Milestone 6 Blue Network and vyos Provisioning with Ansible - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
This page journals content related to NET/SEC/SYS-480 milestone 6.
NOTE: For the Milestone video, I actually recreated fw-blue1 from scratch. The steps taken were the exact same, but the DHCP IP assigned on the 480-WAN interface before Ansible might be different. BE SURE TO USE Get-VMIP TO GET THE IP/VMName/MAC.
Table of contents
VM Inventory
Milestone 6.1 - Network Utility Functions
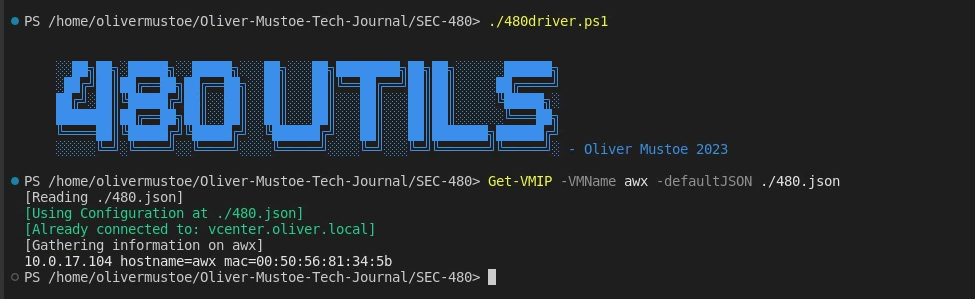
First I created the functions Get-VMIP to get networking information about the VMs first adapter, New-Network to create a new virtual switch/portgroup, and StandardError where I placed the standard error formatting that I use in my try catch statements in 480-utils.psm1.
With these functions I could get the networking information I needed (command run and output below):
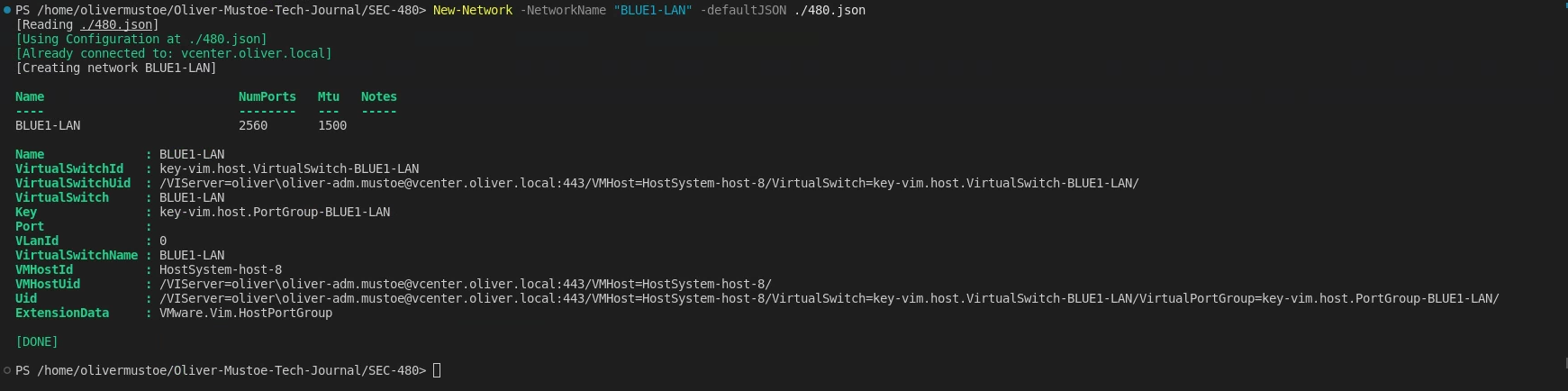
And I could make a new Virtual network (command run and output below):
New-Network -NetworkName "BLUE1-LAN" -defaultJSON ./480.json
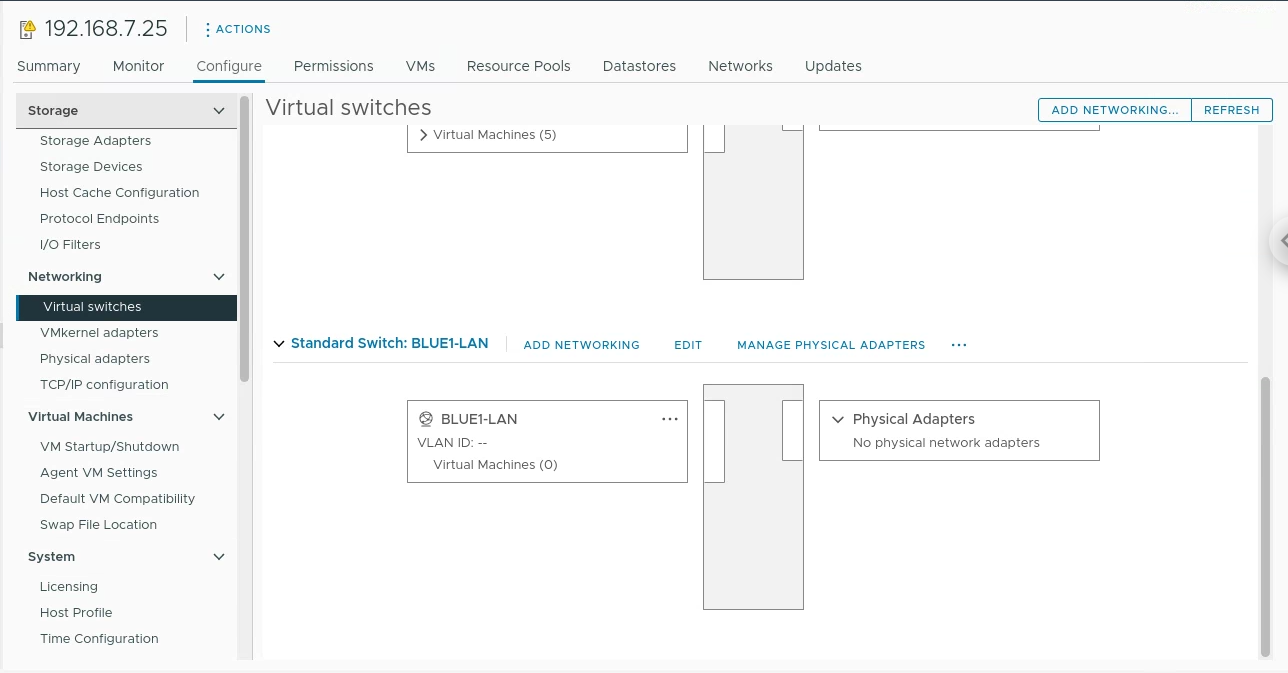
6.1 reflection
This part of the milestone was a nice brush up on Powershell, after not using it for a few days, and a cool chance to add extra utility to 480-utils. I originally was pulling the hostname VMWare detected for my get-ip function, but I relooked at the documentation and realized that I was actually just supposed to get the vm name (which I was entering anyway, so I could just pull that.) The creation of the virtual switch/portgroup was much simpler than I thought it was going to be, which is appreciated (thanks VMWare.)
