Tutorial: Connect virtual networks with virtual network peering using the Azure portal - abhi0751/Blogimages GitHub Wiki
You can connect virtual networks to each other with virtual network peering. These virtual networks can be in the same region or different regions (also known as Global VNet peering). Once virtual networks are peered, resources in both virtual networks can communicate with each other, with the same latency and bandwidth as if the resources were in the same virtual network. In this tutorial, you learn how to:
- Create two virtual networks
- Connect two virtual networks with a virtual network peering
- Deploy a virtual machine (VM) into each virtual network
- Communicate between VMs
If you prefer, you can complete this tutorial using the Azure CLI or Azure PowerShell.
Before you begin, you need an Azure account with an active subscription. If you don't have one, you can create an account for free.
- Sign in to the Azure portal.
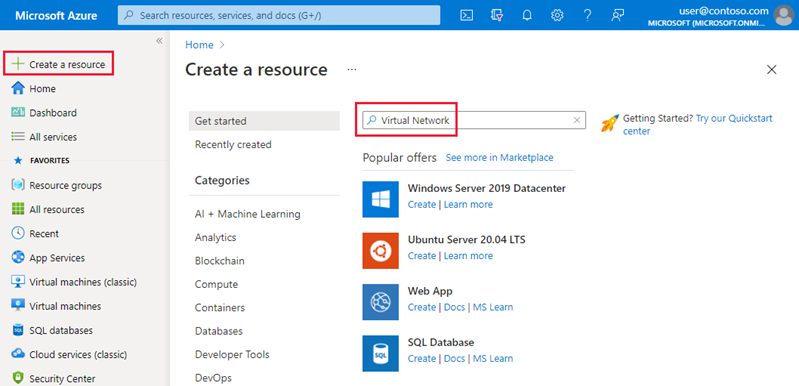
- On the Azure portal, select + Create a resource.
- Search for Virtual Network, and then select Create.
- On the Basics tab, enter or select the following information and accept the defaults for the remaining settings:
TABLE 1 Setting Value Subscription Select your subscription. Resource group Select Create new and enter myResourceGroup. Region Select East US. Name myVirtualNetwork1 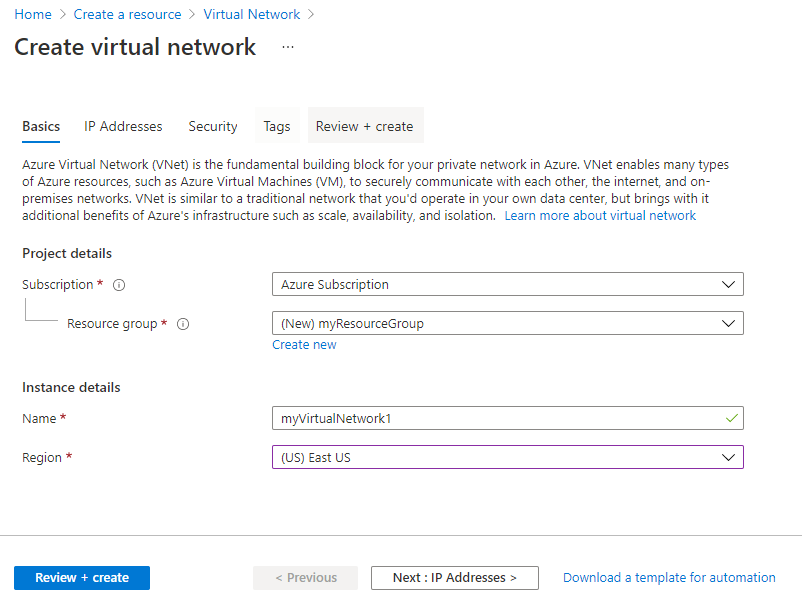
- On the IP Addresses tab, enter 10.0.0.0/16 for the Address Space field. Click the Add subnet button below and enter Subnet1 for Subnet Name and 10.0.0.0/24 for the Subnet Address range.
