Read: Class 12 Domain Controller - VascoLucas01/networking-reading-notes GitHub Wiki
Introduction
In this Read it will be addressed the difference and understanding of a domain and a workgroup. Additionally, it will be a discussed how DNS works.
What is a Windows Domain and How does it affect my PC?
Windows domains are typically used on large networks - corporate networks, school networks, and government networks. They aren't something you'll encounter at home unless you have a laptop provided by your employer or school.
A typical home computer is an isolated entity. You control the settings and user accounts on the computer. A computer joined to a domain is different - these settings are controlled on a domain controller.
What is a Domain?
Windows domains provide network administrators with a way to manage a large number of PCs and control them from one place. One or more servers - known as domain controllers - have control over the domain and the computers on it.
Domain Controllers are servers that manage authentication and authorization in a Windows domain. They are responsible for managing user accounts, groups, and computer accounts within the domain. Here are some examples of domain comtrollers: Active Directory Domain Services (AD DS), Samba, FreeIPA, Novell eDirectory and Oracle Directory Server.
Domains are generally made up of computers on the same local network. However, computers joined to a domain can continue communicating with their domain controller over VPN or internet connection. This allows businesses and schools to remotely manage laptops they provide to their employees and students.
Domain Controllers. In fact, it is important to notice that it is possible the existence of multiple Domain Controllers, but the question is "Why multiple Domain Controllers?". This existence provides fault tolerance and the critical data is replicated between the DCs.
When a computer is joined to a domain, it doesn't use its own local user accounts. User accounts and passwords are managed on the domain controller. When you log into a computer on that domain, the computer authenticates your user account name and password with the domain controller. This means you can log in with the same username and password on any computer joined to the domain.
Network administrators can change group policy settings on the domain controller. Each computer on the domain will get these settings from the domain controller and they'll override any local settings users specify on their computers. All the settings are controlled from a single place. This also "locks down" the computers. You probably won't be allowed to change many system settings on a computer joined to a domain.
Because domain aren't intended for home users, only a computer running Professional or Enterprise version of Windows can be joined to a domain.
Workgroups vs. Domains
Every Windows computer not joined to a domain is part of a workgroup. A workgroup is a group of computers on the same local network. Unlike on a domain, no computer on a workgroup has control over any other computer. A workgroup doesn't require a passwork either.
DNS - The Internet's Directory Service
Just as humans that can be identified by their social security number, citizen card or by their name, so too can Internet hosts. One identifier for a host is its hostname. Hostnames - such as www.facebook.com, www.google.com - are mnemonic and are therefore appreciated by humans. However, hostnames provide little, if any, information about the location within the Internet of the host. Furthermore, because hostnames can consist of variable-lenght alphanumeric characters, they would be difficult to process by routers. For these reason, hosts are also identified by so-called IP addresses.
We discuss IP addresses in some detail in a previous Read, but it is useful to say brief words about them now. An IP address consists of four bytes and has a rigid hierarchical structure. An IP address looks like 121.7.106.83, where each period separates one of the bytes expressed in decimal notation from 0 to 255. An IP address is hierarchical because as we scan the address from left to right, we obtain more and more specific information about where the host is located in the Internet.
Services provided by DNS
We have just seen there are two ways to identify a host - by a hostname and by an IP address. People prefer the more mnemonic hostname identifier, while routers prefer fixed-length, hierarchically strutured IP address. In order to reconcile these preferences, we need a directory service that translates hostnames to IP addresses. This is the main task of the Internet's domain name system (DNS). The DNS is a distributed database implemented in a hierarchy of DNS servers, and an application-layer protocol that allows hosts to query the distributed database. The DNS protocol runs over UDP and uses port 53.
All this process of translating hostnames into IP addresses takes time, but, fortunately, the desired IP address is often cached in a "nearby" DNS server, which helps to reduce DNS network traffic as well as the average DNS delay.
DNS provides a few other important services in addition to translating histnames to IP addresses:
- Host aliasing
- Mail server aliasing
- Load distribution
A simple design for DNS would have one DNS server that contains all the mappings. In this centralized design, clients simply directs all queries to the single DNS server, and the DNS server responds directly to the querying clients. Although the simplicity of this design is attractive, it is inappropriate for today's Internet, with its vast (and growing) number of hosts. The problemas with a centralized design include:
- A single point of failure
- Traffic volume
- Distant centralized database
- Maintenance
In summary, a centralized database in a sigle DNS server simply doesn't scale. Consequently, the DNS is distributed by design.
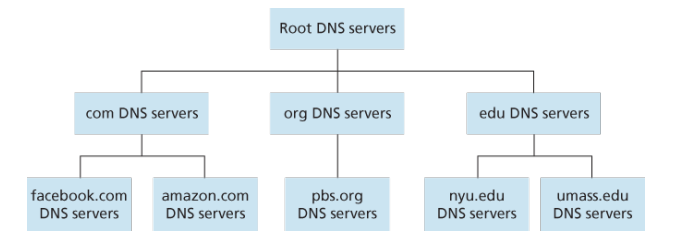
So, in order to deal with the issue of scale, the DNS uses a large number of servers, organized in a hierarchical fashion and distributed around the world. No single DNS server has all of the mappings for all of the hosts in the Internt. Instead, the mappings are distributed across the DNS servers. To a first approximation, there are three classes of DNS servers - root DNS servers, top-level domain (TLD) DNS servers, and the authoritative DNS servers - organized in the figure below.