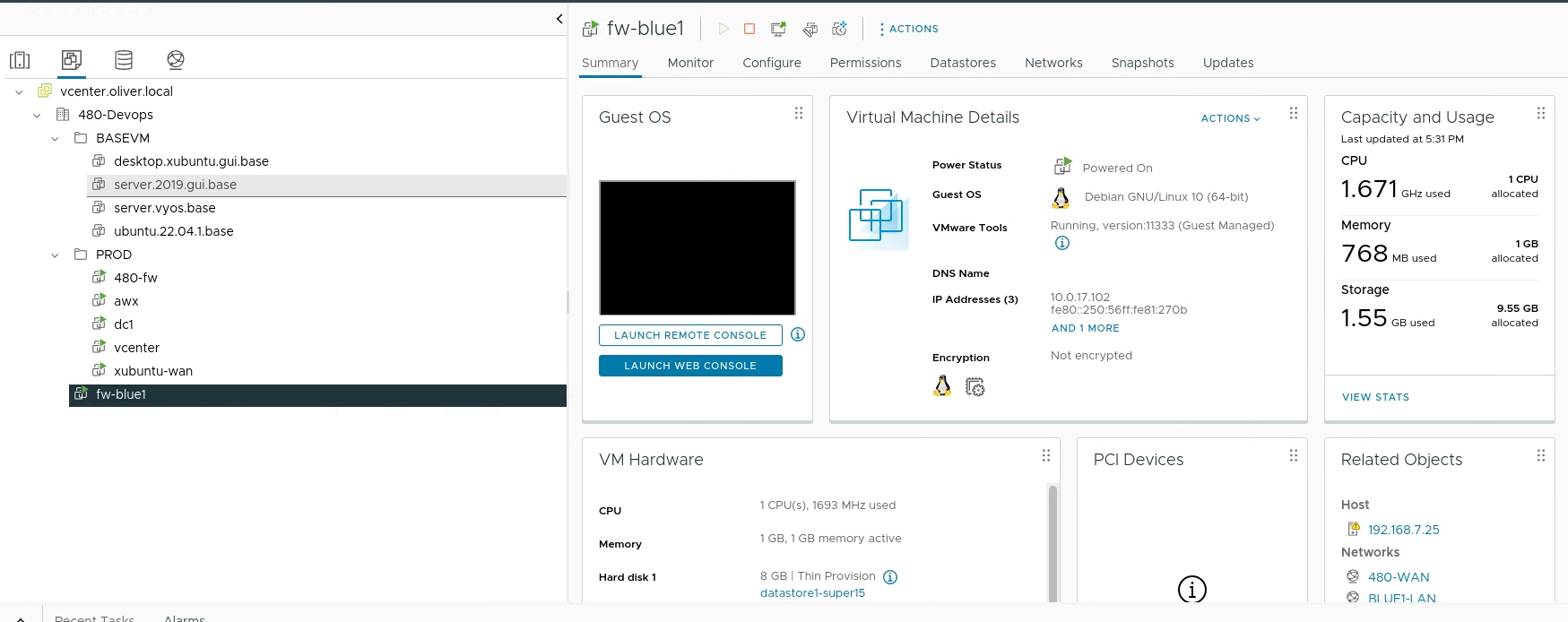
Milestone 6.2 - Cloning, Networking and Starting fw-blue1
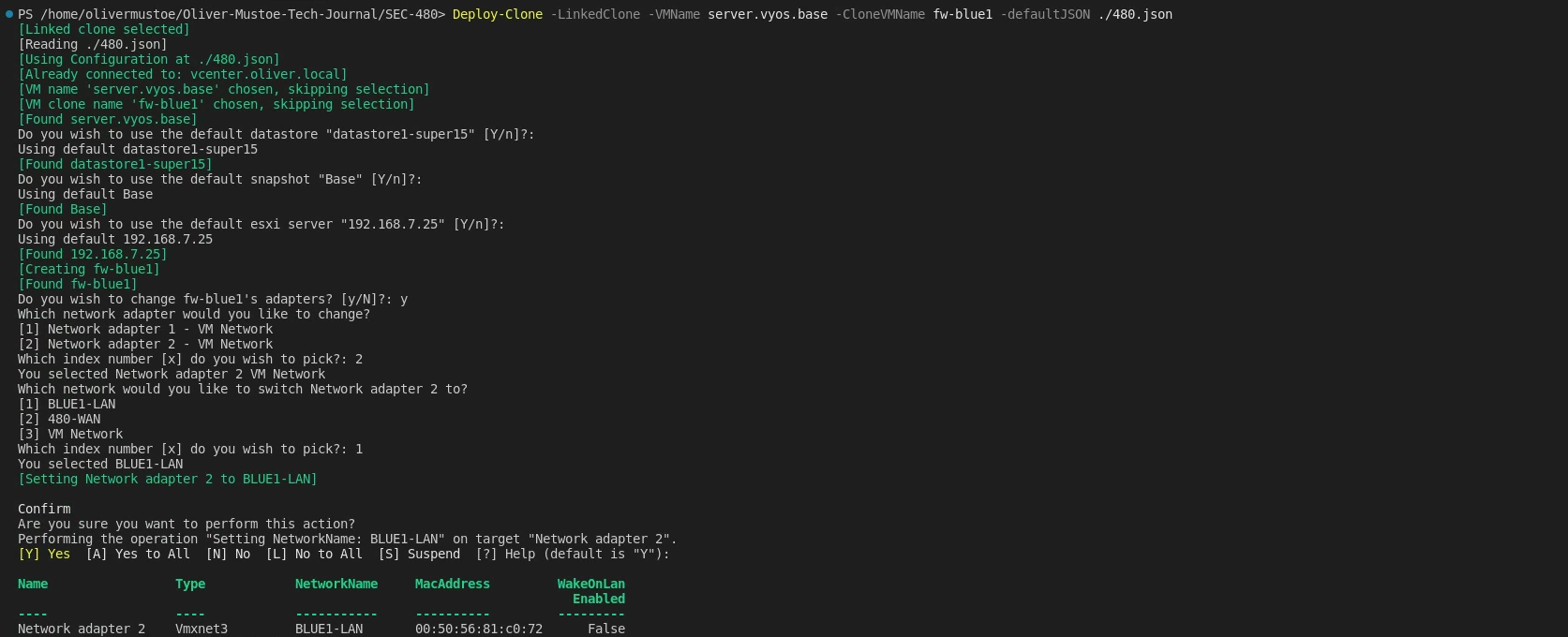
I updated/refined my previous functions to switch network adapters/power on a VM and deployed “fw-blue1” like the following (NOTE: After completeing fw-blue1, "Switch-VMNetworkAdapter" function was changed to "Set-Network". The functions functionality was not changed!):
