Configuring a Thales SafeNet Luna HSM Provider - Senetas/SKC GitHub Wiki
Install the Windows Client
Before using the Thales Luna HSM with Senetas Key Orchestrator, the Thales Luna SA client must be installed and configured.

Install the Safenet Luna SA client
Configure the Connection between the HSM and the Windows Server
This example assumes that there is already a partition already created called suredrop on this HSM
Make sure that the HSM and the Windows Client can ping each other and there are no firewalls in-between
c:\Program Files\SafeNet\LunaClient>pscp [email protected]:server.pem .
[email protected]'s password:
server.pem | 1 kB | 1.1 kB/s | ETA: 00:00:00 | 100%
Copy the HSM certificate to the client
c:\Program Files\SafeNet\LunaClient>vtl addServer -n 192.168.20.101 -c server.pem
vtl (64-bit) v10.2.0-111. Copyright (c) 2020 SafeNet. All rights reserved.
New server 192.168.20.101 successfully added to server list.
Register the HSM certificate with the client
c:\Program Files\SafeNet\LunaClient>vtl createcert -n 192.168.20.102
vtl (64-bit) v10.2.0-111. Copyright (c) 2020 SafeNet. All rights reserved.
Private Key created and written to: C:\Program Files\SafeNet\LunaClient\cert\client\192.168.20.102Key.pem
Certificate created and written to: C:\Program Files\SafeNet\LunaClient\cert\client\192.168.20.102.pem
Create a client certificate
c:\Program Files\SafeNet\LunaClient>pscp cert\client\192.168.20.102.pem [email protected]:
[email protected]'s password:
192.168.20.102.pem | 1 kB | 1.1 kB/s | ETA: 00:00:00 | 100%
Copy the client certificate to the HSM
[hsm-shared-dc3-01] lunash:>client register -client 192.168.20.102 -ip 192.168.20.102
'client register' successful.
Command Result : 0 (Success)
Register the client certificate on the HSM
[hsm-shared-dc3-01] lunash:>service restart ntls
Checking for connected clients before stopping NTLS service:
There are no connected clients. Proceeding...
Stopping ntls:OK
Starting ntls:OK
Command Result : 0 (Success)
Restart the NTLS service
[hsm-shared-dc3-01] lunash:>client assignPartition -client 192.168.20.102 -partition suredrop
'client assignPartition' successful.
Command Result : 0 (Success)
Assign a partition to the client on the HSM
[hsm-shared-dc3-01] lunash:>client show -client 192.168.20.102
ClientID: 192.168.20.102
IPAddress: 192.168.20.102
HTL Required: no
OTT Expiry: n/a
Partitions: "suredrop"
Command Result : 0 (Success)
Confirm that the client is registered correctly
c:\Program Files\SafeNet\LunaClient>vtl verify
vtl (64-bit) v10.2.0-111. Copyright (c) 2020 SafeNet. All rights reserved.
The following Luna SA Slots/Partitions were found:
Slot Serial # Label
==== ================ =====
0 482052008 suredrop
Verify the slot on the client
c:\Program Files\SafeNet\LunaClient\CSP>register /library
register (64-bit) v10.2.0-111. Copyright (c) 2020 SafeNet. All rights reserved.
Success registering SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Luna enhanced RSA and AES provider for Microsoft Windows.
Success registering SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Luna Cryptographic Services for Microsoft Windows.
Success registering SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Luna SChannel Cryptographic Services for Microsoft Windows.
Register the CSP provider on the client
c:\Program Files\SafeNet\LunaClient\CSP>register
register (64-bit) v10.2.0-111. Copyright (c) 2020 SafeNet. All rights reserved.
***************************************************************************
* *
* Safenet LunaCSP, Partition Registration *
* *
* Protect the HSM's challenge for the selected partitions. *
* *
* NOTE: *
* This is a WEAK protection of the challenge. *
* After you have configured all applications that will use *
* the LunaCSP and ran them once, you MUST run: *
* register /partition /strongprotect *
* to strongly protect the registered challenges. *
* *
***************************************************************************
This is a destructive procedure and will overwrite any previous registrations.
Do you wish to continue?: [y/n]y
Do you want to register the partition named 'suredrop'?[y/n]: y
Enter challenge for partition 'suredrop' :*************
Success registering the ENCRYPTED challenge for partition 'suredrop:0'.
Only the LunaCSP will be able to use this data.
Registered 1 partition(s) for use by the LunaCSP.
Register the partition with CSP
(You will need to enter the PED pin)
Configure the Windows KSP Provider

