Getting OIDC Access Token using curl - amsalama/dcm4chee-arc-light GitHub Wiki
Sign in with User/Password admin/admin at the Realm Admin Console of Keycloak at
https://<host>:<port>/admin/<realm>/console - you have to replace <host> by the host name and <port> by
the https port of the keycloak server and <realm> by the realm name.
Note :
-
https://<host>:<port>/admin/<realm>/consoleapplies only for Keycloak v18.0+ and if default KC_HTTP_RELATIVE_PATH is used. - If lower versions of Keycloak are used or if KC_HTTP_RELATIVE_PATH
is set to
/authfor Keycloak v18.0+, thenhttps://<host>:<port>/auth/admin/<realm>/console
Create an OIDC client with curl as Client ID
and change the default values for Access Type and Service Accounts Enabled in the client Settings tab:

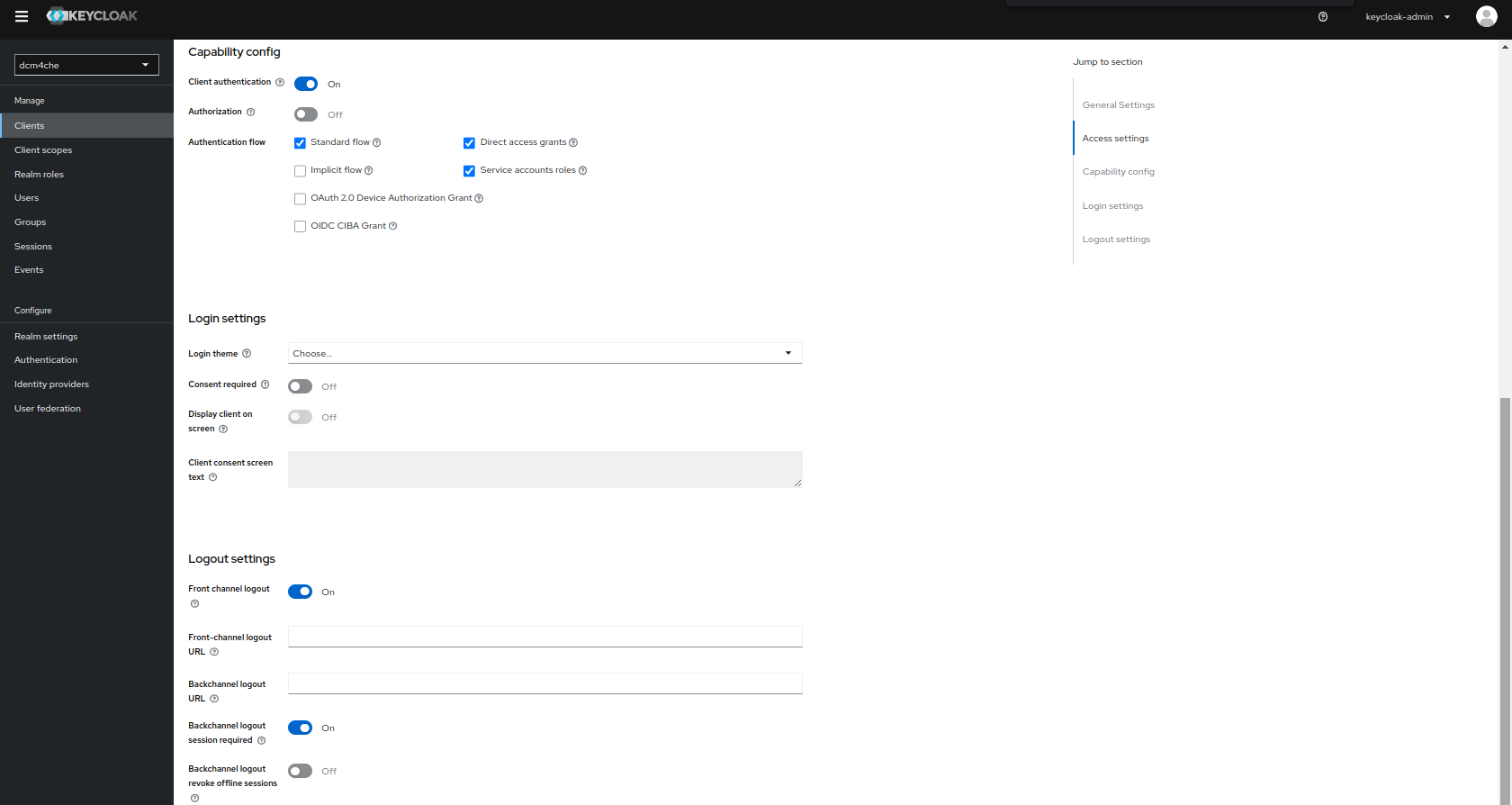
You have to Save the changes before adding the Role user in the Service Account Roles tab:
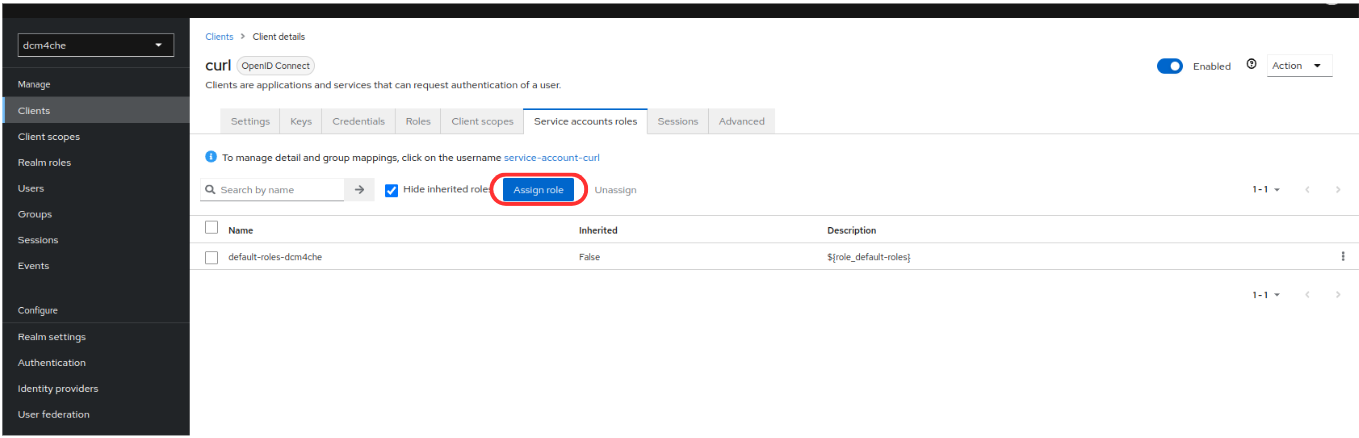
and store the Secret from the Credentials tab:
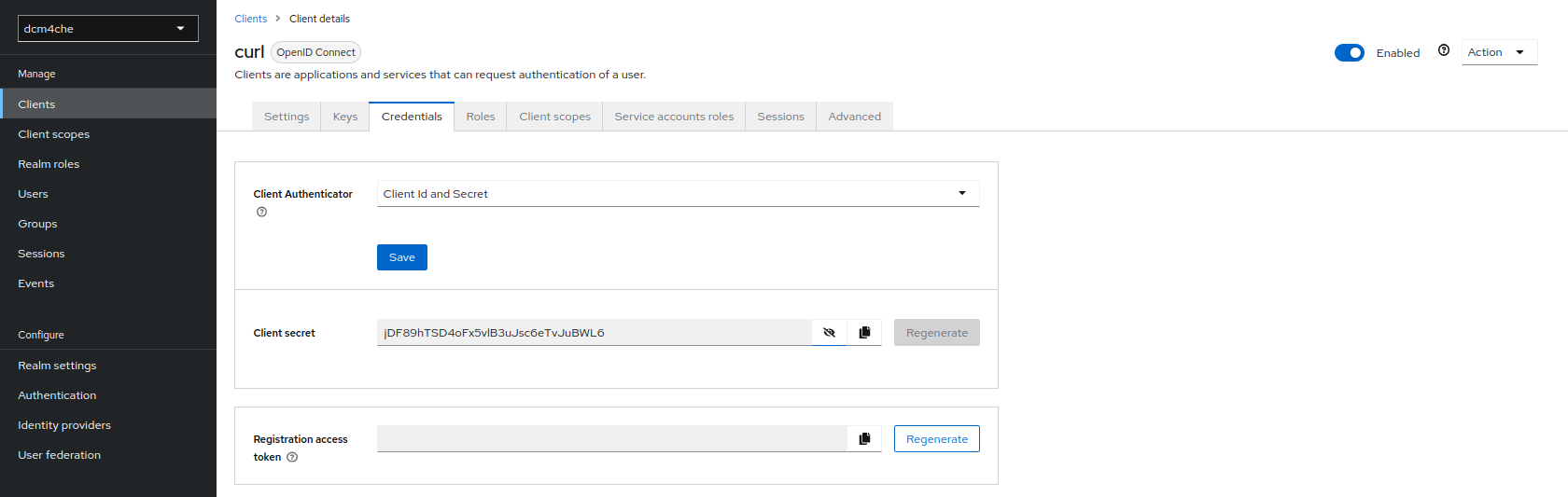
for later use.