Deploy-Clone -LinkedClone -VMName server.vyos.base -CloneVMName fw-blue1 -defaultJSON ./480.json
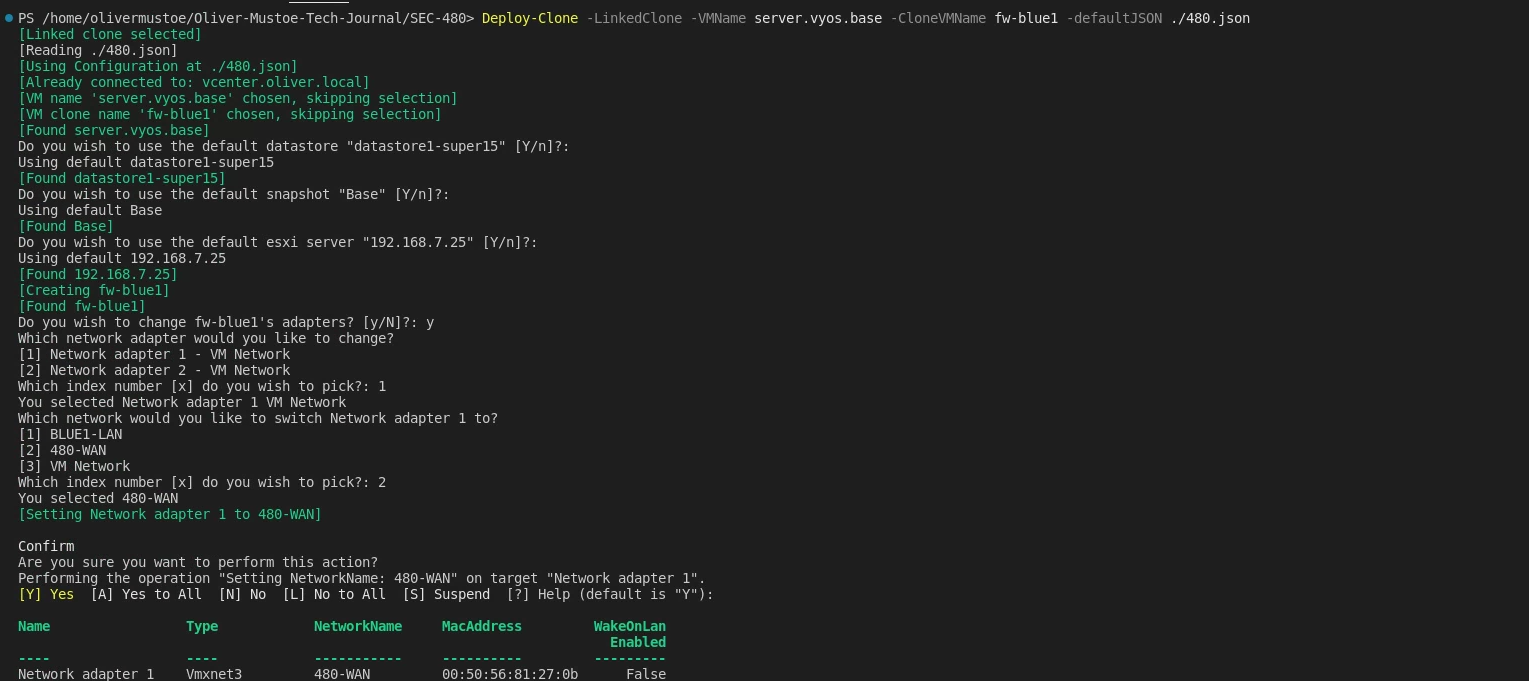
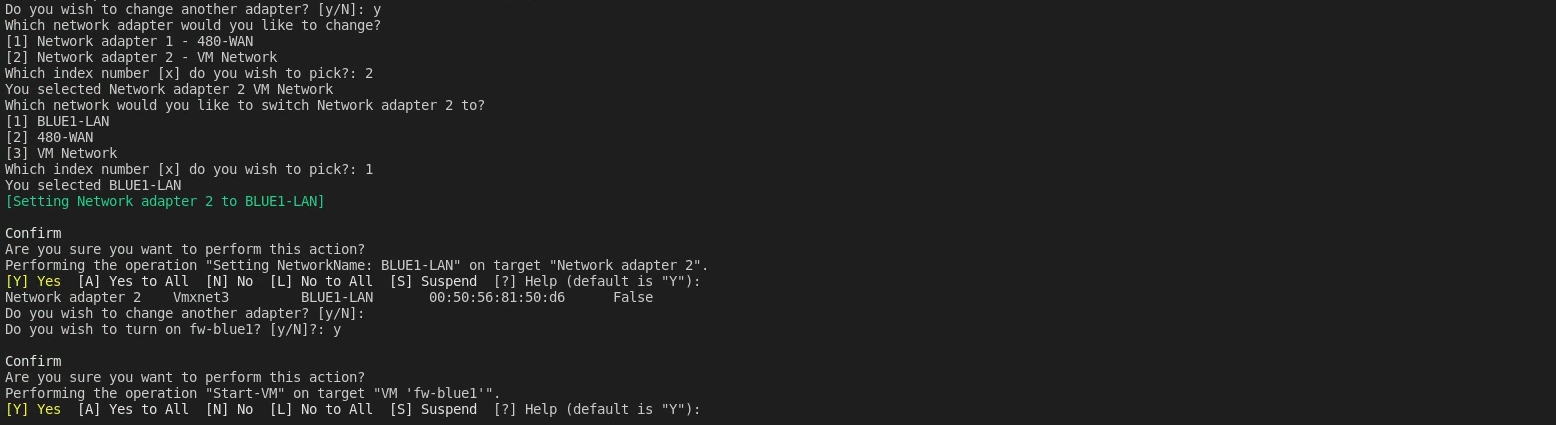
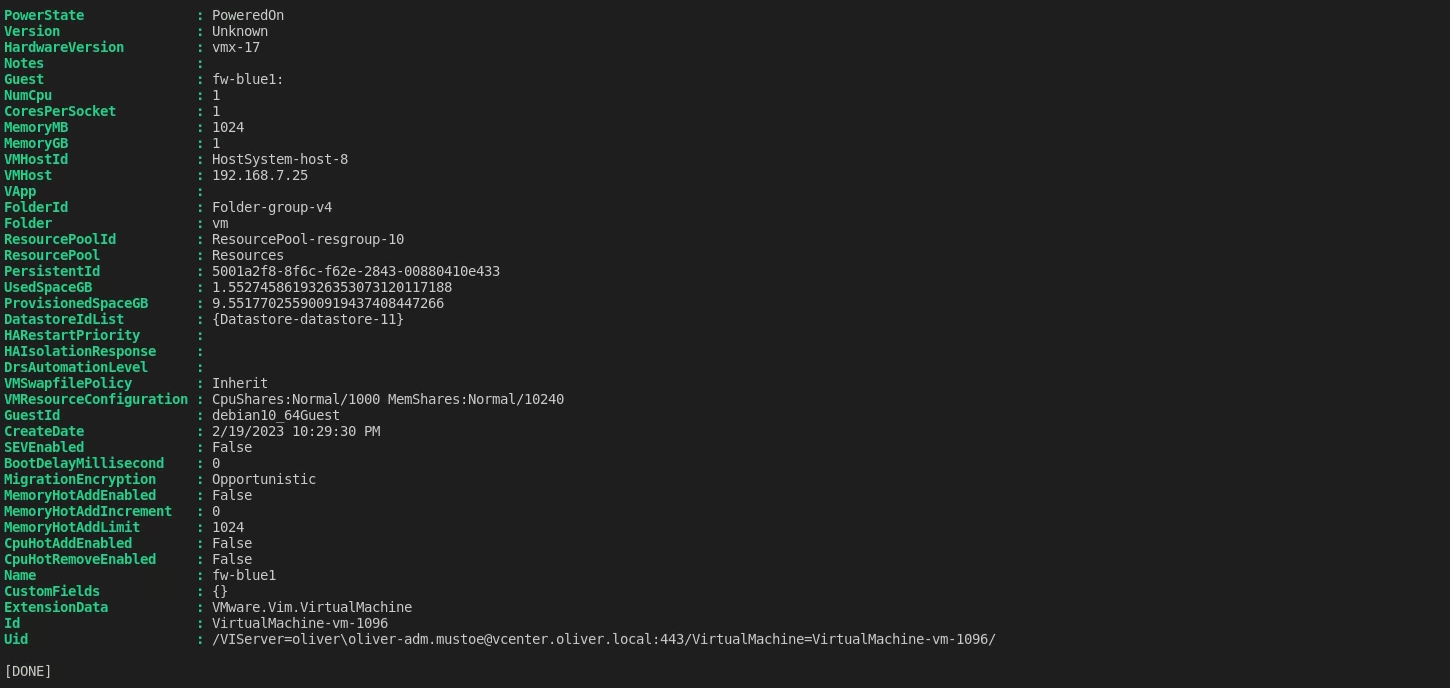
Strangely, when I tried to login the password I had on file was wrong (also double checked and COULD SSH into 480-fw with the password and it works, and I checked the history of 480-fw and didn’t see any changes to the password.)
