Project 2 Remote Access Research and Integration - Zacham17/my-tech-journal GitHub Wiki
Remote Desktop Connection Over a Wireguard VPN
Overview
The goal of this project is to allow a new administrative user, Tanisha, the ability to administer the network via RDP session into MGMT02. In this project, I deployed a Wireguard VPN Server on my jump server VM and configured the traveler VM as a VPN client. I configured Wireguard to tunnel RDP connections over the VPN and forward them to mgmt02 in order for Tanisha to be able to successfully RDP into mgmt02.
Installing Wireguard VPN Server on jump:
- Before installing Wireguard on jump, I updated packages using
sudo apt update. - I then installed Wireguard using the command,
sudo apt install wireguard. - I then used the following commands to generate public and private keys for the VPN server. The keys are important in allowing Client-Server Connections:
wg genkey | sudo tee /etc/wireguard/private.key: generates a private keysudo chmod go= /etc/wireguard/private.key: changes access of the private key to root onlysudo cat /etc/wireguard/private.key | wg pubkey | sudo tee /etc/wireguard/public.key: creates a public key based on the private keyecho 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.d/10-wireguard.conf: Adds a command to enable IP forwarding to the 10-wireguard.conf filesysctl -p /etc/sysctl.d/10-wireguard.conf: Runs the command to enable IP forwarding
Wireguard Server Configuration:
- I configured the Wireguard server with the following settings:
- IP Address: 172.16.0.1/24
- Listening Port: 50120
- VPN Traffic for port 3389(RDP) forwarded to Jump and then to MGMT02
- One peer configuration(public key, VPN IP, and Keep Alive Time) to represent the client on traveler
- The configuration file, which is located at /etc/wireguard/wg0.conf can be seen below:
SERVER wg0.conf Configuration File:
## Wireguard Server Configuration ##
## Zachary Morris ##
## References Used:
## https://www.digitalocean.com/community/tutorials/how-to-set-up-wireguard-on-ubuntu-20-04, ##
## https://serverfault.com/questions/1075973/wireguard-how-to-only-tunnel-some-of-the-traffic ##
[Interface]
## My VPN server Private IP address ##
Address = 172.16.0.1/24
## My VPN server port ##
ListenPort = 50120
## VPN server's private key##
PrivateKey = XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
## Forward IP Traffic to jump ##
## Before interface wg0 is up ##
## Drop all outgoing packets from the client subnet ##
PreUp = iptables -I FORWARD -s 172.16.0.1/24 -o ens160 -j DROP
## Allow clients to connect to the local network through jump ##
PreUp = iptables -I FORWARD -s 172.16.0.1/24 -d 172.16.50.4/29 -j ACCEPT
## Allow clients to connect to tcp port 3389 on mgmt02 ##
PreUp = iptables -I FORWARD -s 172.16.0.1/24 -d 172.16.200.11 -p tcp --dport 3389 -j ACCEPT
## After interface wg0 is up ##
PostUp = iptables -t nat -I POSTROUTING -o ens160 -j MASQUERADE
## After interface wg0 is down ##
PostDown = iptables -D FORWARD -s 172.16.0.1/24 -o ens160 -j DROP
PostDown = iptables -D FORWARD -s 172.16.0.1/24 -d 172.16.50.4/29 -j ACCEPT
PostDown = iptables -D FORWARD -s 172.16.0.1/24 -d 172.16.200.11 -p tcp --dport 3389 -j ACCEPT
## Before interface wg0 is down ##
PreDown = iptables -t nat -D POSTROUTING -o ens160 -j MASQUERADE
[Peer]
## Peer Traveler ##
PublicKey = 3U7kaseJ39Ct0BLR803Vvv4tuq8kQ+BBEEVOzKcV0Qk=
AllowedIPs = 172.16.0.2/32
PersistentKeepalive = 21
Edge01 Firewall Configuration
Make a Firewall NAT rule for VPN Connections
- I set a NAT destination rule on edge01 to translate connections to port 50120 on the WAN interface to port 50120 on the jump server, which is hosting the VPN server
- The commands that I used to make the rule are shown below:
set nat destination rule 30 description 'VPN'
set nat destination rule 30 destination port '50120'
set nat destination rule 30 inbound-interface 'eth0'
set nat destination rule 30 protocol 'udp'
set nat destination rule 30 translation address '172.16.50.4'
set nat destination rule 30 translation port '50120'
commit
save
Make a Firewall rule the WAN-to-DMZ firewall to allow VPN Connections
- Connections to jump on port 50120 need to be allowed so I implemented a firewall rule on the WAN-to-DMZ firewall in order to do this.
