4. SIEM Implementation (A Home Lab) - OmarFloresE/HomeNetSecUpgrade GitHub Wiki
Note: Optional Advanced Section
Implementing a Security Information and Event Management (SIEM) system in a home network can be seen as overkill for typical use.
However, if you're enthusiastic about diving deep into network security – much like lifting the hood of a car to understand the intricacies of its engine – then this section is definitely for you. Utilizing a SIEM as a home lab not only offers a fascinating insight into how data flows within your network but also serves as an excellent practical learning tool. This is particularly beneficial for those aspiring to become SOC Analysts or join a cybersecurity Blue Team. Here, you’ll get a hands-on experience in monitoring, analyzing, and responding to security events, a cornerstone skill in these fields.
Hands on experience is something you just have to create for yourself sometimes my fellow nerds!
What is a SIEM? (Security Information & Event Management)
-
Definition and Function: SIEM combines security information management (SIM) and security event management (SEM) to provide real-time analysis of security alerts generated by applications and network hardware.
-
Core Capabilities: It collects and aggregates log data, provides alerting, dashboards, and advanced analytics for anomaly detection. (Something unusual happening within your network? It can send a proper alert)
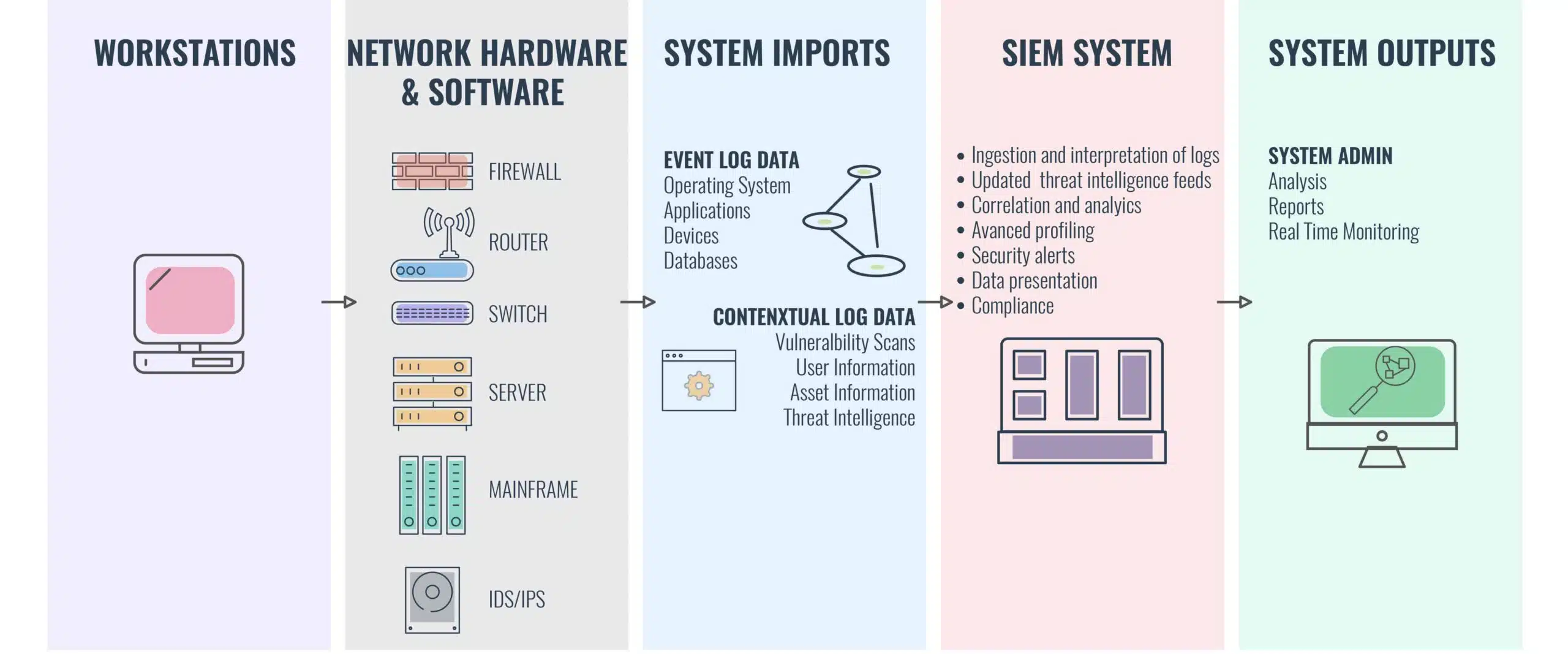
Benefits of SIEM in your Home Network
Here are 3 good reasons to implement and gain some practical experience from a SIEM Home Lab!
1. Enhanced Network Visibility:
-
Comprehensive Monitoring: SIEM provides an overview of all the activities across your network. This includes traffic patterns, connected devices, and any anomalies.
