Home - PaloAltoNetworks/minemeld GitHub Wiki

What is MineMeld?
An extensible Threat Intelligence processing framework brought to you by Palo Alto Networks.
What is MineMeld for?
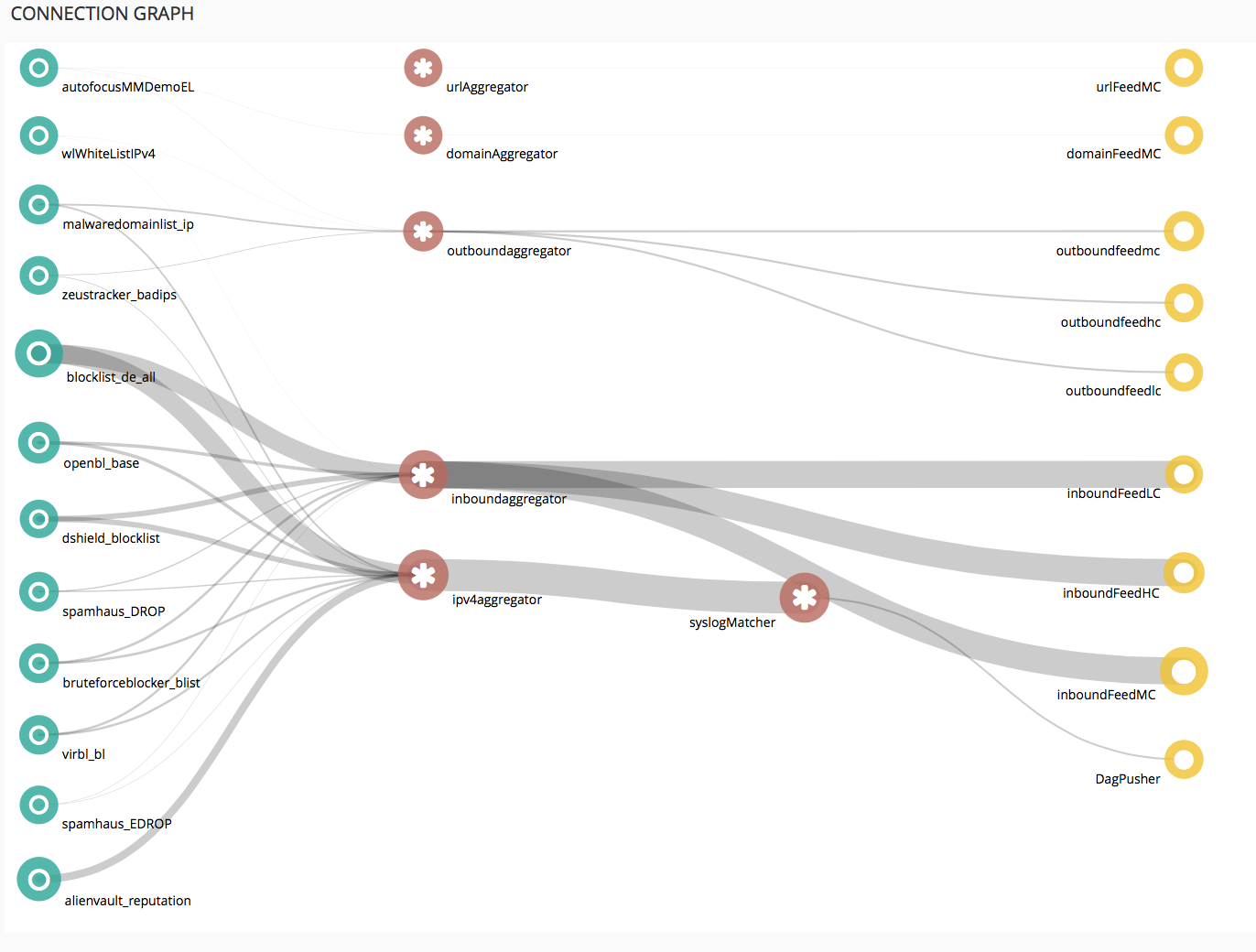
MineMeld is a community supported tool to manipulate list of indicators and transform/aggregate them for consumption by third party enforcement infrastructure. MineMeld has many use-cases and can easily be extended to fulfill many more. Here are a few examples:
- Connect to the Spamhaus DROP feed and transform it for enforcement by Palo Alto Networks EDL (External Dynamic List) objects
- Mine Office 365 IP addresses provided by Microsoft and dynamically create an EDL list for usage in a Palo Alto Networks security policy to further restrict trafic
- Aggregate CERTs and ISACs Threat Intelligence feeds, removing duplicates, expiring entries and consolidating attack directions and confidence levels then make this list available for enforcement by third party tools
- Extract indicators from syslog messages and aggregate them with indicators coming from 3rd party sources
Check this page for a brief list of currently supported nodes/feeds.
Where from here?
- Install and Use MineMeld
- Read about MineMeld Architecture
Where is the code?
There are 2 main components of MineMeld. Each component has its own repo:
The library of node prototypes is maintained in minemeld-node-prototypes.
How can I contribute?
- Read the contribution guidelines
- Follow the developer's guide to bootstrap your development environment
- Read how to write a simple Miner
Additional material
Check the recordings of the Palo Alto Networks Ignite 2016 plenary session to know more about MineMeld. If you are looking for some introductory videos about Threat Intelligence you can check the videos of Palo Alto Networks Unit42 Ignite sessions (1, 2). If instead you are looking for a good introduction to Threat Indicators, check this great video from Kyle Maxwell and Alex Pinto.