SEC 335 W1 Notes - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
NOTE: Information on this page is intended as notes and does contain text copy and pasted from readings/online sources. I do not claim to own this information, I have simply captured it for my studying needs.
Below are notes taken during/after class 8/30/22:
Filename: D1 -- 8/30/22
OS's and internet based applications commonly are sources of security breaches. Students will learn about the information security flaws in software systems, vulnerabilities inherent in common network services, ways to secure Internet servers and services, and increasing security awareness in organizations. Students will also learn the methodologies and tools used to probe networks for vulnerabilities and propose solutions. Hands-on activities will give the necessary background to assess security. Scenarios will provide opportunities to discuss security, ethics, and incident response.
Attack boxes to make them better, identify vulnerabilities
Tech journaling:
Huge, document your stuff as you go!!!
Eth hacking:
Rules to govern ourselves by by using offensive techniques
My group for the rules of hacking came up rules about hacking
tl;dr Ethically hack, not just hack
We were/are group 8
What is penetration testing (not the same as operation security, or information security):
-
Legal and authorized ability to hack and exploit vulnerabilities in client systems
-
Offensive security may not have the same authorization
Physical redteaming = Physically breaking into a company that is authorized
Black box hacking = affect contents of box, no visibility until you are actually hacking, takes longer, more realistic, may miss realistic targets
White box hacking = Already have perms, company may be watching, not realistic but more cost effective, more thorough, ensure everything is touched, results may not be entirely accurate to ease of exploiting
Types of hacking can be interchangeable, hybrid, start in white then blackbox
Vuln assessment is NOT the same as a pentest (often mistaken)
Vuln assessments can be used with a pentest
Pentesters complete many of the activities and use the same tools of malicious actors
Rules of engagement = protect self and customer, 5 W's
What can make you slip from pentest to hacker?:
-
Exit the scope for interest
-
Money
-
Sending stuff to friends
-
Power trip
-
Curiosity
-
A little too deep
-
Not reporting mistakes
Report mistakes
Cyber attack method:
Attacks are varied as motives and targets
Follow the same pattern (generally):
-
Recon - Find the targets
-
Probe - Find the vulnerability
-
Exploit - take advantage of the vulnerability to successfully complete attack
How to identify targets?: Scans
Try to find vulnerabilities to exploit
Stackoverflow checking
Once you find targets, exploit it
Phases of Pent test:
Similar to Cyber attack method
Gotta write report, and motivation is different
Reconnaissance:
Goals: Finding information about targets
-
Network info:
-
IP Addresses, Ranges
-
Domain info
-
Systems
-
Server names/Ips
-
Applications
-
What are they running
-
Security Tools
-
Firewalls
-
IPS
-
Endpoint Protection
-
People
-
Admins, Engineers
-
Developers
-
Others?
-
Partners
-
Vendors
-
Hosting Providers
Active vs. Passive Recon:
-Active recon includes interacting directly with the target. It is important to note that during this process, the target may record our IP address and log our activity. Requires permission if going beyond public access!
GREY AREA GOES HERE
-Passive recon makes use of the vast amount of information available on the web. When we are conducting passive reconnaissance, we are not interacting directly with the target and as such, the target has no way of knowing, recording , or logging our activity.
Passive: Domain Registration
ICANN - INternet corporation for assigned names and numbers (ICANN)
Organizations must register domain names
- Domain whois
Whois domain
Passive: IP Address Registration
IANA resources
Divided into 5 regions
Each region has a whois service
Net.educause.edu
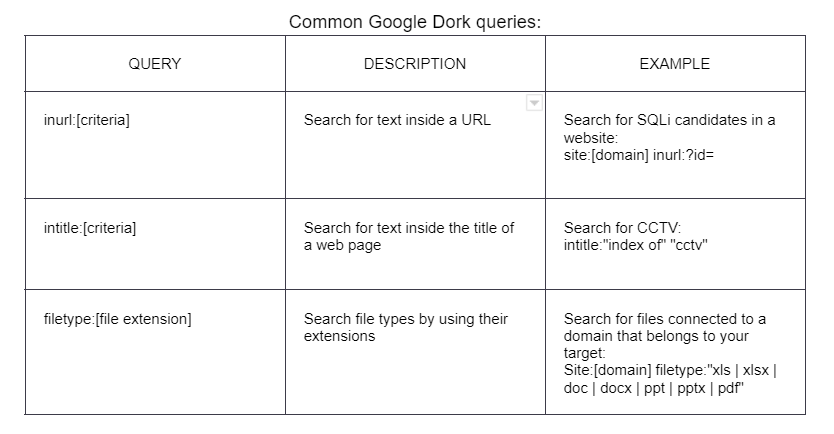
Passive: Google Hacking
Using public search engines and directories can yield a lot of valuable information
"Google Hacking" - using sites like Google to gather information anonymously (target cannot see unless you click through links)
What type of information
-
Interesting folks
-
Server info
-
Sensitive files
-
Vulnerabilities/footholds
-
Others?