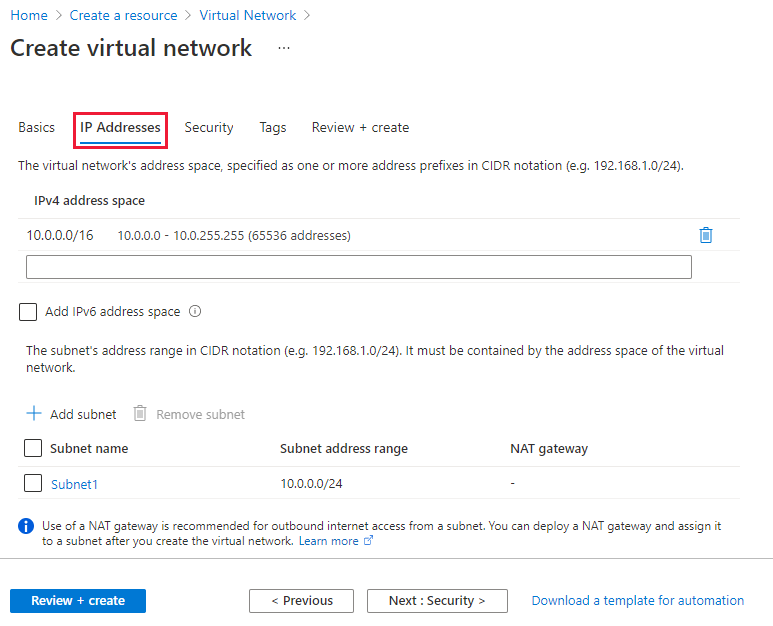
- Select Review + create and then select Create.
- Repeat steps 1-5 again to create a second virtual network with the following settings:
TABLE 2 Setting Value Name myVirtualNetwork2 Address space 10.1.0.0/16 Resource group Select Use existing and then select myResourceGroup. Subnet name Subnet2 Subnet address range 10.1.0.0/24
- In the search box at the top of the Azure portal, look for myVirtualNetwork1. When myVirtualNetwork1 appears in the search results, select it.
- Select Peerings, under Settings, and then select + Add, as shown in the following picture:
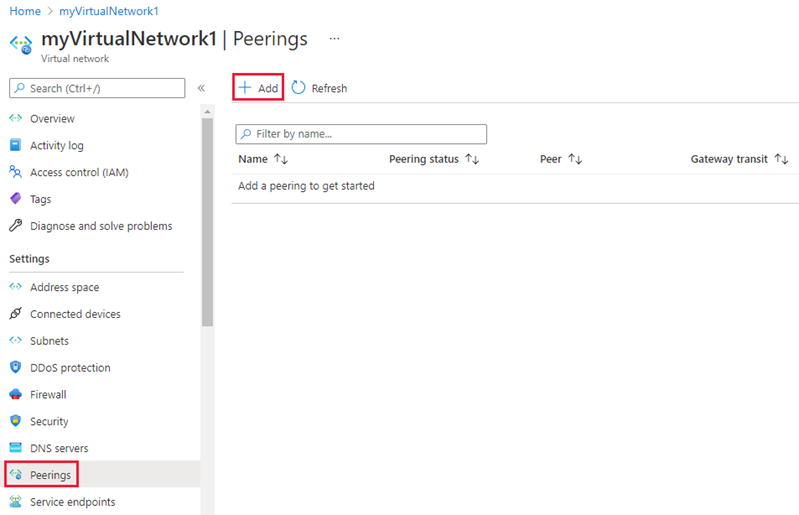
- Enter, or select, the following information, accept the defaults for the remaining settings, and then select Add.
TABLE 3 Setting Value This virtual network - Peering link name Name of the peering from myVirtualNetwork1 to the remote virtual network. myVirtualNetwork1-myVirtualNetwork2 is used for this connection. Remote virtual network - Peering link name Name of the peering from remote virtual network to myVirtualNetwork1. myVirtualNetwork2-myVirtualNetwork1 is used for this connection. Subscription Select your subscription. Virtual network You can select a virtual network in the same region or in a different region. From the drop-down select myVirtualNetwork2 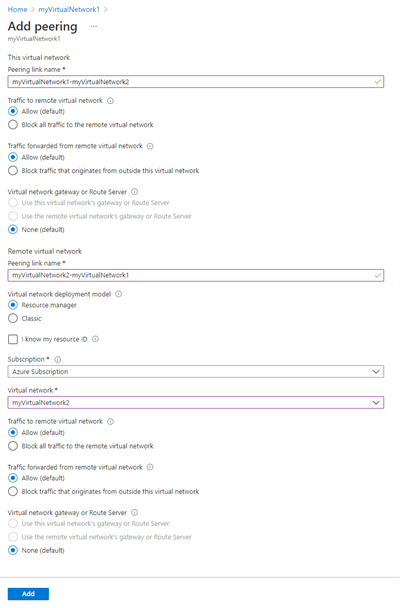 The PEERING STATUS is Connected, as shown in the following picture:
The PEERING STATUS is Connected, as shown in the following picture: 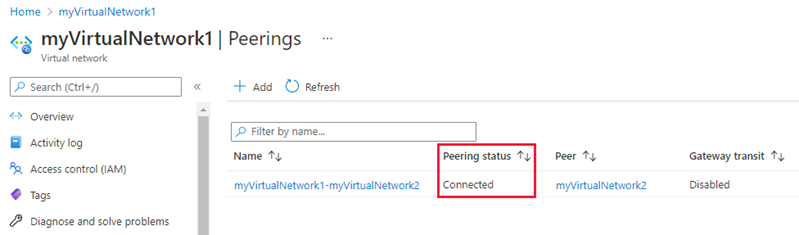 If you don't see a Connected status, select the Refresh button.
