Passive_Recon - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
NOTE: Information on this page is intended as notes and does contain text copy and pasted from readings/online sources. I do not claim to own this information, I have simply captured it for my studying needs.
Below are notes taken during/after:
Filename: D1 -- 8/30/22
-Passive recon makes use of the vast amount of information available on the web. When we are conducting passive reconnaissance, we are not interacting directly with the target and as such, the target has no way of knowing, recording , or logging our activity.
Passive: Domain Registration
Passive: IP Address Registration
-
IANA resources
-
Divided into 5 regions
-
Each region has a whois service
-
Net.educause.edu
Passive: Google Hacking
Using public search engines and directories can yield a lot of valuable information
"Google Hacking" - using sites like Google to gather information anonymously (target cannot see unless you click through links)
What type of information
-
Interesting folks
-
Server info
-
Sensitive files
-
Vulnerabilities/footholds
-
Others?
Filename: CHAPTER 4: Internet Information Gathering
Information looking for during recon:
-
Company subdomains
-
Websites
-
Public IP addresses (including the one on the cloud AWS/Azure)
-
Leaked internal IP addresses
-
Public DNS records (MX mail records, etc.)
-
Leaked credentials (mainly on GitHub or Pastebin)
-
Previous breaches
-
Significant business change (e.g., acquisitions)
-
Business financial information (this can reveal a secret partner)
-
Business phone numbers (for social engineering)
-
Employee public information (for social engineering)
-
A company presence on social media (e.g., LinkedIn)
A list of search engines that you should add to your arsenal kit:
-
Google search engine: google.com - google dork to query powerful information from it's database
-
"site:" is a good first step as it gives all web pages associated with that page
-
Stuff may be leaked on Github
-
Shodan online scanner: shodan.io - scans internet for you
-
DuckDuckGo search engine: duckduckgo.com
When buying a domain name, personal information is required for the registration process. The Whois database will contain most of this info.
The command:
- whois [domain]
Will do a whois query
Whois will reveal as public information:
-
Registrant name
-
Contact phone number
-
E‐mail address
-
Entity physical address
-
Domain expiry date
-
NS (Name Servers) servers
The command:
- theHarvester -d [domain] -b [online sources] -s
Broken down is:
-
‐d is for specifying your target's name.
-
‐s is to search on the Shodan web engine.
-
‐b is the online data source name; in the figure, I've chosen all of them. Here's the list from which you can choose (use the help command ‐h for more options):
-
Baidu
-
Bing
-
bing API
-
Certspotter
-
Crtsh
-
DnsDumpster
-
Dogpile
-
Duckduckgo
-
Github‐code
-
Google
-
Hunter
-
Intelx
-
Linkedin and Linkedin_links
-
Netcraft
-
Otx
-
SecurityTrails
-
Threatcrowd
-
Trello
-
Twitter
-
Vhost
-
VirusTotal
-
Yahoo
-
All (executes all the preceding data sources)
The tool "DMitry" can be used to do multiple tasks at the same time, for example "dmitry -wnse [domain-name.com]" broken down is:
-
‐w : Perform a Whois lookup.
-
‐n : Retrieve records from Netcraft.com about the target.
-
‐s : Look for subdomains.
-
‐e : Search for e‐mail addresses.
-
‐p : Scan for TCP open port (this is not passive).
Maltego is a decent tool but does require payment.
Maltego is a tool that not only can perform many actions, but also visualizes them.
Recon-ng is a free alternative to Maltego.
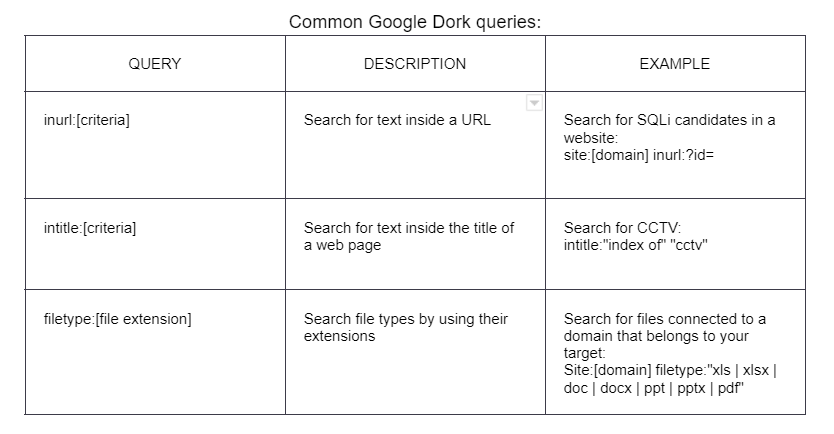
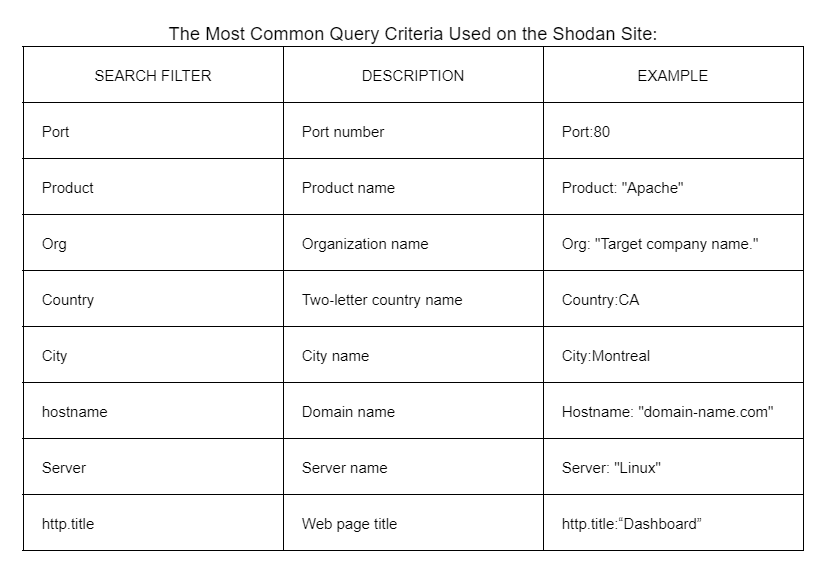
Filename: General passive recon notes
- Dmitry is a really good tool (whois, etc)
- Find information first, then dig
- If in team, attempt to have each person doing something
- Look at the website source code for hints on web server
- Look at business records, find registrar name
- With names, look at associates (linkedin, social media in general)
- Know when to keep digging and what's a dead end
- Document document, and oh...document