Gateway Login - OpenBankProject/OBP-API GitHub Wiki
Introduction
Gateway Login Authorisation is made by including a specific header (see step 3 below) in any OBP REST call.
Note: Gateway Login does not require an explicit POST like Direct Login to create the token.
The Gateway is responsible for creating a token which is trusted by OBP absolutely!!
When OBP recieves a token via Gateway Login, OBP creates or gets a user based on the username supplied.
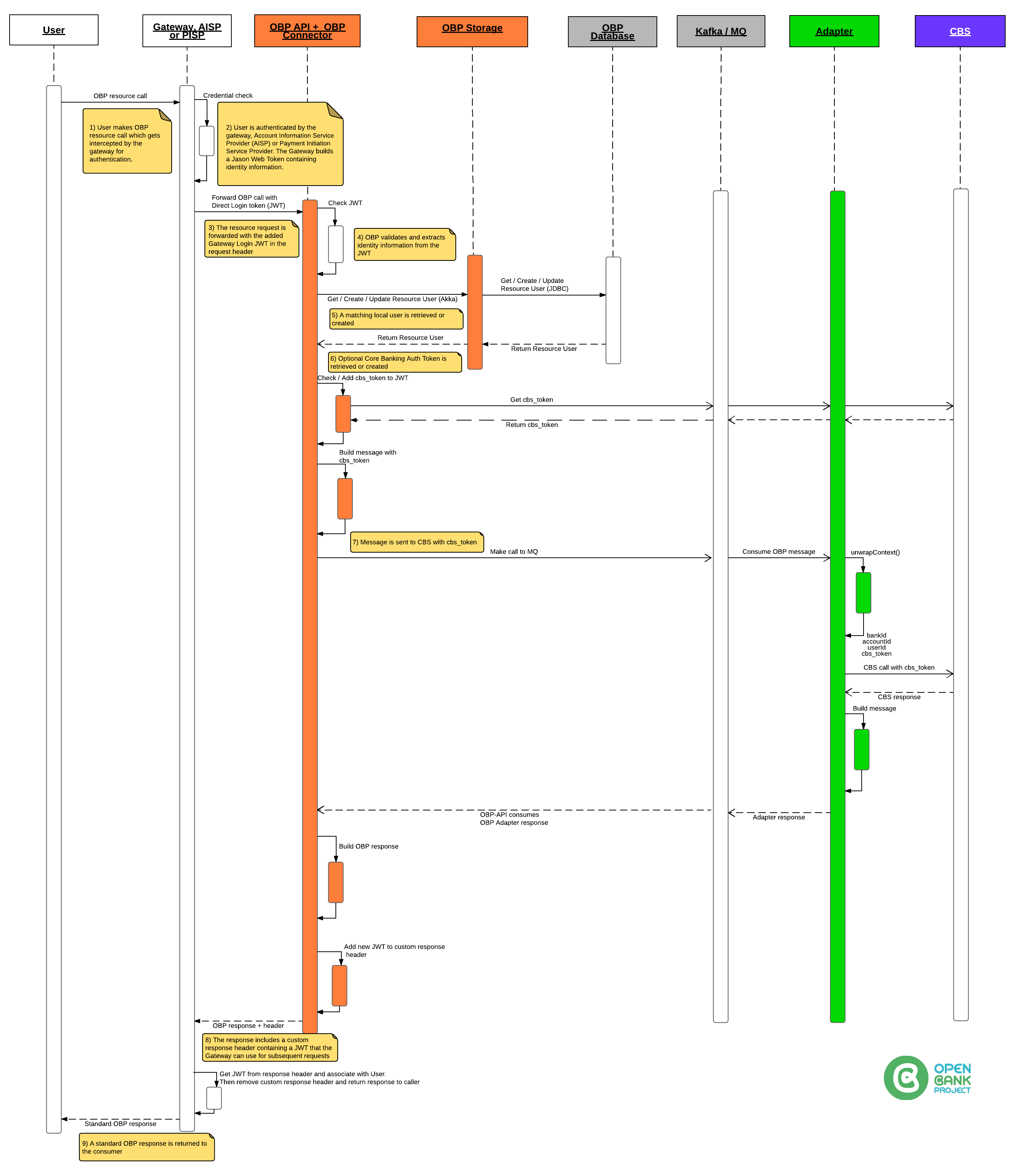
To use Gateway Login:
1) Configure OBP API to accept Gateway Login.
