Port Forwarding and Jump Boxes Lab - Zacham17/my-tech-journal GitHub Wiki
- I removed the static route to the DMZ network on rw01 using the network configuration manager in Linux.
- On fw01, in configuration mode, I used the following commands to set a nat destination rule to forward any port 80 traffic going into the firewall's eth0 interface(WAN) to web01:
set nat destination rule 10 description HTTP->WEB01
set nat destination rule 10 destination port 80
set nat destination rule 10 inbound-interface eth0
set nat destination rule 10 protocol tcp
set nat destination rule 10 translation address 172.16.50.3
set nat destination rule 10 translation port 80
commit
save
- The jump host is going to be used as a Jump Box, which is a system, normally exposing SSH, RDP or a VPN port to a less secure network.
- I set the network configuration of jump as follows:
- Network Adapter: SEC350-01-DMZ
- IP Address: 172.16.150.50
- Netmask: 255.255.255.248(/29)
- Gateway: 172.16.50.2
- DNS: 172.16.50.2
- I used netplan for the network configuration. My 00-installer-config.yaml file looks as follows:
network:
ethernets:
ens160:
addresses:
- 172.16.50.4/29
dhcp4: false
gateway4: 172.16.50.2
nameservers:
addresses:
- 172.16.50.2
version: 2
- I then used
sudo netplan tryandsudo netplan applyto apply the changes. - I also set the system hostname, and changed the password of champuser
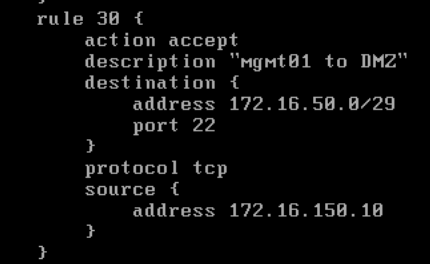
- I needed to allow mgmt01 to SSH into the DMZ
- I set a firewall rule on fw01 for the LAN-to-DMZ firewall to allow such connections. The rule looks as follows:
- On rw01, I ran the
ssh-keygencommand to generate a keypair that will be used for ssh access to jump from rw01. - On jump, I created a passwordless user named zachary-jump, which will be used as the SSH user.
- In zachary-jump's home directory on jump, I created the .ssh/authorized_keys file and put the public key that I generated on rw01 in the file. I did this using the following steps:
- On mgmt01, I ran the command
sudo scp [email protected]:/home/zachary/keys/jump-zachary.pub /home/champuser/Downloadsto retrieve rw01's public key - On mgmt01, I ran the command
scp Downloads/jump-zachary.pub [email protected]:/home/champuser/jump-zachary.pubto move the public key for rw01 onto jump - On jump, I ran the command
sudo cat /home/champuser/jump-zachary.pub > /home/zachary-jump/.ssh/authorized_keysto copy the public key into the authorized_hosts file.
- On mgmt01, I ran the command
- On fw01, in configuration mode, I used the following commands to set a nat destination rule to forward any port 22 traffic going into the firewall's eth0 interface(WAN) to jump:
set nat destination rule 20 description "SSH to JUMP"
set nat destination rule 20 destination port 22
set nat destination rule 20 inbound-interface eth0
set nat destination rule 20 protocol tcp
set nat destination rule 20 translation address 172.16.50.4
set nat destination rule 20 translation port 22
commit
save
-
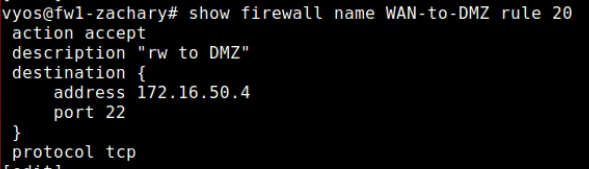
I also adjusted the WAN-to-DMZ firewall to allow SSH traffic from WAN to jump. The rule looks as follows:
-
On rw01, I removed the .ssh/known_hosts file to ensure no prior IP address association prevents a successful connection.
-
On rw01, I then used used the command
ssh -i keys/jump-zachary [email protected]to connect to jump as the zachary-jump user- keys/jump-zachary is the rw01 private key
- 10.0.17.133 is the WAN address on fw01, which forwards to jump
-
I also created an internal admin account on jump called "zachary" with sudo privileges
- Configuring jump as a wazuh agent can be complicated since, jump is not accessible by the internet. To combat this, I used mgmt01 as a means to facilitate downloads of necessary files
- On mgmt01, I ran the command
curl -so wazuh-agent-4.3.10.deb https://packages.wazuh.com/4.x/apt/pool/main/w/wazuh-agent/wazuh-agent_4.3.10-1_amd64.debto download the wazuh-agent installation file - I then transferred the file to jump using the command
scp wazuh-agent-4.3.10.deb [email protected]:/home/zachary/wazuh-agent-4.3.10.deb - Then, on jump, I ran the command,
sudo WAZUH_MANAGER='172.16.200.10' WAZUH_AGENT_GROUP='linux' dpkg -i ./wazuh-agent-4.3.10.deb - To start the wazuh-agent, I ran the commands:
sudo systemctl daemon-reload
sudo systemctl enable wazuh-agent
sudo systemctl start wazuh-agent
- jump then showed up in the Wazuh agents dashboard.
There was one part of this lab that gave me issues. When running the command to install the wazuh-agent on jump, I accidentally typed in the wrong IP address for he manager address. This prevented jump from being registered in wazuh. I knew something was wrong when I ran the command sudo grep ^status /var/ossec/var/run/wazuh-agentd.state and saw the status as "pending". I fixed the issue by editing the /var/ossec/etc/ossec.conf file and changing the address line to be