-
Centralized Dashboard: Most SIEM systems offer a dashboard that consolidates all your security alerts and logs in one place, making it easier to monitor your network's health.
2. Advanced Threat Detection:
-
Real-time Alerts: SIEM systems can analyze network data in real time and alert you to potential threats, such as unauthorized access attempts or suspicious traffic.
-
Pattern Recognition: By continually analyzing your network traffic, SIEM can help identify patterns that might indicate a cybersecurity threat.
3. Learning and Skill Development (Most Importantly!):
-
Practical Experience: For those interested in a career in cybersecurity, a home SIEM system offers a hands-on way to learn about network monitoring, threat detection, and response.
-
Understanding Data Flows: Managing a SIEM provides insight into how data moves across your network, helping you understand and protect it better.
-
Forensic Analysis: In case of a security breach, SIEM logs can provide valuable forensic information to understand what happened and how to prevent future incidents.
Choosing a SIEM Tool
Choosing the right SIEM tool for your home network lab can be daunting at first, because there is no shortage of options! And not to mention ways of implementing said options, but I am getting ahead of myself there.
Deciding on the right SIEM tool for your home network lab involves balancing functionality, ease of use, and your credit card bill at times. While there are numerous options available, from industry standards like Splunk to the open-source alternatives like ELK Stack, the key is to find a tool that aligns with your specific situation and learning goals.
Key Things To Consider
-
Ease of Use: Some tools are way more user friendly than others and have a less steep learning curve! I would recommend working your way up and experimenting with progressively steeper learning curves.
-
Features and Capabilities: Assess the features offered, such as log management, threat detection, compliance reporting, and real-time monitoring. Match these with what you need for your home network and want to experiment with!
-
Scalability: Even if your current network is small, consider whether you might want to expand your SIEM usage in the future. A scalable solution can grow with your needs. For example you can make more computers in your network with VMs to simulate a small office environment.
-
Community and Support: Especially important for open-source tools, a strong community and available support can be invaluable for troubleshooting and learning.
-
Cost: Factor in the cost, keeping in mind that some tools, like Splunk, offer free versions with limited capabilities which might be sufficient for home use, and there are other tools that only offer free trials.
Explore your different options! You don't have to follow this Wiki to the last detail, this could just be a catalyst to you going off the beaten path and really taking the initiative to learn something on your own!
Here are some popular SIEM Tools out there:
Popular SIEM Tools
-
Splunk
Pros: Widely used in the industry, powerful features, extensive documentation.
Cons: Can be complex for beginners, the free version has data limitations.
-
ELK Stack (Elasticsearch, Logstash, Kibana)
Pros: Open-source, highly customizable, good for handling large volumes of data.
Cons: Requires more setup and configuration, steeper learning curve.
-
Wazuh
Pros: Open-source, integrates well with ELK Stack, good for threat detection and response.
Cons: Might require some technical proficiency to set up and manage.
-
Security Onion
Pros: Comprehensive suite for network security monitoring, includes various tools.
Cons: Best suited for users with some background in network security.
A wise man once said,
"If it's free, it's for me".
Wazuh, an open source titan
For our SIEM implementation, we’ll focus on setting up Wazuh in a virtual machine environment. Wazuh is a powerful open-source collection of tools for network security monitoring, including intrusion detection, monitoring, and log management, making it an ideal choice for a home SIEM system for learning valuable concepts!
Setting Up the SIEM Environment
Implementation Options
There are a couple different ways to implement a SIEM in your home network! These are some of your options:
1. Personal/dedicated Device
- For direct access and convenience sake you can monitor your network activity from your everyday personal device! A possible drawback is that a SIEM can be resource intensive.
2. Virtual Machine
- A dedicated virtual environment running in isolation from your main operating system helps reduce risks and you can gain valuable experience using different environments such as Kali Linux and suite of tools for testing and monitoring.
3. Raspberry Pi
- A cost-effective and compact option to consider, with great learning opportunities! While there are performance issues to consider you should be able to get away with using something like a Raspberry Pi model 3/4 for a small home network.

For This Lab We'll Use!

For this Home Lab we will be using Virtual Box (by Oracle) to create VMs and deploy Kali Linux to send telemetry, and Ubuntu Desktop with Wazuh configured inside to host the SIEM manager and create agents.
Setting Up Your Virtual Environments
1. Choose Your Virtualization Platform of Choice
- I am going to be using Virtual Box by Oracle. https://www.virtualbox.org/
2. Download a VM/ISO
- I will getting the prebuilt Kali Linux VM from the official website.
- I will also be downloading the ISO file for the Ubuntu desktop from the link below and booting it up in Virtual Box.
https://www.kali.org/get-kali/#kali-virtual-machines | https://ubuntu.com/download/desktop
3. Load the VM/ISO within the Virtual Box
- Both of the credentials should be Kali/Kali for the Kali Linux VM
- Make sure to give Ubuntu the necessary resources to host Wazuh effectively!
