Wazuh Web Application Firewall Lab - Zacham17/my-tech-journal GitHub Wiki
Temporary fw01 Firewall Rule
- On fw01 I needed to create a firewall rule that allowed web01 to receive updates and download modSecurity.
- For the WAN-to-DMZ firewall, I allowed established connections using the following commands:
set firewall name WAN-to-DMZ rule 1 action accept
set firewall name WAN-to-DMZ rule 1 state established enable
commit
save
- For the DMZ-to-WAN firewall, I created a rule that allowed connections to the WAN from web01 in order for it to download updates and software. I used the following commands to do so:
set firewall name DMZ-to-WAN rule 999 action accept
set firewall name DMZ-to-WAN rule 999 description "Updates to web01"
set firewall name DMZ-to-WAN rule 999 source address 172.16.50.3
commit
save
mod_security on web01
- On web01, I installed mod_security, the core ruleset associated with it, and the php to make the webshell work, all using the the following command:
sudo yum install mod_security mod_security_crs php php-common php-opcache php-cli php-gd php-curl php-mysqlnd -y- Note: In order for the command to work, rule 999 on the DMZ-to-WAN firewall must be enabled and active
- After the command executed, I deleted rule 999 on the DMZ-to-WAN firewall
- I then restarted httpd using
systemctl restart httpd
- Mod_security error logs can be found in /etc/httpd/logs/error_logs
Testing Mod_Security
- From rw01, I curled the contents of the web01, using
curl http://172.16.50.3, to ensure I could connect
- I then downloaded a file, found here, into a shell.php file in the /var/www/html directory, using the wget command.
- Browsing to the shell.php from a browser provides a window with an input field where commands can be input. Some command paths need to be specified, such as ifconfig. Examples are shown below:
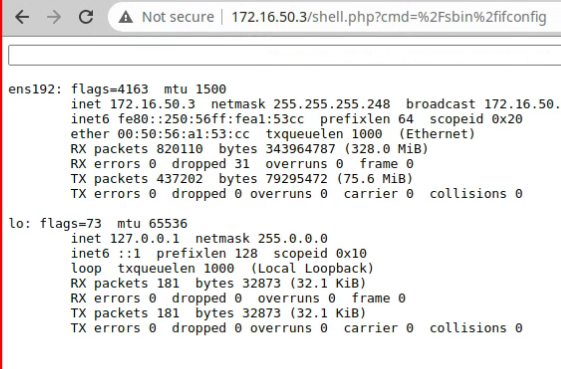
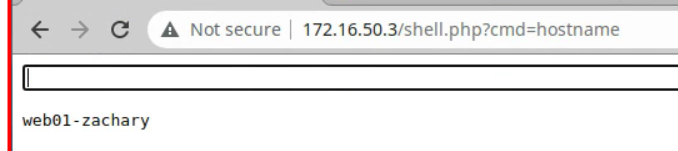
- Some commands that require elevated privileges will cannot be executed from this window, such as
cat /etc/passwd. The user will be met with a 403 error when trying to enter that command.
Viewing Error Logs
- When I attempted to run
cat /etc/passwd and produced a 403 error, the event was logged by ModSecurity.
- I was able to view the log in "/etc/httpd/logs/error_log"
- The event was also logged on Wazuh as a "Web Server 400 Error Code". It showed details such as the exact error code and the URL data that showed the command that was attempting to be executed.