Because of this I created a new full linked clone from 480-fw:
Deploy-Clone -FullClone -VMName 480-fw -CloneVMName test-vyos -defaultJSON ./480.json
Powered on test-vyos and selected the option for the login reset:
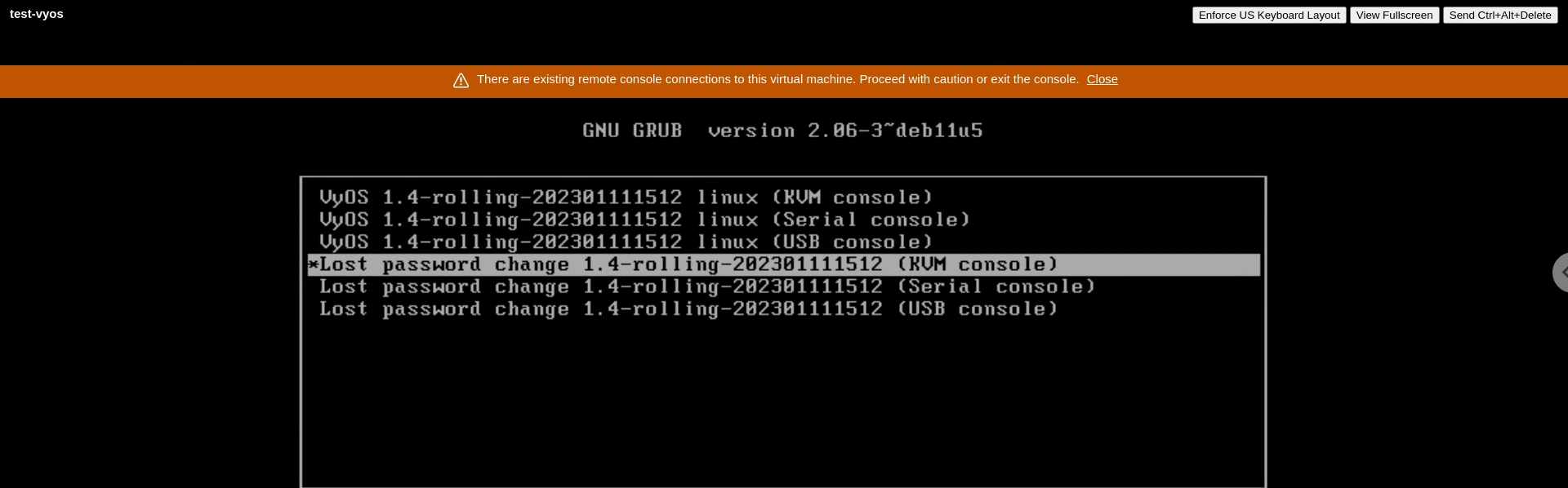
Selected ‘y’ to reset the login to the password on file:
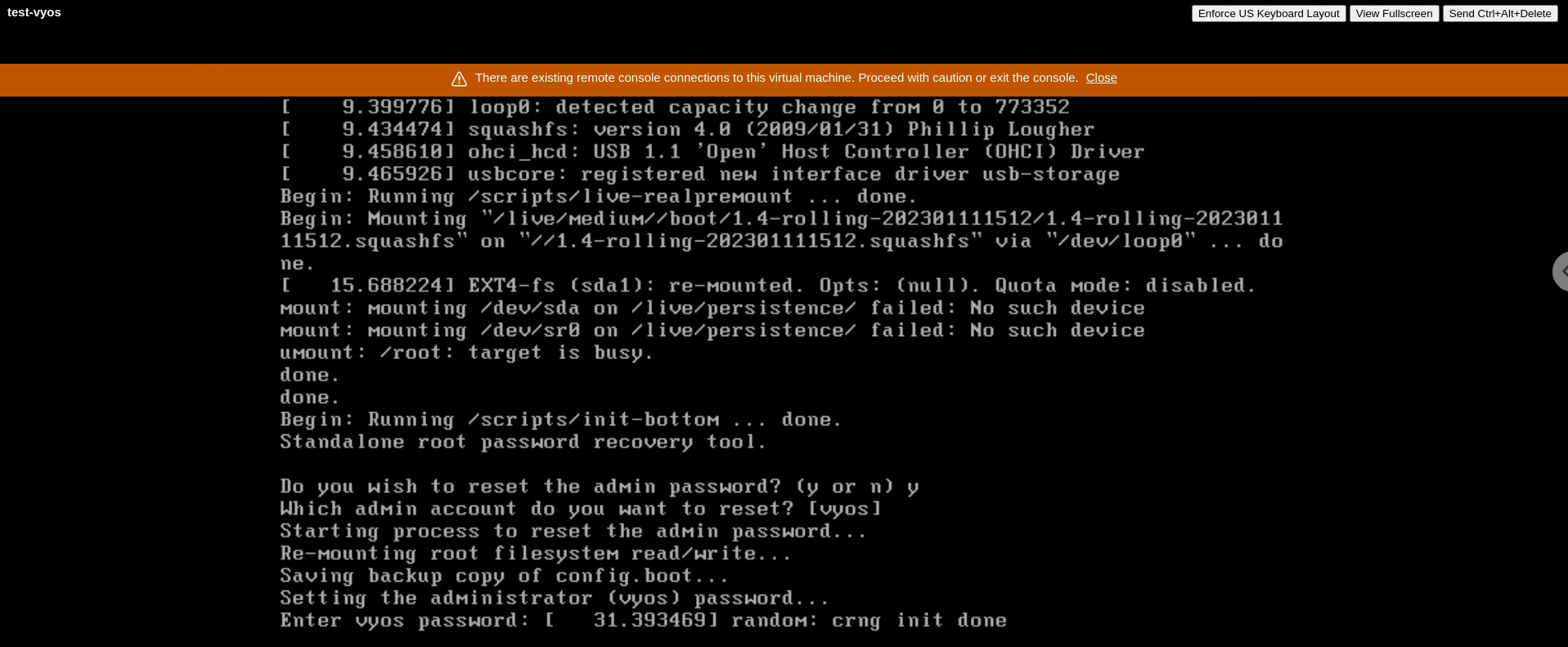
I then logged in with the reset password and ran the following to prep the VM (from Milestone 1):
configure
delete interfaces ethernet eth0 hw-id
delete iterfaces ethernet eth1 hw-id
set interfaces ethernet eth0 address dhcp
set service ssh listen-address 0.0.0.0
commit
save
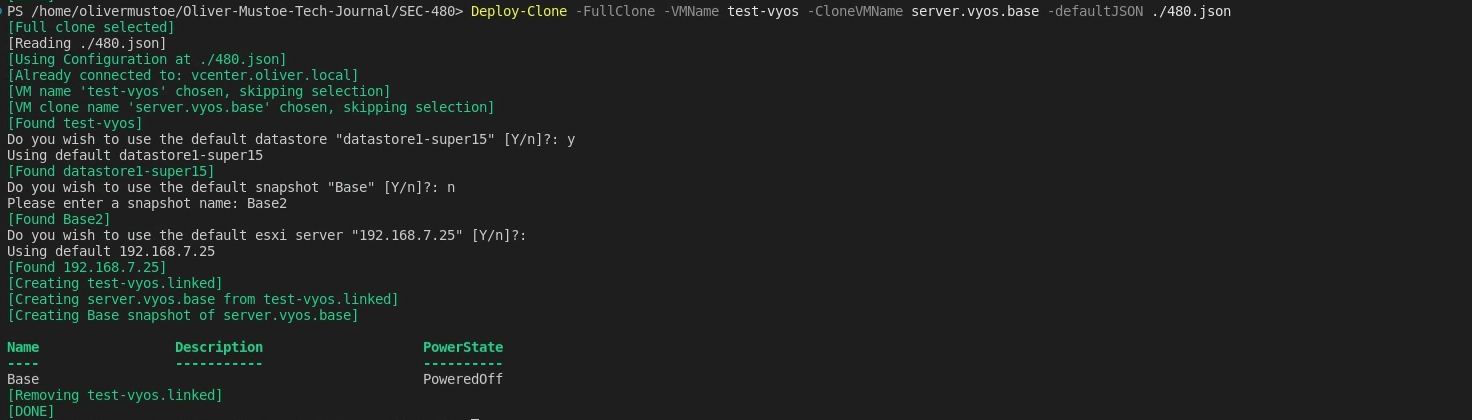
I would then power down the VM > Take a snapshot called Base2 > Deploy a new vyos base with the following (deleted the other base and fw-blue1):