Set up properties in a props file
# -- Gateway login --------------------------------------
# Enable/Disable Gateway communication at all
# In case isn't defined default value is false
# allow_gateway_login=false
# Define comma separated list of allowed IP addresses
# gateway.host=127.0.0.1
# Define secret used to validate JWT token
# gateway.token_secret=secret
# -------------------------------------- Gateway login --
Please keep in mind that property gateway.token_secret is used to validate JWT token to check it is not changed or corrupted during transport.
2) Create / have access to a JWT
HEADER:ALGORITHM & TOKEN TYPE
{
"alg": "HS256",
"typ": "JWT"
}
PAYLOAD:DATA
{
"username": "simonr",
"is_first": true,
"timestamp": "timestamp",
"consumer_id": "123",
"consumer_name": "Name of Consumer"
}
VERIFY SIGNATURE
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
) secret base64 encoded
Here is the above example token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
AS8D76F7A89S87D6F7A9SD876FA789SD78F6A7S9D78F6AS79DF87A6S7D9F7A6S7D9F78A6SD798F78679D786S789D78F6A7S9D78F6AS79DF876A7S89DF786AS9D87F69AS7D6FN1bWVyIn0.
KEuvjv3dmwkOhQ3JJ6dIShK8CG_fd2REApOGn1TRmgU
3) Try a REST call using the header
Using your favorite http client:
GET /obp/v3.0.0/users/current
Body
Leave Empty!
Headers:
Authorization: GatewayLogin token="your-jwt-from-step-above"
Here is it all together:
GET /obp/v3.0.0/users/current HTTP/1.1 Host: localhost:8080 User-Agent: curl/7.47.0 Accept: / Authorization: GatewayLogin token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9. AS8D76F7A89S87D6F7A9SD876FA789SD78F6A7S9D78F6AS79DF87A6S7D9F7A6S7D9F78A6SD798F78679D786S789D78F6A7S9D78F6AS79DF876A7S89DF786AS9D87F69AS7D6FN1bWVyIn0. KEuvjv3dmwkOhQ3JJ6dIShK8CG_fd2REApOGn1TRmgU"
CURL example
curl -v -H 'Authorization: GatewayLogin token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
AS8D76F7A89S87D6F7A9SD876FA789SD78F6A7S9D78F6AS79DF87A6S7D9F7A6S7D9F78A6SD798F78679D786S789D78F6A7S9D78F6AS79DF876A7S89DF786AS9D87F69AS7D6FN1bWVyIn0.
KEuvjv3dmwkOhQ3JJ6dIShK8CG_fd2REApOGn1TRmgU" http://localhost:8080/obp/v3.0.0/users/current
You should receive a response like:
{
"user_id": "33fd104f-3e6f-4025-97cc-b76bbdc9148e",
"email": "[email protected]",
"provider_id": "marko.milic",
"provider": "https://tesobe.openbankproject.com",
"username": "marko.milic",
"entitlements": {
"list": []
}
}
and custom response header i.e. OBP returns a new token in the custom response header called GatewayLogin (to the Gateway)
{
"username": "simonr",
"CBS_auth_token": "fapsoidfuipoi889w3ih", (Encrypted by OBP Adapter)
"timestamp": "timestamp",
"consumer_id": "123",
"consumer_name": "Name of Consumer"
}
GatewayLogin token="eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9. AS8D76F7A89S87D6F7A9SD876FA789SD78F6A7S9D78F6AS79DF87A6S7D9F7A6S7D9F78A6SD798F78679D786S789D78F6A7S9D78F6AS79DF876A7S89DF786AS9D87F69AS7D6FN1bWVyIn0. KEuvjv3dmwkOhQ3JJ6dIShK8CG_fd2REApOGn1TRmgU"
Under the hood
The file, GatewayLogin.scala handles the Gateway Login.
We:
-> Check if Props allow_gateway_login is true
-> Check if GatewayLogin header exists
-> Check if getRemoteIpAddress is OK
-> Look for "token"
-> If "is_first" is true -OR- CBS_auth_token is empty then, call CBS to get accounts
The CBS_auth_token (either the new one from CBS or existing one from previous token) is returned in the GatewayLogin custom response header.
More information
Parameter names and values are case sensitive.
Each parameter MUST NOT appear more than once per request.