Threat intel guide - V1D1AN/S1EM GitHub Wiki
With S1EM, you have two tools to do Threat Intel which are MISP and OpenCTI.
When you have change the default password in MISP, you have this interface:
Now you need to enable feeds to get information from open sources, go to Sync Actions and List feeds:

Select all feeds (1) and click on Enable Selected (2):

Click on Yes for Enable Feed(s) and click on Fetch and store all feed data (3).
Go to Administration and Jobs for verify the synchronization:
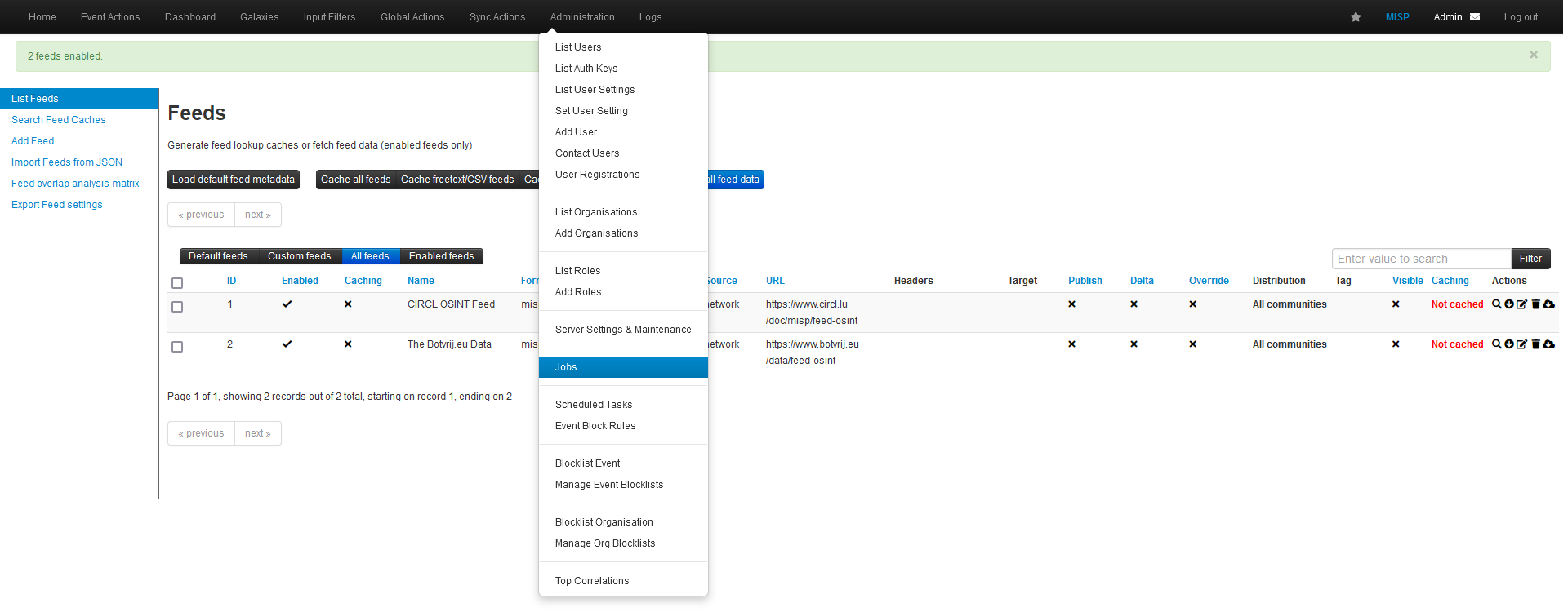
You must see the jobs starting:
Now, you must have events in MISP:
With S1EM, you have already rules for matching your log with IOC from MISP:
You can add your own feeds for having others Indicators of compromise.
Alienvault OTX is a good feeds of informations. You have only the basic with S1EM.
After you are logging on OpenCTI, you arrive to homepage:
Just after the deploy of S1EM, OpenCTI pull informations from MITRE:
When OpenCTI finish with MITRE, OpenCTI will get informations from your MISP configured, with S1EM, MISP and OpenCTI are interconnected:
After Opencti get all informations, you can use Cortex for search observables into OpenCTI.
With S1EM, you have the basic of connector, you can add several connectors.
For this, you go on https://github.com/OpenCTI-Platform/connectors
