Read: Class 07 Web Server Deployment - VascoLucas01/networking-reading-notes GitHub Wiki
Introduction
In recent years, Internet companies such as Google, Microsoft, Facebook, and Amazon (as well as their counterparts in Asia and Europe) have built massive data centers, each housing tens to hundreds of thousands of hosts, and concurrently supporting many distinct cloud applications (e.g., search, e-mail, social networking, and e-commerce). Each data center has its own data center network that interconnects its hosts with each other and interconnects the data center with the Internet.
In fact, there are many ways to design a network and in this Read it wil be discussed the three-tier architecture, software defined networking, spine and leaf configurations, the difference between north-sout traffic, network devices, connectors and standards.
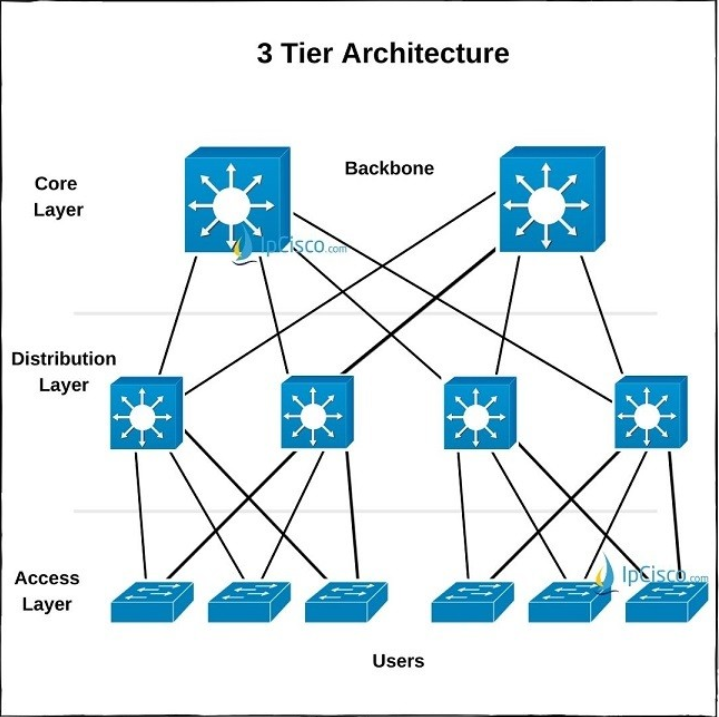
Three-Tier Architecture or Three-Layered Hierachical Model
This architecture is used by large enterprises because it is scalable and resilient solution for them. 3 Tier Architecture consists of three layers. These layers are:
-
Core of the Network - sometimes referred as the center of the network and this is usually where the major services are located (web servers, database servers, name servers, etc...).
-
Distribution - manages the communication between all of the users and the core of the network; provides redundancy and control of traffic into and out of the core.
-
Access - where users are located.
Core of the Network
Core layer is also known as Backbone Network. Core Layer connects distribution layer devices.
Routing protocols are used in this layer and the main duty of this layer is provifing routing between them and the distribution layer. Redundanct is also important fort his layer. So, redundant core devices are used to overcome single point of failure.
This hierarchical network is either important because it is easier to troubleshoot and easier to design.
Distribution Layer
Distribution layer is the middle layer of 3 Tier Architecture. This layer works as the bridge of Access Layer and Core Layer. It is the aggregation layer of all Access switches. Instead of Access layer switches, multilayer switches are used in Distribution layer.
Redundancy us used in this layer to overcome single point of failure.
Access Layer
Access Layer is the lower layer of 3 Tier Architecture. It is the closest layer to the end users. In this Access Layer, Access switches resides and users are connected to these switches.
In Access Layer, Network Access Policies, Layer 2 Security Mechanisms like Port Security are used. Beside, Layer 2 Loop prevention mechanims like STP, RSTP, PVST, MST are used in this layer. Another important and most used technolog in this layer is VLANs. With VLANs, different parts of the company is divided.
SDN Architecture
In recent years, we've taken this idea of physical networking components and we've tried to virtualize those systems, similar to what we've done with virtual servers. We've been able to take the different functions of these networking devices and separate them into separate functional planes of operation. There are three primary planes of operation:
- Data Plane
- Control Plane
- Management Plane

Data Plane
This is where the real work of the networking component is done.
All of the work to be able to forward traffic between locations is handled by the data plane.
Control Plane
However, then has to be something to manage what the data plane is doing, and that's managed from this plane.
Management Plane
Here, the network administrators need some way to control these devices.
This is the application layer of SDN architecture.
Spine and Leaf Architecture
With the new requirements to become more scalable, fast and efficient, a new datacenter design is developed. This design is replaced with three tier design that is used mostly in networking World. This technology that is also a good solution for evolving datacenters is called Spine and Leaf Architecture.
Spine and Leaf Architecture is the network architecture with which all the devices are the same segments away.