- Adjust the setting as necessary, I would recommend this video by Network Chuck if you are totally new to Virtual Machines it provides great insight towards how they work and the settings
Implementing Kali Linux and Ubuntu is straight forward enough, but Wazuh will require additional considerations.
Wait, How Does Wazuh Work?
Wazuh is an open-source SIEM platform for threat detection and incident response, renowned for its adaptability and integration capabilities! Here's a quick breakdown on how it works:
The image above is from the official website describing the main components that make up the structural workflow of Wazuh. Although the indexer, server, and dashboard still remain the integral parts of Wazuh, there has been a evolution in the way people may refer to them as. Below is how these components may get referred by and described as:
1. Wazuh Server (previously known as Wazuh Manager):
This is the central component of the Wazuh architecture, analogous to what was previously referred to as the Wazuh Manager. It processes data sent by Wazuh Agents and executes analytical and response actions.
2. Wazuh Indexer (integration with Elastic Stack):
The Wazuh Indexer is a powerful, highly scalable tool that indexes and stores the security events received from the Wazuh Server. It similar in function to Elasticsearch in the traditional Elastic Stack. This component is essential for managing the high volume of data in a way that facilitates efficient searching and analysis.
3. Wazuh Dashboard (integration with Kibana):
The Wazuh Dashboard is a web-based user interface that provides visualization and insights into the data processed by Wazuh. It replaces what was traditionally accomplished with Kibana in the Elastic Stack, offering a more integrated and Wazuh-focused user experience for data management, visualization, and reporting.
Everything is very customizable and user friendly, which is what makes Wazuh so awesome! Apart from being totally free too!
Another term you will see often when it comes to Wazuh is the flexible deployment of agents that act as endpoints for your SIEM. You can think of them as an extra set of eyes for your SIEM, or the kids in the classroom that tell the teacher everything about everyone.
The flexibility of these agents is astounding as you can deploy them on almost any type of architecture and machine.
Now that you understand the major concepts of what makes Wazuh tick let's jump right into the installation process!
Deploying Wazuh on Ubuntu!
Installation
Installing Wazuh is surprisingly simple! It is a straightforward process, but I will always encourage you to go look at the official and up to date documentation! Reading documentation is as unavoidable as taxes buddy.
If you don't feel like exploring the docs today, that's okay stick with me here and follow these steps to get your Wazuh environment up and running!
Prerequisites (Set the stage here)
Ensure that your Ubuntu Desktop VM is set up and running!
I have mine at 120gbs of storage, 4 cores, and 8gbs of RAM along with the network settings set to Bridged Adapter.
And now we're off to the races.
Step 1: Let's use the installation assistant!
Let's make life a little easier for us and use the installation assistant.
-
Run the command to install cURL if you don't already have it!
sudo apt install curl -
Now run the command to install the installation assistant!
curl -sO https://packages.wazuh.com/4.7/wazuh-install.sh && sudo bash ./wazuh-install.sh -a
Give it a minute or 5.
Once finished you will get an output laid out like this:
We will use this information to access the Wazuh dashboard through a browser! Your username will initially be admin and keep in mind that extremely long password you get, make sure to copy that.
Step 2: Accessing our dashboard
In order to access our dashboard we'll need the IP address assigned to this VM and we can set up a static IP address exclusively for this VM or you can just saved a snapshot of this VM's current state and keep that IP address it already has.
In order to get your local IP address open up your terminal and run the command
ip a s
Go ahead and slap that IP address into your favorite browser and you'll see the login screen!
Input admin for username and that crazy long password for your password to get into your dashboard!
**Step 3: Your Dashboard **
Right off the bat Wazuh gives you some out of the box dashboard options to explore and customize!
Now that we're in business we can deploy agents across different machines, analyze our home network traffic, and explore a handful of other security concepts!
Concepts To Explore:
-
Network Traffic Analysis: Familiarize yourself with the basics of network traffic analysis using Wazuh! Identify what normal traffic looks like so you can later easily recognize anomalies!
-
Dashboard Customization: Explore the dashboard features of the Wazuh, customize the dashboard to display relevant information for understanding what data is the most critical to you!
-
Simulate Security Events: This is where the Kali Linux VM comes into play! Once you're comfortable with monitoring, use Kali Linux to generate simple security events, like a ping sweep, or port scan against your Ubuntu Wazuh agents. Observe how these events are captured and logged by Wazuh and it can help you understand how IRL threats might appear in your logs.
-
Alert Configurations: Start Configuring basic alerts in Wazuh! Choose a simple criteria like alerts for multiple failed login attempts or weird traffic spikes.
-
Involvement & Expansion: It's no fun to learn alone! Consider joining a community online related to home labs, SIEMs or Wazuh. For example r/homelab on Reddit and continue to expand your lab space to learn more and do more!