- The commands that I used are shown below:
set firewall name WAN-to-DMZ rule 30 action accept
set firewall name WAN-to-DMZ rule 30 description “VPN to jump”
set firewall name WAN-to-DMZ rule 30 destination address 172.16.50.4
set firewall name WAN-to-DMZ rule 30 destination port 50120
set firewall name WAN-to-DMZ rule 30 protocol udp
commit
save
- NOTE: Wireguard VPN used UDP, not TCP
Install Wireguard VPN on Windows Client(traveler):
Below are the steps that I used to install and configure the Wireguard VPN Client on traveler
- Get the Wireguard installer from https://www.wireguard.com/install/
- Download the Windows Installer and run the installer.
- Once installed, open Wireguard and add an empty tunnel. You should be given a private and public key for the client.
- I then updated the client configuration, by clicking “edit” in wireguard.
Wireguard Server Configuration:
- I configured the Wireguard client with the following settings:
- IP Address: 172.16.0.2/24
- Listening Port: 50120
- One peer configuration(public key, Allowed IP, and Keep Alive Time, and Endpoint Address) to represent the VPN Server
- The Allowed IP is set to 0.0.0.0/0, which means all traffic is tunneled through the VPN.
- The Endpoint is set to the edge01 WAN interface address on port 50120, because NAT forwards that trafffice to jump(which is the VPN server).
- The configuration file can be seen below: CLIENT wg0-tanisha.conf CONFIG:
[Interface]
## This Desktop/client's private key ##
PrivateKey = XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
## Client ip address ##
Address = 172.16.0.2/24
[Peer]
## Jump Wireguard Server Public Key ##
PublicKey = 6pyXGtn6nMnOEmj69GZk+vCLGi1qH6XSHspVEz265hM=
## set ACL ##
AllowedIPs = 0.0.0.0/0
## VPN Server's local IPv4 address and port ##
Endpoint = 10.0.17.133:50120
PersistentKeepalive = 21
Connect the Client to the Server
- To connect the client to the VPN Server, the VPN Server must be running. To do this, to command,
sudo systemctl start [email protected], can be used. - After making sure that the Wireguard server is successfully running, On traveler, I opened Wireguard on the client and clicked “Activate” to connect traveler to the VPN. I know this is successful when I see that the client is both sending and receiving data to/from the VPN server. I can also see the wg0 interface active on both the client and server. The screenshot below shows this:
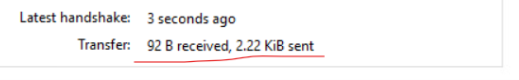
RDP from Traveler to MGMT02
Now that I am connected to the VPN, I am able to connect to mgmt02 via RDP, using the IP address of mgmt02.. The screenshot below shows the initiated login screen for Tanisha through RDP.
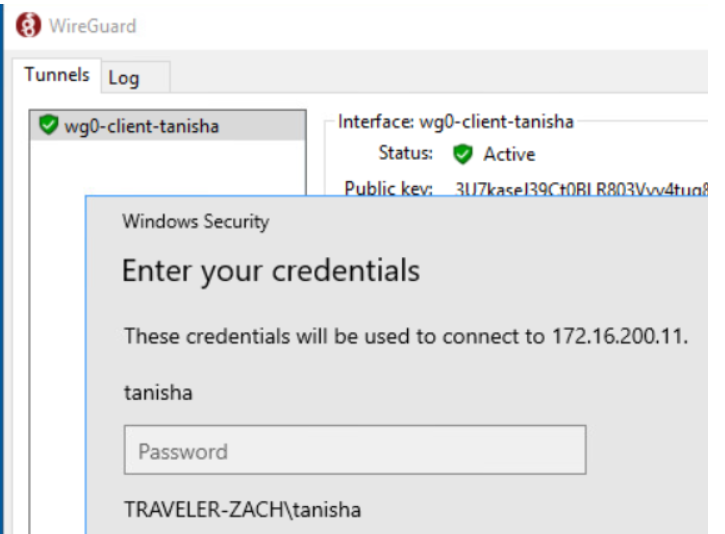
Other Notes:
- Remember to restart the wireguard service whenever the configuration is changed
- For security purposes, I added a Tanisha user to traveler and mgmt02.
- The client can easily disconnect from the VPN by clicking "deactivate".
- Make sure remote connections to mgmt02 are allowed.
References Used:
- https://serverfault.com/questions/1075973/wireguard-how-to-only-tunnel-some-of-the-traffic
- https://www.cyberciti.biz/faq/ubuntu-20-04-set-up-wireguard-vpn-server/
- https://www.digitalocean.com/community/tutorials/how-to-set-up-wireguard-on-ubuntu-20-04
- https://serversideup.net/how-to-configure-a-wireguard-windows-10-vpn-client/