effort, save lot of time, enhance data collection and technology optimization. By means of low-cost computing, the cloud, big data, analytics, and mobile technologies, physical things can share and collect data with minimal human intervention. In this hyperconnected world, digital systems can record, monitor, and adjust each interaction between connected things. The physical world meets the digital world—and they cooperate.
1.1 IoT Devices:
IoT devices are pieces of hardware, such as sensors, actuators, gadgets, appliances, or machines, that are programmed for certain applications and can transmit data over the internet or other networks. They can be embedded into other mobile devices, industrial equipment, environmental sensors, medical devices, and more.
Increasingly, IoT devices are using AI and machine learning to bring intelligence and autonomy to systems and processes, such as autonomous driving, industrial smart manufacturing, medical equipment, and home automation. Many of these devices are small, power- and cost-constrained microcontroller-based systems. Network bandwidth and consumer expectations around data privacy and user experience continue to demand more on-device processing, where data is processed on the IoT endpoint, rather than using cloud-based approaches.
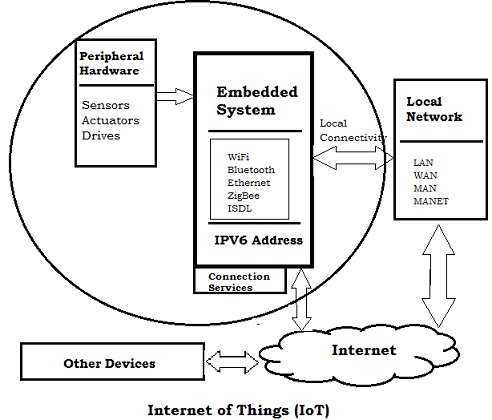
1.2 Communication Protocols used in IoT devices: Whenever we talk about the internet of things, a huge number of devices connected over the internet come to mind. And to let them function well, the communication network between the devices is crucial. This is where protocol makes an entry in the IoT world. IoT communication protocols are modes of communication that ensure optimum security to the data being exchanged between IoT connected devices. The IoT devices can be connected via an IP network or a non-IP network. Though there is a difference in their range, power, and memory used. Connections through IP networks are complex, and take high memory and power from the IoT devices while the range is not a problem. On the other hand, non-IP networks like bluetooth require less memory and power but have a range limitation. Types of IoT Protocols: (a)IoT Network Protocols: IoT network protocols are designed to connect medium to high power devices over the network. IoT network protocols allow data communication within the scope of the network.They are - HTTP, LoRaWAN, bluetooth, zigbee are some of the popular IoT Network protocols. (b)IoT Data Protocols – IoT data protocols are designed to connect low power IoT devices. Without any internet connection, they are capable of providing end-to-end communication with the hardware.They are - MQTT, CoAP, AMQP, M2M Communication protocol, XMPP etc
1.3 Iot Security:
As connected devices continue to increase in number, it is increasingly challenging for enterprises to secure them and keep threats at bay. Fraught with vulnerabilities and offering an attack surface ripe for security breaches, IoT devices are attractive targets for cybercriminals. Whether enterprises are just starting out with IoT adoption or looking to expand their established IoT networks, all face similar challenges when it comes to managing, monitoring and securing their connected IoT environments. Therefore, it becomes important to explore the potentials of IoT protocols and standards, which creates a secure environment. Using these protocols, local gateways and other connected devices can communicate and exchange data with the cloud.
- Employ Device Discovery for Complete Visibility
- Apply Network Segmentation for Stronger Defense
- Adopt Secure Password Practices
- Continue to Patch and Update Firmware When Available
- Actively Monitor IoT Devices at All Times
1.4 Data:
Devices and technology connected over the Internet of Things (IoT) can monitor and measure data in real time, and these data can offer valuable insight to help save time, energy, and money. But, how are IoT data collected, processed, and analyzed? Internal sensors collect data from IoT consumer devices, such as security systems, smart appliances, smart TVs, and wearable health meters. Data are collected from commercial devices, as well, including commercial security systems, traffic monitoring devices, and weather tracking systems. The data are transmitted, saved, and can be retrieved at any time. Below are examples of the types of data that IoT devices collect: Automation data. Many people are skeptical of device automation. Whether it’s automated lights in an office or automatic settings on a thermostat, automation is necessary. Without automation, someone’s job would be remembering to adjust the thermostat settings twice a day, and the last one out turns off all the lights. Status data. The most basic and prevalent type of IoT data is status data. Most IoT devices generate status data, which are collected as raw data, and then used for more complex analysis. Location data. Think of location data as an indoor global positioning system: Rather than directing you to a specific destination, location data enable you to track packages, pallets, and equipment in real time. Farmers can track equipment during the harvest. A warehouse supervisor can find a specific pallet of parts on the shop floor. At the consumer level, you can use location data to track a lost phone, laptop, or even your keys. Processing IoT Data - The massive amount of data that IoT sensors and devices generate must be processed before the information can be used. However, because the data often come from numerous devices or in different formats, there are several things you must do before processing or applying any type of analytics to the data: · Standardize or transform the data to a uniform format, ensuring that that format is compatible with your application. · Store or create a backup of the newly transformed format. · Filter any repetitive, outdated, or unwanted data to help improve accuracy. · Integrate additional structured (or unstructured) data from other sources to help enrich your current data set.