Syslog Organization on Log01(Rocky Linux) - Zacham17/my-tech-journal GitHub Wiki
Using mgmt01 to Manage VMs
- Network Configuration:
- Adapter: SEC350 LAN
- IP Address: 172.16.150.10
- Netmask: 255.255.255.0
- Gateway: 172.16.150.2
- DNS: 172.16.150.2
NAT setup for LAN to WAN on fw01
- I used the following commands in order to set up NAT from LAN to WAN on fw01
- I made sure to change the rule to an unused one
set nat source rule 20 description "NAT FROM LAN to WAN"set nat source rule 20 outbound-interface eth0set nat source rule 20 source address 172.16.150.0/24set nat source rule 20 translation address masqueradecommitsave
DNS forwarding for the LAN Network on fw01
- I used the following commands to configure DNS forwarding for the LAN network on fw01
set service dns forwarding listen-address 172.16.150.2set service dns forwarding allow-from 172.16.150.0/24set service dns forwarding systemcommitsave
Chrome Remote Desktop on mgmt01
- I installed Chrome remote Desktop on mgmt01 to remotely access it.
- From mgmt01, I am able to SSH into systems such as log01 and web01
SSH keybased authentication
- To use keybased authentication for an ssh connection, use the command
sudo ssh-keygen - Then use the command
sudo ssh-copy-id USER@DESTINATIONHOST - You will then be able to ssh into the host using ssh keybased authentication.
Changing the Vyos Password
- To change a Vyos Password, even when forgotten, you can reboot the system, and when the GRUB menu appears, select the "Lost Password(KVM)" option.
- You can then follow the prompts to set a new password for your chosen user.
- Alternatively, in configuration mode, the command
set system login user [username] authentication plaintext-password [password]can be used to set a user password
Log Organization on log01
- Comment out the following lines, shown in the screenshot below, in /etc/rsyslog.conf if they are not already commented out.
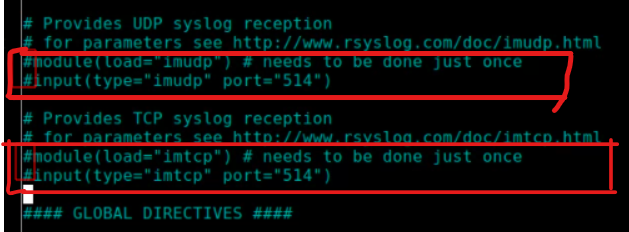
- Create a file in the /etc/rsyslog.d/ directory. My file is called sec350.conf. Add the following contents to the file:
module(load="imudp")
input(type="imudp" port="514" ruleset="RemoteDevice")
template(name="DynFile" type="string"
string="/var/log/remote-syslog/%HOSTNAME%/%$YEAR%.%$MONTH%.%$DAY%.%PROGRAMNAME%.log"
)
ruleset(name="RemoteDevice"){
action(type="omfile" dynaFile="DynFile")
}
- After creating the file, restart the rsyslog service.
- To test this, from web01, run the command
logger -t SEC350 Testing web01->log01 custom rsyslog configuration - Back on log01, in the /var/log/remote-syslog/ directory, there should now be a directory for the web01 system logs. Mine is called web01-zachary.
- In the directory, you should see the test log that was just sent.
Logging Authorization Events from web01
- On web01 in the /etc/ryslog.d/ directory create a sec350-client.conf file and add the following contents to the file."
user.notice @172.16.50.5
authpriv.* @172.16.50.5
- Restart the rsyslog service
- To test this change, from rw01, ssh into web01, but make sure to type the password wrong at least once.
- On log01 navigate to the web01 directory in the /var/log/remote-syslog/ directory and in it, you should see a log with the .sshd.log extension.
catthat log and what you see should contain lines similar to what is shown in the screenshot below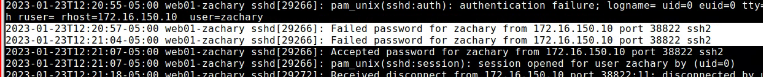
Logging authorization events on fw01.
- On fw01 in configuration mode, use the command
set system syslog host 172.16.50.5 facility authpriv level info - Don't forget to commit and save
- Restart the rsyslog service
- Log out of vyos and then log back in via ssh, but type the wrong password a couple times.
- Back on log01, there is now a fw01 related directory in /var/log/remote-syslog/, containing a .sshd.log file.
catthe file to see logs of the failed login attempts. - NOTE: A useful command to see log files in a user-friendly format is the
treecommand
Reflection
This lab didn't prove to be very difficult. Some things I found notable was making sure to ensure that I used the correct subnet mask in my configurations. I also found chrome remote desktop and SSH very convenient in this lab. I haven't worked much with logs yet, so this lab was a good introduction to logging for me.