Spine Layer
Is the core layer. Routing is the first duty of this layer. Spline switches don't connect directly to each other.
Leaf Layer
Consists of access devices, switches, servers, edge routers, etc...
ADVANTAGES
- Simple cabling
- Redundancy
- Fast
DISAVANTAGES
- Additional switches may be costly
Futhermore, the leaf switches connect back to the spine, and then the spine determines where the traffic goes from there.
Traffic flows

East-West Traffic
Traffic between devices in the same data center.
Relatively fast response times.
North-South Traffic
Ingress/egress to an outside device.
Network Locations
There may be users in a branch office that need local devices. There might be a local switch, router, or firewall, or you may be installing client devices in that branch office. You might also isntall information in a on-premises data center. This is an in-house data center that you're responsible for. You manage the electrical systems, and you're responsible for the ongoing monitoring of those systems.
Your organization might also contract with a third-party to use their data center, or a portion of their data center, through something called co-location.
Network Devices
To make a network, it is needed a number of devices. Networks are built using multiple devices, such us:
- Routers
- Switches
- Access Points
- Cloud-based network controller
- Firewall
- Network interface card
- Repeater
- Hub
- Cable/DSL modem
- Bridge
- Patch panel
- Power over Ethernet (PoE)
- Ethernet over power
Routers
A router is used to connect LANs; you can even use a router to connect dissimilar toplogies that use the same protocol, because physical specifications don't apply. A router can be a dedicated hardware device or a computer system with more than one network interface and the appropriate routing software. All modern network operating systems include the functionality to act as a router.
Switches
Like routers, switches are the connectivity points of an Ethernet network. Devices connect to switches via twisted-pair cabling, one cable for each device. The difference between hubs and switches is in how the devices deal with the data they receive. Whereas a hub forwards the data it receives to all the ports on the device, a switch forwards it to only the port that connects to the destination device. It does this by learning the Media Access Control(MAC) address of the devices attached to it and then matching the destination MAC address in the data it receives.
Managed:
Managed switches are those used in an enterprise netwrok. These switches can be configured with advanced features such as virtual LANs (VLANs). They are managed remotely, using either a command-line interface or in some cases a GUI management interface.
Unmanaged:
Unmanaged switches are those that cannot be managed remotely; and while they can provide basic switching devices (full duplex service), they cannot be configured with the more advanced services of a managed switch.
Access Points
Access points (APs) are transmitter and receiver (transceiver) devices used to create a wireless LAN (WLAN). An AP is typically a separate network device with a built-in antenna, transmitter, and adapter. APs use the wireless infraestructure network mode to provide a connection between WLANs and a wired Ethernet LAN. APs also typically have several ports, giving you a way to expand the network to support additional clients.
Depending on the size of the network, one or more APs might be required. Additional APs are used to allow access to more wireless clients and to expand the range of the wireless network. Each AP is limited by a transmission range - the distance a client can be from an AP and still obtain a usable signal. The actual distance depends on the wireless standard being used and the obstructions and environmental conditions between the client and the AP.
Cloud-based network controller
The new paradigm in networking is to move the intelligence from the routers, switches, and access points to a cloud-based network controller. Software-defined networking uses a controller to manage all the routing switching and wireless control while the devices simply handle data forwarding.
Firewall
A firewall is a server that sits between the internal network and the rest of the world (or between a public and private network) and filters what goes between the two. While the filtering can be done on programs, most firewalls are created on ports since applications and protocols use ports that are recognized. Open ports are those that allow trafic, whereas closed ports are those that block traffic. The firewall can be software- or hardware-based, and most incorporate both. The firewal may incorporate a proxy, a gateway, and a filter.
Network interface card
Network interface cards (NICs) are expansion cards that are installed into slots in a desktop computer. These cards connect the computer to a network. In most cases today, devices large and small have integrated or built-in network interfaces.
Repeater
A repeater or extender is a device that regenerates any signal that goes through it. It can be used to exted«nd a cable run that exceeds the maximmum allowable distance. For example, if you needed to run a cable with a maximum allowable legth of 100 meters for 150 meters, you could put a repeater between two 75-meter lenghts of cable, and the problem would be solved.
Hub
Hubs are used in networks that use twisted-pair cabling to connect devices, and they can be used to join segments into larger networks. A hub directs data packets to all devices connected to it, regardless of whether the data package is destined for the device. This makes them inneficient by nature and can create a performance bottleneck on busy networks. In its most basic form, a hub does nothing except provide a pathway for electrical signals to travel along. Such a device is called a passive hub. Far more common nowadays is an active hub, which, as well as providing a path for the data signals, regenerates the signal before it forwards it to all the connected devices. In addition, an active hub can buffer data before it forwarding it. However, a hub does not perform any processing on the data i forwards, nor does it perform any error checking.
Cable/DSL modem
A modem, short for "modulator/demodulator", is a devices that converts the digital signals generated by a computer into analog signals that can travel over conventional phone lines. The modem at the receiving end converts the signal back into a format that the computer can understand. Modems can bu used to connect an ISP or as a mechanism for dialing up a LAN.
Cable and DSL modems, however, are not true modems in that they do not convert between analog and digital signal. These devices are really systems that take the information and place it on either the cable or DSL network so the SIP can transfer it to the internet and back.
Bridge
Bridges are used to divide larger networks into smaller sections. Bridges accomplish this by sitting between two physical network segments and managing the flow of data between the two. By looking at the MAC addressof the devices connected to each segment, bridges can elect to forward the data (if they believe thar the destination address is on another interface) or block it from crossing (if they can verify that it is on the interface from wich it came).
Patch Panel
A patch panel is a device to which the cables runnning through the walls from the hosts are connected. Then shorter cables called patch cables run from the patch panel to the switch or hub.
Power over Ethernet (PoE)
Many times when installing devices, the device needs to be located far from an available power outlet. On switches that support Power over Ethernet (PoE), the swotch can supply power on the same data cable used to connect to the device. So if you get the device within 100 meters of a switch, you can eliminate the need to install costly power outlets.
Injectors
A PoE injector is a device that can be used to provide PoE to a device when the switch does not support PoE. It plugs into the wall; then a line providing data and the PoE is run to the device, and another cable runs to the switch.
Switch
Enterprise-grade switches such as Cisco switches can also some equipped with PoE ports. The ports can be set to provide power to the devices connected.
Ethernet over Power
Ehternet over Power is a technology designed to enable the sending of Ethernet frames over the power lines in a facility.
Network Connectors
Local Connector (LC)

