03 ~ Attacking ~ Detection Diagrams - SYWorks/wireless-ids GitHub Wiki
Diagram of Hacking/Detection Process

Step-by-step Attacking/Detection diagram
-
Attacker setting up his fake access point similar to victim’s AP name

-
WIDS detected Evil Twins

-
Attacker sent deauthentication to client & Access Point
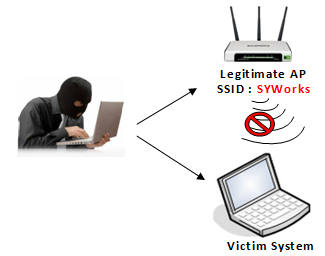
-
WIDS detected Deauth flooding.
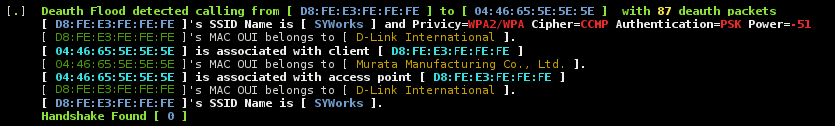
-
Victim carelessly connected to the fake access point set by attacker

-
Change in connection from one access point to another

Support & Like My Page SYWorks