Deploy-Clone -FullClone -VMName test-vyos -CloneVMName server.vyos.base -defaultJSON ./480.json
I then deployed fw-blue1 like the previous deployment:
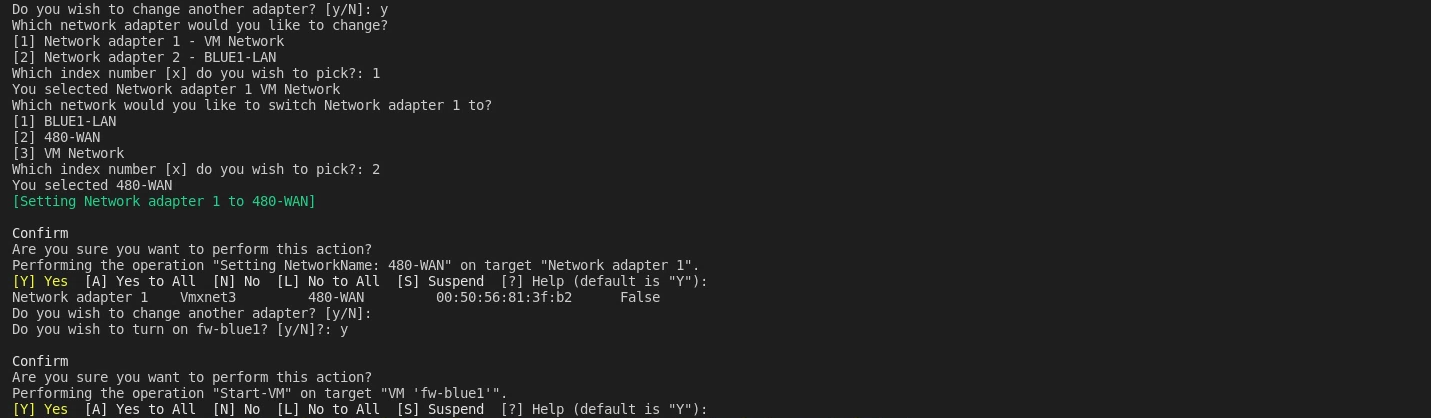
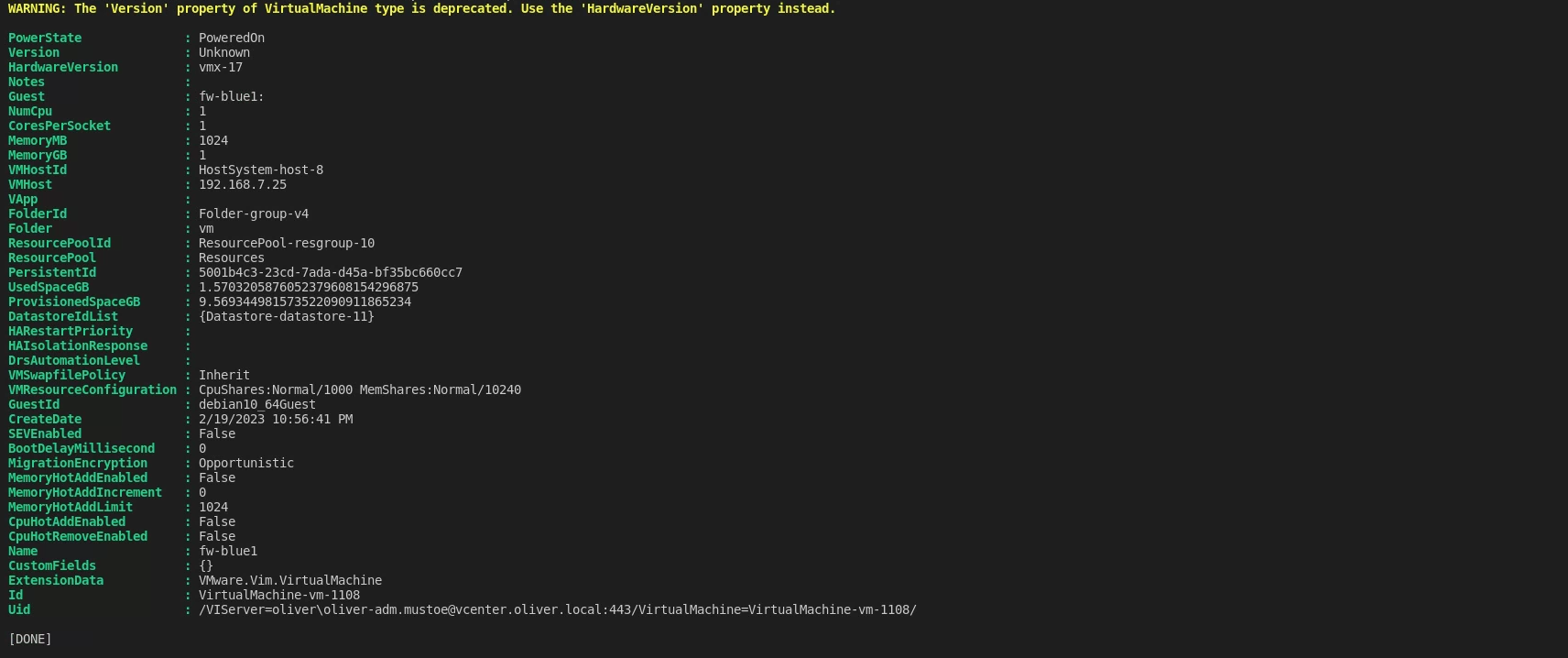
And I was able to login successfully:
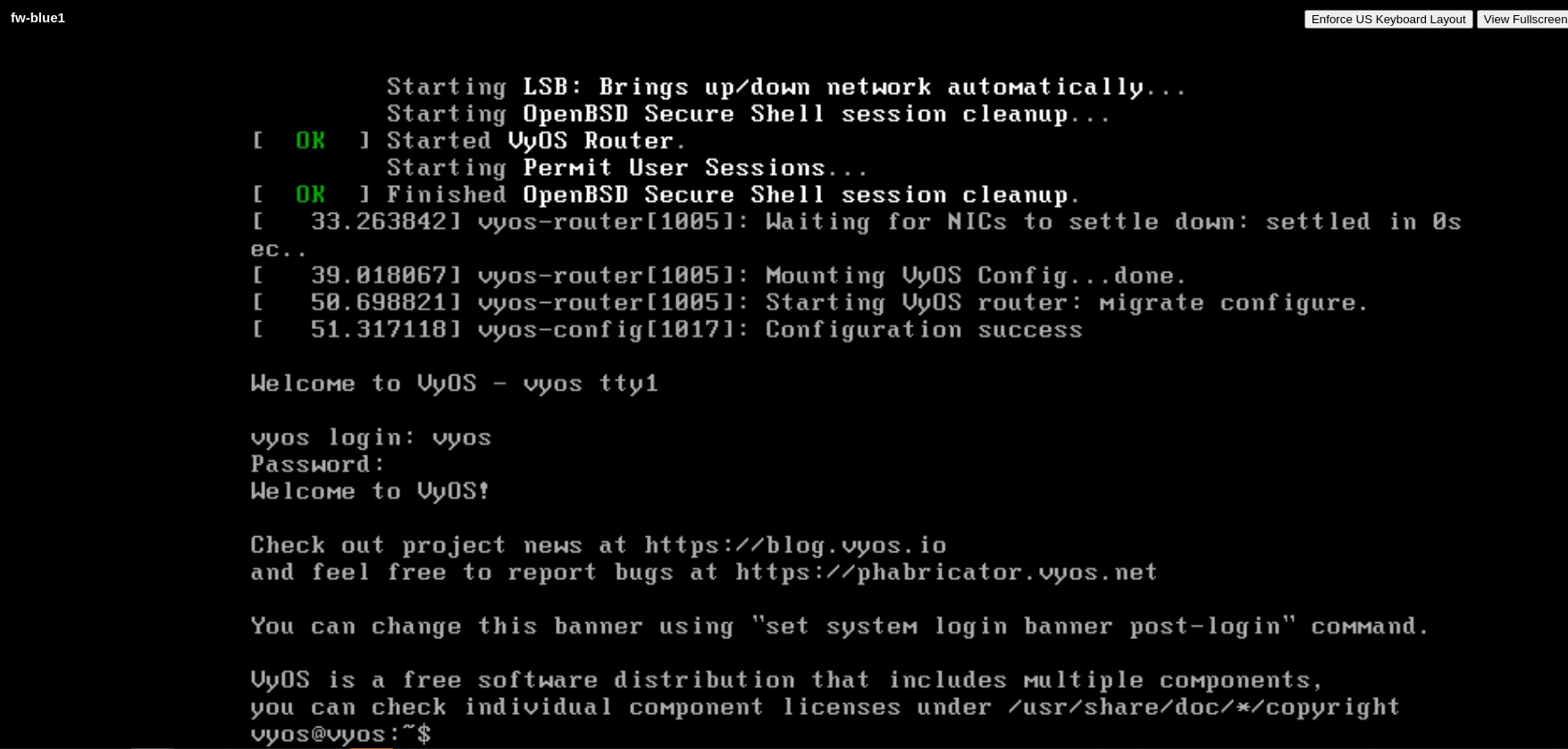
6.2 reflection
This part of the milestone was way more convoluted than it needed to be on my end. I still don't know what happened in making the base image from 480-fw that the password wasn’t set, I even tried the default vyos:vyos user/pass combination but that didn’t work. This did give me the opportunity to see how powerful/useful 480-utils is. I could quickly make a new full clone, run what I needed to, and perfectly redeploy fw-blue1 in a very faster amount of time compared to by hand. Either way, I can access both my firewalls and am prepped for Ansible!