-
Root DNS servers. Root name servers provide the IP addresses of the TLD servers.
-
Top-level domain (TLD) servers. For each of the top-level domains - top-level domains such as com, org, net, edu and all of the country top-level domains such as pt, uk, fr - there is TLD server. TLD servers provide the IP addresses for authoritative DNS servers.
-
Authorative DNS servers. Every organization with publicly accessible hosts on the Internet must provide publicly accessible DNS records that map the names of those hosts to IP addresses. An organization's authoritative DNS server houses these DNS records.
The root, TLD, and authoritative DNS servers all belong to the hierarchy of DNS servers. There is another important type of DNS server called the local DNS server. A local DNS server does not strictly belong to the hierarchy of servers but is nevertheless central to the DNS architecture. Each ISP - such as a residential ISP or an institutional ISP - has a local DNs server. When a host connects to an ISP, the ISP provides the host with the IP addresses of one or more of its local DNS servers.
DNS Caching
Our discussion thus far has ignored DNS caching, a critically important feature of the DNS system. In truth, DNS extensively exploits DNS caching in order to improve delay performance and to reduce the number of DNS messages ricocheting around the Internet. The idea behind DNS caching is very simple. In a query chain, when a DNS server receives a DNS reply, it can cache the mapping in its local memory.
DNS Records and Messages
The DNS servers that together implement the DNS distributed database store resource records (RRs), including RRs that provide hostname-to-IP address mappings. Each DNS reply message carries one or more resources records.
A resource record is a four-tuple that contains the following fields:

TTL is the time to live of the resource record; it determines when the resource record shoulb be remove from a cache. The meaning of Name and Value depend on Type:
-
If type=A, then Name is a hostname and Value is the Ip address for the hostname. Thus, a Type A record provides the standard hostname-to-IP address mapping. As an example, (relay1.bar.foo.com, 145.37.93.126, A) is a Type A record.
-
If Type=NS, then NAme is a domain (such as foo.com) and Value is the hostname of an authoritative DNS server that knows how to obtain the IP addresses for hosts in the domain. This record is used to route DNS queries further along in the query chain. As an example, (foo.com, dns.foo.com, NS) is a Type NS record.
-
If Type=CNAME, then Value is canonical hostname for the alias hostname Name. This record can provide querying hosts the canonical name for a hostname. As an example, (foo.com, relay1.bar.foo.com, CNAME) is a CNAME record.
-
If Type=MX, then Value is the canonical name of a mail server that has an alias hostname Name. As an example, (foo.com, mail.bar.foo.com, MX) is an MX record. Mx records allow the hostnames of mail servers to have simple aliases.
If a DNS server is authorative for a particular hostname, then the DNS server will contain a Type A record for the hostname. (Even if the DNS server is not authorative, it may contain a Type A record in its cache.) If a server is not authorative for a hostname, then the server will contain a Type NS record for the domain that includes the hostname; it will also contain a Type A that provides the IP address of the DNS server in the Value field of the NS record. As an example, suppose an edu TLD server is not authorative for the host gaia.cs.umass.edu. Then this server will contain a record for a domain that includes the host gaia.cs.umass.edu., for example, (emass.edu, dns.umass.edu, NS). The edu TLD server would also contain a Type A record, which maps the DNS server dns.umass.edu to an IP address, for example, (dns.umass.edu, 128.119.40.111, A).
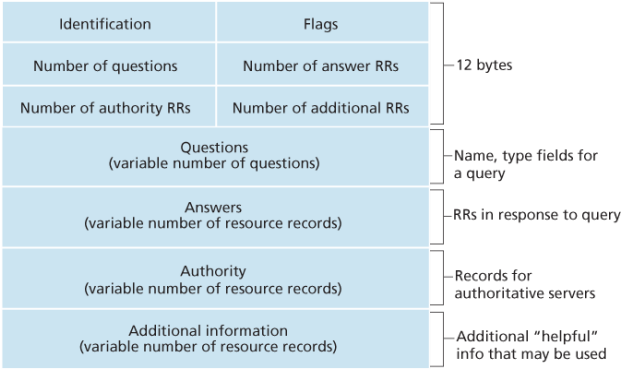
DNS Messages
There are only two kinds of DNS messages, DNS query and DNS reply. Furthermore, both query and reply messages have the same format, as shown below.
FOCUS ON SECURITY
"We have seen that DNS is a critical component of the Internet infrastructure, with many important services - including the Web and e-mail - simply incapable of functioning without it. We therefore naturally ask, how can DNS be attacked? Is DNS a sitting duck, waiting to be knocked out of service, while taking most Internet applications down with it?