Straight Tip Connector (ST)

Subscriber Connector (SC)
MT-RJ or Mechanical Transfer Register Jack

Fiber Optics
There's all sorts of physics that go into the idea of making sure the optimal amount of light is getting from the beginning to the very end of the connection.
Return loss is how much light is reflected back to the source and thereby creating an inefficiency in the amount of light that you're able to send to the other side.
To be able to minimize the amount of return loss, we have different connectors that we might use:
UPC connector
Ultra-polished connector where the ferrules are connecting together at a 0-degree angle.
APC connector
Angled polished connector, because there is a very slight 8-degree angle between the connector types.
RJ-11
An RJ-11 is a standard connector for a telephone line and is used to connect a computer modem to a phone line.
RJ-45
A registered jack (RJ) is a plastic plug with small metal tabs, like a telephone cord plug. Numbering is used in the naming: RJ-11 has two metal tabs, and RJ-14 has four. RJ-45 has eight tabs and is used for Ethernet 10 BaseT/100 BaseT, 1000Base, and 10GBase networking. The maximum cable lenght is 100 meters but can vary slightly based on the category cabling used.
F-connector
This is a coaxial connector. This is the type of connector you will find on a cable modem. And it follows the standards assocaited with DOCSIS or Data Over Cable Service Interface Specification. Many times this is an RG-6 type of coax cable.