Milestone 6.3 - Ansible Ping
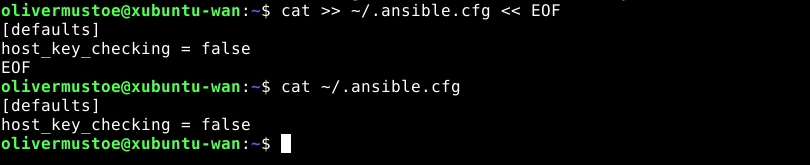
I used the following command to setup my ansible.cfg:
cat >> ~/.ansible.cfg << EOF
[defaults]
host_key_checking = false
EOF
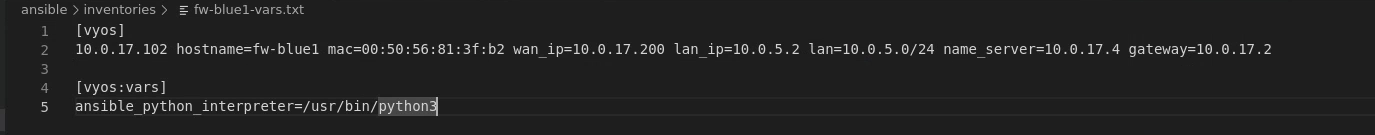
Then I filled in a inventory file (fw-blue1-vars.txt) like the following (taking the output of Get-VMIP -VMName fw-blue1 -defaultJSON ./480.json and adding it before wan_ip):
[vyos]
10.0.17.102 hostname=fw-blue1 mac=00:50:56:81:3f:b2 wan_ip=10.0.17.200 lan_ip=10.0.5.2 network=10.0.5.0/24 nameserver=10.0.17.4 gateway=10.0.17.2
[vyos:vars]
ansible_python_interpreter=/usr/bin/python3
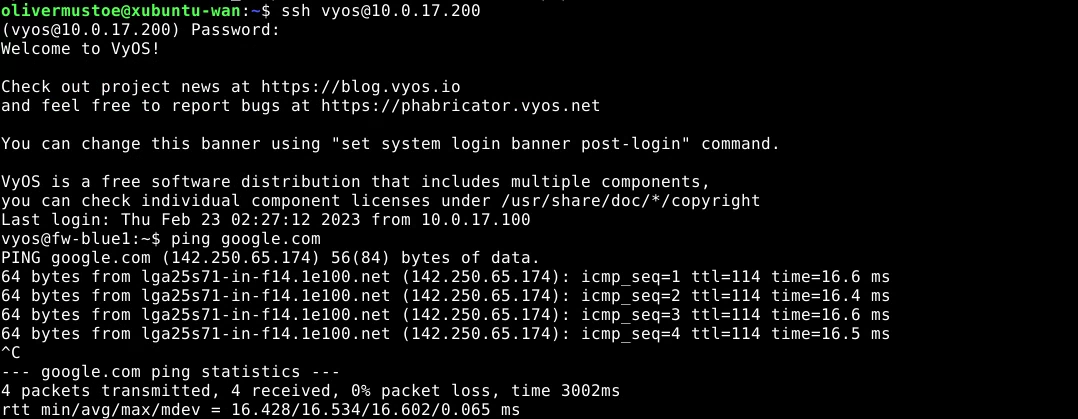
And could ping the host:
ansible vyos -m ping -i ansible/inventories/fw-blue1-vars.txt --user vyos --ask-pass
Milestone 6.4 - vyos configuration
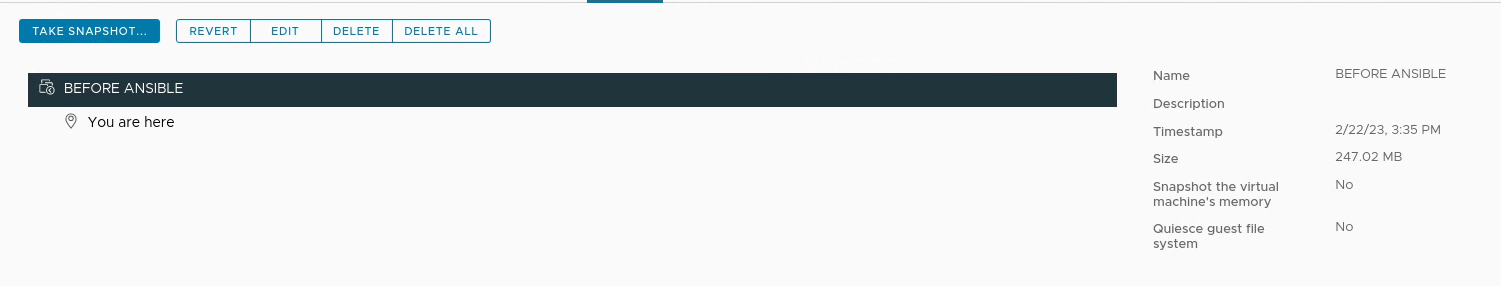
First I created a snapshot of fw-blue1 by going to fw-blue1 in vCenter > shutting it down > Snapshots > TAKE SNAPSHOT… > Named it “BEFORE ANSIBLE”:
Then I powered it on and ran the following commands while SSH’d into fw-blue1/the last command on the system itself:
configure
# Interface setup for eth0
delete interfaces ethernet eth0 address dhcp
set interfaces ethernet eth0 address 10.0.17.200/24
# Interface setup for eth1
set interfaces ethernet eth1 address 10.0.5.2/24
# Gateway and DNS setup
set protocols static route 0.0.0.0/0 next-hop 10.0.17.2
set system name-server 10.0.17.4
# DNS forwarding setup
set service dns forwarding listen-address 10.0.5.2
set service dns forwarding allow-from 10.0.5.0/24
set service dns forwarding system
# NAT forwarding setup
set nat source rule 10 outbound-interface eth0
set nat source rule 10 source address 10.0.5.0/24
set nat source rule 10 translation address masquerade
# Setting system hostname
set system host-name fw-blue1
commit
save
I did this so that the /config/config.boot file would contain the needed file structure for jinja templating.