Request an access token using OAuth 2.0 Client Credentials Grant
$ RESULT=`curl -k --data "grant_type=client_credentials&client_id=curl&client_secret=dfefe9a3-7781-439a-b37f-74de0db03b11" https://test-ng:8843/realms/dcm4che/protocol/openid-connect/token`
$ echo $RESULT | python -m json.tool
{
"access_token": "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJfUjZJWXNHdGdad2dkMDBMdHFRVnRBYlRmOVJTLWxGNUtJUVNBalBGcjVnIn0.eyJqdGkiOiI2N2QyMmQ0My0zMjQ2LTRhYWMtOWEwNi1lZDNlZWVkYmNkYmUiLCJleHAiOjE1Mjg3OTczNzgsIm5iZiI6MCwiaWF0IjoxNTI4Nzk3MDc4LCJpc3MiOiJodHRwczovL3Rlc3Qtbmc6ODg0My9hdXRoL3JlYWxtcy9kY200Y2hlIiwiYXVkIjoiY3VybCIsInN1YiI6ImVmNjRlYjRlLTBhNmQtNGYxMy1iZjQ0LWI2YjQxZWI5YTQ1ZiIsInR5cCI6IkJlYXJlciIsImF6cCI6ImN1cmwiLCJhdXRoX3RpbWUiOjAsInNlc3Npb25fc3RhdGUiOiIyMzNkNDAyYy05YmIwLTRjM2YtOGNmMy1mYjAwNTFjMjNhNGYiLCJhY3IiOiIxIiwiYWxsb3dlZC1vcmlnaW5zIjpbXSwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbInVtYV9hdXRob3JpemF0aW9uIiwidXNlciJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sImNsaWVudEhvc3QiOiIxOTIuMTY4LjIuMTc4IiwiY2xpZW50SWQiOiJjdXJsIiwicHJlZmVycmVkX3VzZXJuYW1lIjoic2VydmljZS1hY2NvdW50LWN1cmwiLCJjbGllbnRBZGRyZXNzIjoiMTkyLjE2OC4yLjE3OCIsImVtYWlsIjoic2VydmljZS1hY2NvdW50LWN1cmxAcGxhY2Vob2xkZXIub3JnIn0.BdtmOKJNi-wzFBy-FUZu6_zRlukU81-yoXGl4YomEXMTLkK4AaUIsBO2Y3LjWt5vDbrki6RXZXNFbTEkDJMsMKXzur_xxAq5PzNE6q0QyEaTttsfrVETuzZMsU9r5Z0dfVSMIdAnpG7qgWMzETj2E9tOuZN1Mn7X8JRl6qQC0RLvl_TZcuRLElHoZbpvs2HiVRYkIhiG9Gn89cc6LT02wXdeGMccNx4jEyCY_YKhKsT6QNfzKmAKtiYdSF_arhlF6rlIf_HcCDjUIkgSQ_bY0LF5tA6FvEM2stCjO2YPjeVU2WrmQOYJyQ1FyvswiGBx2tutE-yLYdEmYwJknF2JuQ",
"expires_in": 300,
"not-before-policy": 1525366513,
"refresh_expires_in": 1800,
"refresh_token": "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJfUjZJWXNHdGdad2dkMDBMdHFRVnRBYlRmOVJTLWxGNUtJUVNBalBGcjVnIn0.eyJqdGkiOiI1MDQxNDQ1Yi01YWQ1LTRhYWUtODNlZS0yNzY3OTUxYWZkODYiLCJleHAiOjE1Mjg3OTg4NzgsIm5iZiI6MCwiaWF0IjoxNTI4Nzk3MDc4LCJpc3MiOiJodHRwczovL3Rlc3Qtbmc6ODg0My9hdXRoL3JlYWxtcy9kY200Y2hlIiwiYXVkIjoiY3VybCIsInN1YiI6ImVmNjRlYjRlLTBhNmQtNGYxMy1iZjQ0LWI2YjQxZWI5YTQ1ZiIsInR5cCI6IlJlZnJlc2giLCJhenAiOiJjdXJsIiwiYXV0aF90aW1lIjowLCJzZXNzaW9uX3N0YXRlIjoiMjMzZDQwMmMtOWJiMC00YzNmLThjZjMtZmIwMDUxYzIzYTRmIiwicmVhbG1fYWNjZXNzIjp7InJvbGVzIjpbInVtYV9hdXRob3JpemF0aW9uIiwidXNlciJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX19.na8T4VGZ3wsj_Qlu0hI9tpp6Gf8LCt6Lwsu5-trIxE6E6-C6bEt1yYwiDEnJCU9L423_uEtNG8PIF_03iJwxlG_5Xdq-wi5djx3RiQHoSXgCINsHW8hNNmwy0RG1o8ubV3SgSFM7gS6zR6VSh1wEjh5XJIcgDBbPP4gzMKik_MEj6X64WnSoWjSOwYNgcAdlFpJMlig1E9W0MJooROSPC92PJWTMeFvFnTouYeuKAH-Z-jsRI8D66eTFMEnpyqB-VsXt6eoJClyYyvzul21LBXZPxX8tEjkdclX07PFANUbq1Kl8qW0DElusLRwKmKoBt2DDAxg1AavXvGb3HE36Ig",
"session_state": "233d402c-9bb0-4c3f-8cf3-fb0051c23a4f",
"token_type": "bearer"
}Note :
-
https://test-ng:8843/realms/dcm4che/protocol/openid-connect/tokenapplies only for Keycloak v18.0+ and if default KC_HTTP_RELATIVE_PATH is used. - If lower versions of Keycloak are used or if KC_HTTP_RELATIVE_PATH
is set to
/authfor Keycloak v18.0+, thenhttps://test-ng:8843/auth/realms/dcm4che/protocol/openid-connect/token
$ TOKEN=`echo $RESULT | sed 's/.*access_token":"\([^"]*\).*/\1/'`
$ curl -H "Authorization: Bearer $TOKEN" http://test-ng:8080/dcm4chee-arc/aets/DCM4CHEE/rs/studies?StudyInstanceUID=1.3.6.1.4.1.5962.99.1.939772310.1977867020.1426868947350.4.0
:Inspect the included JSON Web Token (JWT)
$ JWT=`echo $RESULT | sed 's/[^.]*.\([^.]*\).*/\1/'`
$ echo $JWT | base64 -d | python -m json.tool
base64: invalid input
{
"acr": "1",
"allowed-origins": [],
"aud": "curl",
"auth_time": 0,
"azp": "curl",
"clientAddress": "192.168.2.178",
"clientHost": "192.168.2.178",
"clientId": "curl",
"email": "[email protected]",
"exp": 1528797378,
"iat": 1528797078,
"iss": "https://test-ng:8843/realms/dcm4che",
"jti": "67d22d43-3246-4aac-9a06-ed3eeedbcdbe",
"nbf": 0,
"preferred_username": "service-account-curl",
"realm_access": {
"roles": [
"uma_authorization",
"user"
]
},
"resource_access": {
"account": {
"roles": [
"manage-account",
"manage-account-links",
"view-profile"
]
}
},
"session_state": "233d402c-9bb0-4c3f-8cf3-fb0051c23a4f",
"sub": "ef64eb4e-0a6d-4f13-bf44-b6b41eb9a45f",
"typ": "Bearer"
}