Ehternet Standards
- 10BASE-T
- 100BASE-TX
- 1000BASE-T
- 10GBASE-T
- 40GBASE-T
- 100BASE-FX
- 100BASE-SX
- 1000BASE-SX
- 1000BASE-LX
- 10GBASE-SR
- 10GBASE-LR
Taking as an example the 10BASE-T, the 10 would be for 10-megabit, the BASE would be for the baseband technology that's used on that wire, and generally, you'd see a T or a TX at the end to specify that that is a twisted pair.
Cat 5
Cat 5 transmits data at speeds up to 100 Mbps and was used with Fast Ethernet (operating at 100 Mbps) with a transmission range of 100 meters. It contains four twisted pairs of copper wire to give the most protection. Although it had its share of popularity (it's used primarily for 10/100 Ethernet working), it is now an outdated standard. Newer implementations use the 5e standard.
Cat 5e
Cat 5e transmits data at speeds up to 1 Gbps (1000Mbps). Category 5e cabling can be used up to 100 meters, depending on the implementation and standard used and provides a minimum of 100 MHz of bandwidth. It also contains four twisted pairs of copper wire, but they're phusically separated and contain more twists per foot than Category 5 to provide maximum interference protection.
Cat 6
Cat 6 transmits data at speeds up to 10 Gbps, has a minimum of 250 MHz of bandwidth, and specifies cable lenghts up to 100 meters (using Cat 6a). It contains four twisted pairs of copper wire and is used in 10GBaseT networks. Category 6 cable typically is made up of four twisted pairrs of cooper wire, but its capabilities far exceed those of other cable types. Category 6 twisted pair uses a longitudinal separator, which separates each of the four pairs from each other and reduces the amount of crosstalk possible.
Plenum
Plenum cable is a specific type of cable that is rated for use in plenum spaces - those spaces in a building used for heating and air-conditioning systems. Most cable cannot be used in the plenum because of the danger of the fire (or the fumes the cable give off as they burn). While it is more expensive, plenum calbe is fire-rated and meets the necessary standards, which makes it acceptable to use in these locations. It replaces PVC with a Teflon-like material.
Shielded Twisted Pair
Shielded twisted pair (STP) differs from unshielded twisted pair (UTP) onli in the preence of the shielding, which resembles aluminum foil directly beneath the outer insulation. The shielding adds to the cost of the cable, eliminates interference from the outside the cable and as a rule of thumb based on current prices is that STP is 30 percent more expensive than ITP for the same length of cable.
Unshielded Twisted Pair
Unshielded twisted pair (UTP) is the most populat twisted-pair cabling in use and should be used in any scenario where external interference is not an issue.
Questions
- What are some common use cases for NGINX?
NGINX is a popular web server and reverse proxy that can also function as a load balancer, HTTP cache, and content delivery network (CDN). Some common use cases for NGINX include -> Web serving, load balancing, reverse proxy, etc...
- How does NGINX handle tasks that could slow down the web server?
NGINX have and asynchronous architecture, caching and load balacing that helps handling the tasks. The more interesting, for me, is the asynchronous architecture which allows the server to handle multiple requests concurrently without blocking any one connection. This is in contrast to a traditional synchronous architecture, which processes each request sequentially, one at a time.
- Describe, as if to a non-technical friend how to actually pronounce “NGINX”, and why an org might chooose to use it.
"NGINX" can be pronounced as "engine-ex". The reason an org might choose to use it is because NGINX is a powerful web server that can handle a lot of traffic and perform many different tasks, like serving web pages, handling requests, and load balancing. It's especially useful for large organizations or websites that get a lot of traffic because it can help improve website speed and stability.
REFERENCES
1 - https://ipcisco.com/lesson/network-topology-architectures/
2 - https://www.ciscopress.com/articles/article.asp?p=2995354&seqNum=2
3 - https://www.professormesser.com/network-plus/n10-008/n10-008-video/network-architectures-n10-008/
5 - https://www.professormesser.com/network-plus/n10-008/n10-008-video/network-connectors-2/
6 - https://www.professormesser.com/network-plus/n10-008/n10-008-video/ethernet-standards-n10-008/
7 - A+ Complete Review Guide, Network+
THINGS THAT I WANT TO KNOW MORE ABOUT
What is the main difference between a switch and a bridge?