Home - Theo88/Apk_Secu GitHub Wiki
Welcome to the Apk_Secu wiki!
Online tools:
- MobSF DynamicAnalyzer https://mobsf.live/
Offline tools:
SSLUnpinning - Certificate Pinning Bypass TrustMeAlready
- Android Emulators https://www.genymotion.com/

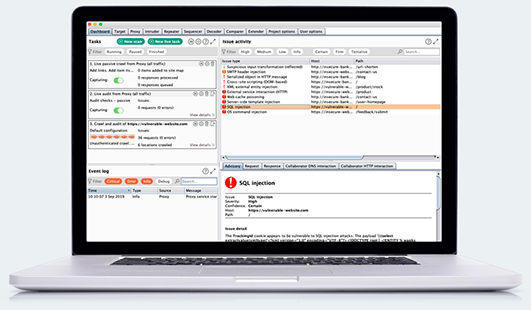
- Burp Suite https://portswigger.net/burp
- ByteCode Viewer https://bytecodeviewer.com/

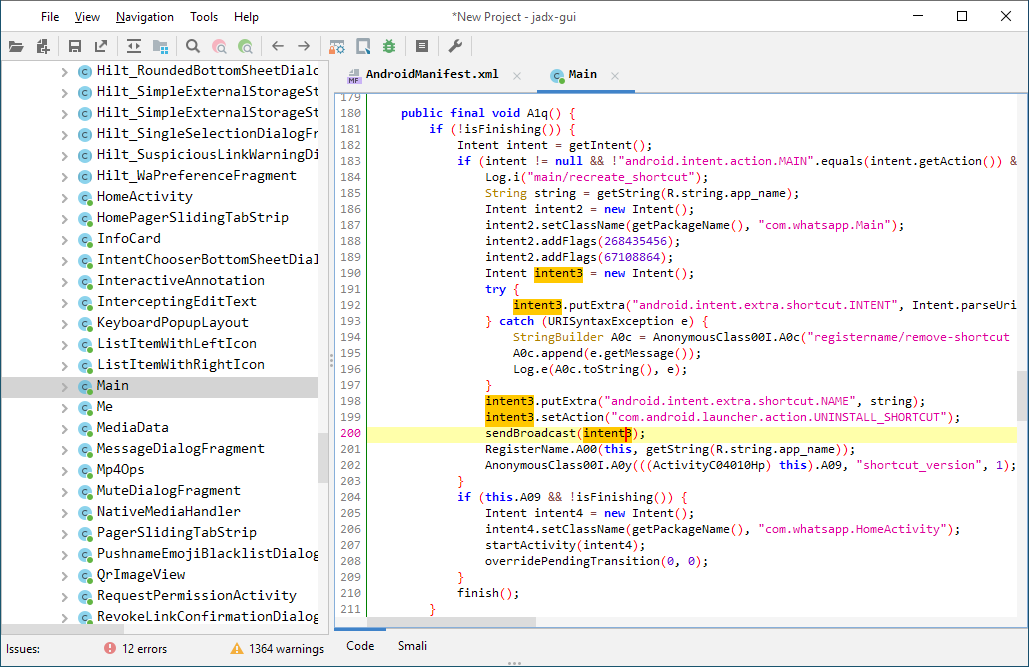
- JADX - Dex to Java decompiler https://github.com/skylot/jadx
- APK Easy Tool https://forum.xda-developers.com/t/discontinued-windows-apk-easy-tool-v1-60-2022-06-23.3333960/
- dbSPY DLL usefull for Xamarin dll investigation https://github.com/dnSpy/dnSpy

List of OpCodes https://7d2dsdx.github.io/Tutorials/index.html?OpCodesExample.html
-
Decompress DLL from xamarin with "python Xamarin_XALZ_decompress.py name-of-compress.dll name-of-newfile.dll" source python script: https://github.com/x41sec/tools/blob/master/Mobile/Xamarin/Xamarin_XALZ_decompress.py
-
DLL investigation ILSpy https://github.com/icsharpcode/ILSpy
-
Raccoon - The APK downloader from google Play Store: https://raccoon.onyxbits.de/ https://github.com/onyxbits/Raccoon *** Use a different account from your regular one to login on google playstore and use Raccoon

- An Intent traffic monitoring tool. [2Y2s1mple] /[xintent] https://github.com/2Y2s1mple/xintent

# Learning:
- https://www.youtube.com/AndroidAppSec
- https://github.com/RavikumarRamesh/hpAndro1337/tree/main/Android%20AppSec%20(Kotlin)
- Frida https://www.youtube.com/watch?v=iMNs8YAy6pk&list=PLXTKrjaFK4buFqW36Ci-b9dTOxjDTdAI4&index=3
- Android Application Pentesting - Mystikcon 2020 https://www.youtube.com/watch?v=NrxTBcjAL8A
- Android Application Pinning Bypass | Pinned @ HackTheBox https://www.youtube.com/watch?v=CJR_BSIStmE&t=318s
- https://maoutis.github.io/
- Step by step guide link FRIDA Genymotion and Burp Suite https://arben.sh/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/