If you don't see a Connected status, select the Refresh button.
Create a VM in each virtual network so that you can test the communication between them.
- On the Azure portal, select + Create a resource.
- Select Compute, and then Create under Virtual machine.
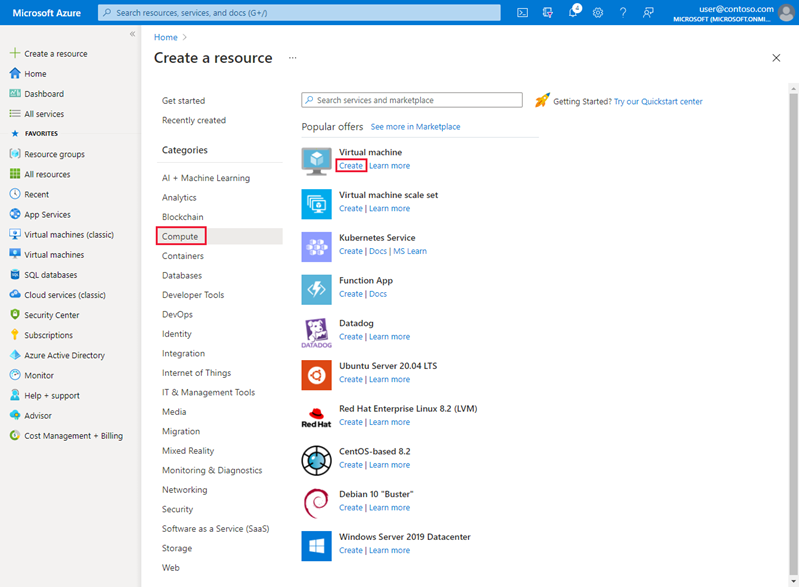
- Enter, or select, the following information on the Basics tab, accept the defaults for the remaining settings, and then select Create:
TABLE 4 Setting Value Resource group Select Use existing and then select myResourceGroup. Name myVm1 Location Select East US. Image Select an OS image. For this VM Windows Server 2019 Datacenter - Gen1 is selected. Size Select a VM size. For this VM Standard_D2s_v3 is selected. Username Enter a username. The username azure was chosen for this example. Password Enter a password of your choosing. The password must be at least 12 characters long and meet the defined complexity requirements. 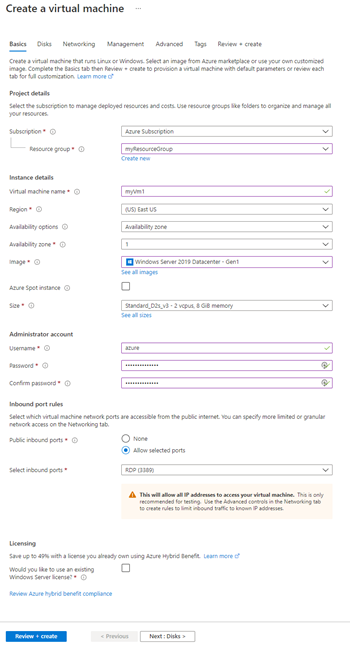
- On the Networking tab, select the following values:
TABLE 5 Setting Value Virtual network myVirtualNetwork1 - If it's not already selected, select Virtual network and then select myVirtualNetwork1. Subnet Subnet1 - If it's not already selected, select Subnet and then select Subnet1. Public inbound ports Allow selected ports Select inbound ports RDP (3389) 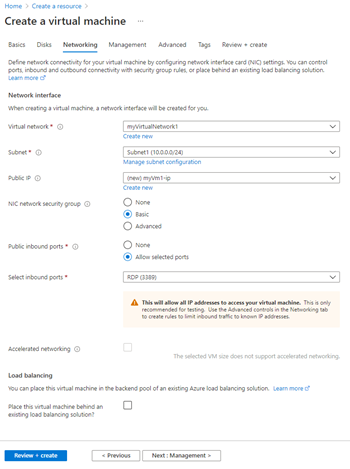
- Select the Review + Create and then Create to start the VM deployment.
