Lab 9.2 - Zacham17/my-tech-journal GitHub Wiki
Lab 9.2: Exploiting Gloin
In this lab, I was able to leverage a vulnerability found on the gloin host and gain root access.
Reconnaissance
- I gathered information on the system before finding and exploiting the vulneravility
Target IP Address
- I already knew the DNS server being used by the host is 10.0.5.22 and the domain is shire.org
- To find the ip address of the gloin host, I ran the command
nslookup gloin.shire.org 10.0.5.22- From this command, I found the target IP address to be
10.0.5.31
- From this command, I found the target IP address to be
Finding Open Ports
- I found open ports on gloin using the command
sudo nmap -Pn -A -sV -O -p 1-6000 10.0.5.31 - I found the following open ports and services:
- Port 22/tcp: SSH
- Port 443/tcp: http(s)
- Port 3389/tcp Microsoft Terminal Services/RDP
- The scan also revealed that the gloin host is running Windows
Finding Vulnerabilities
SQL Injection
- Since port 443 is open, I browsed to
https://10.0.5.31in my browser, and was redirected tohttps://10.0.5.31/entrance_exam/login.php- This page consists of a field asking for a reference code.
- I decided to use an SQL injection technique to test for an SQL Injection vulnerability. I did this by entering
1' OR 1=1 --+into the reference code box, and was able to get a successful login, showing me that there is an SQL Injection vulnerability.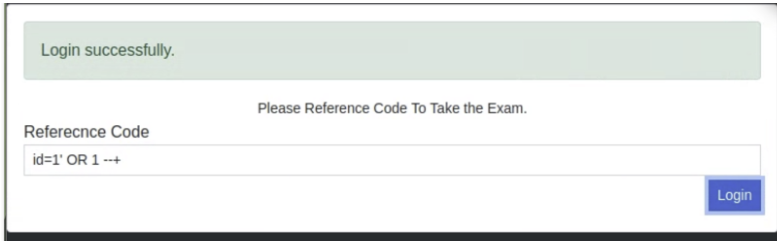
- I was logged in as the John Smith user, but I wasn't able to do much from here.
Directory Browsing
- After collaborating with some classmates, I decided to run the
dirbcommand which is a web content scanner that will reveal any directories that I can browse to from the browser. I ran the commanddirb https://10.0.5.31/entrance_exam -r /usr/share/wordlists/dirb/common.txt - The command revealed the following accessible directories:
https://10.0.5.31/entrance_exam/adminhttps://10.0.5.31/entrance_exam/csshttps://10.0.5.31/entrance_exam/dbhttps://10.0.5.31/entrance_exam/imageshttps://10.0.5.31/entrance_exam/js
- The two most important directories are
https://10.0.5.31/entrance_exam/adminandhttps://10.0.5.31/entrance_exam/db - When I browsed to the "admin" directory, I was brought to a log in page asking for a user and password. By entering
1' OR 1=1 --+into both fields, I was able to successfully gain access to the administrator account for the web server/database. From here, I was able to manage users, and change admin credentials, but I didn't utilize any of these to gain access to the base gloin host. - Instead I browsed to
https://10.0.5.31/entrance_exam/dband found a file calledexam_db.db, which I downloaded and viewed using DB browser.
Gaining a Foothold
- In the
exam_db.dbfile, I navigated to the admin_list table of the database and found the administrator user, that I logged in as earlier using SQL injection, and an encrypted password for the account. - I quickly determined by the hash length that MD5 encryption was used and I ran it through an md5 decryption website
- The website successfully decrypted the password, which told me that the hash wasn't even salted.
Achieving Root/Administrative Level Compromise
- Knowing that SSH is running on the open port 22 on the target system and knowing that the windows default administrative user is administrator, I attempted an SSH log in for the administrator account on gloin.
- From my kali VM, I ran the command,
ssh [email protected]and entered the password I just decrypted, and was successfully able to log in at an administrative level.- This means that the database administrator and the administrator of the gloin host share the same password.
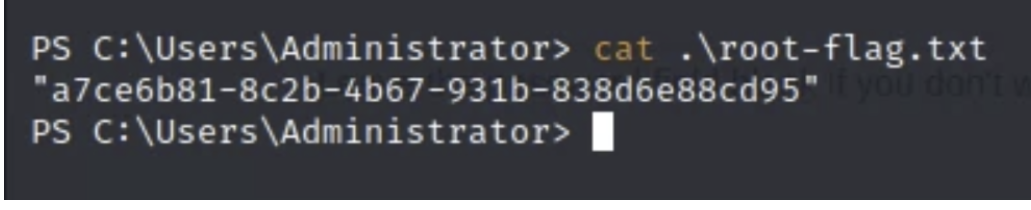
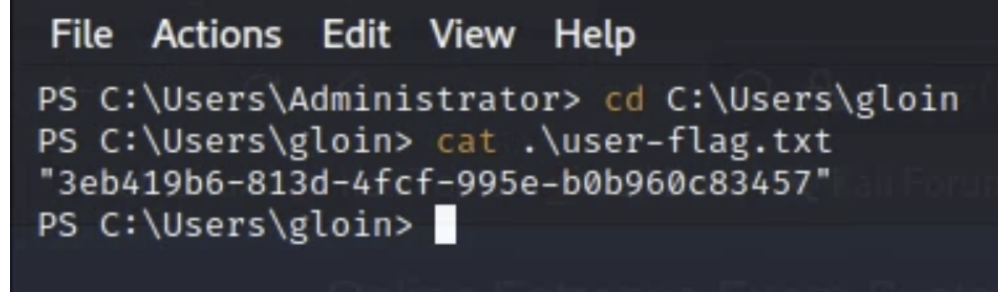
- From there, I used the cat command to get the contents of the root-flag.txt file and the user-flag.txt file, which is located in C:\Users\gloin\
Root Flag:
User Flag:
How Vulnerabilities Can Be Mitigated
- There is a lot that can be done to increase the security of the gloin host.
- One thing that can be done is to implement systems to prevent vulnerabilities such as SQL injections.
- Something else to increase security is to prevent directory traversal from the web browser to directories that not everyone is supposed to have access to, such as the DB directory.
- A third suggestion that I would make is to increase password security by using more secure and unpredictable password, using better hashing algorithms(use a hash salt), and don't repeat passwords across users like was done between the Administrator user for gloin and the administrator user of the database.
Reflection
Exploiting the gloin target did prove to be quite simple, but there was one part of the process that I had trouble with. After proving an SQL injection vulnerability and logging into the John Smith user, I had trouble figuring out what to do next. After some research and collaboration with classmates, I ended up using the dirb command targeted at gloin and from there, I was able to smoothly continue and complete the lab and gain administrative access to gloin.