The first type of attack that comes to mind is a DDoS bandwidth-flooding attack against DNS servers. For example, an attacker could attempt to send to each DNS root server a deluge of packets, so many that the majority of legitimate DNS queries never get answered. Such a large-scale DDoS attack against DNS root servers actually took place on October 21, 2002. In this attack, the attackers leveraged a botnet to send trunck loads of ICMP ping messages to each of the 13 DNS root IP addresses.
Fortunately, this large-scale attack cause minimal damage, having little or no impact on users' Internet experience. The attackers did succeed at directing a deluge of packets at the root servers. But many of the DNS root servers were protected by packet filters, configured to always block all ICMP ping messages direscted at the root servers. The protected servers were thus spared and functioned as normal. Furthermore, most local DNS servers cache the IP addresses of top-level-domain servers, allowing the query process to often bypass the DNS root servers.
A pottencially more effective DDoS attack against DNS would be send a deluge of DNS queries to top-level-domain servers, for example, to all the top-level-domain servers that handle the .com domain. It would be harder to filter DNS queries directed to DNS servers; and top-level-domain server are not as easily bypassed as are the root servers. But the severity of such an attack would be partially mitigated by caching in local DNS servers.
DNS could potentially be attacked in other ways. In a man-in-the-middle attack or on-path attack, the attacker intercepts queries from hosts and returns bogus replies. In the DNS poisoning attack, the attacker sends bogus replies to a DNS server, tricking the server into accepting bogus records into its cache. Either of these attacks could be used, for example, to redirect an unsuspecting Web user to the attacker's Web site. These attacks, however, are difficult to implement, as they require intercepting packets or throttling servers.
In summary, DNS has demonstrated itself to be surprisingly robust against attacks. To date, there hasn't been an attack that has successfully impeded the DNS service."
Famous DNS Attacks Type
- DNS Cache Poisoning Attack
- Distributed Reflection Denial of Service (DRDoS)
- DNS Hijacking
- Phantom Domain Attack
- SYN Flood Attacks
- Random Subdomain Attack
- DNS Tunneling
- DNS Flood Attack
- Domain Hijacking
- Botnet-based Attacks
Dig tool
The "dig" command is a network administration tool used to perform DNS (Domain Name System) lookups. It is available on most Unix-like systems, including Linux and macOS.
When you run the "dig" command followed by a domain name, it will query the DNS server for information about that domain name, such as its IP address or DNS records.
Questions
- Explain the role of a Domain Controller?
In general, a domain controller is a server that provides centralized authentication and authorization for resources within a specific domain or network. While this term is most commonly associated with Windows Server environments, other operating systems and directory services may provide similar functionality with different terminology and implementations.
- What is the benefit of being able to login with the same username and password on any computer joined to the domain? What are the security risks?
The benefit of being able to login with the same username and password on any computer joined to the domain is that users can easily access their resources and settings, regardless of which computer they are using. This is because the domain controller centrally manages user accounts, which means that user credentials are valid on any computer joined to the domain.
This also simplifies the administration and management of user accounts, as IT staff can easily manage and update user accounts from a central location.
However, this convenience can also pose security risks if user accounts are compromised. If an attacker gains access to a user's credentials, they can potentially access all resources and settings associated with that user across the entire domain. Therefore, it is important to implement strong password policies, two-factor authentication, and other security measures to prevent unauthorized access to user accounts.
- Describe how group policies are used in domains?
Group policies are a powerful tool used in domains to centrally manage and configure user and computer settings. Group policies can be applied at various levels within a domain, including at the domain level, or organizational unit (OU) level.
Group policies are used to enforce security settings, such as password complexity requirements. They can also be used to configure user preferences, such as disabling certain programs. Group policies can be used to deploy software, scripts, or updates across the domain, as well as to restrict access to certain resources or features.
Group policies can be created and managed using the Group Policy Management Console (GPMC) on a domain controller or a workstation with the Remote Server Administration Tools (RSAT) installed. Once a policy is created, it can be linked to a specific OU or applied to a specific group of users or computers. Group policies are applied in a specific order, known as the Group Policy processing order, to ensure that conflicting policies are resolved appropriately.
- In what other ways can you think of that domains could be used beyond what was presented in the reading?
Internet of Things (IoT) device management: Domains can be used to manage and secure IoT devices, such as sensors and smart devices, in a network environment. This includes managing access control, configuring settings, and monitoring and controlling device behavior.
Authentication for cloud services: Domains can be used to authenticate and authorize access to cloud services, such as Microsoft 365 or Google Workspace. This allows users to access cloud services using the same login credentials they use for on-premises resources, simplifying access management and reducing the need for multiple sets of credentials.
References
1 - https://www.howtogeek.com/194069/what-is-a-windows-domain-and-how-does-it-affect-my-pc/
2 - Computer Networking, "A Top-Down Approach", KUROSE ROSS, SEVENTH EDITION