Find the KspConfig utility and run it

c:\Program Files\SafeNet\LunaClient\cryptoki.dll

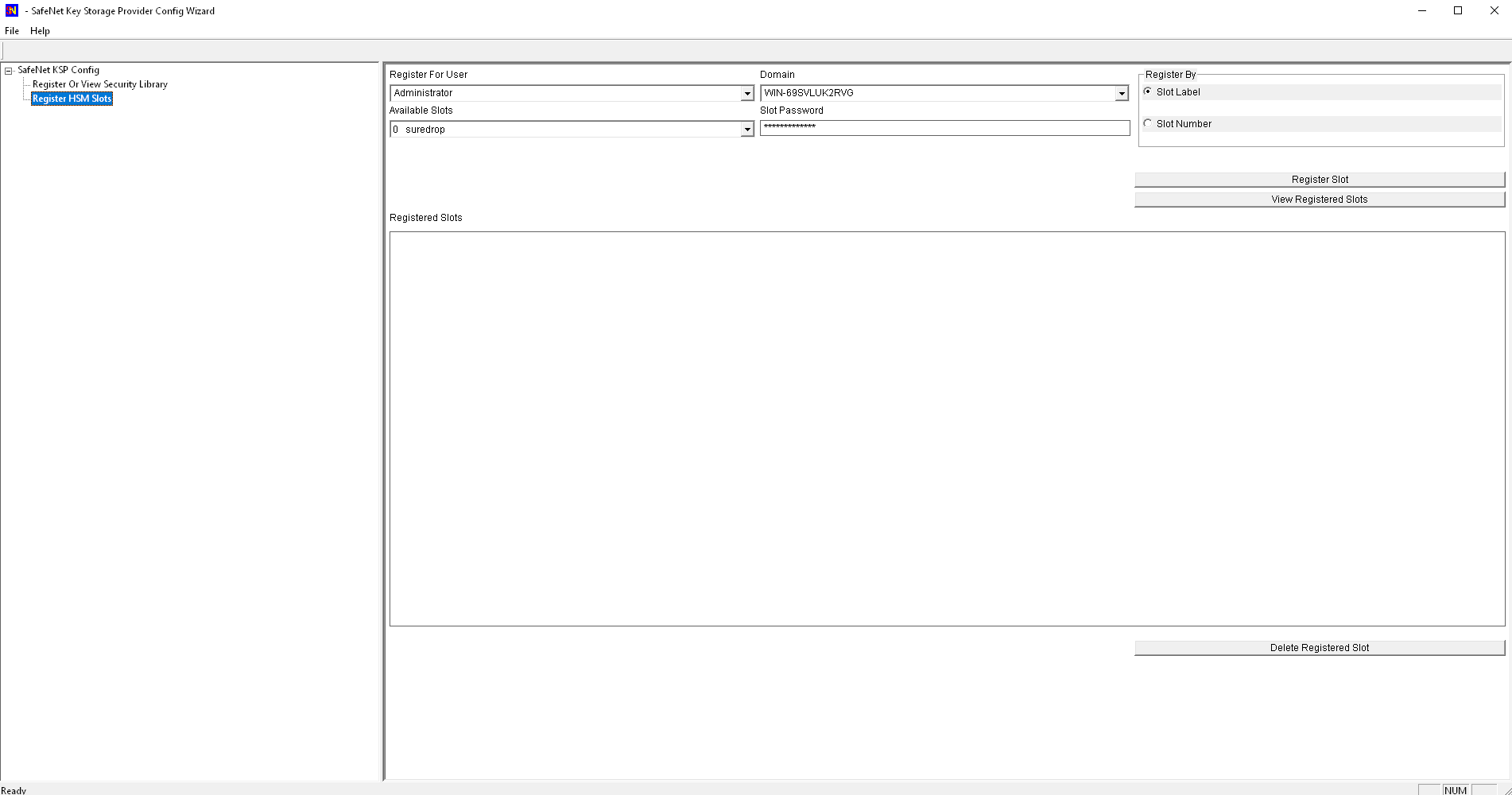
Click on Register HSM Slots and enter the slot password. Then click on Register Slot
(You will need to enter the PED pin)
 Do the same for the
Do the same for the SYSTEM account under the NT AUTHORITY domain.
Configure the HSM Provider in SKC
In SKC goto Manage -> Providers > Add
 Select
Select 5. Add SafeNet Luna HSM

Select Yes to this prompt if you have followed the instructions above

Enter a name and a description and priority

Enter the name of the key that will be automatically created in the HSM in the registered domain slot.

Confirm the creation of this provider.
*** Important ***
Encrypt at least one item using the Crypto -> Encrypt function.
You will need to enter the PED pin the very first time an encrypt operation is run