Repeat steps 1-6 again to create a second virtual machine with the following changes:
| Setting | Value |
|---|---|
| Name | myVm2 |
| Virtual network | myVirtualNetwork2 |
The VMs take a few minutes to create. Do not continue with the remaining steps until both VMs are created.
Note
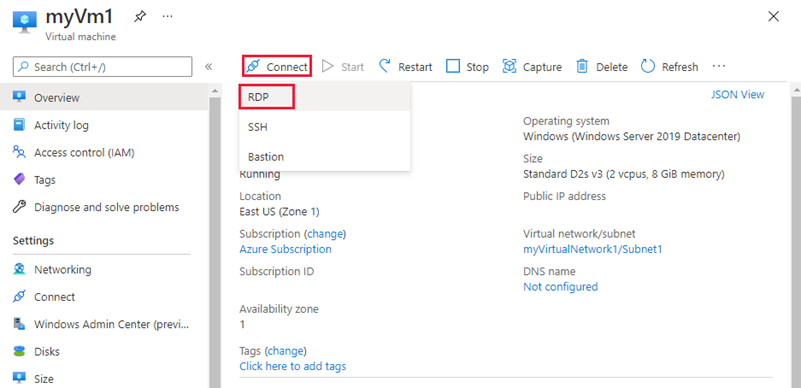
Azure provides an default outbound access IP for Azure Virtual Machines which aren't assigned a public IP address, or are in the backend pool of an internal Basic Azure Load Balancer. The default outbound access IP mechanism provides an outbound IP address that isn't configurable. The default outbound access IP is disabled when a public IP address is assigned to the virtual machine or the virtual machine is placed in the backend pool of a Standard Load Balancer with or without outbound rules. If a Azure Virtual Network NAT gateway resource is assigned to the subnet of the virtual machine, the default outbound access IP is disabled. For more information on outbound connections in Azure, see Using Source Network Address Translation (SNAT) for outbound connections.- In the search box at the top of the portal, look for myVm1. When myVm1 appears in the search results, select it.
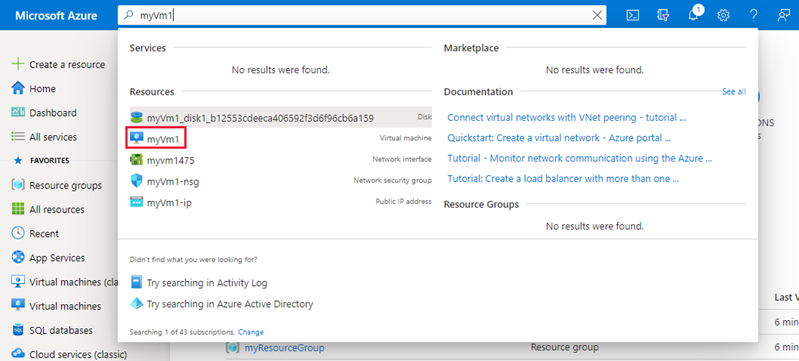
- To connect to the virtual machine, select Connect and then select RDP from the drop-down. Select Download RDP file to download the remote desktop file.
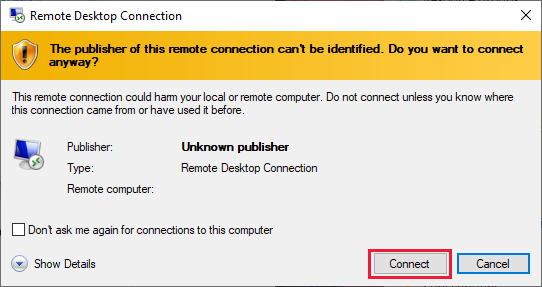
- To connect to the VM, open the downloaded RDP file. If prompted, select Connect.