After running the commands, I saved the output of:
cat /config/config.boot
on fw-blue1 to a file in my Github repository under SEC-480/ansible/files/vyos/config.boot.js:
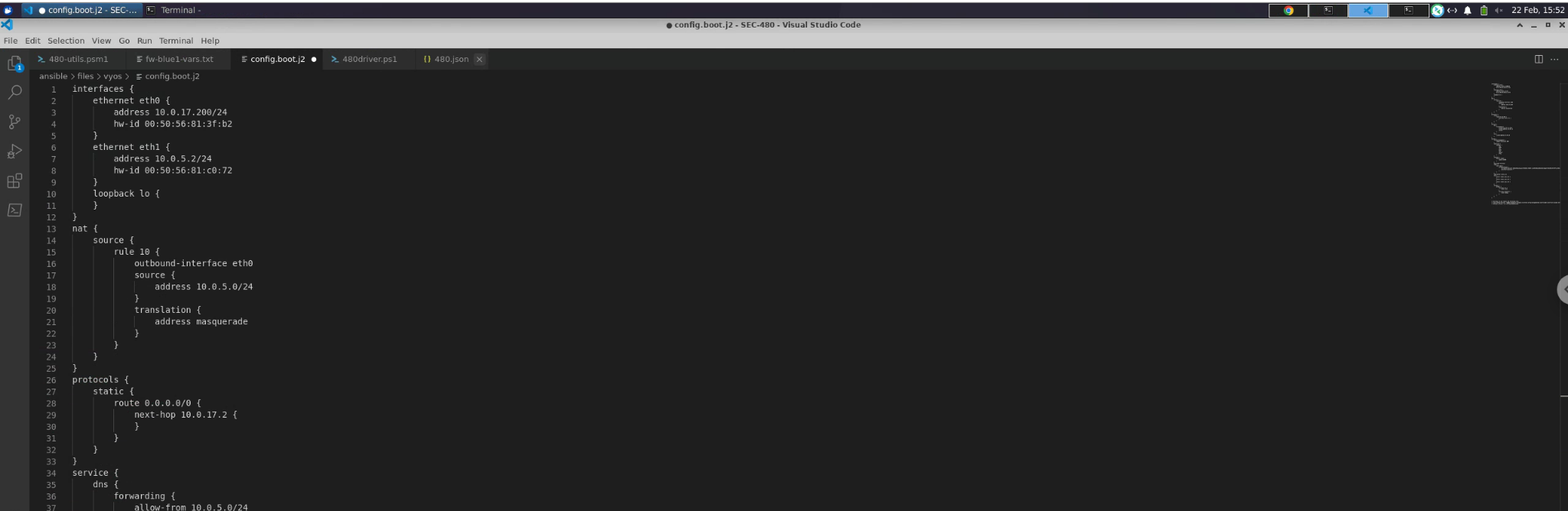
I then updated my vars file like the following:
Then, taking from my fw-blue1-vars.txt file, for each variable set in the vars file I would replace the value in the config.boot.j2 file with the key in jinjia format ({{ }}). For example in the case of the variable key pair gateway=10.0.17.2 , I would replace all instances of 10.0.17.2 with {{ gateway }}. I would also make sure that none of the replaces would impact another replace, so in the case of 10.0.17.2 I added a space at the end of the find to ensure I only interacted with just that IP!
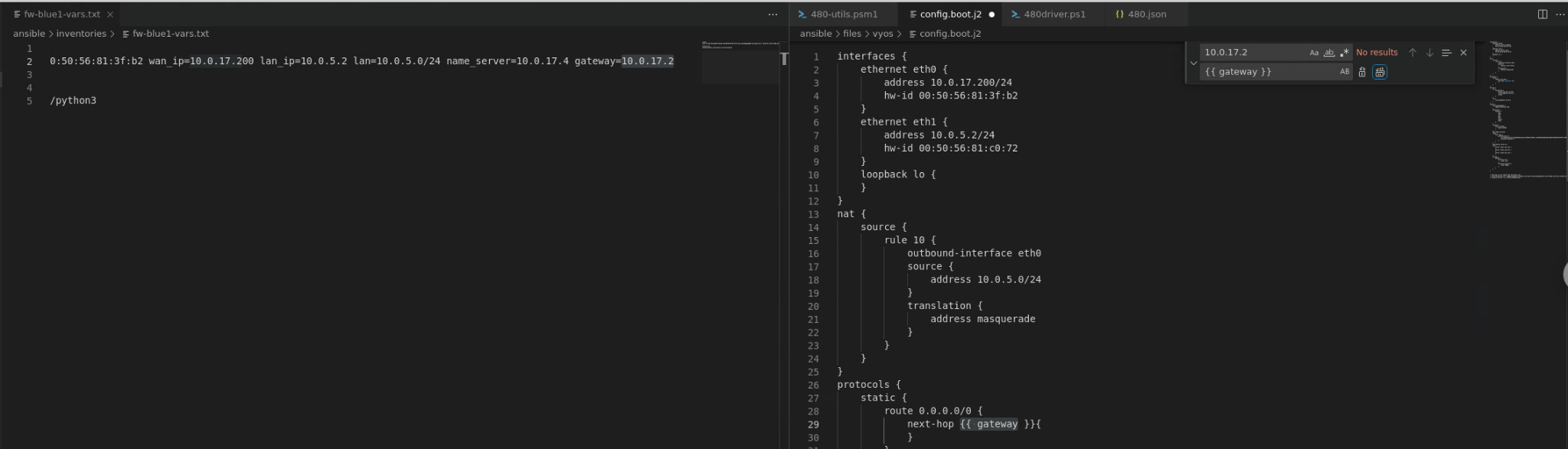
For 10.0.17.2, I would have to add back in the space:
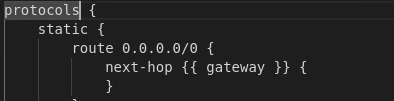
I would also remove the lines in the interfaces section dealing with hw-id’s:
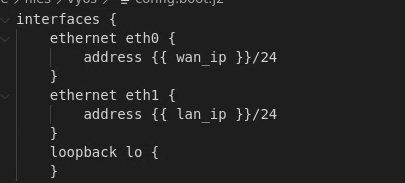
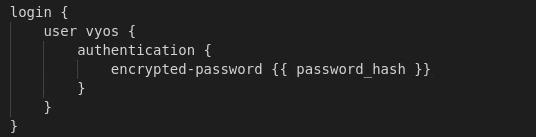
I also had to edit the password lines to look like the following (removing plaint-text password):
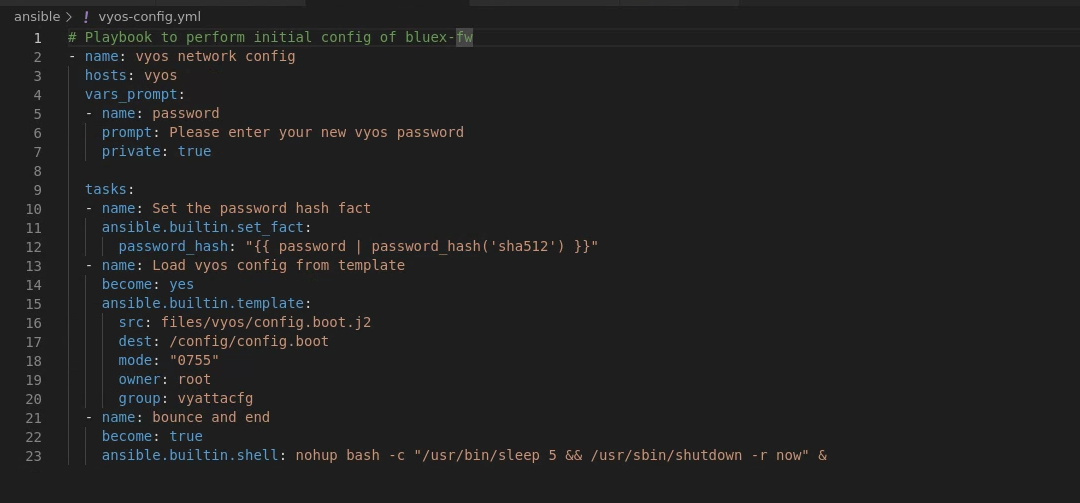
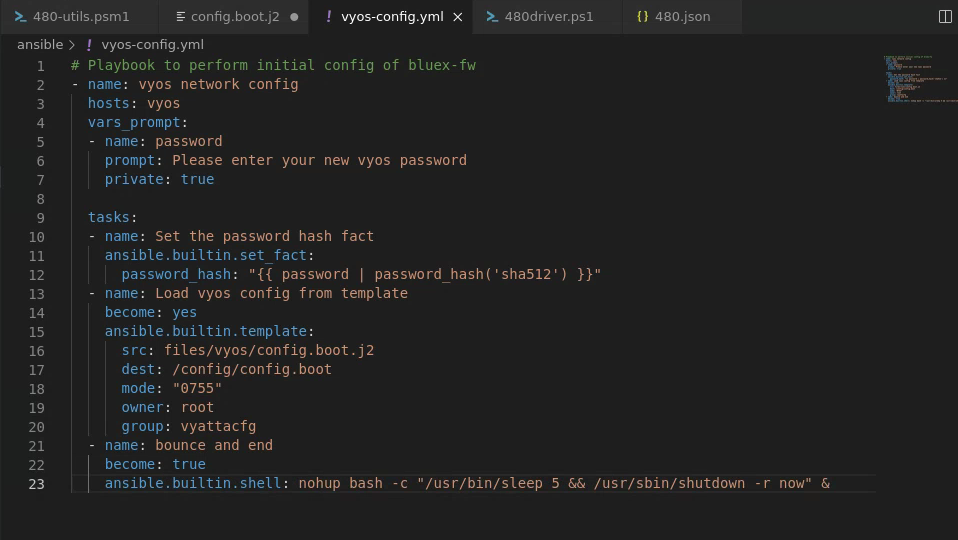
I then made the following Ansible file to configure fw-blue1:
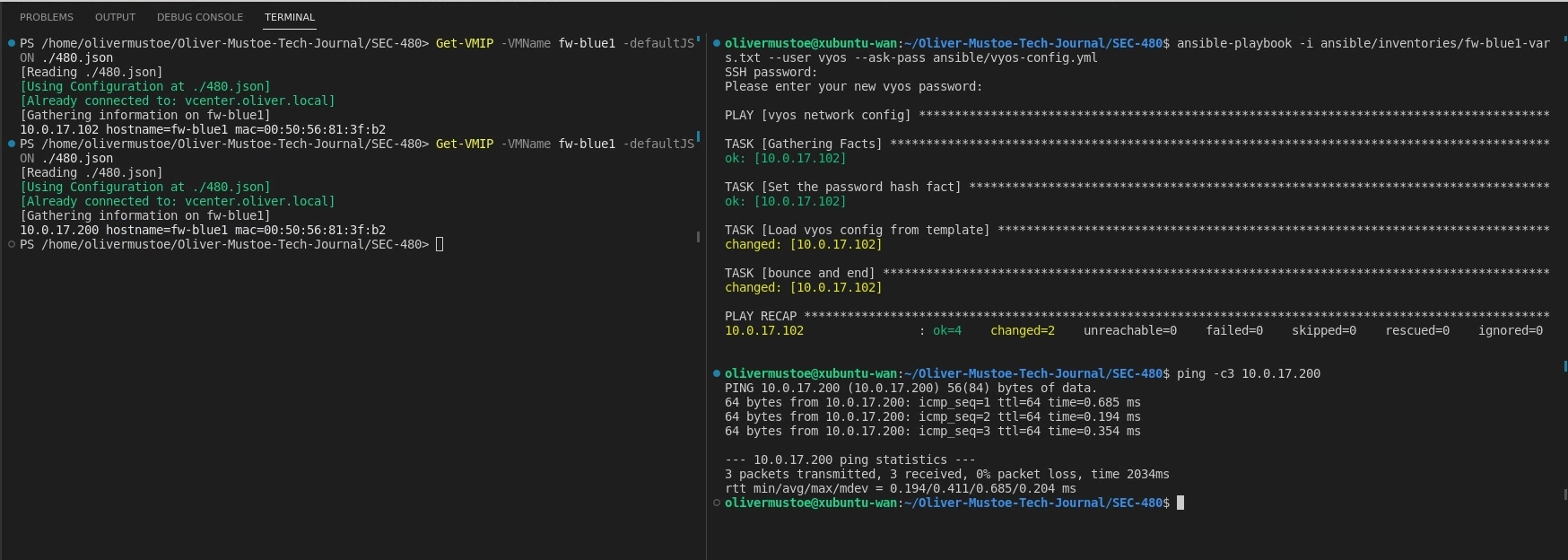
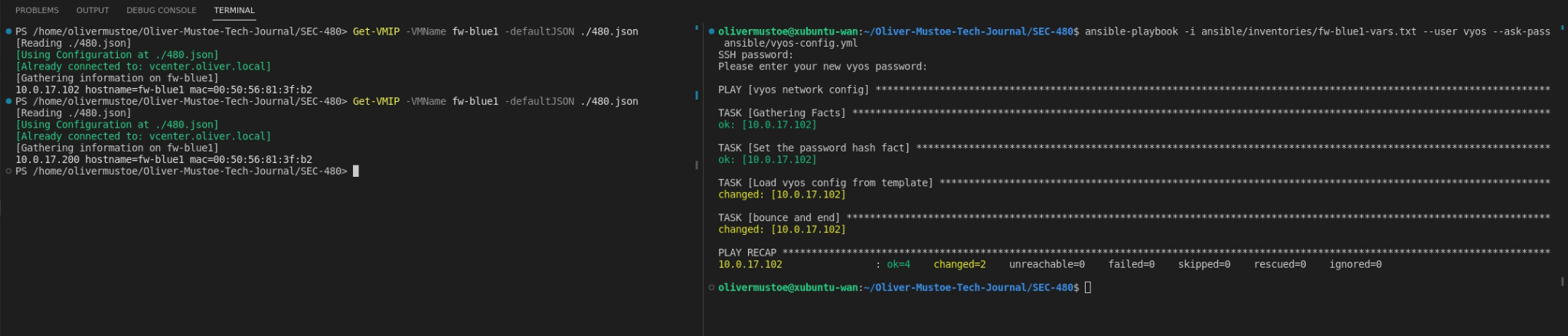
Below is a running of the Ansible script (right, and the output of Get-VMIP (on the left):
ansible-playbook -i ansible/inventories/fw-blue1-vars.txt --user vyos --ask-pass ansible/vyos-config.yml
Troubleshooting 6.4:
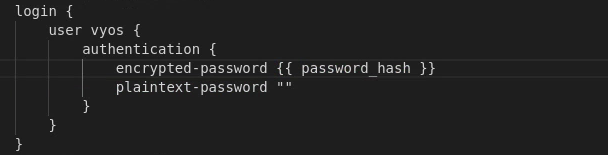
First I set the encrypted password to line in the config to {{ password_hash }}:
With this set and saved, I then made my Ansible script like the following:
