Lab 1.1 Routing and DMZ - Zacham17/my-tech-journal GitHub Wiki
rw01 Setup
Network Adapter:
- SEC350-WAN
- I set the hostname on the rw01 system to rw01-zachary
- I added a new sudo user to the system
- I adjusted the network configuration as follows:
Network configuration:
- IP: 10.0.17.33
- Default Gateway: 10.0.17.2
- DNS: 10.0.17.2
fw01 Setup
Network Adapters:
- SEC350-01-WAN
- SEC350-01-DMZ-zachary.morris
- SEC350-01-LAN-zachary.morris
- I set the hostname on the fw01 system to fw1-zachary
- I adjusted the network configuration as follows, while disabling DHCP:
Network configuration:
- eth0 IP: 10.0.17.133/24 (WAN)
- eth1 IP: 172.16.50.2/29 (DMZ)
- eth2 IP: 172.16.50.2/24 (LAN)
Internet Access
- I used the following commands, in configuration mode, to allow fw01 to reach the internet:
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2set system name-server 10.0.17.2
web01 setup
Network Adapter:
- SEC350-01-DMZ-zachary.morris
- I set the hostname on the fw01 system to web01-zachary
- I added a new sudo user to the system, called zachary
- Using the nmtui configuration tool, I set the network configuration as follows
Network configuration:
- IP: 172.16.50.3/29
- Default Gateway: 172.16.50.2
- DNS: 172.16.50.2
NAT and DNS Forwarding Setup on fw01
- Using the following commands in configuration mode on fw01, I configured NAT from the DMZ to the WAN:
set nat source rule 10 description "NAT FROM DMZ to WAN"set nat source rule 10 outbound-interface eth0set nat source rule 10 source address 172.16.50.0/29set nat source rule 10 translation address masqueradecommitsave
- Now the web01 system can ping out to the internet, but still can't perform DNS lookup
- DNS Forwarding can be set up using the following commands in configuration mode:
set service dns forwarding listen-address 172.16.50.2set service dns forwarding allow-from 172.16.50.0/29set service dns forwarding system
- Now web01 is able to resolve dns names. I tested this by pinging google.com
log01 setup
Network Adapter:
- SEC350-01-DMZ-zachary.morris
- I set the hostname on the fw01 system to log01-zachary
- I added a new sudo user to the system, called zachary
- Using the nmtui configuration tool, I set the network configuration as follows
Network configuration:
- IP: 172.16.50.5/29
- Default Gateway: 172.16.50.2
- DNS: 172.16.50.2
HTTPD and Firewall on web01
- I installed httpd on web01 using the command
sudo yum install httpd. Once installed, I started httpd
- I then configured the firewall on web01 using the commands
firewall-cmd --permanent --add-service httpfirewall-cmd --permanent --add-service https
- I then restart the firewall service using
firewall-cmd --reload
Testing HTTPD on web01 from rw01
- On rw01, I configured static routing in the network configuration to route addresses in the DMZ to fw01's WAN interface.
- The static routing configuration is as follows:
- Address: 172.16.50.0
- Netmask: 255.255.255.248
- Gateway: 10.0.17.133
- I then reset the network interface by disconnecting and reconnecting it.
Configuring rsyslog services on log01
- On log01, I allowed traffic for TCP/UDP port 514 using the commands:
firewall-cmd --permanent --add-port 514/tcpfirewall-cmd --permanent --add-port 514/udp
- I then restarted the firewall using
firewall-cmd --reload
- I then installed the rysylog service on log01 using
sudo yum install rsyslog
- I then edited the /etc/rsyslog.conf file, and uncommented lines as shown below:
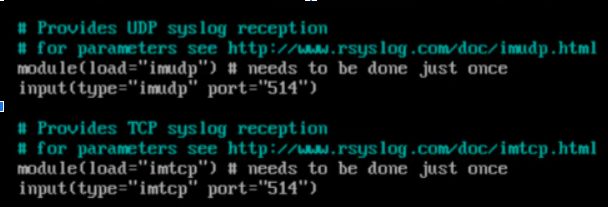
- I then started the rsyslog service and ensure my configuration was applied using the command
netstat -tupan | grep 514
Configuring rsyslog services on web01
- I installed the rysylog service on web01 using
sudo yum install rsyslog
- I then created and edited the /etc/rsyslog.d/sec350.conf file, and added the line
user.notice @172.16.50.5
- I then started the rsyslog service
- I then tested rsyslog messaging from web01 to log01 by using the command,
logger -t test TESTFROMWEB01TOLOG01
- I confirmed that the message worked by tailing the /var/log/messages file on log01
Notes