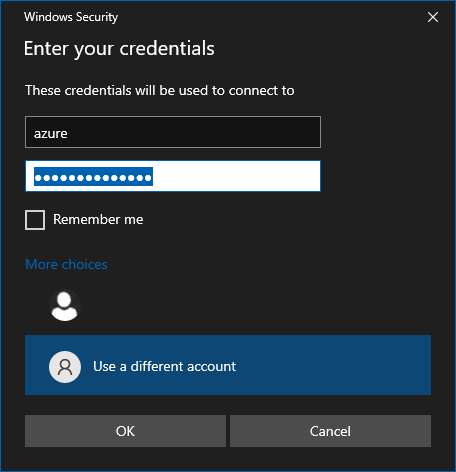
- Enter the user name and password you specified when creating the VM (you may need to select More choices, then Use a different account, to specify the credentials you entered when you created the VM), then select OK.
- You may receive a certificate warning during the sign-in process. Select Yes to continue with the connection.
- In a later step, ping is used to communicate with myVm1 VM from the myVm2 VM. Ping uses the Internet Control Message Protocol (ICMP), which is denied through the Windows Firewall, by default. On the myVm1 VM, enable ICMP through the Windows firewall, so that you can ping this VM from myVm2 in a later step, using PowerShell:
PowerShellCopy
<pre>New-NetFirewallRule –DisplayName "Allow ICMPv4-In" –Protocol ICMPv4Though ping is used to communicate between VMs in this tutorial, allowing ICMP through the Windows Firewall for production deployments isn't recommended. - To connect to the myVm2 VM, enter the following command from a command prompt on the myVm1 VM:
Copy
<pre>mstsc /v:10.1.0.4 - Since you enabled ping on myVm1, you can now ping it by IP address:
Copy
<pre>ping 10.0.0.4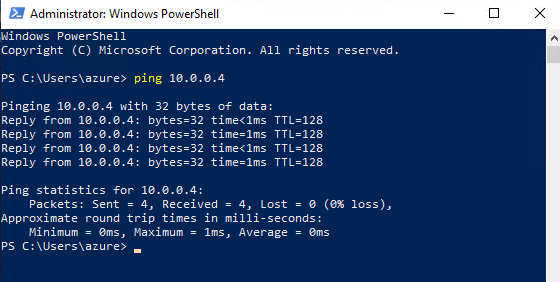
- Disconnect your RDP sessions to both myVm1 and myVm2.
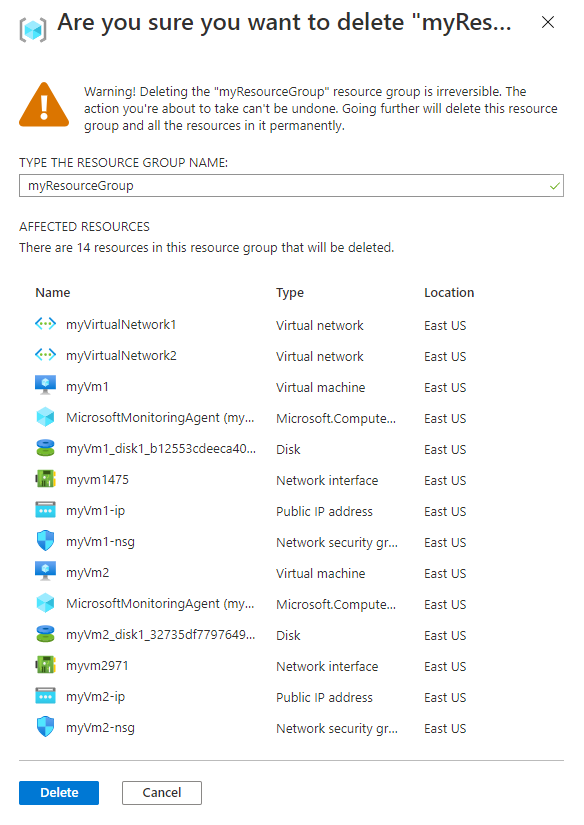
When no longer needed, delete the resource group and all resources it contains:
- Enter myResourceGroup in the Search box at the top of the portal. When you see myResourceGroup in the search results, select it.
- Select Delete resource group.
- Enter myResourceGroup for TYPE THE RESOURCE GROUP NAME: and select Delete.