Then I reset fw-blue1 back to the snapshot and turned it on, once it was on I ran the above script like the following (left shows the ip changing, right shows the ansible playbook run!):
But this resulted in the password not changing, but everything else was implemented correctly. To troubleshoot, I took the initial configuration I made and fw-blue1’s config after using Ansible. I didn’t see anything different. I then compared the fw-blue1’s config after using Ansible to 480-fw and found that the plaintext-password line was removed. Once I removed this line from config.boot.j2, the password worked!
6.3 and 6.4 reflection
I decided to combine the last 2 sub-milestones of milestones 6 together as 6.3 didn’t have much substance to reflect on. Having had some experience with Ansible, I had never before set up the inventory with the variables set. I have previously used group_vars to set variables, but I have never done it in the inventory file before. While later ansible scripts will require the use of an ansible-vault for secrets, it was interesting to see the ability to give variables to hosts in that way. In 6.4, I have used jinja templating a bit in Python and in Ansible scripts, but I have not used it solely for templating. It is very interesting to me and I want to see other applications for it. When making my config, I did have a bit of confusion when it came to setting the password, as it seemingly refused to change. I believe this to be the doing of the plaintext-password line, and I think I could have saved myself a lot of hassle by resetting fw-blue1 when I set its config manually THEN taking its configuration as a base. Also had a weird issue where my spaces were being replaced by a different unicode character, don't even know how that happened but I have added it to the troubleshooting steps! Overall, a fun milestone and I can’t wait for more Ansible!
Sources for all:
Can't find something? Check in the Milestone 6 Backup