Home - Yash-777/Java_Mail GitHub Wiki
Windows

Please use MXtoolBox to have a test for your MX records.
Test mail server SMTP (port 25)
Mail Server: Connection issue
javax.mail.MessagingException: Could not connect to SMTP host: mail.corporate.online, port: 25;
nested exception is:
java.net.SocketException: Permission denied: connect
at com.sun.mail.smtp.SMTPTransport.openServer(SMTPTransport.java:1282)
at com.sun.mail.smtp.SMTPTransport.protocolConnect(SMTPTransport.java:370)
at javax.mail.Service.connect(Service.java:275)
Mail Server send Mail to ToAddress Mail Server:
Caused by: javax.mail.SendFailedException: Invalid Addresses;
nested exception is:
com.sun.mail.smtp.SMTPAddressFailedException: 550 5.1.2 unknown host or domain: [email protected];
This means that our mail server was not able to locate the mail server for corporate.online (mail.corporate.online) in the Internet's domain name service (DNS). If it can't be found in the DNS, the mail server can't connect to the target mail server to deliver the message.
KeyStore Explorer is an open-source GUI replacement for the Java command-line utilities keytool and jarsigner. KeyStore Explorer presents their functionality, and more, via an intuitive graphical user interface.

When using SSL/TLS, it's important to ensure that the server you connect to is actually the server you expected to connect to, to prevent "man in the middle" attacks on your communication. Use Trust Manager/Trusted Certificates.
Trusted Certificates
To establish an SSL/TLS connection, the JavaMail client must be able to verify that the security certificate presented by the server it is connecting to is "trusted" by the client. Trusted certificates are maintained in a Java keystore file on the client. The J2SE SDK "keytool" command is used to maintain the keystore file.
There are two common approaches for verifying server certificates. The first approach is probably most common for servers accessible to partners outside a company. The second approach is probably most common for servers used within a company.
-
Server certificates may be signed be a well-known public Certificate Authority (TrustedRoot CA
.pfx,.p12). The default Java keystore file contains the public keys of well-known Certificate Authorities and can verify the server's certificate by following the chain of certificates signing the server's certificate back to one of these well known CA certificates.In this case the client doesn't need to manage certificates explicitly but can just use the default keystore file.
-
Server certificates may be "self-signed" (
.jks). In this case there is no chain of signatures to use in verifying the server's certificate. Instead, the client will need the server's certificate in the client's keystore file. The server's certificate is imported into the keystore file once, using the keytool command, and after that is used to verify connections to the server. A single keystore file may contain certificates of many servers.In this case the client will need to set the appropriate System properties to point to the client's keystore file containing the trusted certificate. These properties can be set when invoking the "java" command, or can be set programmatically. For example,
java -Djavax.net.ssl.trustStore=$HOME/.keystore ...
Server Identity Check
RFC 2595 specifies addition checks that must be performed on the server's certificate to ensure that the server you connected to is the server you intended to connect to. This reduces the risk of "man in the middle" attacks. For compatibility with earlier releases of JavaMail, these additional checks are disabled by default. We
strongly recommend that you enable these checks when using SSL.
To enable these checks, set the "mail.<protocol>.ssl.checkserveridentity" property to "true".
Generate the Client & Server certificates Spring Boot Client authentication demo
Note that when using Tomcat as the embedded servlet container, you can’t have the keystore file inside your jar/war, they need to be on the filesystem. If you want to run this example using tomcat copy the server.jks to a folder and reference that folder instead of classpath:server.jks
From the project root:
keytool -genkeypair -alias serverkey -keyalg RSA -dname "CN=Server,OU=Spring team,O=Pivotal,L=Ave of Americas,S=NY,C=US"
-keypass s3cr3t -keystore server.jks -storepass s3cr3t
keytool -genkeypair -alias clientkey -keyalg RSA -dname "CN=Client,OU=Spring team,O=Pivotal,L=Ave of Americas,S=NY,C=US"
-keypass s3cr3t -keystore client.jks -storepass s3cr3t
Export Client and server certificates
keytool -exportcert -alias clientkey -file client-public.cer -keystore client.jks -storepass s3cr3t
keytool -exportcert -alias serverkey -file server-public.cer -keystore server.jks -storepass s3cr3tImport client certificate onto server keystore (and vice versa)
keytool -importcert -keystore server.jks -alias clientcert -file client-public.cer -storepass s3cr3t -noprompt
keytool -importcert -keystore client.jks -alias servercert -file server-public.cer -storepass s3cr3t -nopromptYou now have two keystore files, one for the server with a client cert, and one for the client with a server cert.
During the authentication using client certs, the client send its certificate to the server that needs to have it on its keystore to accept the connection. The client needs the server cert because we are using self signed certs and the http client would not accept a certificate that was not signed by a known CA.
SocketFactory « Default handshaking protocols « To avoid SSLException use https.protocols system property.
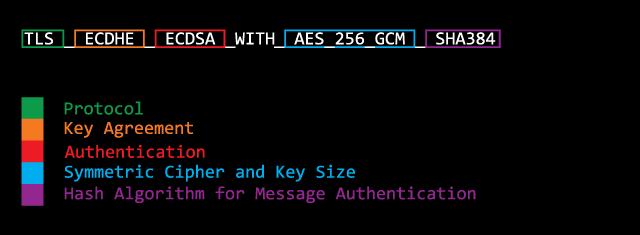
A cipher suite is a collection of symmetric and asymmetric encryption algorithms used by hosts to establish a secure communication in Transport Layer Security (TLS) / Secure Sockets Layer (SSL) network protocol.
Ciphers are algorithms, more specifically they’re a set of steps for both performing encryption as well as the corresponding decryption.
A cipher suite specifies one algorithm for each of the following tasks:
- Key exchange
- Bulk encryption
- Message authentication
System.setProperty("https.protocols", "SSLv3");
// (OR)
System.setProperty("https.protocols", "TLSv1");