Create SEC-355 folder in bookmarks
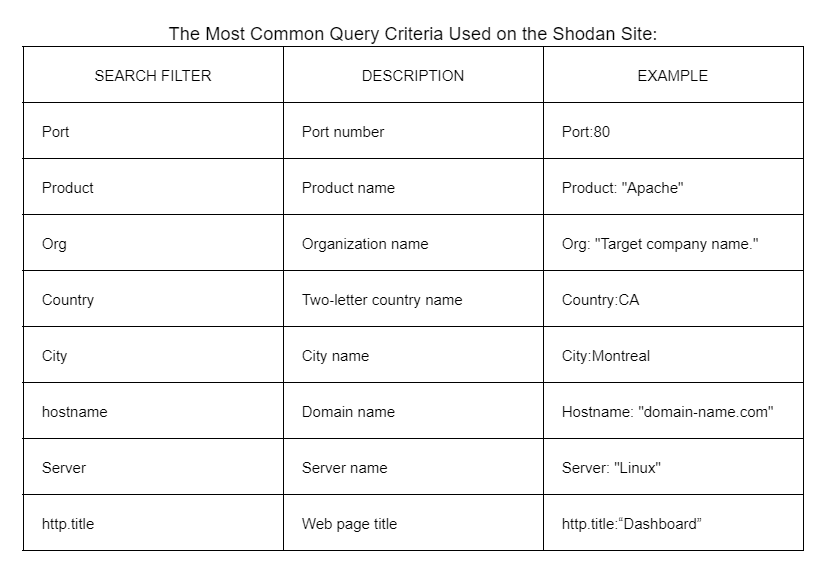
shodan
Other tools: Will be used next week
The Harvester = Command line tool to query multiple search engines
Netcraft
Metagoofi (grey area)
DNS can provide a tester with systems to target
Nslookup and dig are useful tools
Dnsrecon
Filename: CHAPTER 4: Internet Information Gathering
Information looking for during recon:
-
Company subdomains
-
Websites
-
Public IP addresses (including the one on the cloud AWS/Azure)
-
Leaked internal IP addresses
-
Public DNS records (MX mail records, etc.)
-
Leaked credentials (mainly on GitHub or Pastebin)
-
Previous breaches
-
Significant business change (e.g., acquisitions)
-
Business financial information (this can reveal a secret partner)
-
Business phone numbers (for social engineering)
-
Employee public information (for social engineering)
-
A company presence on social media (e.g., LinkedIn)
A list of search engines that you should add to your arsenal kit:
-
Google search engine: google.com - google dork to query powerful information from it's database
-
"site:" is a good first step as it gives all web pages associated with that page
-
Stuff may be leaked on Github
-
Shodan online scanner: shodan.io - scans internet for you
-
DuckDuckGo search engine: duckduckgo.com
When buying a domain name, personal information is required for the registration process. The Whois database will contain most of this info.
The command:
- whois [domain]
Will do a whois query
Whois will reveal as public information:
-
Registrant name
-
Contact phone number
-
E‐mail address
-
Entity physical address
-
Domain expiry date
-
NS (Name Servers) servers
The command:
- theHarvester -d [domain] -b [online sources] -s
Broken down is:
-
‐d is for specifying your target's name.
-
‐s is to search on the Shodan web engine.
-
‐b is the online data source name; in the figure, I've chosen all of them. Here's the list from which you can choose (use the help command ‐h for more options):
-
Baidu
-
Bing
-
bing API
-
Certspotter
-
Crtsh
-
DnsDumpster
-
Dogpile
-
Duckduckgo
-
Github‐code
-
Google
-
Hunter
-
Intelx
-
Linkedin and Linkedin_links
-
Netcraft
-
Otx
-
SecurityTrails
-
Threatcrowd
-
Trello
-
Twitter
-
Vhost
-
VirusTotal
-
Yahoo
-
All (executes all the preceding data sources)
The tool "DMitry" can be used to do multiple tasks at the same time, for example "dmitry -wnse [domain-name.com]" broken down is:
-
‐w : Perform a Whois lookup.
-
‐n : Retrieve records from Netcraft.com about the target.
-
‐s : Look for subdomains.
-
‐e : Search for e‐mail addresses.
-
‐p : Scan for TCP open port (this is not passive).
Maltego is a decent tool but does require payment.
Maltego is a tool that not only can perform many actions, but also visualizes them.
Recon-ng is a free alternative to Maltego.